Legal Aspect and Ethics of Computing Course Note
Made by Mike_Zhang
Notice | 提示
PERSONAL COURSE NOTE, FOR REFERENCE ONLY
Personal course note of COMP3511 Legal Aspect and Ethics of Computing, The Hong Kong Polytechnic University, Sem2, 2023/24.
Mainly focus on Ethical Management and Analysis, InfoSec Ethics, AI Ethics, Privacy & GDPR, Computer Related Law & International AI, Computer Related Crime Case Studies, IP Management, Entrepreneurship Sustainability Development, Entrepreneurship Ecosystem, and Professional Bodies and Code of Conduct.个人笔记,仅供参考
本文章为香港理工大学2023/24学年第二学期 计算机法律和伦理(COMP3511 Legal Aspect and Ethics of Computing) 个人的课程笔记。
Unfold Study Note Topics | 展开学习笔记主题 >
1. Introduction
1.1 What is right things to do?
https://www.youtube.com/watch?v=kBdfcR-8hEY
1.2 The Trolley Problem
To Turn or Not To Turn?
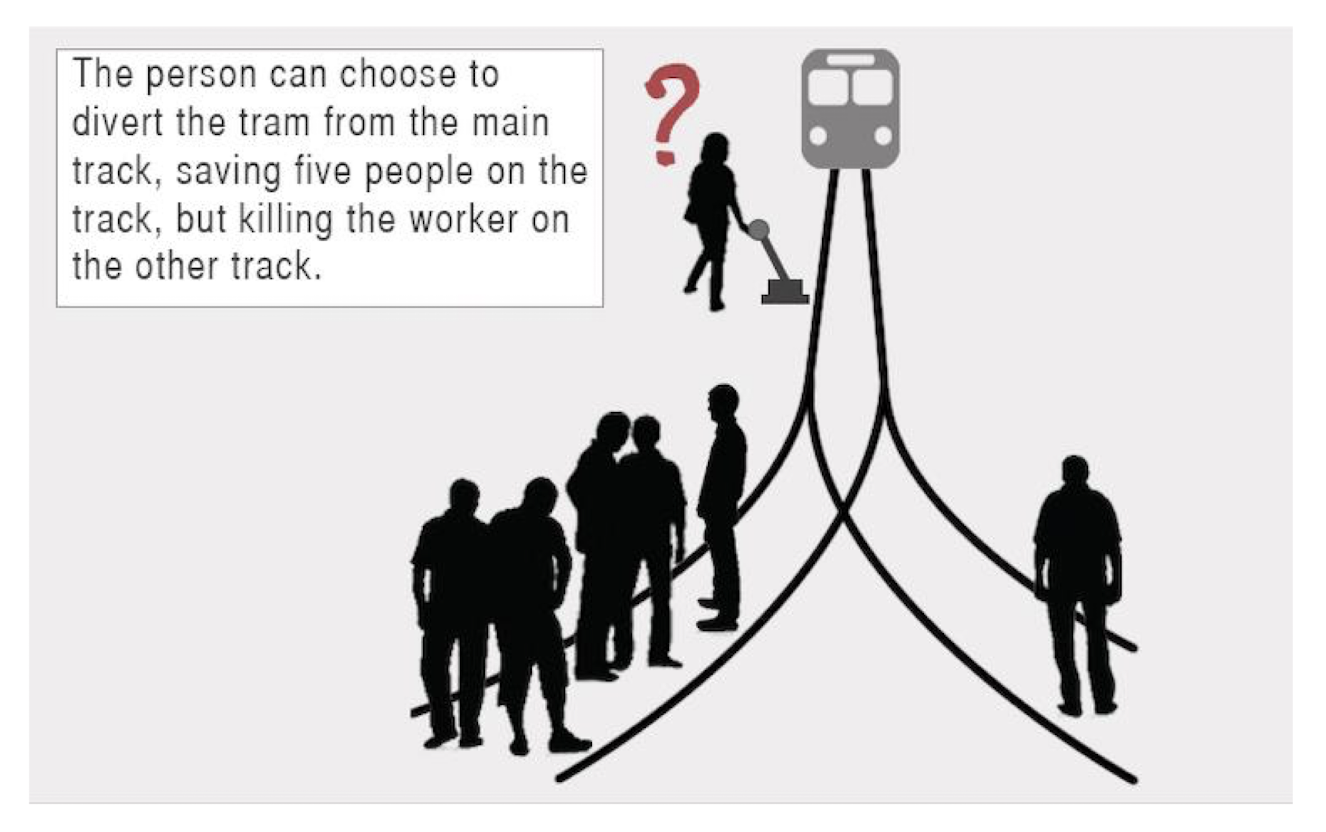
https://theconversation.com/the-trolley-dilemma-would-you-kill-one-person-to-save-five-57111
1.3 A two-year-old’s solution to the trolley problem
https://www.youtube.com/watch?v=-N_RZJUAQY
1.4 The Footbridge Dilemma
To Push or Not To Push?

https://theconversation.com/the-trolley-dilemma-would-you-kill-one-person-to-save-five-57111
1.5 Reasoning from Previous Polling
https://www.youtube.com/watch?v=kBdfcR-8hEY
1.6 What is Ethics?
- Ethics is a branch of philosophy, an academic subject concerned with the fundamental nature of knowledge, reality, and existence.
- Ethics considers people’s values and sources.
- Consider how people and groups translate those values into behavior in different over time and place
- Some values that philosophers consider include justice, equality, and human rights.
- Ethics as “the philosophical study of morality (道德)”
- Ethics is founded in a society’s moral code
- the rules (conventions) by which a society lives (an established consensus)
- but there are conflicts…
- Moral code depends on personal background
- age group, ethnic and cultural background, religion, gender,…
- E.g. “Should I put Grandma into a retirement home?”
- E.g. “Should I buy/manufacture/distribute pirated software?”s
1.7 Where Do Ethics and Values Come From?
- Philosophers called objectivists see the ethics project as identifying the right thing to do or the right action to take morally.
- Divine Command theory (神聖命令理論) proceeds from the assumption that a God who exists provides an objective set of ethical standards and that humans can behave ethically.
- Plato’s Theory of Forms - which suggests that we have an ideal “something” in mind and that we can then compare a particular experience to that ideal.
- A moral relativist believes that there is no one absolute right or wrong position.
- Not everyone will see a moral problem in the same way.
- Ethicists also disagree about whether ethical values change over time.
- Moral relativists argue that as technologies advance, ethical values can change too.
- For example, they argue that many people today enjoy sharing on social media, and therefore, people don’t value privacy the same way they did in the past.
- Objectivists argue that ethical decisions rest on stable core values, regardless of one’s environment
1.8 Definition of Computer Ethics
- Maner’s definition: examines “ethical problems aggravated, transformed or created by computer technology”
- Johnson’s Definition: ethics studies the way in which computers “pose new versions of standard moral problems and moral dilemmas, exacerbating (worsen) the old problems, and forcing us to apply ordinary moral norms in uncharted realms (unexplored area).”
Gotterbarn’s Definition: a branch of professional ethics, concerned primarily with standards of good practice and codes of conduct for computing professionals
Moor’s Definition: a field concerned with “policy vacuums” and “conceptual muddles (confusion)” regarding the social and ethical use of information technology.
- Analysis of the nature and social impact of computer technology and the corresponding formulation and justification of policies for the ethical use of such technology
- independent of any specific philosopher’s theory
- compatible with a wide variety of approaches to ethical problem-solving
- Analysis of the nature and social impact of computer technology and the corresponding formulation and justification of policies for the ethical use of such technology
Bynum’s Definition: identifies and analyzes the impacts of information technology on such social and human values as health, wealth, work, opportunity, freedom, democracy, knowledge, privacy, security, self-fulfillment, etc.
- Employs applied ethics, sociology of computing, technology assessment, computer law, and related fields.
1.9 History of Computer Ethics (1940s - 1970s)
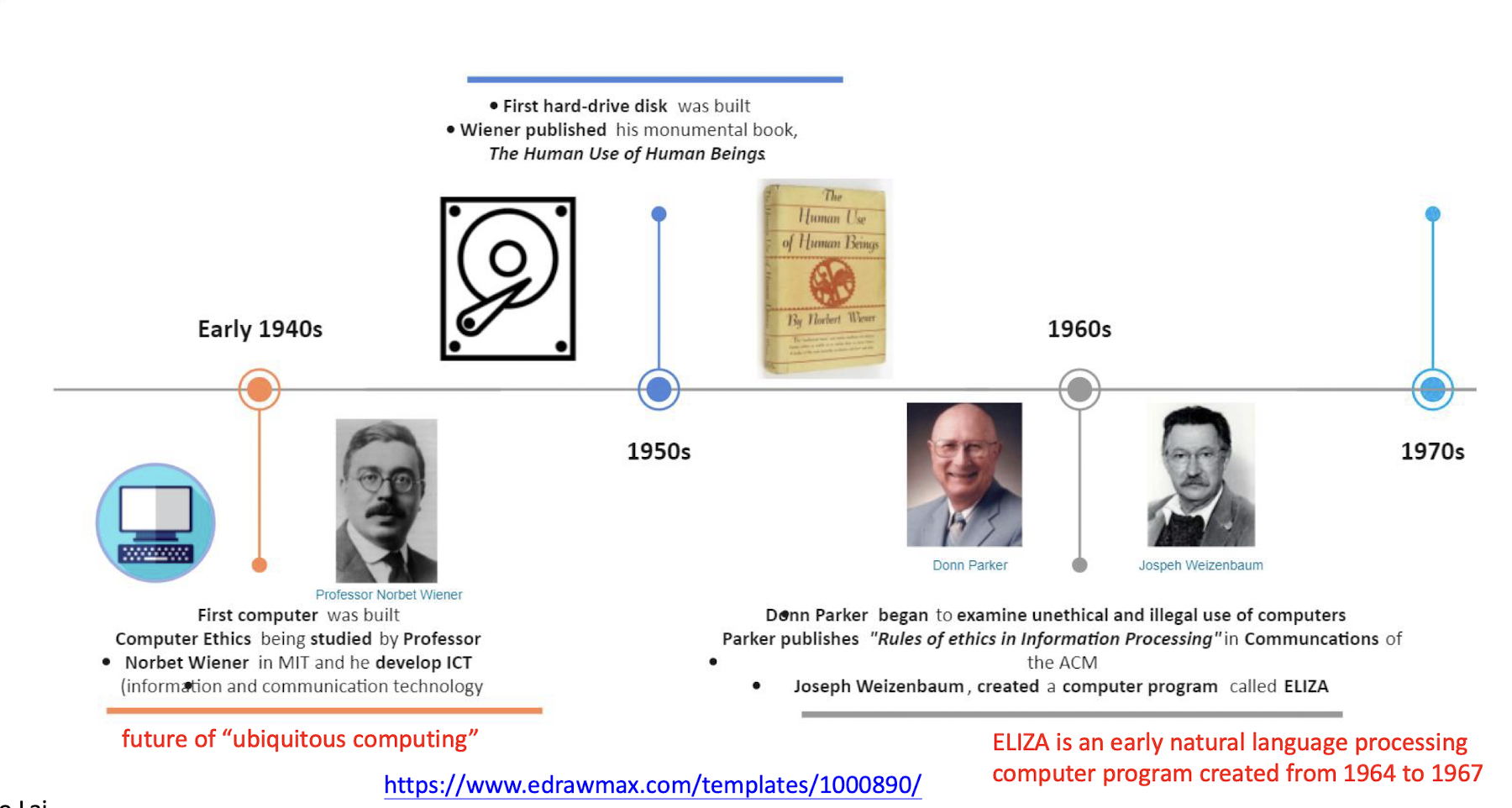
https://www.edrawmax.com/templates/1000890/
History of Computer Ethics (1970s - 1995)
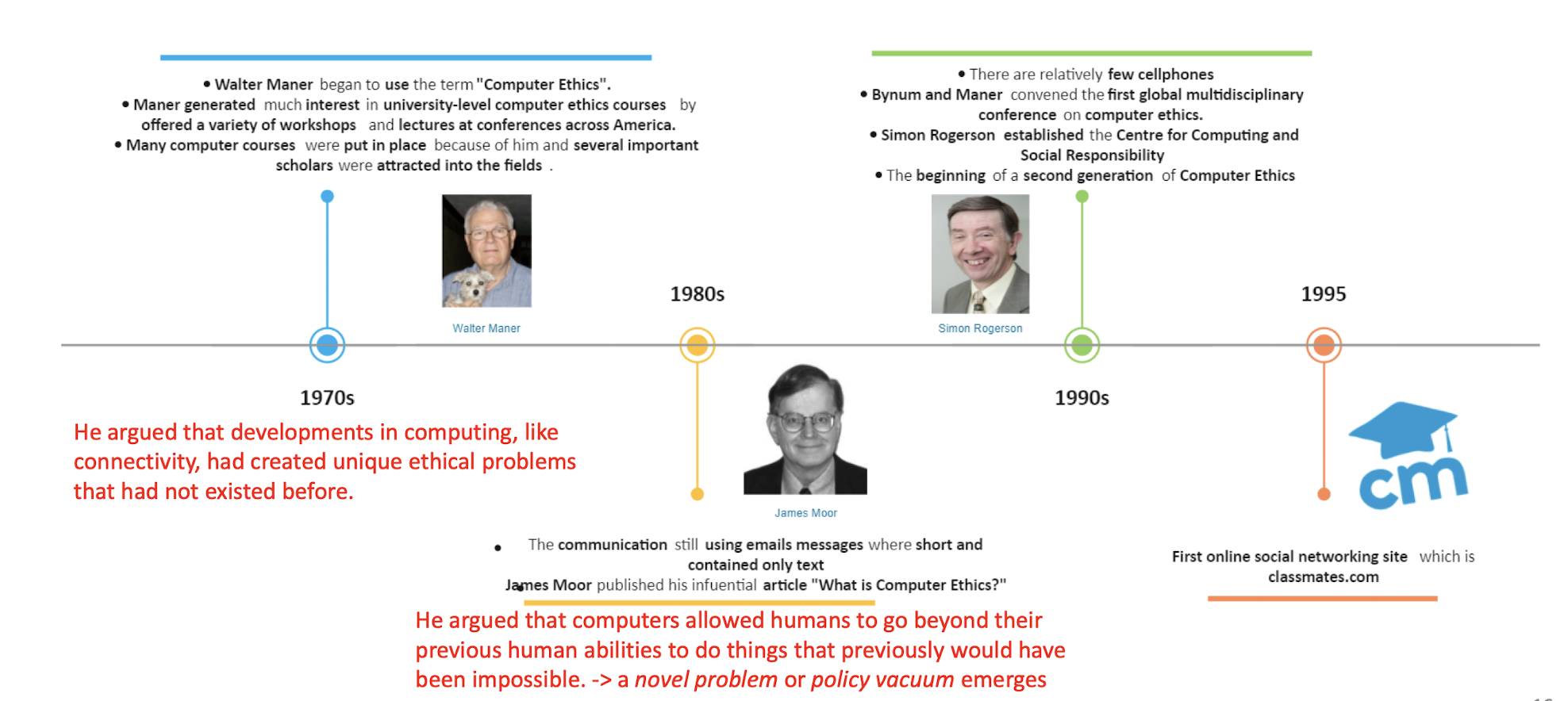
https://www.edrawmax.com/templates/1000890/
History of Computer Ethics (1995 - 2023)
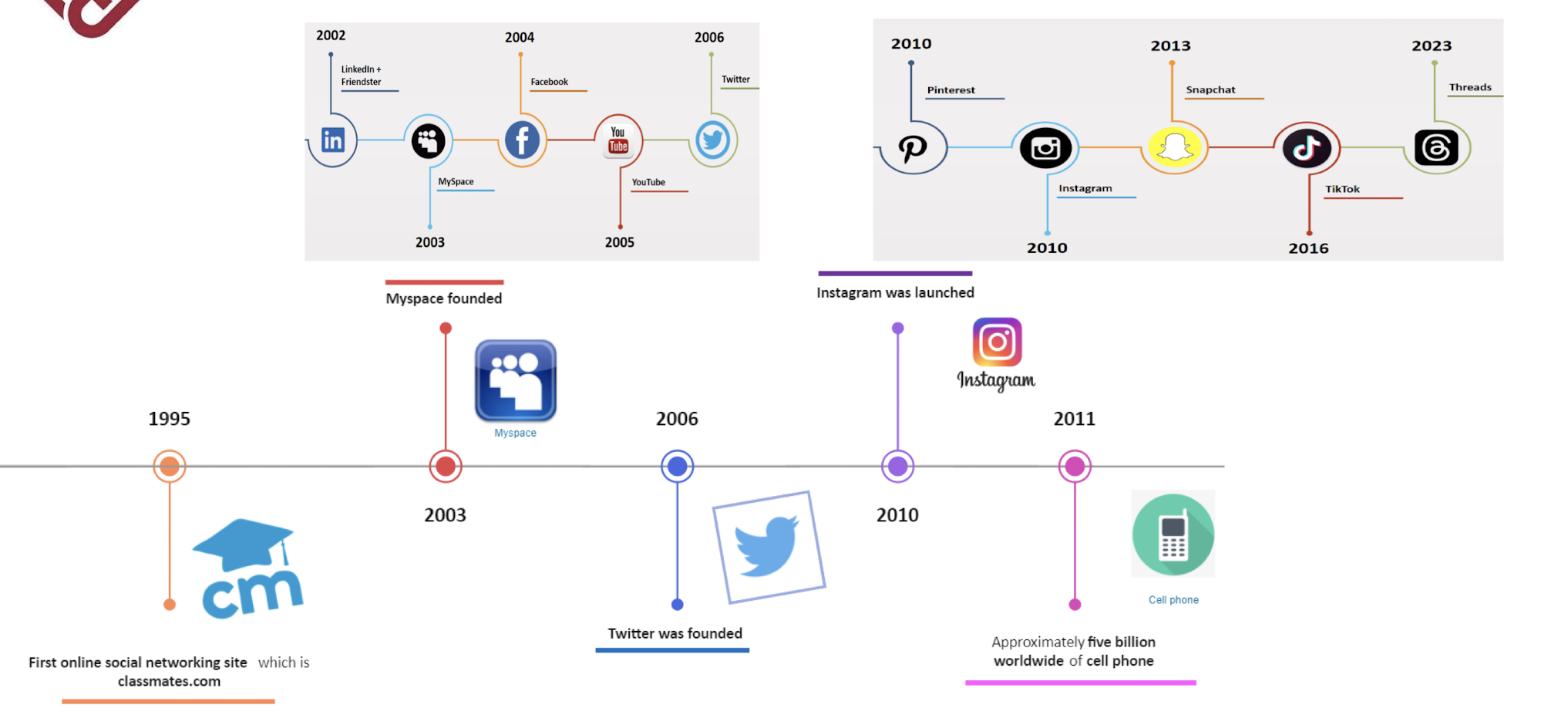
1.10 The Ethics of User-Centered Design
- User-centered design refers to a design process centered explicitly around the needs and experiences of a product’s users.
- User-centered design can be implemented in designing both user interfaces and user experiences.
- The designer might think about those who will use a product - including technology-phobic users, older users, those with a disability involving motor skills, or those who are visually or hearing impaired.
- E.g., someone who uses a phone to call for help after an accident might be frightened and unable to focus quickly
- One of the goals of user-centered design is to identify those who might be marginalized or excluded from using technologies as they exist in their present form.
1.11 Cybersecurity Scenarios Which Present Competing Goals
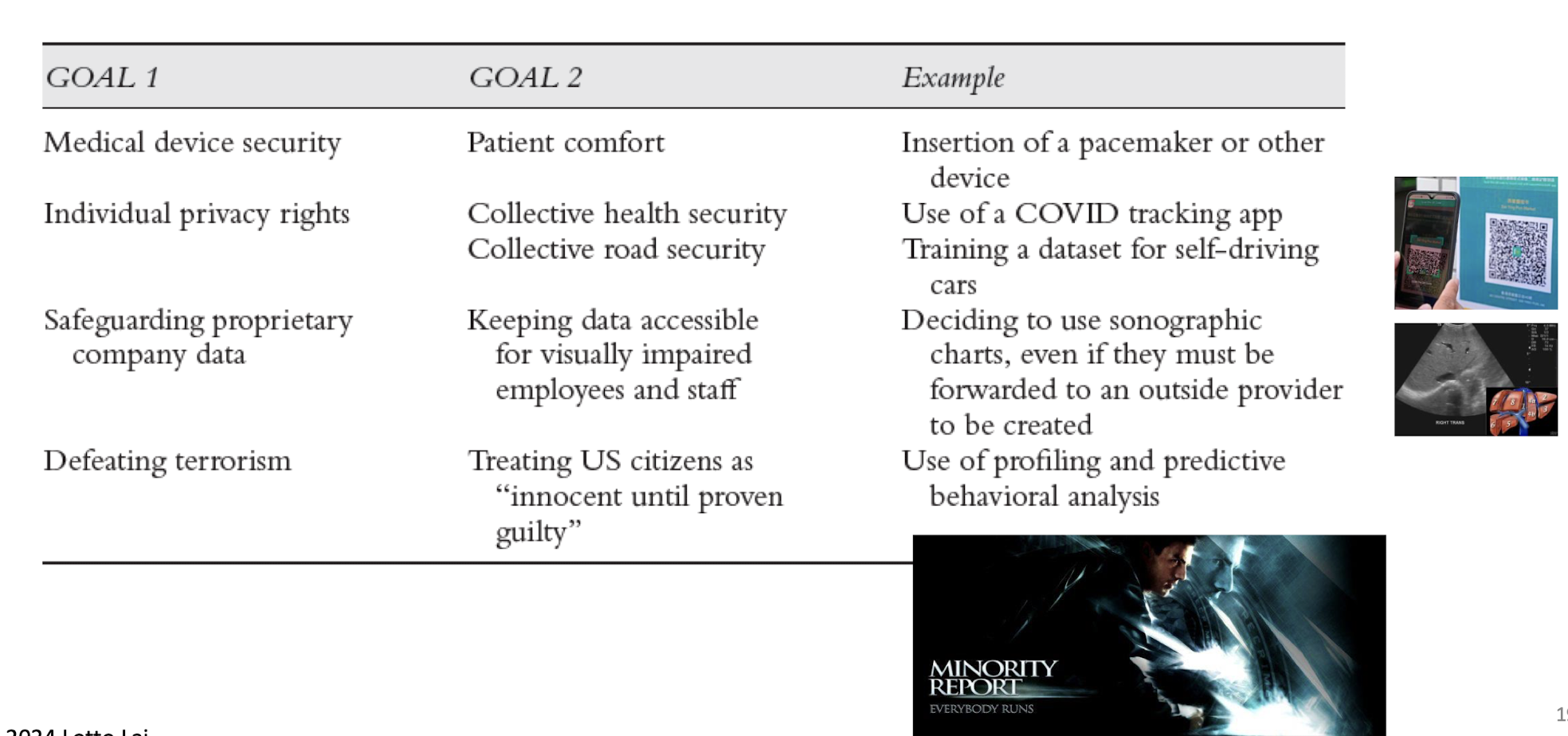
1.12 The Relationship Between Ethics and Religion
- Ethical arguments establish standards of behavior and practice and provide a basis for describing the moral violations of individual or group.
- Ethics requires accountability. Example, who are religious and accountable to God.
- World’s major religions are including Buddhism, Confucianism, Judaism, Islam, and Christianity.
- We can also identify ethics based on the values of a community, including profession such as environmentalist community, military members, etc.
1.13 The Relationship Between Ethics and Law
I obey the laws, you might think, why should I think about ethics?
Unethical information technology use as: the willful violation - by any individual, group, or organization - of privacy and property and access and accuracy - concerning information / information goods resident within or part of an information system, owned / controlled by any other individual group of the organization.
Act as unethical if it breaks the rules or causes harm to others
Conventional morality are often codified into laws.
Whether law precedes ethics or ethics precedes laws appears in current debates about the foundation of ethics in cyberspace (chicken or egg problem).
One difference between a profession and a mere job is that professionals often work independently, without supervision. They need to think critically when the rules are unclear or ambiguous, or when more than one rule applies.
1.14 Compliance with applicable legal requirement
HKSAR Ordinances and Regulations
Safety and Environmental Related Legal Requirement
Security Related Legal Requirement
1.15 Legal Requirement employed in HKSTP
- HKSTP Ordinance Chapter 565
- Employment Ordinance, Chapter 57
- Employees’ Compensation Ordinance, Chapter 282
- Minimum Wage Ordinance, Chapter 608
- Labour Relations Ordinance, Chapter 55
- Immigration Ordinance, Chapter 15 (Part IVB)
- Occupational Safety and Health Council Ordinance, Chapter 411
- Sex Discrimination Ordinance, Chapter 480
- Disability Discrimination Ordinance, Chapter 487
- Family Status Discrimination Ordinance, Chapter 527
- Mandatory Provident Fund Scheme Ordinance, Chapter 485
- Race Discrimination Ordinance, Chapter 602
- Personal Data (Privacy) Ordinance, Chapter 486
1.16 Safety Related Legal Requirement Review
| Cap | Description | |
|---|---|---|
| 51 | Gas Safety Ordinance | |
| 56 | Boilers and Pressure Vessels Ordinance | |
| 95 | Fire Services (Installations and Equipment) Regulations | |
| 123 | Building Ordinance | |
| 132 | Public Health and Municipal Services Ordinance | |
| 133 | Pesticides Ordinance | |
| 282 | Employee’s Compensation Ordinance | |
| 295 | Dangerous Goods Ordinance | |
| 303 | Radiation Ordinance | |
| 314 | Occupier’s Liability Ordinance | |
| 360 | Pneumoconiosis (Compensation) Ordinance | |
| 371 | Smoking (Public Health) Ordinance | |
| 406 | Electricity Ordinance | |
| 469 | Occupational Deafness (Compensation) Ordinance | |
| 470 | Builders’ Lift and Tower Working Platforms (Safety) Ordinance | |
| 502 | Fire Safety (Commercial Premises) Ordinance | |
| 572 | Fire Safety (Buildings) Ordinance | |
| 595 | Hazardous Chemical Control Ordinance | |
| 618 | Lifts & Escalators (General) Ordinance | |
| 354C | Waste Disposal (Chemical Waste) General Regulation | |
| 354O | Waste Disposal (Clinical Waste) General Regulation | |
| 509A | Occupational Safety and Health (OSH) Regulation | |
| 509A | Manual Handling Operations | |
| 509B | OSH (Display Screen Equipment(DSE)) Regulation | |
| 59AA | F&IU (Carcinogenic Substances) Regulations | |
| 59AB | F&IU (Dangerous Substances) Regulations | |
| 59AE | F&IU (Confined Spaces) Regulations | |
| 59AF | F&IU (Safety Management) Regulations | |
| 59D | F&IU (First Aid in Notifiable Workplaces) Regulations | |
| 59S | F&IU (Protections of Eyes) Regulation | |
| 59T | F&IU (Noise at Work) Regulation | |
| 59V | F&IU (Fire Precautions in Notifiable Workplaces) Regulations | |
| 59W | F&IU (Electricity) Regulations | |
| 59Z | F&IU (Safety Officers and Safety Supervisors) Regulations | |
| Code of Practice on Safety Management | ||
| Code of Practice on Prevention of Legionnaires’ Disease |
1.17 Environmental Related Legal Requirement Review
| Cap | Air Quality | |
|---|---|---|
| 311 | Air Pollution Control Ordinance | |
| 403 | Ozone Layer Protection Ordinance | |
| 374 | Road Traffic Ordinance | |
| 611 | Motor Vehicle Idling (Fixed Penalty) Ordinance | |
| Noise Emissions | ||
| 400 | Noise Control Ordinance | |
| 374A | Road Traffic Ordinance Road Traffic (Construction and Maintenance of Vehicles) Regulation | |
| Waste Management | ||
| 354 | Waste Disposal Ordinance | |
| Wastewater Discharge | ||
| 358 | Water Pollution Control Ordinance | |
| 463 | Sewage Services Ordinance | |
| Dangerous Goods/Materials Storage | ||
| 295 | Dangerous Goods Ordinance (DGO) |
| Cap | Miscellaneous |
|---|---|
| 132 | Public Health and Municipal Services Ordinance |
| 133 | Pesticides Ordinance |
| 207 | Plant (Importation and Pest Control) Ordinance |
| 95 | Fire Services Ordinance |
| 502 | Fire Safety (Commercial Premises) Ordinance |
| 371 | Smoking (Public Health) Ordinance |
| 610 | Buildings Energy Efficiency Ordinance |
| 303 | Radiation Ordinance |
| 51 | Gas Safety Ordinance |
Other Requirements
- A Concise Guide to the Ozone Layer Protection Ordinance
- Code of Practice on the Packaging, Labeling and Storage of Chemical Wastes
- Safe and proper use of pesticides
- EPD Practice Notes for Professional Persons
- Air Conditioning Refrigerants - A Time for Change (PN 4 / 94 )
- Code of Practice for the Management of Clinical Waste - Small Clinical Waste Producers
Security Related Legal Requirement Review
| Cap | Ordinance / Regulation | Compliance (Y/N) |
|---|---|---|
| 43 | Trade Marks Ordinance | Y |
| 60 | Import and Export Ordinance | Y |
| 106 | Telecommunications Ordinance | Y |
| 200 | Crimes Ordinance | Y |
| 210 | Theft Ordinance | Y |
| 445 | Layout-Design (Topography) of Integrated Circuits Ordinance | Y |
| 486 | Personal Data (Privacy) Ordinance | Y |
| 514 | Patents Ordinance | Y |
| 522 | Registered Designs Ordinance | Y |
| 528 | Copyright Ordinance | Y |
| 544 | Prevention of Copyright Piracy Ordinance | Y |
| 553 | Electronic Transactions Ordinance | Y |
| 559 | Trade Marks Ordinance | Y |
| 568 | Copyright (Suspension of Amendments) Ordinance | Y |
| 593 | Unsolicited Electronic Messages Ordinance | Y |
1.18 HKSTP compliance documentation
For external use (on website)
- Complaints Management Policy
- Corporate Governance Report
- A Guide to Handle Corporate Governance Matters For Board of Directors and Senior Management
- Whistleblowing Policy
For internal use (staff only)
- Corporate Compliance Division - Operation Procedure Manual
- Corporate Compliance Charter
- Whistleblowing Policy
- Risk Management Policy
- Risk Management Procedures
- Complaints Management Policy and Procedures
- Internal Audit Process
1.19 What is Computer Related Crime?
The use of computer, the Internet and telecommunication or information devices has brought us much convenience in all kinds of our daily pursuits, from learning, leisure, personal communication to conducting business activities. However, at the same time, the convenience of this virtual space has created a great potential for abuse by criminals.
Computer crime or computer related crime or technology crime, are descriptions commonly used interchangeably to refer to any illegal act committed by application of computer technologies or usage of such technologies as a means in the commission of the offence.
Computer crime can be categorized as follows:
- crime that is directly targeted at the computer or computer system e.g. hacking into a server or defacing a web page
- crime that uses the Internet e.g. Internet gambling or pornography
- crime that involves the retrieval of digital data of evidential value e.g. fraud-data storage or payment records
https://www.infosec.gov.hk/en/knowledge-centre/computer-related-crime
1.20 Number of Computer Crime Cases and Financial Losses in Hong Kong
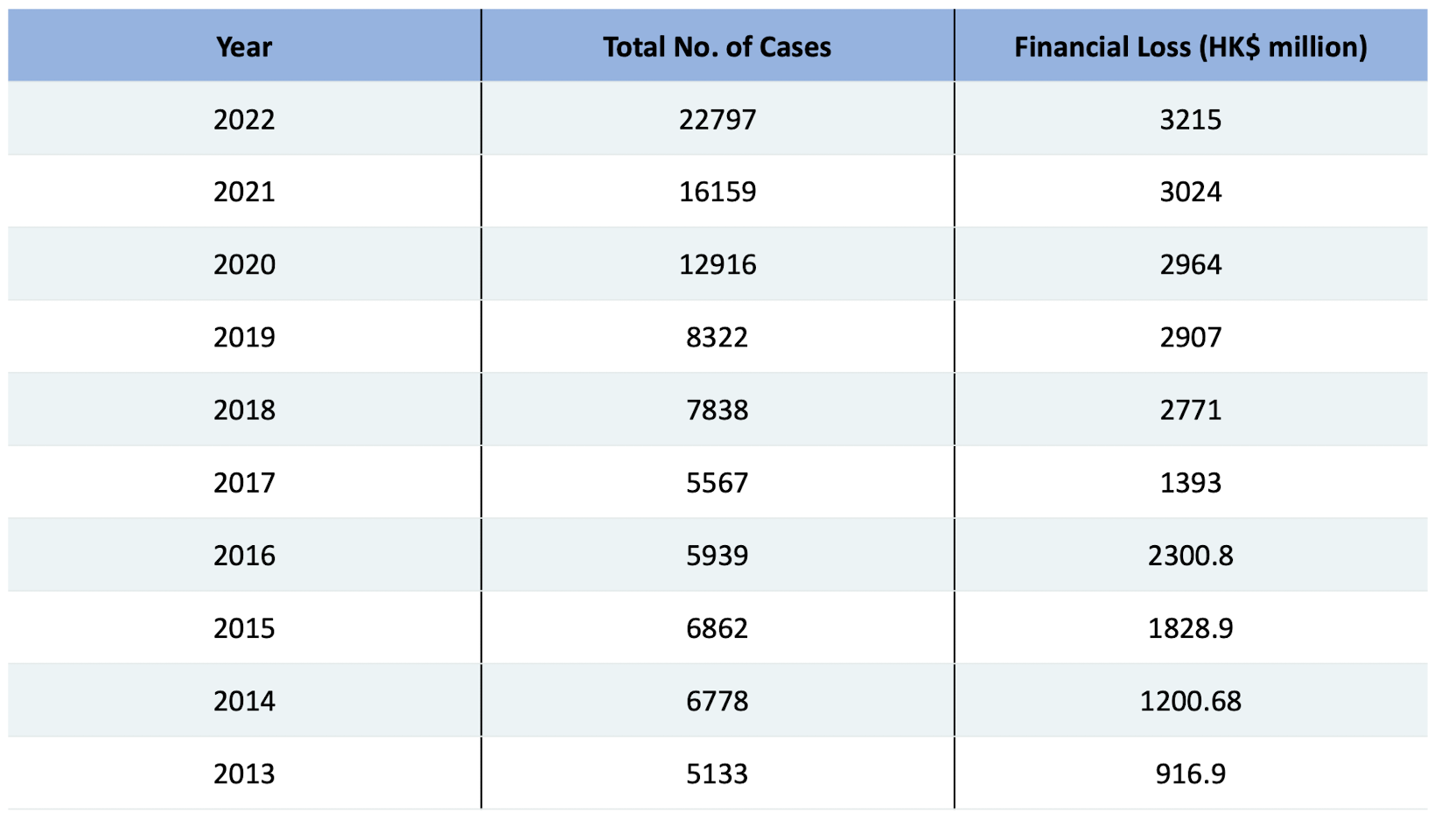
https://www.infosec.gov.hk/en/knowledge-centre/computer-related-crime
1.21 Types of Computer Related Crimes

https://cyberdefender.hk/en-us/theft_of_identity/
1.22 Man-in-the-middle Attack
- A man-in-the-middle attack refers to an attack in which attacker monitors the communication between the sender and the receiver, and secretly intercepts, modifies and manipulates the content without victims being aware of it during data transmission on the Internet. Ways of attack include IP spoofing, Domain Name Server (DNS) spoofing, Address Resolution Protocol (ARP) spoofing, email phishing, Secure Sockets Layer (SSL) stripping and Wi-Fi eavesdropping.

https://cyberdefender.hk/en-us/mitm/
1.23 Advanced Persistent Threat (APT) Attack
An APT is a common cyberattack which is accurately planned against specific organizations or targets in multiple directions.
This penetration attack starts by collecting intelligence, in which the attacker comes to grips with the target’s information system structure, and then hide and monitor the target in order to steal the target’s confidential information step by step.

Safety precautions for enterprises:
- Install reputable information security software, conduct system update and scanning regularly
- Deploy a multi-layer information security defense mechanism
- Restrict and manage internal sensitive data to establish monitoring and access policies
- Back up the data of the company regularly and do not connect the backup data to computers
- Control and manage employees’ use of applications on company devices
- Educate employees about information security
https://cyberdefender.hk/en-us/apt_attack/
1.24 Internet of Things (IoT) Attack
- The Internet of Things is a system of mobile devices or household equipment connected together by the Internet and is able to transfer and handle data and information in order to make command and take control over designated devices or equipment. As long as the devices (such as the commonly used smart phones or tablets, and recently, even vehicles, light bulbs and refrigerators) are equipped with Internet functions, they are part of the IoT.

https://cyberdefender.hk/en-us/iot_attack/
1.25 Distributed Denial of Service (DDoS) Attack
- Distributed denial of service attack (DDoS) evolves from the traditional denial of service attack (DoS). Hackers utilize multiple infected computer systems (i.e. Botnet) to generate huge volumes of traffic, overloading the target servers or exhausting all available server resources, resulting in server crash and disruption of service. It is like an unexpected traffic jam clogging up the highway, preventing regular traffic from arriving at its destination.
https://cyberdefender.hk/en-us/ddos/
1.26 Ransomware Attack
Ransomware is a malware that prevents or restricts users from accessing computer systems. Hackers will infect and intrude into target computer systems via emails, websites or malicious advertisements.
With ransomware installed on computers or other devices within the network, certain files such as document files, spreadsheets, digital photos, etc. will be encrypted and become inaccessible to the users.
A message will then appear on victims’ computers, demanding ransom payments in Bitcoin in exchange for the decryption key.
https://cyberdefender.hk/en-us/ransomware/
1.27 Phishing Attack
Phishing attack is a widespread cybercrime. Hackers send phishing emails or text messages impersonating organizations such as the government, banks, online payment service providers, online retailers or business partners, with links or QR codes directing to phishing websites which look like the genuine websites of relevant organizations, tricking the recipients into inputting login passwords, personal information , credit card details , etc.
Hackers may also attach links, QR codes or files in the messages, if the recipients click on the links or open attachments indiscriminately, their devices may be infected by malware.
https://cyberdefender.hk/en-us/phishing_attack/
1.28 Hong Kong Cyber Security Threat Landscape (Dec 2022 to Nov 2023)
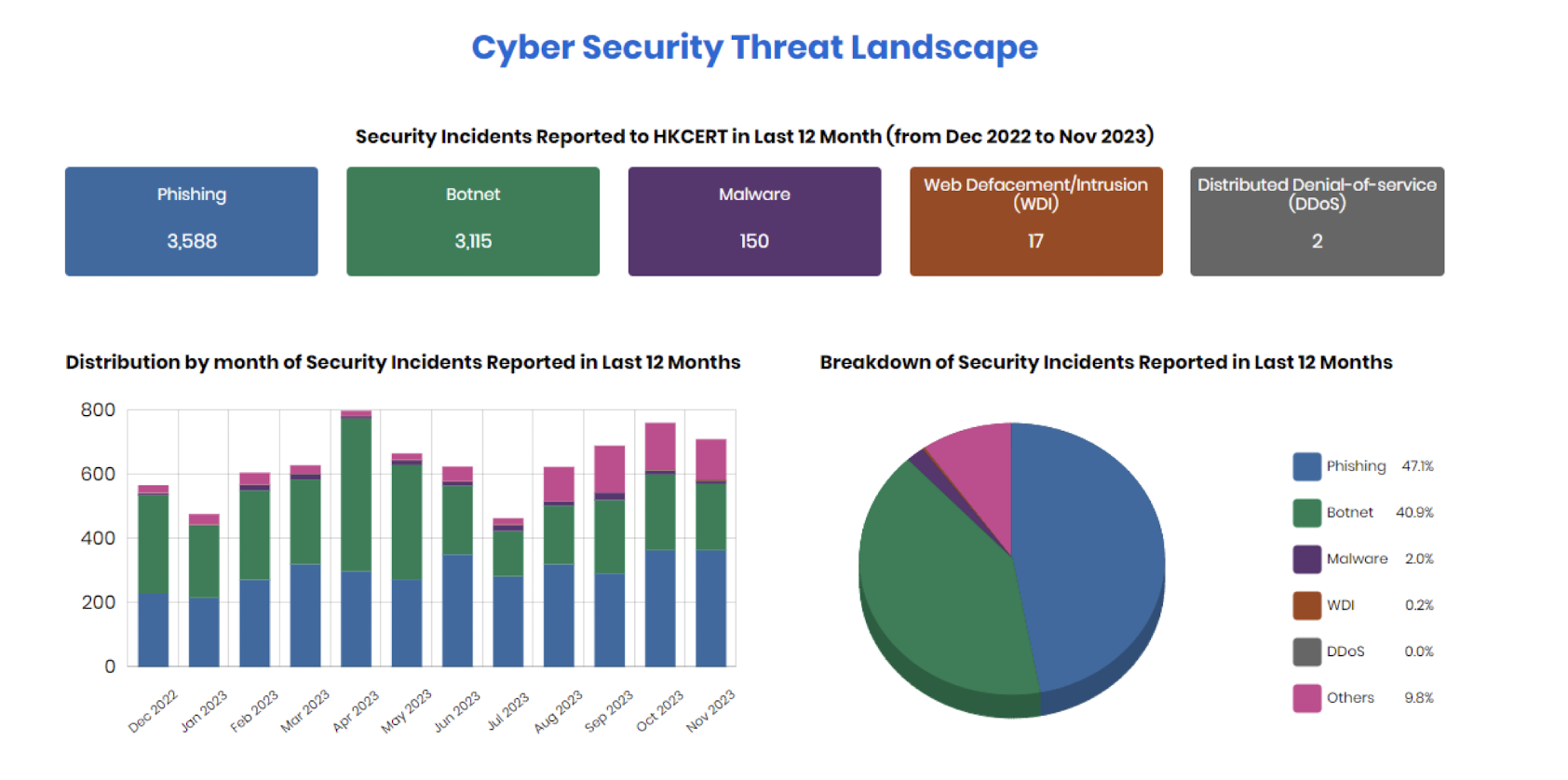
1.29 Computer Related Crime Impacts
In the information age, the use of computers or information systems is applied nearly everywhere in our modern society.
It includes critical infrastructures such as power supply systems, fresh water supply systems, public transportation, communications networks, etc., to all kinds of business operations.
Criminal damages to these systems create much greater impact than that of conventional criminal attacks.
- Loss of data and information
- Damage of IT resources
- Time wasting in reading, checking, verifying ( e.g. hoax/cheat) and re-setting the system
- Wasting bandwidth
- Unavailability of service
- Unauthorized use or misuse of computer systems
- Loss of customer trust
- Loss of public confidence
- Disruption of Production
- Financial Loss
- Reputation of Companies
1.30 Security Incident Cases in Hong Kong
Focus: Protect Your WhatsApp Account & Be Cautious Of Scams Targeting Hong Kong WhatsApp Users (Q3 2023)
Recently, there have been a series of scams in Hong Kong involving the theft of WhatsApp accounts , posing a serious threat to the public’s personal privacy and information security. In order to protect the interests of citizens, the Hong Kong Computer Emergency Response Team Coordination Centre (HKCERT) specifically advises everyone to strengthen the protection of their WhatsApp accounts. The following will introduce the operation methods of these scams and provide some preventive measures to help citizens increase their awareness and protect their personal information.
The purpose of these scammers is mainly financial gain. They use social engineering and technical means to deceive victims into scanning the QR codes of fake WhatsApp websites ( phishing websites ) or stealing the one-time verification codes (OTP) of victims’ accounts, thus gaining control of their WhatsApp accounts. Once they have control of the account, scammers can impersonate the victim and send fraudulent messages to their contacts, and even further deceive others.
https://www.hkcert.org/watch-report/hong-kong-security-watch-report-q3-2023
Sensitive data, including employee details and credit card records , from a Hong Kong technology park that describes itself as a “digital technology flagship” have been leaked online, the company said.
Cyberport said in a statement released on Tuesday it had been the victim of a “malicious intrusion” in mid-August and found information related to the hack “on the dark web”.
The data included “names and contact details of individuals, human-resources related data of employees, ex-employees and job applicants, and a small number of credit card records” , it said.
Operating since 2004, Cyberport described itself as a “digital technology flagship and incubator for entrepreneurship” and said it has more than 800 start-ups and technology firms at its site in southern Hong Kong island.
The hack was not disclosed until September 6, nearly three weeks after Cyberport notified Hong Kong’s privacy watchdog, leading lawmakers and experts to question the delay.
“We decided not to disclose the incident externally to avoid any unnecessary concern,” it said, adding that it did not initially know the extent of the damage.
“As the victim of a malicious intrusion, Cyberport condemns all form of cybercrime and will fully cooperate with law enforcement.”
The hack has been linked to ransomware Trigona after a website bearing its logo posted 438 gigabytes of Cyberport files.
“We decided not to disclose the incident externally to avoid any unnecessary concern,” it said, adding that it did not initially know the extent of the damage.
A spreadsheet seen by AFP listed the birthdays, addresses, ID card numbers, salaries and computer passwords of 166 current and former employees, including six executives.
Other files included information about company finances, business plans, government dealings and legal correspondence.
https://hongkongfp.com/2023/09/13/hong-kong-tech-park-says-data-exposed-by-malicious-hack/
15:30, 13 SEPTEMBER 2023
Hong Kong’s consumer watchdog has fallen victim to hackers and has warned the public of a suspected data breach, just two weeks after it emerged that Cyberport tech hub suffered a data leak.
The Consumer Council said on Friday that a cyberattack against its computer system had been identified on Wednesday, causing damage to about 80 per cent of their systems and disruption to their hotline services and price comparison tools. Whether a personal data breach was involved , and the scope of the data leak, remains to be confirmed.
Sensitive data including the HKID numbers of current and former staff, and their family members, and credit card information for around 8,000 subscribers of the council’s monthly CHOICE magazine, are potentially at risk, the council said at a Friday press briefing. Job applicants may also be victims, they added.
The case has been referred to the police and reported to the Privacy Commissioner’s Office, a statutory body that ensures the protection of personal data. The Office said on Thursday that it was looking into the incident, as it appealed to possibly affected individuals to remain vigilant against the theft of their data.
A ransomware note claimed to have obtained employee and client data during the attack, Chan said. It had demanded US$500,000 (HK$3.9 million) be paid by Saturday night, and up to US$700,000 (HK$5.5 million) if the deadline was not met.
The leak came just two weeks after Cyberport revealed news of a data breach in August that led to sensitive personal information of staff being uploaded to the “dark web.”
1.31 OGCIO Press Release
- The Government is very concerned about the recent incidents of unauthorised access into computer systems of individual public organisations by hackers. These incidents suggest that cybersecurity threats are increasingly commonplace. All sectors of society must take effective measures to safeguard their systems and enhance security of the networks and data.
The cybersecurity incident at Cyberport in August 2023 was caused by ransomware. Meanwhile, the computer system of the Consumer Council (the Council) was similarly attacked by hackers with ransomware in end-September 2023.
With regards to the security of information systems and cyberspace, the Government has devised and implemented on an ongoing basis a multi-layered system covering assessment, monitoring, risk management and contingency.
Besides, the Critical Infrastructure Security Coordination Centre (CISCC) of the Police is committed to strengthening the protection and resilience of critical infrastructure through public-private partnership, risk management and on-site security inspections, etc.
the Government has been promoting some strengthen capability of relevant practitioners on cybersecurity protection measures.
https://www.ogcio.gov.hk/en/news/press_releases/2023/11/pr_20231122.html
2 Ethical Management and Analysis
2.1 Eight Moral Theories
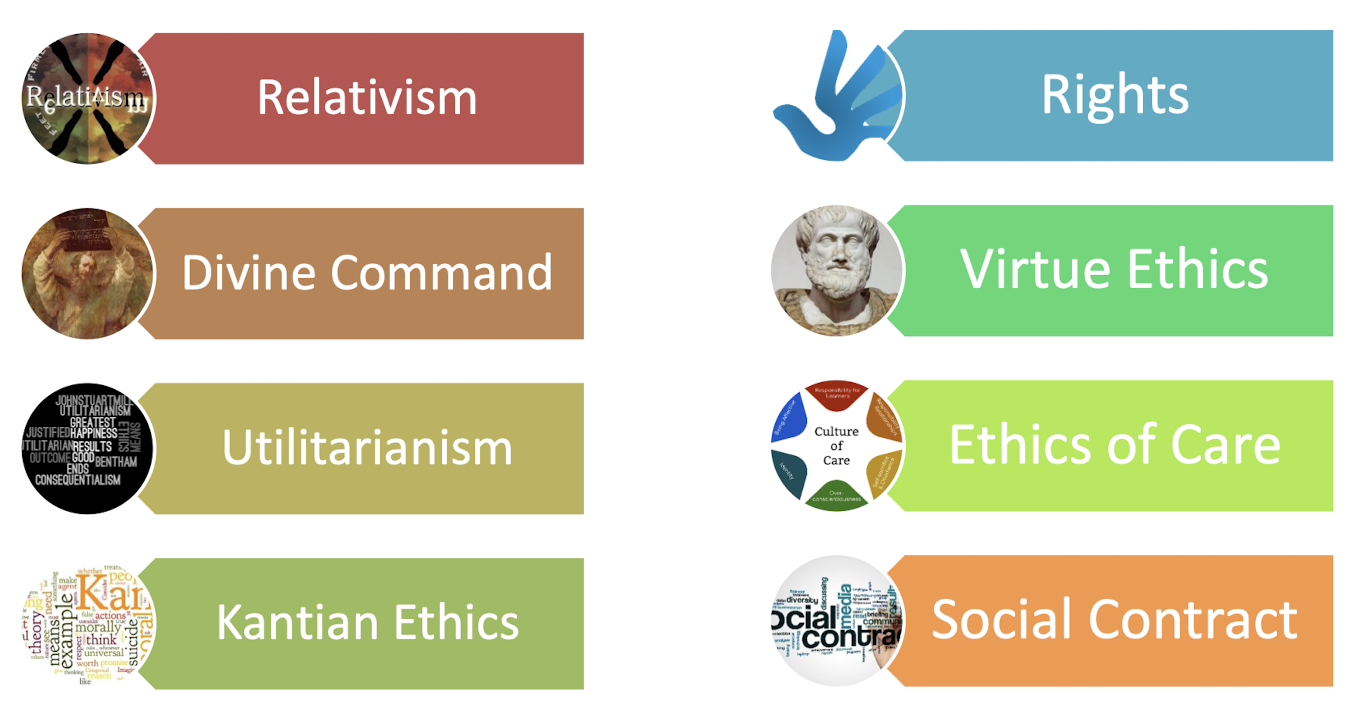
https://www.gvsu.edu/cms4/asset/CE2B2300-A796-67AD-C1B5A6B62C598E40/concise_guidetoethics.doc
2.1.1 Relativism
相對主義
Descriptive Ethical Relativism (敘述倫理相對主義) claims that as a matter of fact and observation different cultures DO have different values.
Normative Ethical Relativism (規範倫理相對主義) claims that each culture’s values, however different, are right for THAT culture.
In other words that the moral rightness and wrongness of actions varies from society to society and that there are no absolute universal moral standards binding on all men at all times.
| Not considered to be Immoral by many in USA | Considered to be Immoral by many in |
|---|---|
| Eating Beef | India |
| Drinking alcohol, Gambling | Middle Eastern Islamic Countries |
| Women in school or business | Afghanistan |
| Women wearing shorts, face uncovered | Iran, Saudi Arabia, Sudan |
2.1.2 Divine Command
( 神聖命令 )
- Most often championed within cultures that have a strong monotheistic tradition (一神論傳統), there are a couple of versions of Divine Command.
- There are those who would claim that all genuine morality is whatever God commands - something is right because God commands it.
- Others would maintain that ethics has its grounding in something other than God (usually Reason ), but that in cases where conflicts arise God’s will always overrides ‘normal’ ethics.
- God’s will is usually known through sacred texts or prophets and teachers or directly through conscience.
2.1.3 Utilitarianism
( 功利主義 )
While it takes many forms, the most basic formulation of utilitarianism is that one should always act so to maximize the greatest good for the greatest number.
Utilitarians are interested in consequences , and look at consequences to judge whether an act was good or bad, right or wrong.
The “good” for Utilitarians may be pleasure, happiness, justice, individual preferences, or a host of other options (including, in business terms, profit ).
Utilitarians look at the consequences of acts, rules, motives, and practices depending upon what kind of Utilitarians they are.
2.1.4 Kantian Ethics
( 康德倫理)
Immanuel Kant, a German philosopher who many consider the most influential philosopher of all, at least next to Plato.
Kant was concerned with duty and motivation - an act’s moral worth depends upon the real reason for which it was done.
What we can know of morality comes from Reason , and what we can do morally is tied to knowing our duty and doing it for its own sake (纯粹为此而已).
We do what is right because it is the right thing to do , and for no other reason.
Kant universalized his concerns in his well-known categorical imperative (定言令式/絕對命令), which states that we should “ always act in such a way that you can will that the maxim (principle) behind your action can be willed as universal law. “
In other words, before you can excuse your (mis)behavior you should be sure to understand that you’d be willing to excuse similar behavior in others under the same conditions. (No double standard!)
2.1.5 Rights
( 權利 )
Rights theories get inordinately complex but essentially say that how we treat others is a matter of the legitimate claims (合法主張) they can make on us as persons who have certain rights , either inalienable (unable to be taken away from) or granted them by law.
Negative rights are those that obligate us from interfering with the rights-holder. Examples are the rights to life, liberty, expression, pursing happiness, etc.
Positive rights are those that obligate us to do something on behalf of the rights-holder. Examples would be provision of basic food and shelter, education, fair treatment under the law, basic health care, etc.
2.1.6 Virtue Ethics
( 美德倫理 )
Virtue Ethics is very much back in favor among ethicists and policymakers.
It is associated with Aristotle, as well as Catholicism, Buddhism, and other religious traditions.
It puts the emphasis not so much on what a person does in any given moral dilemma, but more on the lifelong development of a person’s character , on who that person will be.
Virtue Ethics is interested in looking at what the virtuous life consists of, and how best to implant in people those virtues that will allow them to have good live, live in which their communities prosper.
One of the insights of Virtue Ethics is that it does a society or business little benefit to have good laws, rules, and policies in place if there aren’t wise, compassionate, and judicious people around to apply and administer them.
2.1.7 Ethics of Care ( 關懷倫理 )
This notion of ethics has only recently been formalized and categorized, and it comes out of feminist philosophy and literature.
The idea here is that ethics, primarily, is and ought to be about caring for others , about understanding and relieving their pain and suffering.
That ethics is finally about the quality of the relationships we have, not about some impartial or universal principles.
https://www.cambridgescholars.com/product/978-1-5275-6508-1
2.1.8 Social Contract
( 社會契約 )
- The view that moral and political beliefs and responsibilities are dependent upon a contract or agreement (implicit as well as explicit) between persons who see that a community or state can only be formed and maintained that way.
https://www.youtube.com/watch?v=UY3aMtMkoEU&t=25s
2.2 Ethical Framework
Three models of decision-making - virtue ethics ( 美德倫理 ) , utilitarian ethics ( 功利主義倫理 ) , and deontological ethics ( 義務倫理 ). (where Deontology is a universal ethical theory that considers whether an action itself is right or wrong .)
Some questions about cybersecurity
- Should you send spam e-mails, and what is the consequence?
- Should you engage in cyberwarfare against your own country on behalf of another country paying for your expertise?
- How should you treat potentially embarrassing or incriminating information you find about an employee while monitoring a computer system?
2.2.1 Three Ethical Model

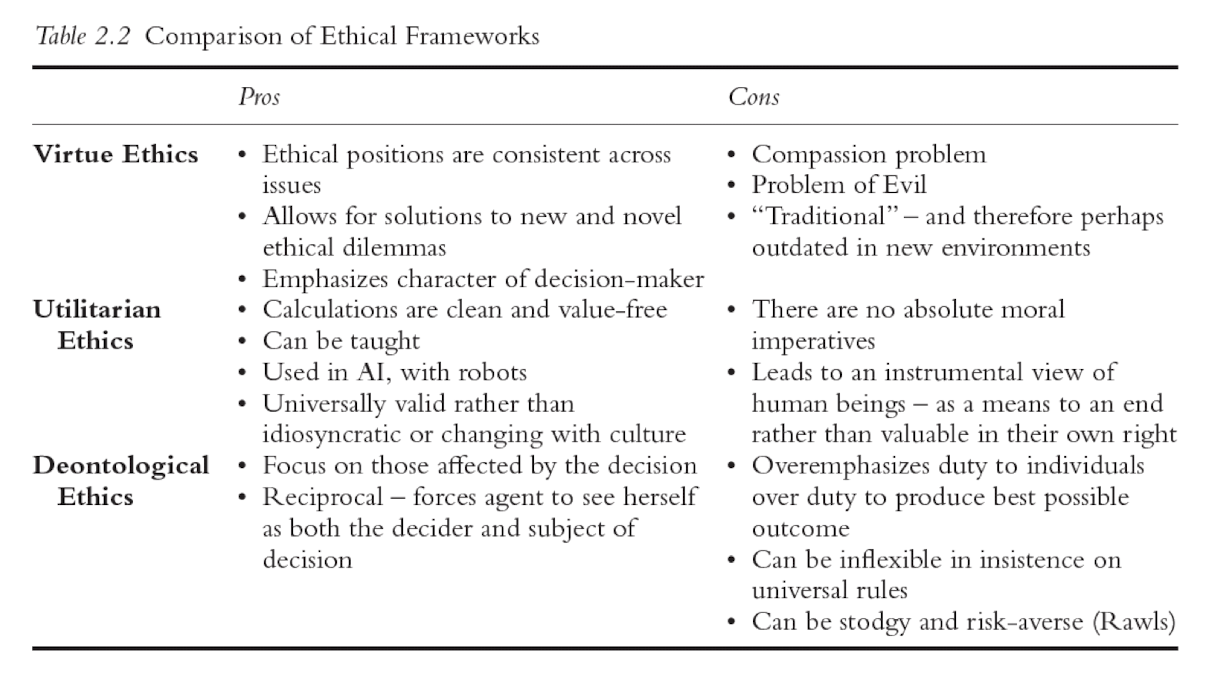
2.2.1.1 Virtue Ethics ( 美德倫理 )
In Aristotle’s view, an ethical individual is someone who does and feels “the right things at the right time in the right way and for the right reasons”
Virtue ethics’ emphasis on intent.
Virtue ethics is also instrumental in framing a professional ethic and building professionalism.
12 “ techno-moral virtues “ identified as “honesty, self-control, humility, justice, courage, empathy, care, civility, flexibility, perspective, magnanimity, and wisdom.”
Virtue ethics often form the basis of a professional code of ethics.
What characteristics, values, and habits should a member of my profession cultivate and represent?”
2.2.1.2 Utilitarian Ethics ( 功利主義倫理 )
Utilitarianism is sometimes referred to as a teleological or consequentialist theory (目的論或結果論) since it is concerned with the endpoint or the decision’s consequences rather than the decision-maker’s attitude or intent.
The ideas of Jeremy Bentham (1748-1832), an eighteenth-century British social reformer. John Stuart Mill (1806-1873) built upon Bentham’s ideas, called “Utilitarianism.”
“Utilitarian calculus” refers to a process of decision-making in which individuals weigh the possible costs and benefits associated with a particular choice
Pros and Cons of Utilitarian Ethics
Utilitarian ethics could be programmed into self-driving autonomous vehicles (AV) driving programs.
They argue that it is possible to create “ moral algorithms that align with human moral attitudes “ (Bonnefon et al., 2016).
But such practical approach might prescribe that seem morally or ethically troublesome. (like Trolley Problem)
In applying utilitarianism in computer ethics, we again encounter the uniqueness debate.
2.2.1.3 Deontological Ethics ( 義務倫理 )
Immanuel Kant (1724-1804) was a German philosopher who believed humans have a privileged place in the universe due to their ability to reason. (the father of deontological ethics)
Kantian ethics is also called deontological or ethics of duty or obligation.
A deontological approach deems an action moral or ethical if the duty has been complied with. (simply the right thing to do)
It suggests that everyone should define and agree to adhere to the same set of standards.
The second principle of Kantian ethics is the notion of reversibility , or the Golden Rule. (“Would I be harmed if someone took the same action against me?)
Trust is a fundamental component of ethics. Many Chinese people saw the Golden Rule as similar to a principle that exists in Confucian ethics
Many critiques such that universal duties in all situations are too idealistic and ultimately unachievable.
2.2.2 Comparison Summary of Three Frameworks
2.2.3 Three Models Thinking about Computer Ethics
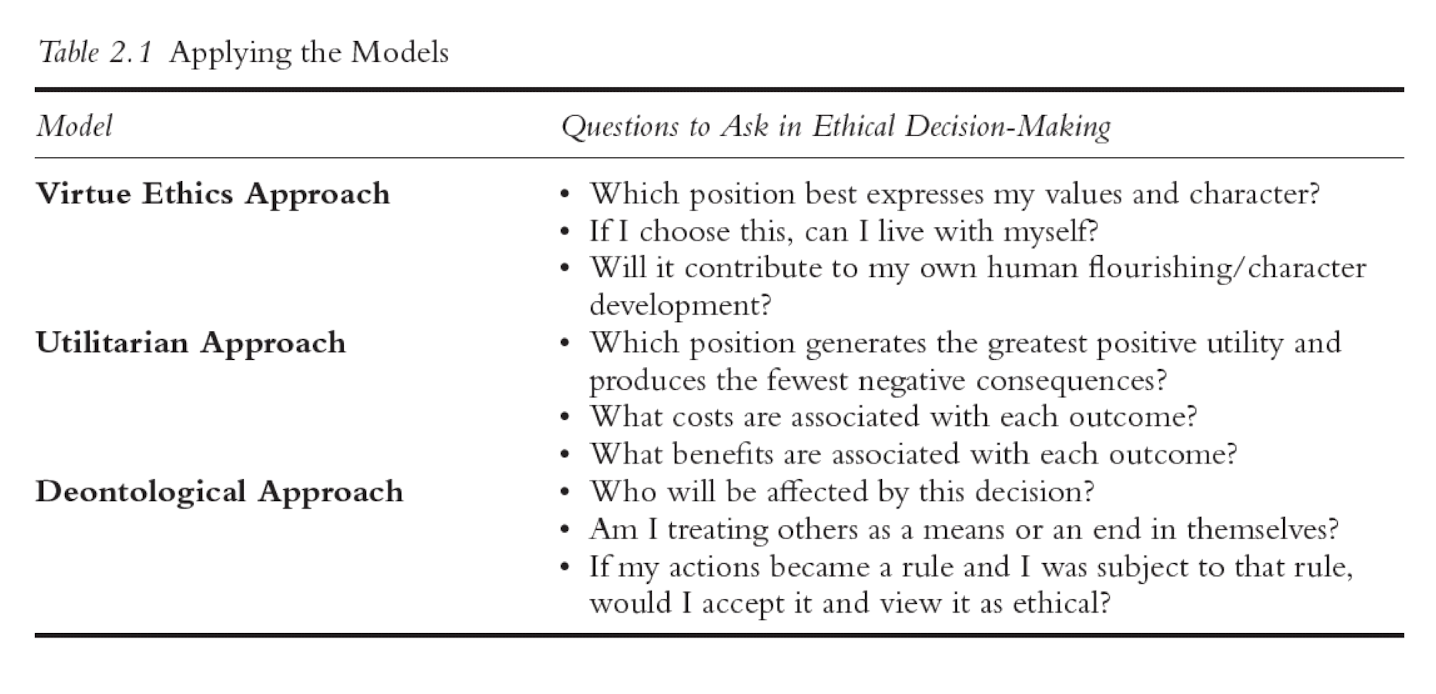
The agent-centered virtue ethics model assumes that individuals make decisions and that the most ethical solution is the one that helps an individual to develop their character, leading to human flourishing.
It is attractive to individuals today because of its emphasis on each individual’s inherent rights and dignity and its requirement that decisions be made and applied consistently.
The utilitarian model , in contrast, advocates a type of situational ethics where “ the right thing to do “ is highly affected by the environment in which decisions are made.
In this model, as noted, the decision-maker’s intent is not essential. Instead, what counts is the outcome.
The deontological model considers who might be affected by an ethical decision.
Which choice allows the most humane treatment of the participants, not treating them as a means to an end but as ends themselves?
This model helps us think about technology’s effects on people and how people are affecte by technological decision-making.
2.2.4 Apply Three Models in Cybersecurity Ethics
2.2.5 Summary
Virtue ethicists believe that there is some objective list of virtues that, when cultivated, maximize a person’s chance of living a good life.
Utilitarianism assumes that one can measure the utility of particular choices and decide rationally which action will yield the most utility. In seeking a particular end, other values may need to be compromised, and it assumes that what is “best” in one situation might not be best in another.
Deontological ethicists believe that humans can use their reasoning abilities to derive an ethical position by asking a series of questions, including “What would be the outcome if everyone acted this way?” And, “Would I approve of this behavior having the status of a universal law?”
2.2.6 A Layout of Western Ethical Theories
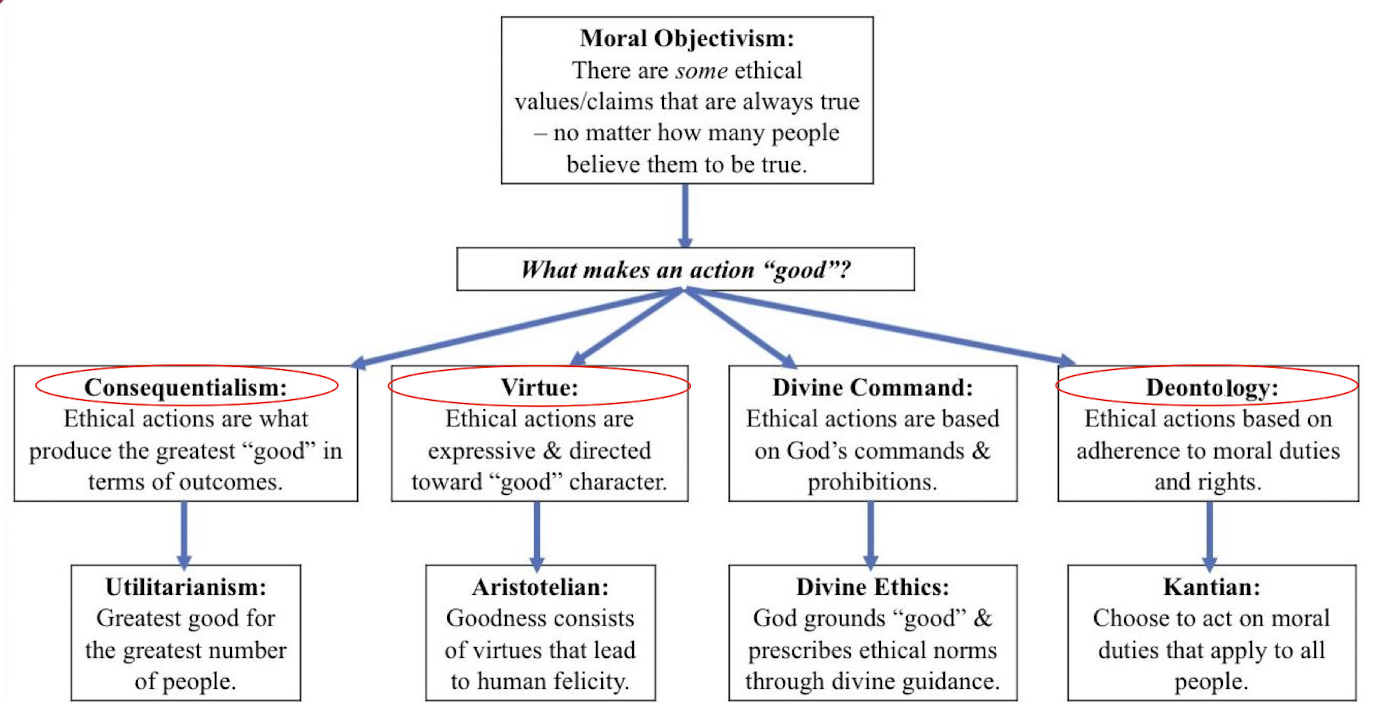
https://twitter.com/KhalilAndani/status/1301980253196300290^23
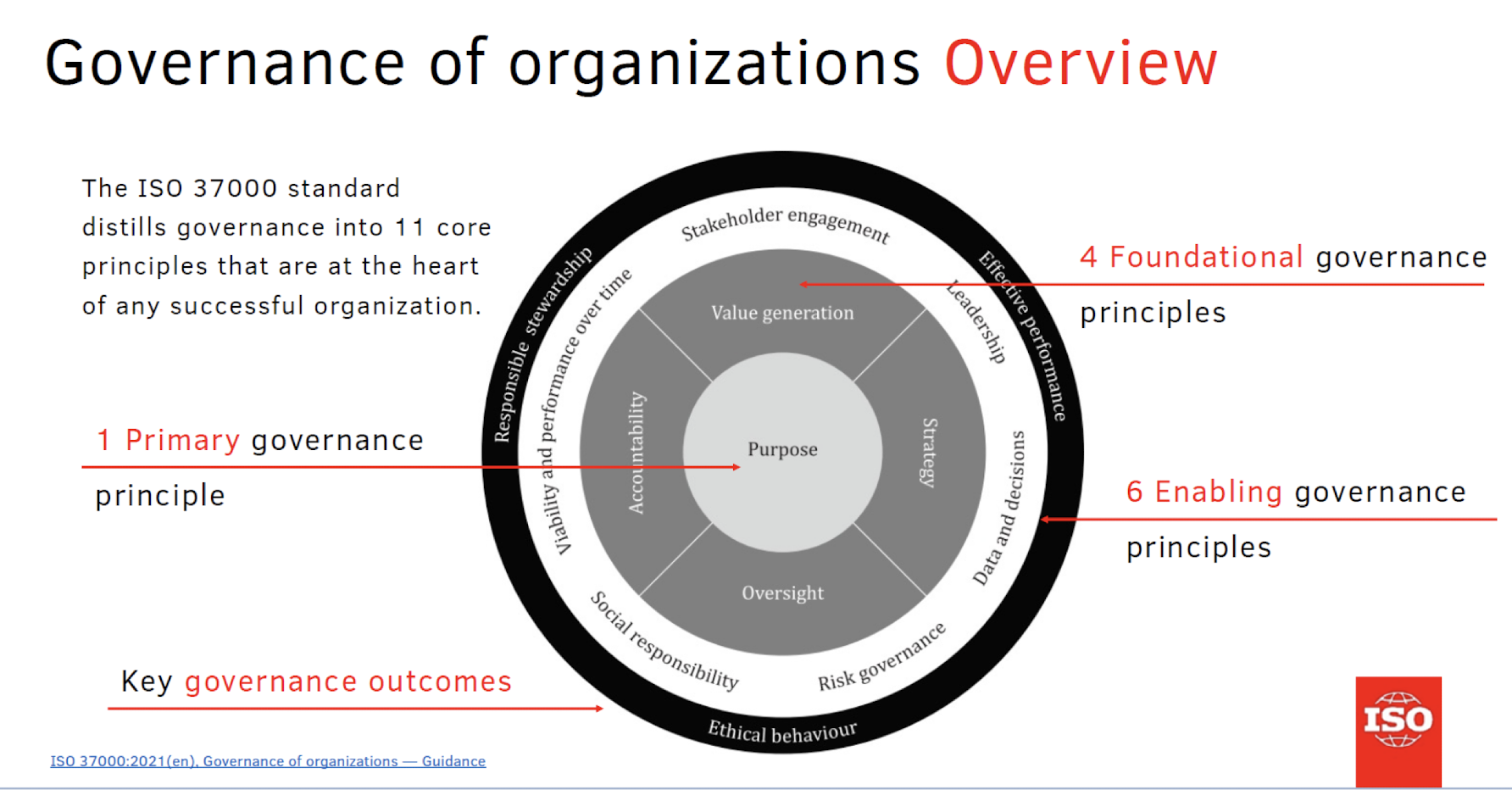
2.3 Business Ethics: ISO 37000
The International Standards Organization (ISO) published ISO 37000 — guidance for the governance of organizations on Sept. 14, 2021.
ISO 37000 is the product of experts from a wide range of organizations in over 70 countries around the world and is billed as the “first ever international benchmark for good governance .”
Principle-based with identified outcomes
The role of ISO 37000 for Developing countries
The corruption perception index and ease of doing business survey confirm that the challenges of organizational governance are perhaps greater in Developing Countries.
Developing countries had fewer relevant laws, codes and standards to draw on, thereby making governance of organizations weaker. ISO 37000 will be a key resource.
2.3.1 Organizational governance expectations are changing fast
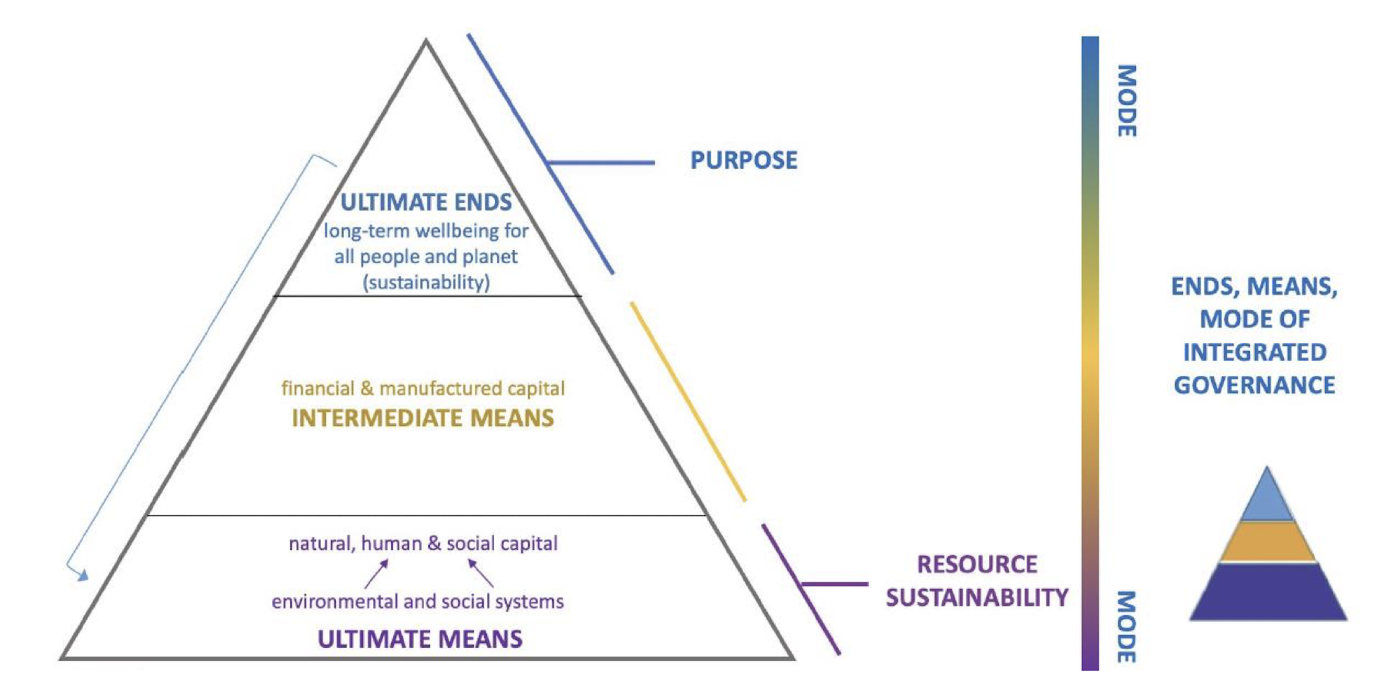
- An economy is about transforming resources into long-term wellbeing for all people and planet.
- Organizations are the key means society has decided we can best enact the economy.
- All organizations are created to help individuals achieve a shared clear goal.
- Governance provides the direction, accountability and oversight of organizations so that they achieve that goal in the way intended.
- Governance until now has been mostly focused on a goal of optimizing benefit to the organization (including members). The end goals of long-term wellbeing and the health of the social and environmental systems this depends on (inc. climate) have been ungoverned.
- This view has been changing fast - towards directly delivering wellbeing for society in a way that protects the social and environmental systems that underpin this wellbeing.
- ISO37000 formalizes this shift.
2.3.2 Governing the Ends, Means and Mode:
2.3.3 Scope of ISO37000: 2021
Governance of Organizations: Guidance
- “The document gives guidance on the governance of organizations.
- It provides principles and key aspects of practices to guide governing bodies and governing groups on how to meet their responsibilities so that the organizations they govern can fulfil their purpose.
- It is also intended for stakeholders involved in, or impacted by, the organization and its governance.
- It is applicable to all organizations regardless of type, size, location, structure or purpose.”
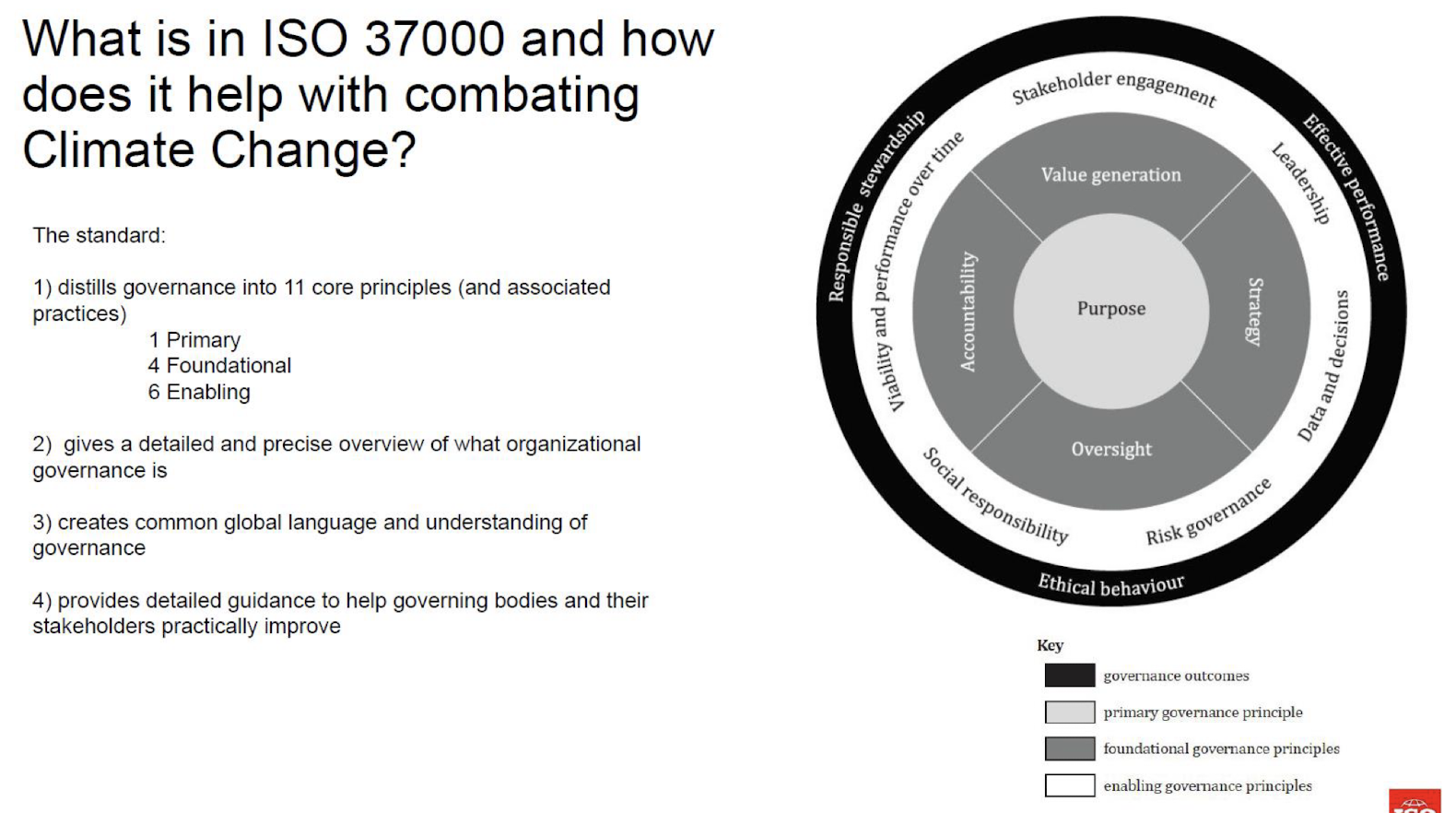
Governing the end, means and mode:
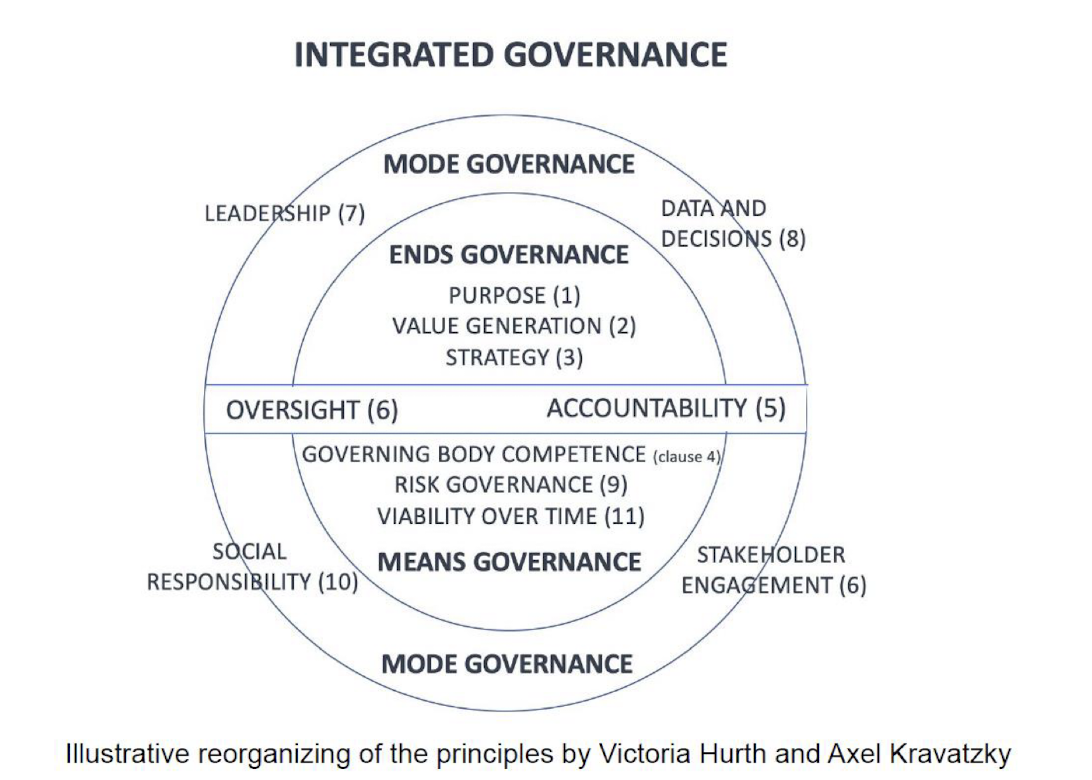
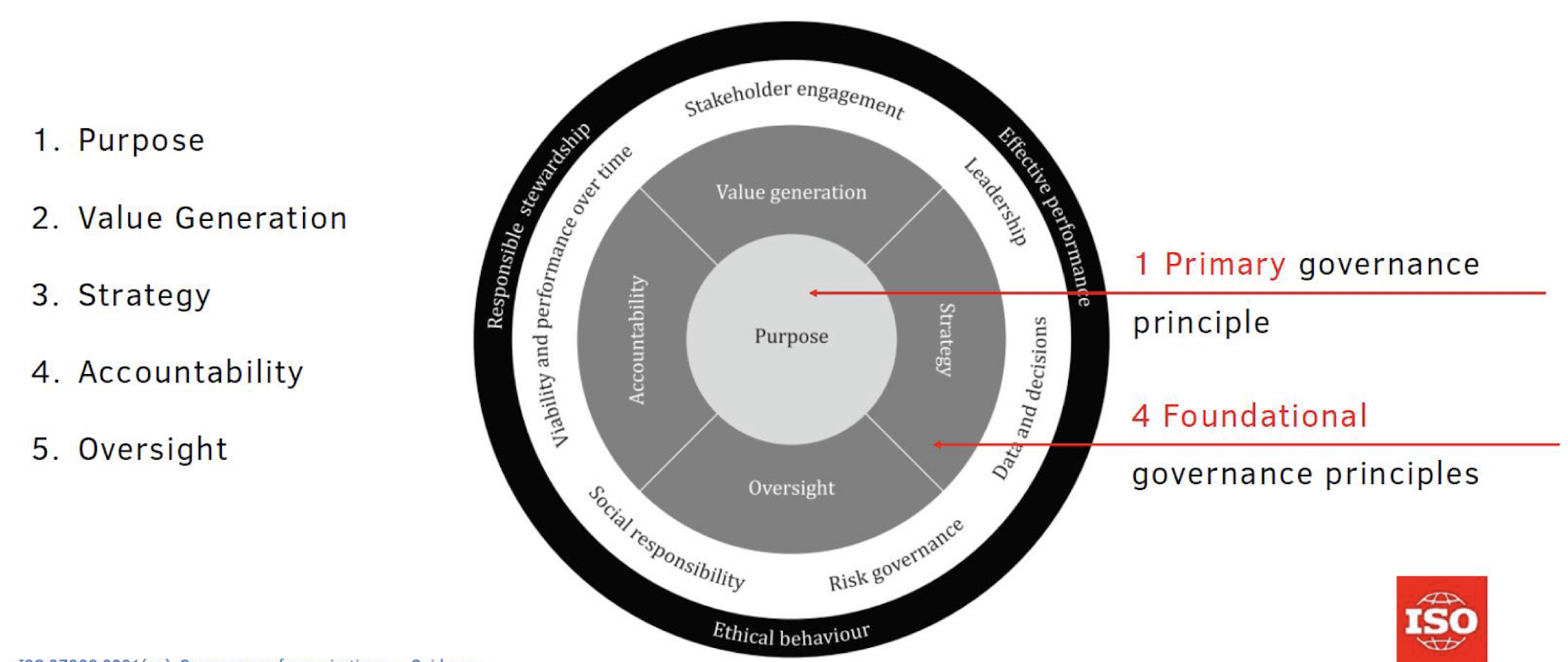
2.3.4 1. Purpose
ISO 37000 clarifies that the governing body is responsible for defining and elaborating a meaningful, relevant organizational purpos e as the reason the organization exists and gives detailed guidance on relevant practice.
It also makes clear that the governing body should define the organizational values as the compass to guide how the purpose is achieved.
The Primary Principle
- Organizational purpose statement defines, specifies, and communicates the ultimate value the organization intends to generate for specified stakeholders.
2.3.5 2. Value Generation
Organizations don’t generate long-term value that achieves the organization’s purpose or avoids harm by chance.
ISO 37000 establishes the responsibility of the governing body role to clarify the value generation objectives and to govern so that these objectives are met. This requires the governing body to define a clear and transparent value generation model that defines, creates, delivers and sustains appropriate value.
A Foundational Principle
- A value generation model provides basis for innovation and collaboration with stakeholders.
2.3.6 3. Strategy
- The governing body should direct and engage with the organizational strategy, in accordance with the value generation model, to fulfil the organizational purpose.
- The governing body sets the strategic outcomes, establishes governance policies to guide the strategy development, and engages in strategic planning.
- The governing body should actively and dynamically steer the strategy in way that balances value generation in the present with value generation in the future.
A Foundational Principle
- The organizational strategy reflects the governing body’s intentions regarding the organization’s achievement of the strategic outcomes within its changing context.
2.3.7 4. Accountability
ISO 37000 clarifies that the governing body is responsible for and accountable to the organization as a whole.
Accountability at all levels is a key aspect of governance. Accountability is established through the assignment of, and agreeing to, responsibility and the delegation of authority.
The governing body can delegate but should demonstrate its willingness to answer for the fulfilment of its responsibilities, even where these have been delegated.
A Foundational Principle
- Accountability engenders trust and legitimacy , which leads to improved outcomes. It is demonstrated through reports, disclosures, effective stakeholder engagement , and applying improvements.
2.3.8 5. Oversight
- ISO 37000 outlines the governing body’s role and responsibility to effectively oversee the organization.
- For the first time ever, clarity is given at a global level on the nature, elements of and integration into organizations of the internal control system and the assurance processes.
A Foundational Principle
- Oversight by the governing body includes ensuring that an internal control system is implemented and assuring itself that the governance system is appropriately designed and operating as intended.
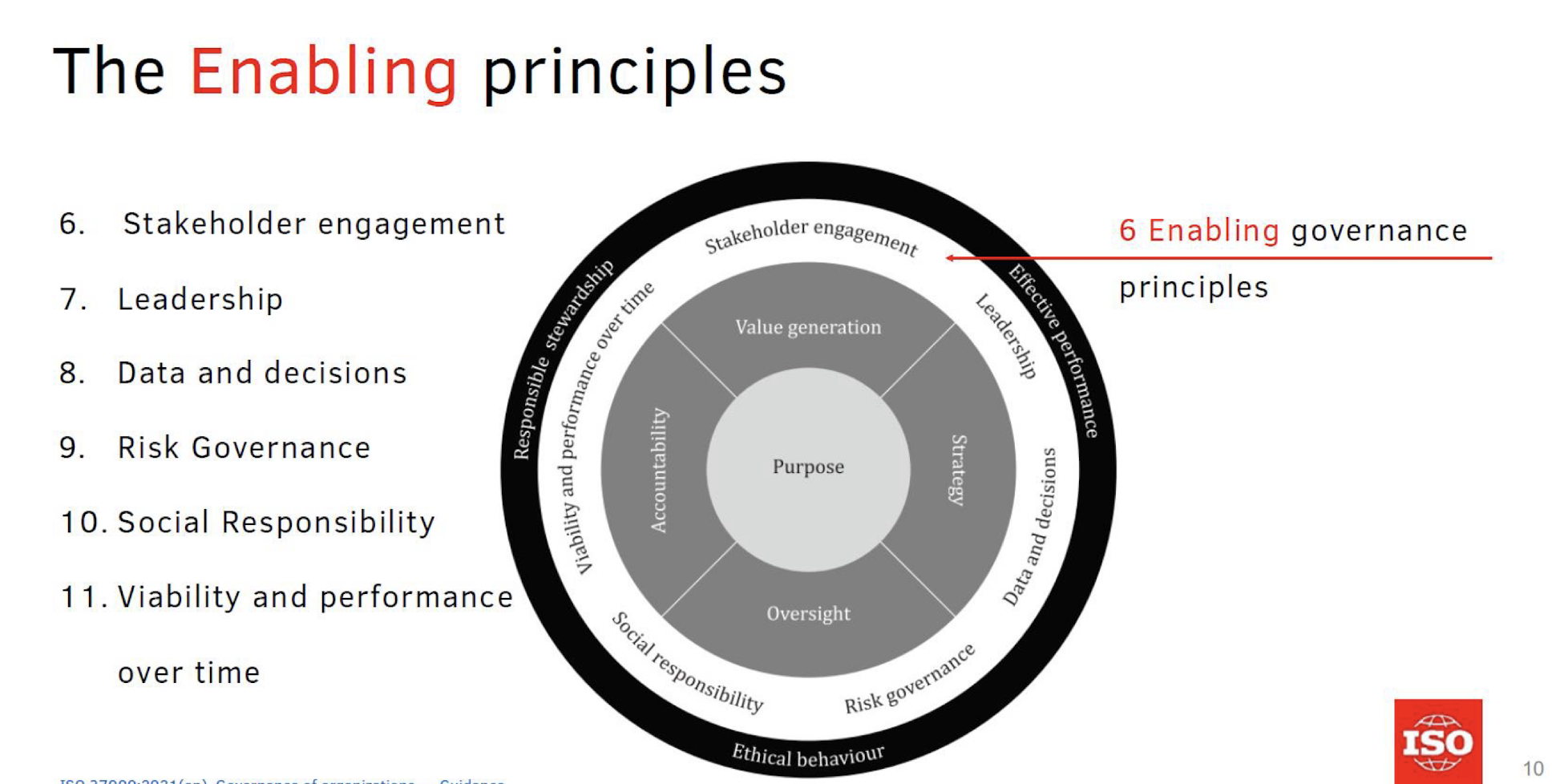
2.3.9 6. Stakeholder engagement
- ISO 37000 outlines why and how the governing body should understand its stakeholders , engage them in achieving the organizational purpose through the strategy, establish clear criteria to determine the relevance of stakeholder expectations, ensure effective relationships are established and maintained , and that expectations become an effective part of organizational decision-making.
An Enabling Principle
- Member, reference, and relevant stakeholder engagement are key.
2.3.10 7. Leadership
- ISO 37000 clarifies that the governing body should be values-driven and lead the organization ethically and effectively and ensure such leadership throughout the organization and its external context.
- The governing body should set the tone for an ethical and values-based organizational culture.
An Enabling Principle
- The governing body should lead by example to create a positive values-based culture , set the tone for others, and engender trust and mutual cooperation with the organization’s stakeholders.
2.3.11 8. Data and Decisions
ISO 37000 outlines that the governing body should recognize data as a strategic and valuable resource for decision making by the governing body.
The governing body ensures that its own decision-making process and those of others in the organizations are ethical, responsible and effective.
An Enabling Principle
- The governing body should ensure that the organization identifies, manages, monitors and communicates the nature and extent of its use of data.
2.3.12 9. Risk Governance
ISO 37000 explains that the governing body sets the tone and shapes the culture for a proactive and anticipative approach to the management of risk across the organization.
The governing body ensures the systematic assessment of risks and defines the risk criteria , in particular the appetite for risk and risk limits.
The governing body assesses, treats, monitors, and communicates the nature and extent of the risks faced when making decisions.
An Enabling Principle
- Accountability engenders trust and legitimacy, which leads to improved outcomes. It is demonstrated through reports, disclosures, effective stakeholder engagement , and applying improvements.
2.3.14 10. Social Responsibility
The governing body should ensure that decisions are transparent and aligned with broader societal expectations.
For an organization to act in a socially responsible way, it needs to operate within the parameters of acceptable behaviour and
not allow actions that are legally or locally permissible but not in line with what is expected of it by its broader stakeholders and society.
A Foundational Principle
- Oversight by the governing body includes ensuring that an internal control system is implemented and assuring itself that the governance system is appropriately designed and operating as intended.
2.3.15 11. Viability and Performance Over Time
- The governing body identifies, describes and assesses the key resources and value generation systems the organization depends on to generate value, how these interrelate and how they are used over time. It ensures that the organization protects and restores the key resources and systems that it depends on or affects.
An Enabling Principle
- Where an organization fails to understand and respond to the needs of the systems of which it is a part, it is unlikely that the organization will remain viable and per form over time.
2.4 Ethics Management System

https://www.koreaaero.com/EN/Sustainability/EthicsManagementSystem.aspx
2.4.1 Ethics Management System
Establishment of Ethics System
- Dedicated organization assignment
- Appointment of compliance officer
- Establishing regulations for ethics
- Distribute employee guide books
- Operation of ethics committee
Preventive Activity
- Ethics management promotion
- Employees and managers training
- Operation of the Cyber Reporting System
- Employees/partners ethical pledge
- Legal advice and consulting
Inspection
- Assess risks by organization
- Periodic, annual audit
- Check compliance with accounting standards
- Compliance with export license
Evaluation of Analysis
- Analyze and mitigate risks
- Annual activity validation
- Report to CEO / Board / Audit Committee
Complement the Ethics System
- Reconstitute annual activities
- Supplement the regulations
- Update international regulations
- Participate in external ethics forums and benchmarking
2.4.2 ISO 37001 - Anti-bribery Management System (ABMS)
- The standard provides guidance to help an organization implement an anti-bribery management systems
- It can also help an organization to prevent, detect, and address bribery.
2.4.3 Three Key Components of ABMS
2.4.4 Potential Benefits of Implementing ABMS
It assists an organization in implementing an anti-bribery management system, or in enhancing its existing controls;
It helps provide assurance to stakeholders that the organization has implemented internationally recognized good practice anti-bribery controls;
In the event of an investigation, it helps provide evidence to the prosecutors or courts that the organization had take reasonable steps to prevent bribery.
2.4.5 Essential Elements for Successful ABMS

2.4.6 ISO 37301 - Compliance Management System (CMS)
The standard provides guidance to help an organization implement a compliance management systems and recommended practices.
It can also help an organization to demonstrate its commitment to comply with relevant laws, regulatory requirements, industry codes and organizational standards , as well as standards of good governance , generally accepted best practices, ethics and community expectations.
https://www.iso.org/standard/75080.html
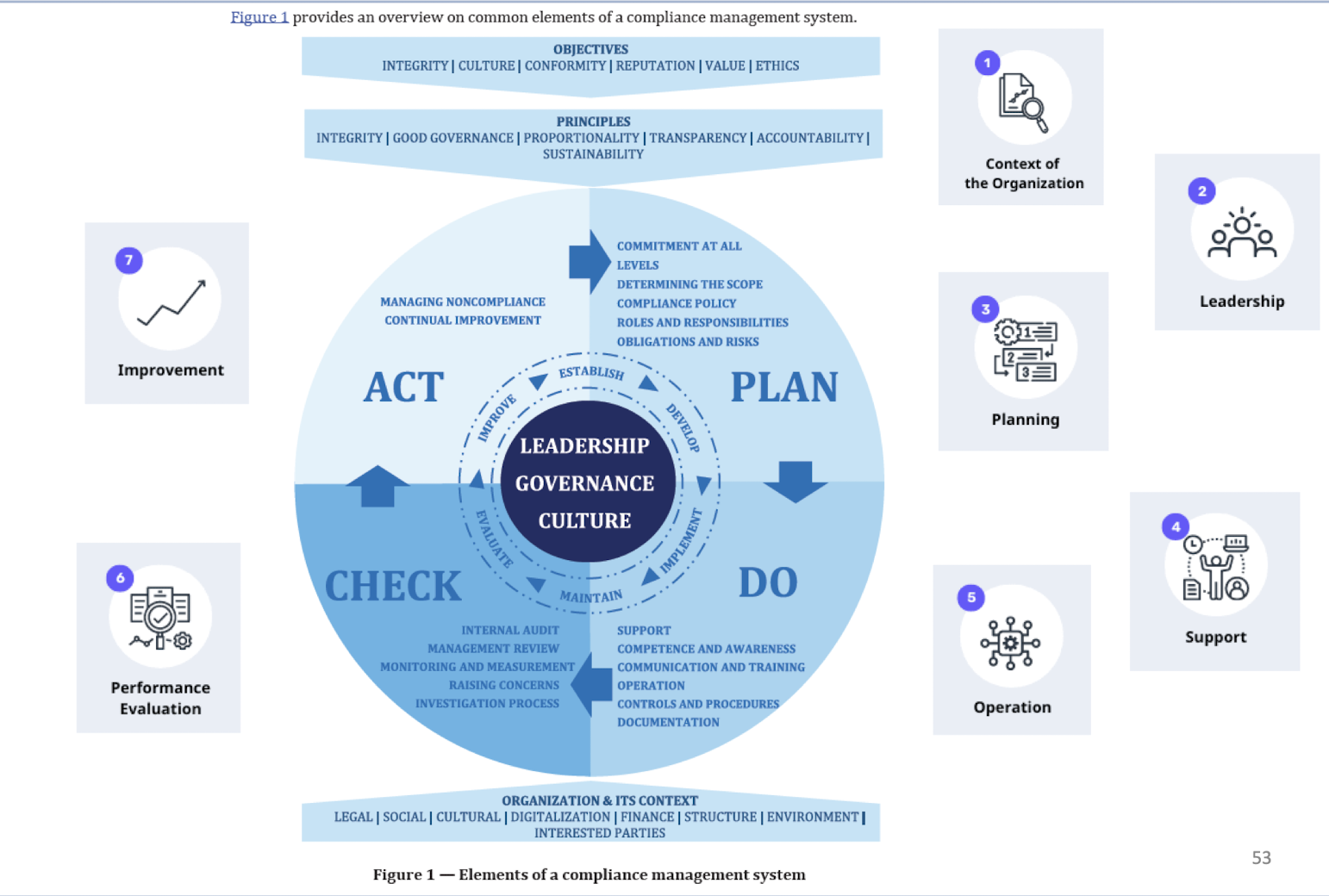
2.4.7 7 Key Elements of Compliance Management System
Context of the Organization - Understanding the organization, stakeholders’ expectations, the strategy and system in place, and how risks are assessed is essential for success.
Leadership - It includes the governing body, anti-bribery policy, compliance function, roles, and responsibilities.
Planning - Address risks, opportunities, and anti-bribery or anti-corruption objectives through compliance activities and planning.
Support - Include resources, training, communication, and documentation that enable staff to know their responsibilities and have the required skills.
Operation - Commitments, gifts, hospitality, donations, and investigations are all due diligence measures that help prevent bribery and corruption.
Performance Evaluation - To ensure the company is running smoothly, regularly check things like progress, performance, and compliance through measures like internal audit and management review.
Improvement - It includes some nonconformity and corrective actions, and program improvement.
2.4.8 Potential Benefits of Implementing CMS
Improving business opportunities and sustainability;
Protecting and enhancing an organization’s reputation and credibility;
Taking into account expectations of interested parties;
Demonstrating an organization’s commitment to managing its compliance risks effectively and efficiently;
Increasing the confidence of third parties in the organization’s capacity to achieve sustained success;
Minimizing the risk of a contravention occurring with the attendant costs and reputational damage.
2.4.9 whistleblowing
reporting of suspected or actual wrongdoing (3.8) by a whistleblower (3.9)
Note 1 to entry: A report of wrongdoing can be verbal, in person, in writing or in an electronic or digital format
Note 2 to entry: It is common to distinguish:
open whistleblowing, where the whistleblower discloses information without withholding their identity or requiring that their identity be kept secret;
confidential whistleblowing, where the identity of the whistleblower and any information that can identify them is known by the recipient but is not disclosed to anyone beyond a need to know basis without the whistleblower’s consent, unless required by law;
anonymous whistleblowing, where information is received without the whistleblower disclosing their identity
Note 3 to entry: Organizations (3.2) can use an alternative term such as “speak up” or “raise a concern”, or an equivalent.
2.4.10 ISO 37002 - Whistleblowing Management System (WMS)
The standard provides guidance to help an organization implement a whistleblowing policies and processes under management systems.
It can also help an organization for establishing, implementing, maintaining and improving a whistleblowing management system, with the following outcomes:
- encouraging and facilitating reporting of wrongdoing ;
- supporting and protecting whistleblowers and other interested parties involved;
- ensuring reports of wrongdoing are dealt with in a proper and timely manner ;
- improving organizational culture and governance ;
- reducing the risks of wrongdoing.
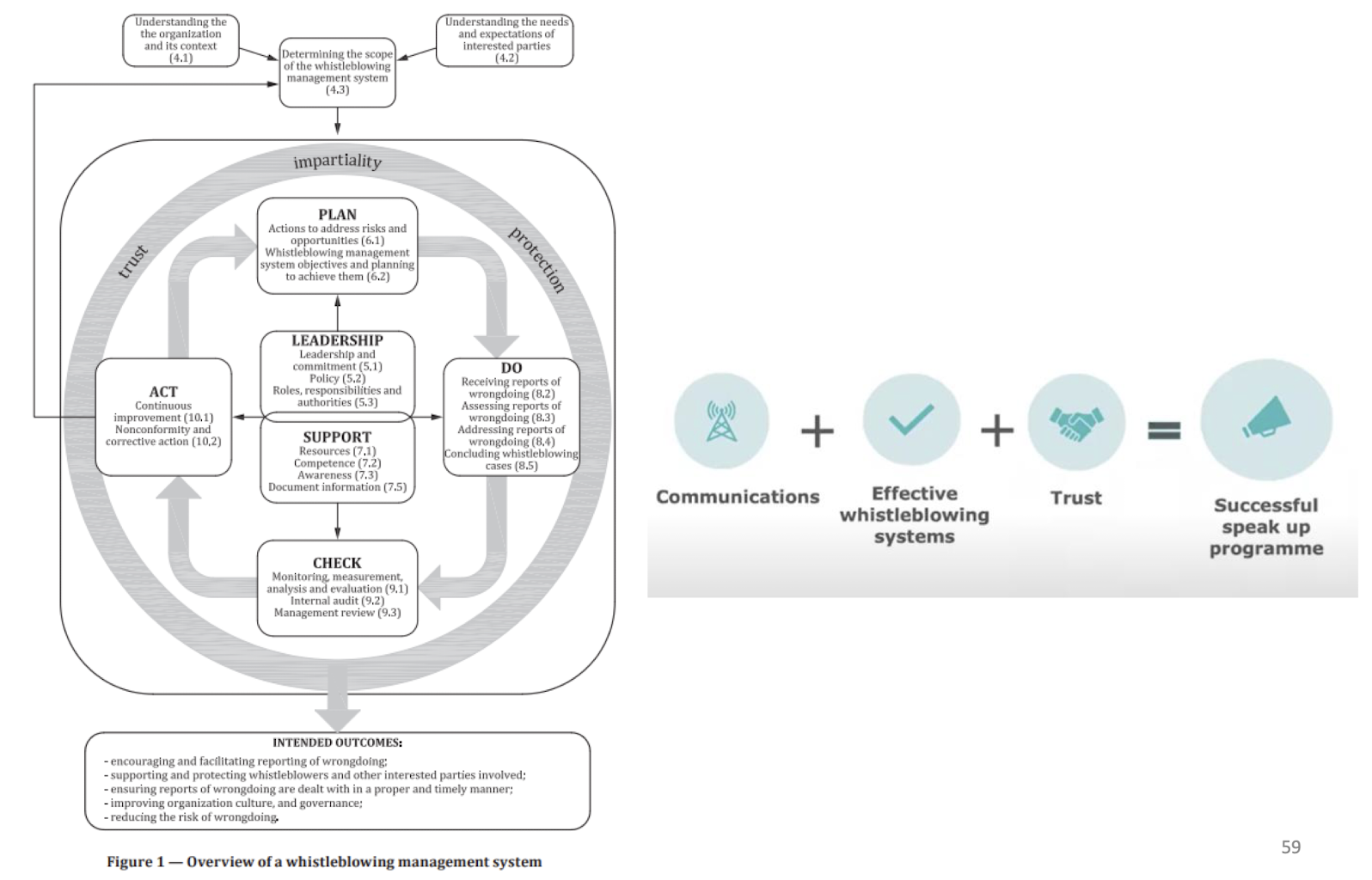
2.4.11 Potential Benefits of Implementing WMS
allowing the organization to identify and address wrongdoing at the earliest opportunity;
helping prevent or minimize loss of assets and aiding recovery of lost assets;
ensuring compliance with organizational policies, procedures, and legal and social obligations;
attracting and retaining personnel committed to the organization’s values and culture;
demonstrating sound, ethical governance practices to society, markets, regulators, owners and other interested parties
2.4.12 Speak Up Culture
Tone from the Top
- Employees hear from senior leadership
- Board reporting and engagement
Management Trusted to Act on Concerns
- Open door management culture
- Training
- Policies & processes
Employees Feel Supported / Confident to Speak Up
- Speak up options are available
- Clear policies on confidentiality and non-retaliation
2.4.13 Whistleblower
Edward Joseph Snowden is an American and naturalized Russian citizen who was a computer intelligence consultant and whistleblower who leaked highly classified information from the National Security Agency (NSA) in 2013 when he was an employee and subcontractor.
PRISM is a code name for a program under which the United States National Security Agency (NSA) collects internet communications from various U.S. internet companies. PRISM is an acronym for Planning Tool for Resource Integration, Synchronization, and Management.
2.4.14 Other Reference of Business Ethics Management:
Business Ethics: Can ISO 37000 enhance your company’s compliance and ethics?
Korea Aerospace Industries Ltd. (KAI) Ethical Management
ISO 37002 on whistleblowing management systems - The ethics perspective
3 InfoSec Ethics
3.1 What is a Hacker?
- When the term “hack” originated in the 1980s, it was often applied to individuals like Steve Jobs and Bill Gates.
- At that time, they seen as engaging in heroic and creative endeavors that produced new technological resources which enriched society
- Today hacking has both negative and positive meanings
- Negative meaning:
- unauthorized access to a system (if an individual working in one section of a corporation is looking at files belonging to another section of the corporation for which he had not been given permission)
- Illegal access to a system (through utilizing stolen passwords, impersonating another user, or simply using an algorithm to guess a password)
- Positive meanings
- While hacking may have initially begun in the early days of the computer revolution as merely a game or joke.
3.2 Types of Cybercrime
- Cybercrimes may have a variety of targets - from private actors to corporate actors to international organizations and nation-states. Hackers may also target different components within a computer system. Different types of cybercrime showed as follows.
- Cybertrespass ( 網路入侵 ) - the use of information technology to gain unauthorized access to computer systems or password-protected sites
- Cyber vandalism ( 網路破壞 ) - the use of information technology to unleash programs that disrupt the operations of computer networks or corrupt data (e.g. DDoS)
- Computer fraud ( 電腦詐欺 ) - the use of deception for personal gain in online business transactions by assuming a false online identity or by altering or misrepresenting data
- Cyberterrorism ( 網路恐怖主義 ) is the execution of politically motivated hacking operations intended to cause grave harm, resulting in either loss of life or severe economic loss.
- Cybercrimes may include attacks on hardware or software (or the supply chain) to damage a system or data.
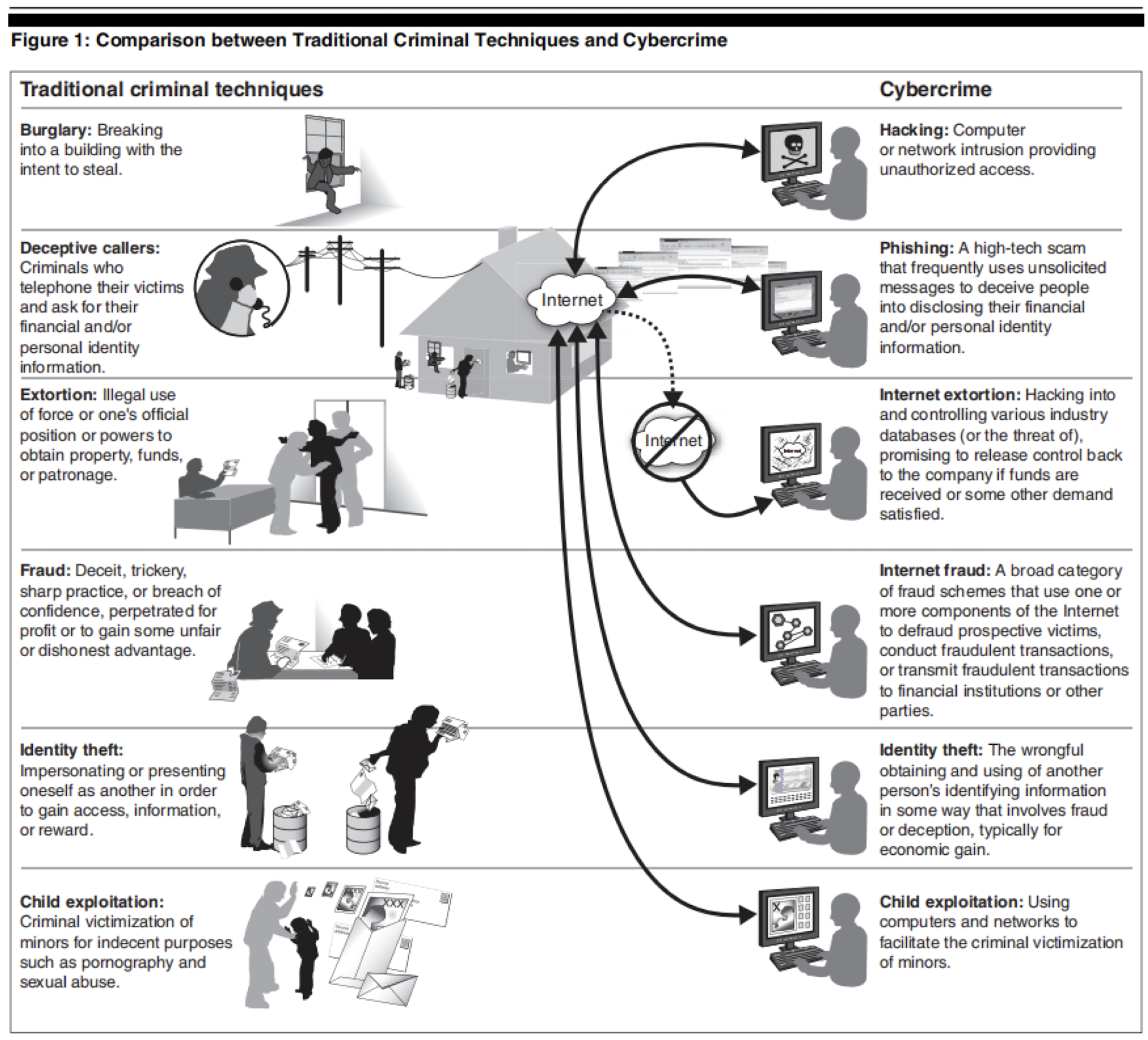
3.3 Is Hacking Always Wrong?
- Not all hacking is illegal!
- we need to consider several factors
- from who the hack targets ,
- to the intents of the hacker,
- to the conditions under which the hack takes place.
- The argument as “Hacking is the skill to question trust and control assumptions expressed in software and hardware, as well as in processes that involve human(s)-in-the-loop.”
- Thus, hackers acquire and use skills like the ability to encrypt and decrypt data, create and transmit viruses, and identify and diagnose security vulnerabilities within a computer system.
- Understand that their actions have ethical consequences can set limits regarding what behaviors cross an ethical line.
Like doctors or martial artists could use their skills to aid humans or harm them
3.4 Why Do People Hack?
- Hackers may have more than one motive, and a hacking attempt may be a “one-of” event or related to a larger strategy
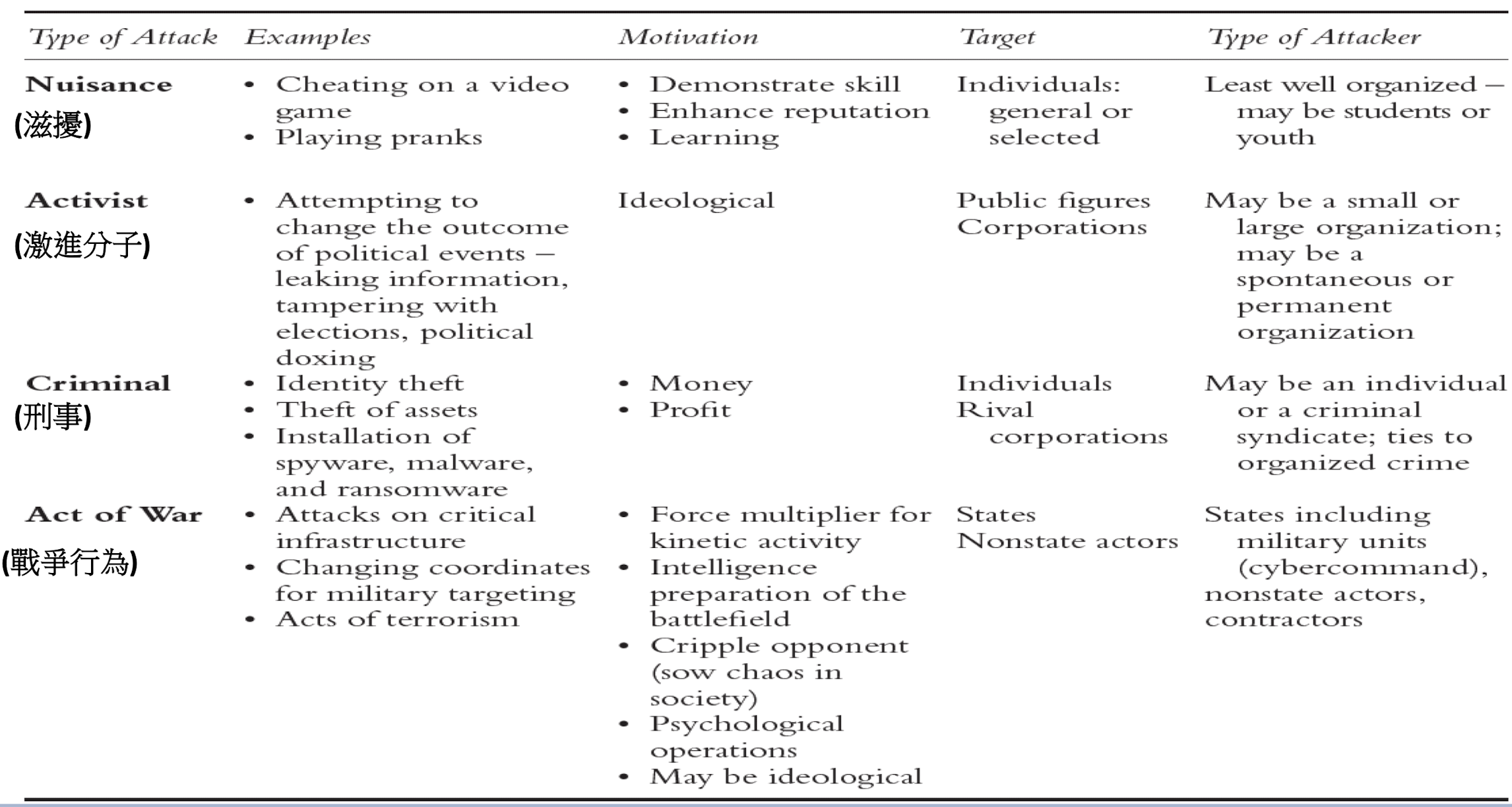
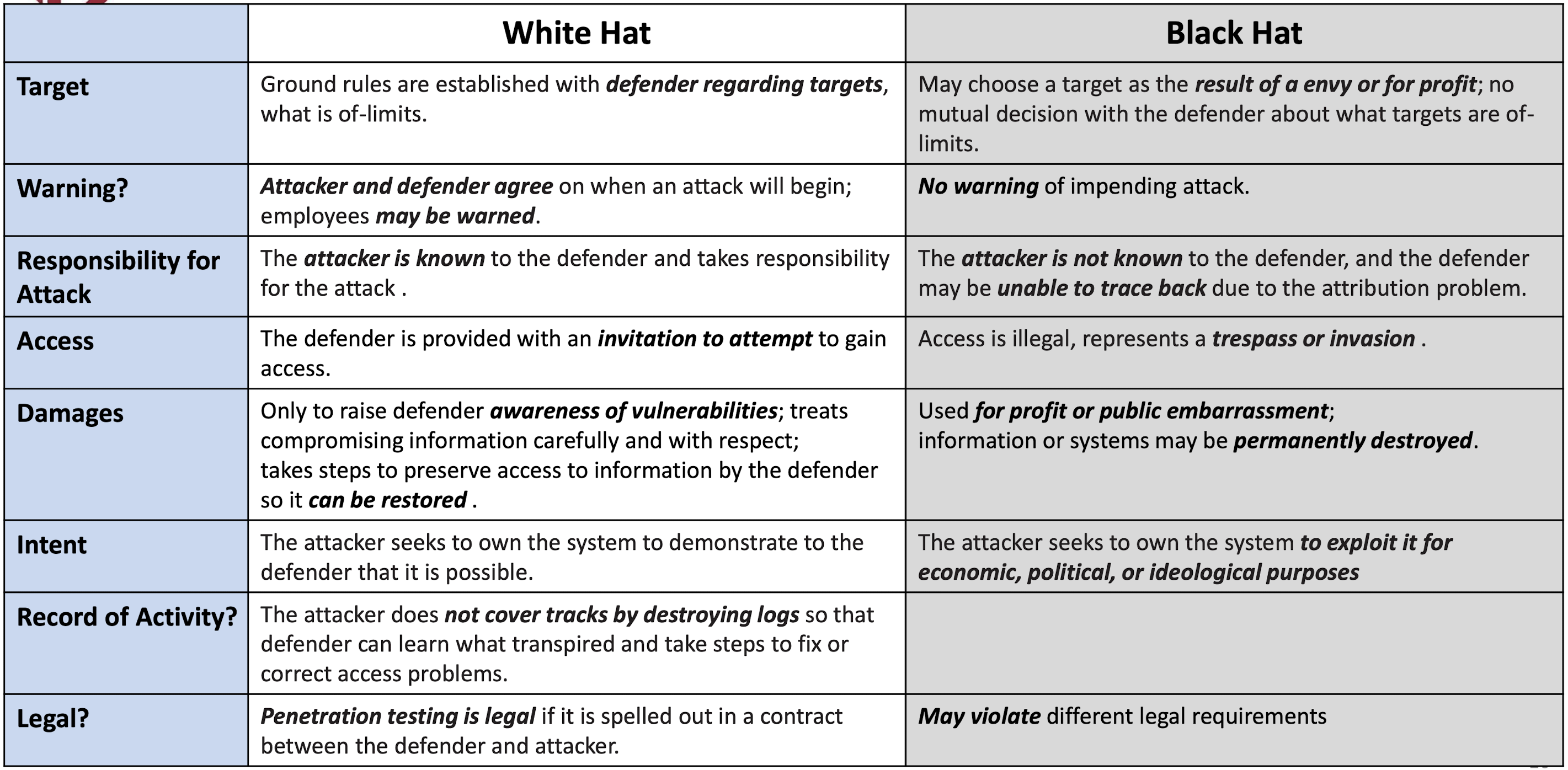
3.5 White Hat, Black Hat, and Grey Hat Hackers
- White hat hacker ( ethical hacker ) works for or with a private corporation or government agency to test their system’s security. (e.g. To identify system vulnerabilities)
- Today, over 50,000 individuals have received the Certification in Ethical Hacking from the International Council of E-Commerce Consultants (EC-Council). The certification is endorsed by the US National Security Agency and the Department of Defense.
- Black hat hackers attempt to breach internet security and gain unauthorized access to a system.
- They seek to destroy or harm the systems they penetrate, often by releasing viruses or destroying files. Black hat hackers’ activities are frequently illegal, and they may work on their own or in collaboration with a criminal organization.
- Grey hat hacker is self-employed, working to collect bug bounties through testing systems without authorization, yet seeking not to damage the systems but rather to enrich himself by collecting rewards for identifying system vulnerabilities.
White Hat Versus Black Hat Hacking Activities
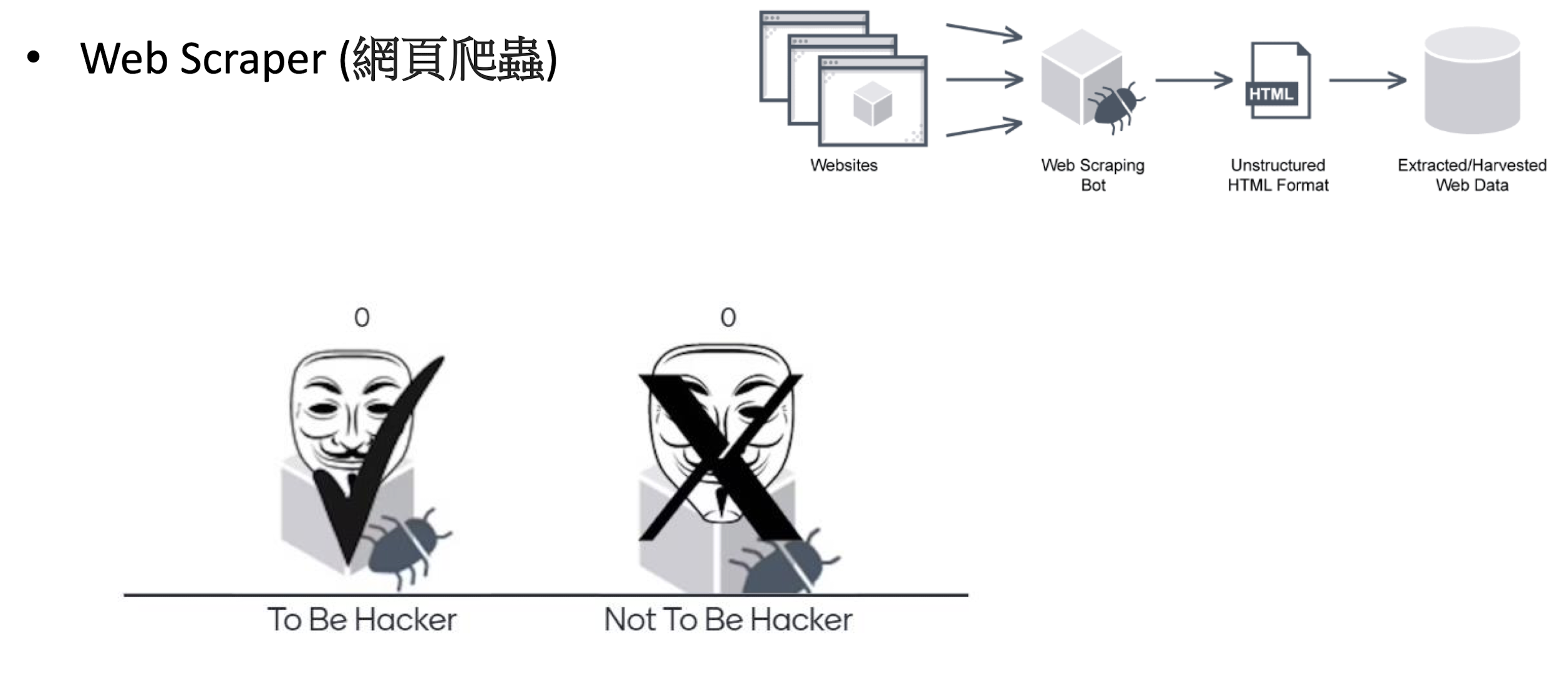
3.6 Discussion - Is Web Scraping Considered Hacking?
- Web scraping is a process by which companies or individuals use automated programs (or bots) to simulate humans who might browse the web.
- If you typed a query into Google such as “real estate listings near me,” you may have been directed to a site displaying information obtained through web scraping.
- Using a web scraping program to impersonate or imitate a human user can be considered deception and an ethical breach.
- Users must often sign the Terms of Service (TOS) before using a site.
- Facebook ‘s TOS expressly forbids users from engaging in Automated Data Collection, which they define as “the collection of data from Facebook through automated means such as harvesting bots, robots, spiders or scrapers.”
- The job-hunting site LinkedIn argues that a user who uses a bot to collect a list of programmers who have a specific certification for employment recruiting is using the site commercially rather than for private use.
- Facebook and LinkedIn was leaked that scraped the data were accused of violating the European Union’s General Data Protection Regulation (GDPR).
3.6.1 Discussion - Regulating Web Scraping
- At present, web scraping exists in a legal grey area - it is neither wholly legal nor illegal, and there are no explicit norms or social expectations regarding what is and isn’t allowed.
- The targets of web scraping are often not government entities but commercial sites such as LinkedIn , eBay , Twitter , and Google , to complicate the matter.
- Application Programming Interface (API) is a software program that allows applications to talk to each other. The API formats and delivers the request to a provider (like Facebook) and then the data back to the client.
- Web scraping represents a sort of “ back door “ to retrieving data - rather than going through the front door provided by the API.
- Some legal scholars suggest that laws about “ trespass to chattel “ (侵害他人動產) could be invoked to punish web scrapers.
3.7 Discussion - Ransomware
- Ransomware is malware that can be secretly loaded onto a computer.
- It can encrypt all of a user’s files. Once that is done, a message alerts the user that unless they pay a “ransom” (usually in cryptocurrency) to a specific address by a particular deadline, all of their data will be destroyed.
- Ransomware attacks may be particularly unethical when used against those most vulnerable in our societies, such as those who are ill and receiving hospital treatment.
- Ethics of Paying a Ransom (Pay or Not Pay?)
- Paying up may encourage a group to carry out more attacks in the future.
- A group might use the proceeds from your ransom to carry out research and development activities to make better weapons in the future.
3.7.1 Discussion - Ransomware Attack
- Attackers infect devices or systems with malware to block access, demanding payment to restore
access and sometimes to avoid dissemination of exfiltrated data. - Step 1 - Infection
- Attackers exploit vulnerabilities in order to gain access to a device or system and then installing malware remotely.
Popular among ransomware groups is spear phishing.
- Attackers exploit vulnerabilities in order to gain access to a device or system and then installing malware remotely.
- Step 2 - Attack
- Once malware has been installed, the actual ransomware attack proceeds.
- Step 3 - Extort (勒索)
- Typically, attacker demands seek payment in untraceable cryptocurrency (e.g. Bitcoin)
- Step 4 - Spread
- Ransomware attackers have become increasingly organized, forming ‘groups’ and conducting repeated attacks
over a sustained period of time.
- Ransomware attackers have become increasingly organized, forming ‘groups’ and conducting repeated attacks
- Prevention and Preparation
- Network security (e.g. firewalls, antivirus software and network traffic monitoring) to prevent and identify intrusions and suspicious activity
- Software patch management to eliminate software vulnerabilities
- Remote access security measures (e.g. Virtual Private Networks (VPNs)) to ensure secure work-from-home, and
- Segmented networks to limit the spread of malware
16
3.8 Cyber / InfoSec / Cybersecurity Ethics
- The term “ cyber ethics “ refers to a set of moral rules or a code of behavior applied to the online environment.
- As a responsible netizen (“citizen of the net” or “net citizen”), you should observe these rules to help make cyberspace a safe place.
- The term “ Information Security (InfoSec) “ refers to the preservation of confidentiality , integrity and availability of information. (CIA)
- Where
- Confidentiality : property that information is not made available or disclosed to unauthorized individuals, entities, or processes
- Integrity: property of accuracy and completeness
- Availability: property of being accessible and usable on demand by an authorized entity
3.9 Internet Responsibly
- The law also governs the Internet and you may attract legal liabilities if you perform the following activities:
- posting obscene and indecent content on the Internet;
- obtaining property or services online by deception;
- spreading viruses or malicious codes; and
- gaining unauthorized access to computers, etc.
- To be a responsible netizen so that:
- Do not store, send or disseminate any content which is likely to be offensive or obscene to a reasonable person.
- Do not access any data, systems or networks without authority or permission.
- Do not spread computer viruses or malicious codes, or conduct any hacking activities on other computers.
- Respect all other Internet users. Do not threaten, harass, stalk or abuse anyone.
3.10 Proper Use of the Internet
- The Internet operates and functions largely on a collaborative basis. Its smooth operation relies heavily on the proper conduct of users
- Be a Law-abiding Internet User
- In the Internet world, users should be aware that their online activities may be liable for criminal or civil offences in the real world.
- In general, any forms of communication, including both verbal and written, and any other acts, are governed by the law. It is applicable to the Internet too.
- Be a Responsible Internet User
- Keep the Internet runs smooth requires contribution and co-operation from everyone in the community.
- As a responsible Internet user, proper behaviors should be kept so as to be a good Internet citizen.
3.10.1 Principles of Proper Behavior for Internet Users
Do not perform any activity which is illegal, fraudulent or prohibited under any legislation, such as:
- Unauthorized access to computers;
- Access to computers with criminal dishonest intent;
- Criminal damage, such as web page defacement or spreading of malwares;
- Obtaining property or services by deception;
- Online theft;
- Online vandalism.
Do not publish, post, distribute, or disseminate any defamatory, infringing, obscene, unlawful materials such as:
- Child pornography;
- Obscene and indecent content;
- Pirated software;
- Harassment, i.e. the persistent annoyance to another person or the interference in another person’s work. This includes, the sending of unsolicited electronic messages.
Do not transmit, distribute, upload or download material, information, or software in violation of any applicable legislation.
- This includes, but not limited to, material protected by privacy and copyright laws. The following are examples:
- Sharing of copyrighted material without consents of copyright owner;
- Collect, distribute, transfer personal information without consents of the subject.
3.10.2 Be a Responsible Internet User
DON’TS
Do not perform any activities which may interfere with other users or restrict or hinder any person from accessing, using or enjoying the Internet;
Do not access, monitor or use any data, systems or networks, including another person’s private information, without authority or permission;
Do not attempt to conduct any network/port scanning or hacking activities on other computers;
- Do not send or distribute any malwares or other harmful programs;
- Do not capture, store, send or disseminate any content or material which is likely to exceed the bounds of generally accepted standards of good taste and ethics / which is likely to be offensive or obscene to a reasonable person;
- Do not access or transmit information or material via the Internet, including email, in an attempt to impersonate another individual;
- Do not submit, publish any information which violates or infringes on the rights of any other person, including the right of privacy;
- Do not aid, abet, encourage or incite any person to do or attempt to do any of the above acts.
DO’S
- Protect your system and data with adequate security measures;
- Good practices in password management, use of software, handling of emails, downloading files, and web surfing will help protect your computer from attack;
- Do treat all other Internet users with respect and do not threaten, harass, stalk, or abuse other users.
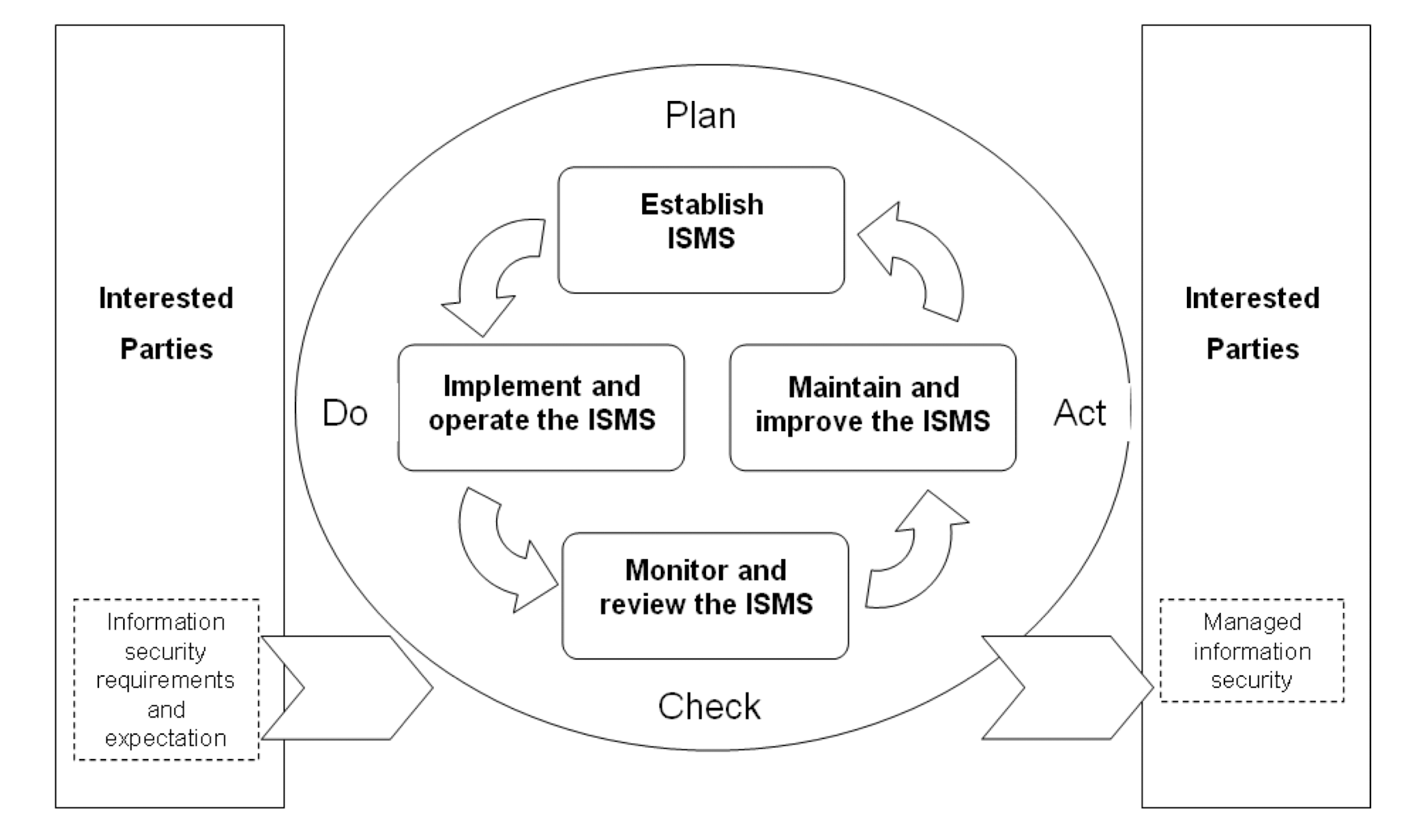
3.11 What is Information Security Management System (ISMS)?
- Information is an asset that, like other important business assets, is essential to an organization’s business and consequently needs to be suitably protected.
- Information Security means preservation of confidentiality, integrity and availability of information; in addition, other properties such as authenticity, accountability, non-repudiation and reliability can also be involved;
- Information Security Management System is a part of the overall management system, based on a business risk approach , to establish, implement, operate, monitor, review, maintain and improve information security.
3.12 ISO 27001
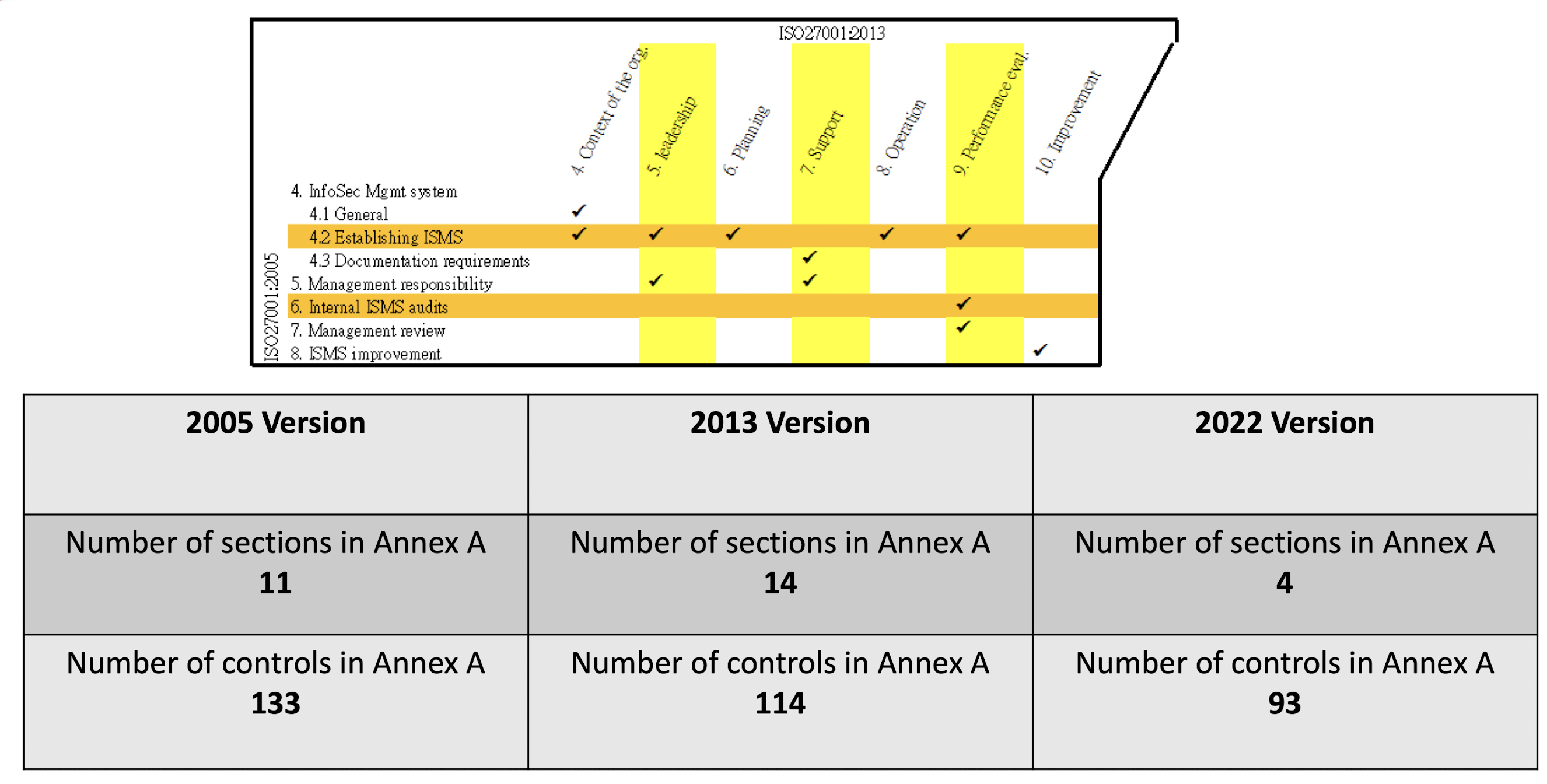
ISO 27001 is the standard for Information Security Management System (ISMS)
implementing 133 control objectives & controls (ISO27001:2005) (114 control obj & controls for 2013 version)
protecting confidentiality, integrity and availability of information
Compliance with ISO 27001 requirements can reduce the security threats from a wide range of sources.
3.12.1 Backgrounds
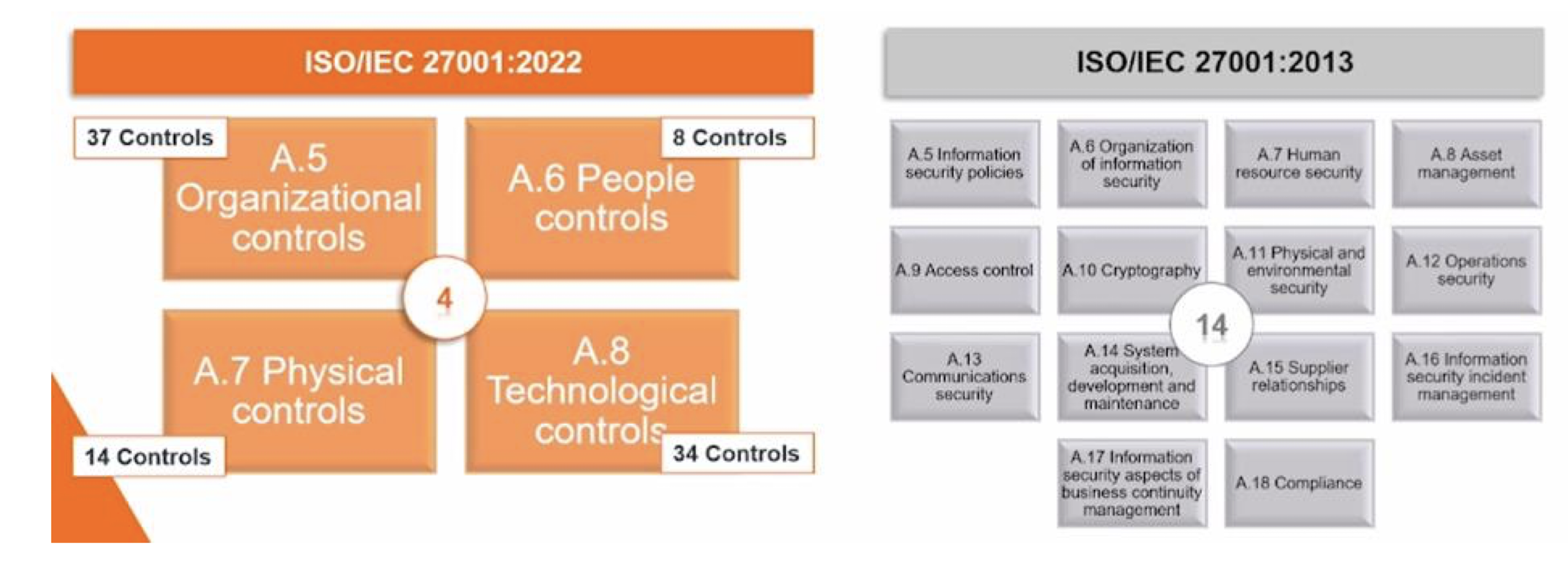
3.12.2 ISO 27001:2005 vs 2013 vs 2022
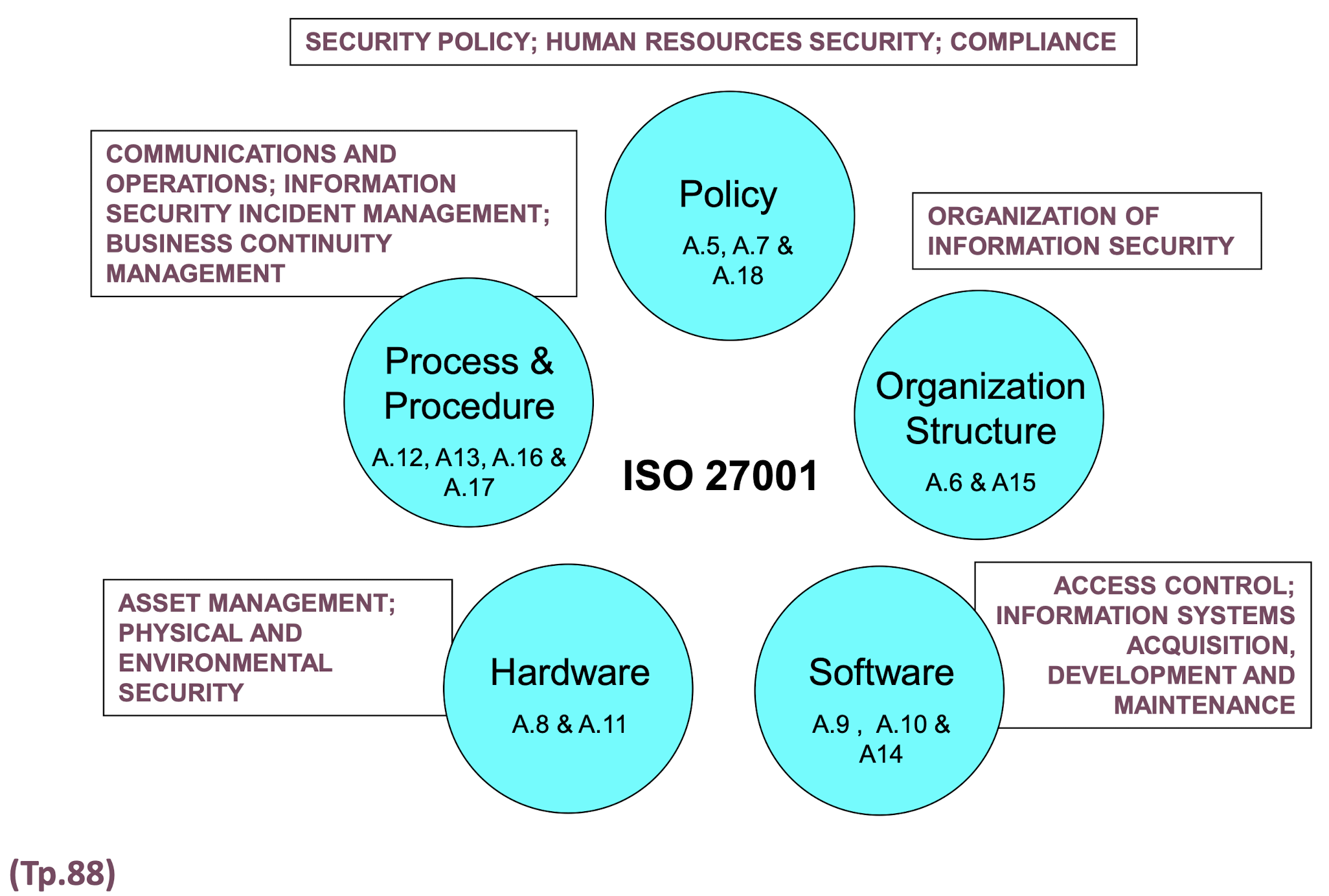
3.12.3 Annex A: Control Objectives and Controls (2013)
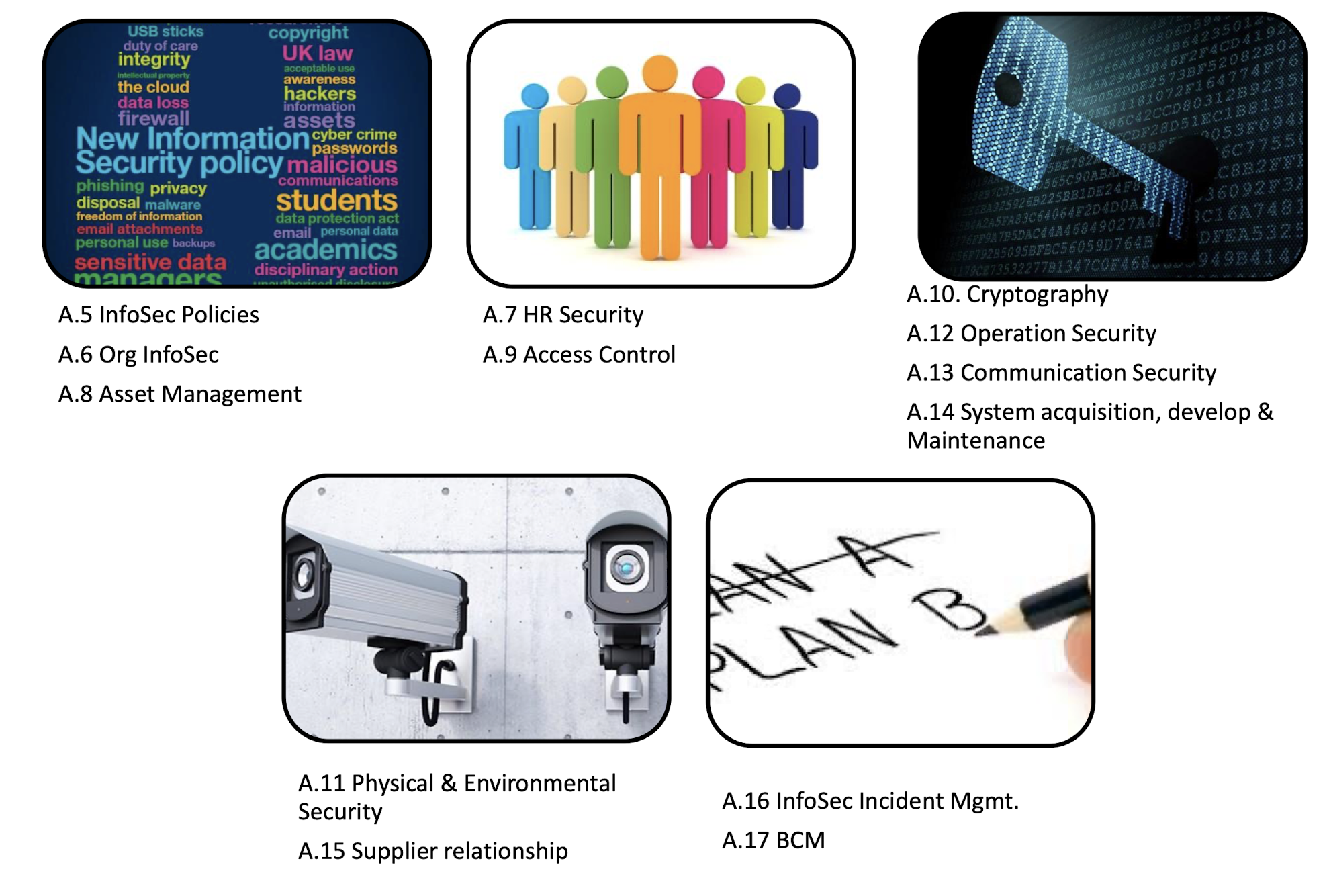
3.12.4 Annex A: Control Domains
3.12.5 InfoSec Management System Model
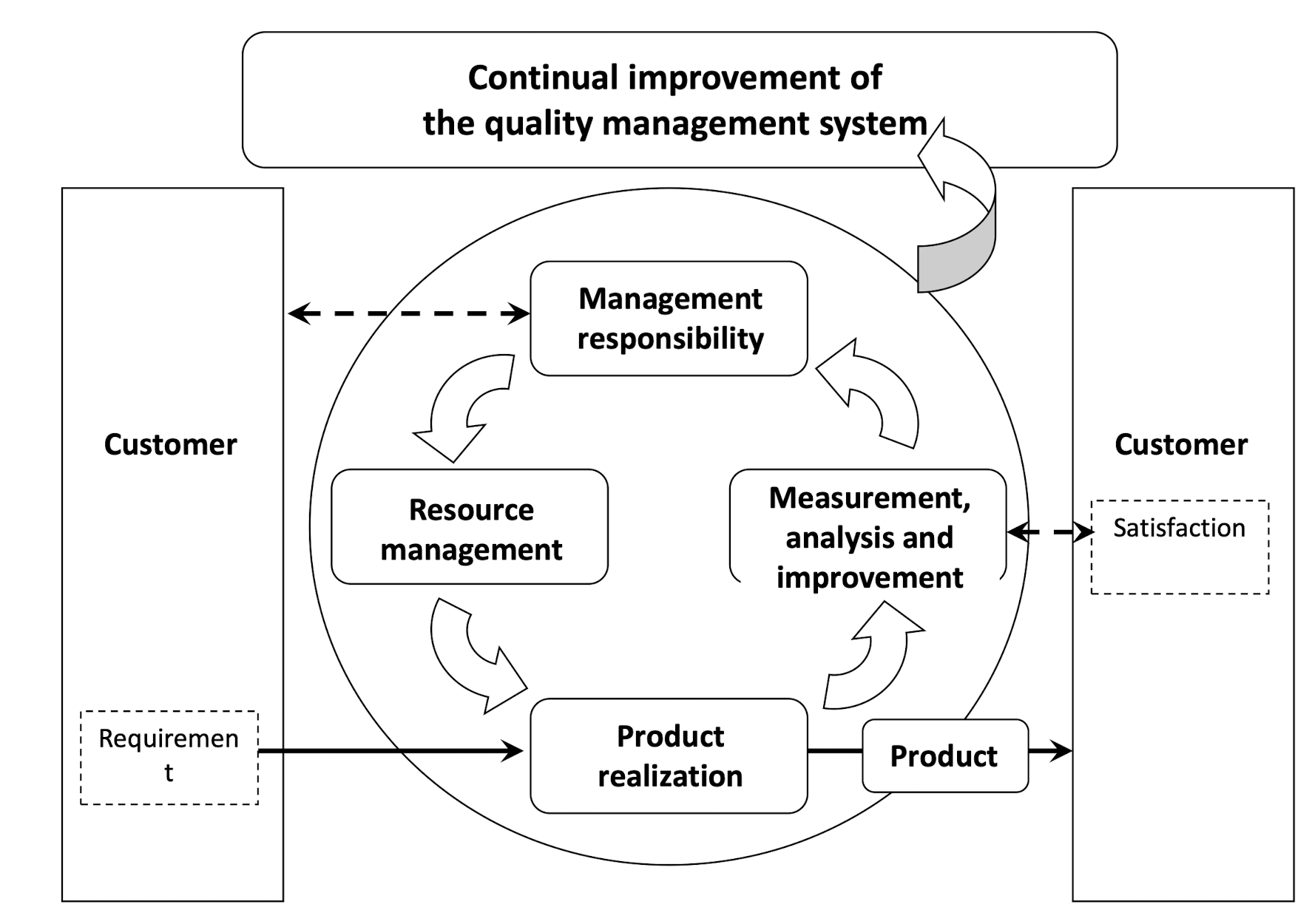
3.13 What is Quality Management System (QMS)?
Based on ISO9000:2005 definition:
- Quality means degree to which a set of inherent characteristics fulfils requirements;
- Management means coordinated activities to direct and control an organization;
- System means a set of interrelated or interacting elements; and so
- Quality Management System is a management system to direct and control an organization with regard to quality.
3.14 Eight quality management principles
- “Customer focus”
- “Leadership”
- “Involvement of people”
- “Process approach”
- “Systems approach to management” (To be removed in ISO 9001:2015)
- “Continual improvement”
- “Factual approach to decision making”
- “Mutually beneficial supplier relationships”.
3.14.1 Quality Management System Model
3.15 ISO 27001 in the World
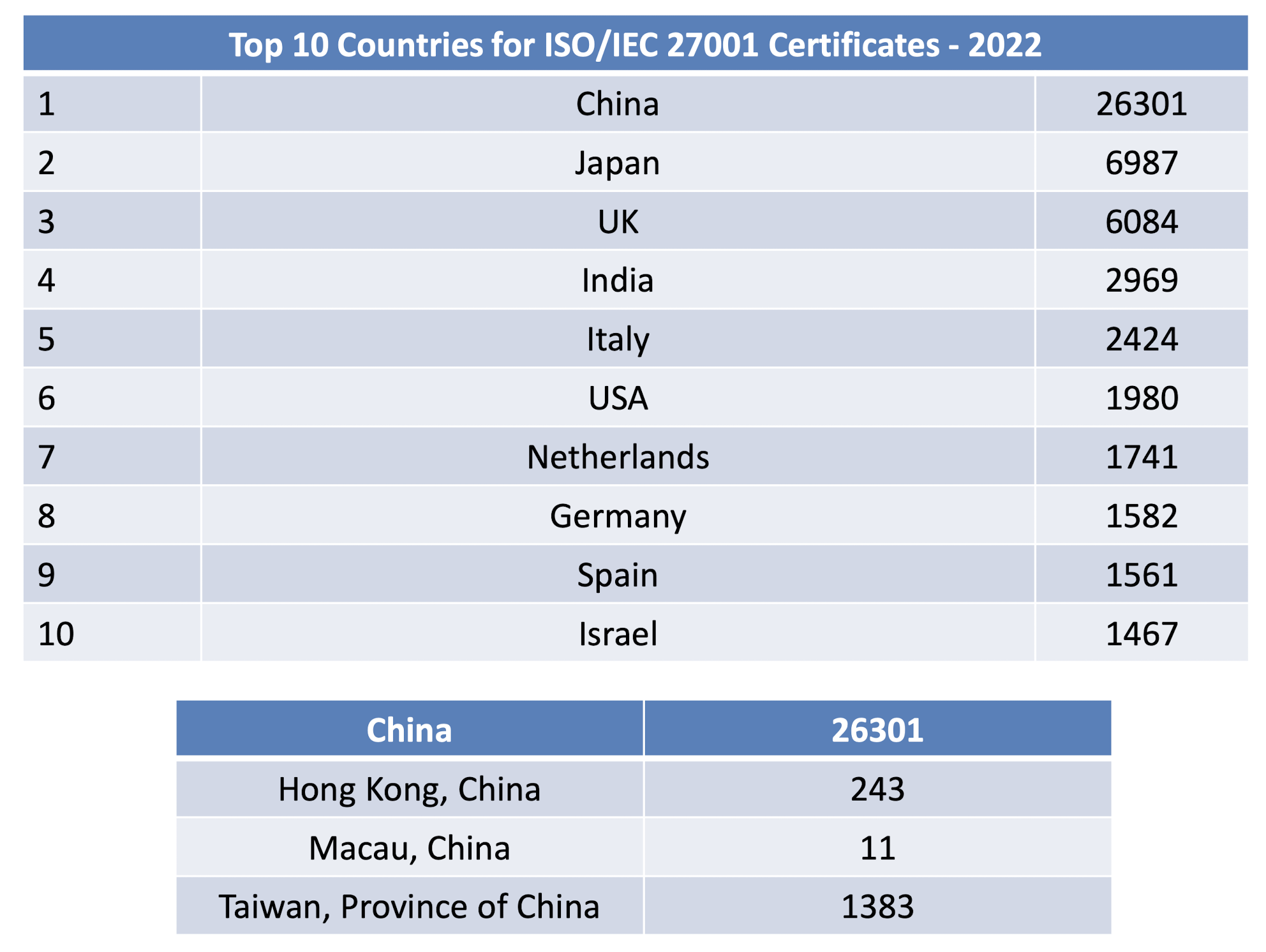
3.16 Barriers of ISO 27001 ISMS Implementation
- no details of risk assessment and management methodology,
- no details of safeguards selection criteria, and
- no further elaboration of the steps in the implementation roadmap, as well as,
- implementation is costly (Fung, 2004; Hong et al ., 2003; Fomin et al. , 2007, Chien et al. , 2007 and Ku et al. , 2009).
- Therefore, how to implement ISO 27001 in an effective and efficient way will be essential in Hong Kong. It forms the basis of the motivation for this project.
3.17 Scope Diagram of QISM Implementation Model
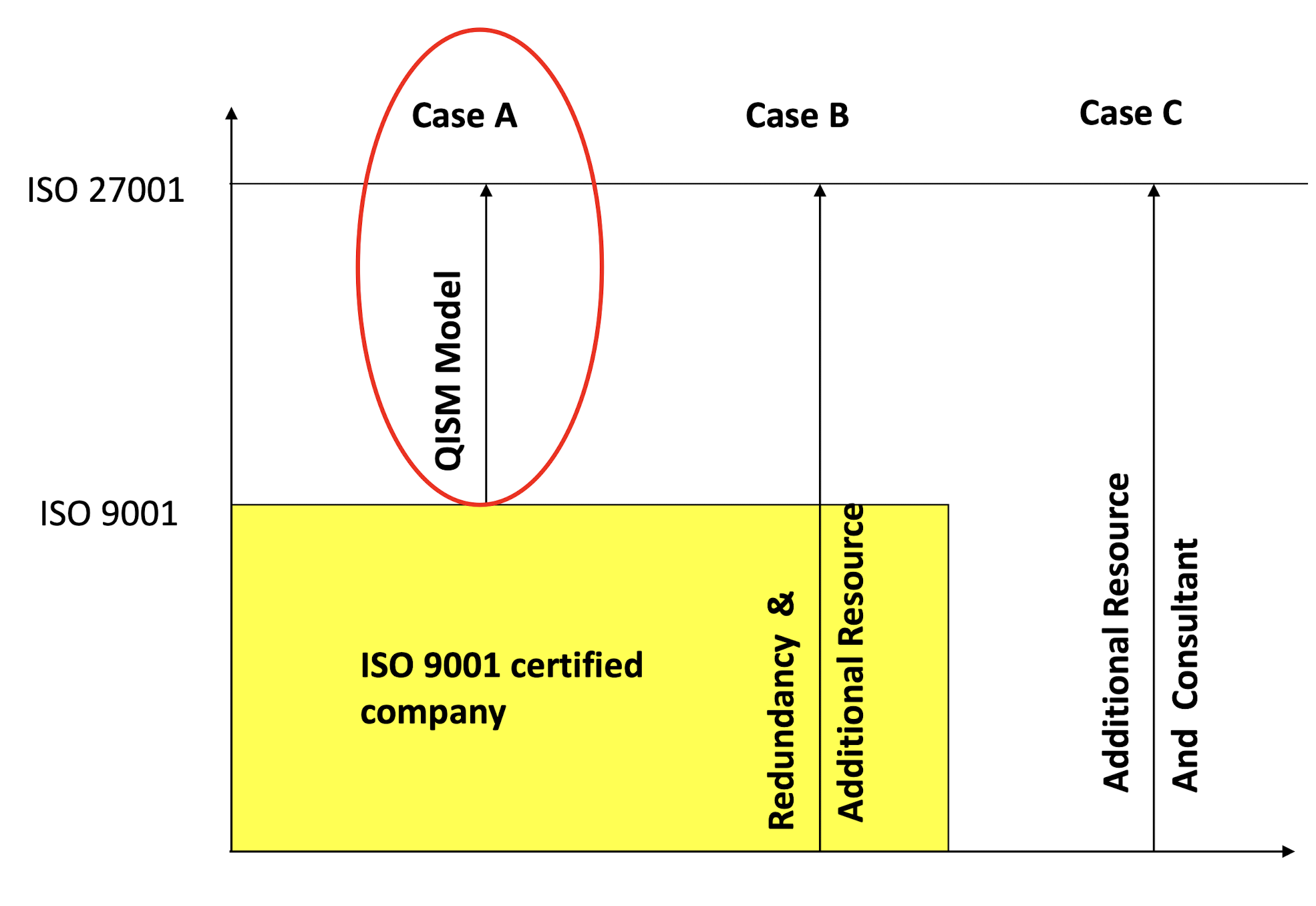
3.18 QMS based Information Security Management (QISM) approach
- Baker & Wallace (2007) pointed out organizations must realize that a large proportion of information security incidents extend far beyond technology (technical controls).
- Management controls should be taken to improve the quality of security policy.
- Novak (2005) commented positive influence of QMS on ISMS.
- ISO 9001 successful experiences (including availability of documents, cost constraints, organization learning and organizational culture) were important motivation of self-implementation of ISO 27001 ISMS. (Barlette, 2008 & Ku et al, 2009)
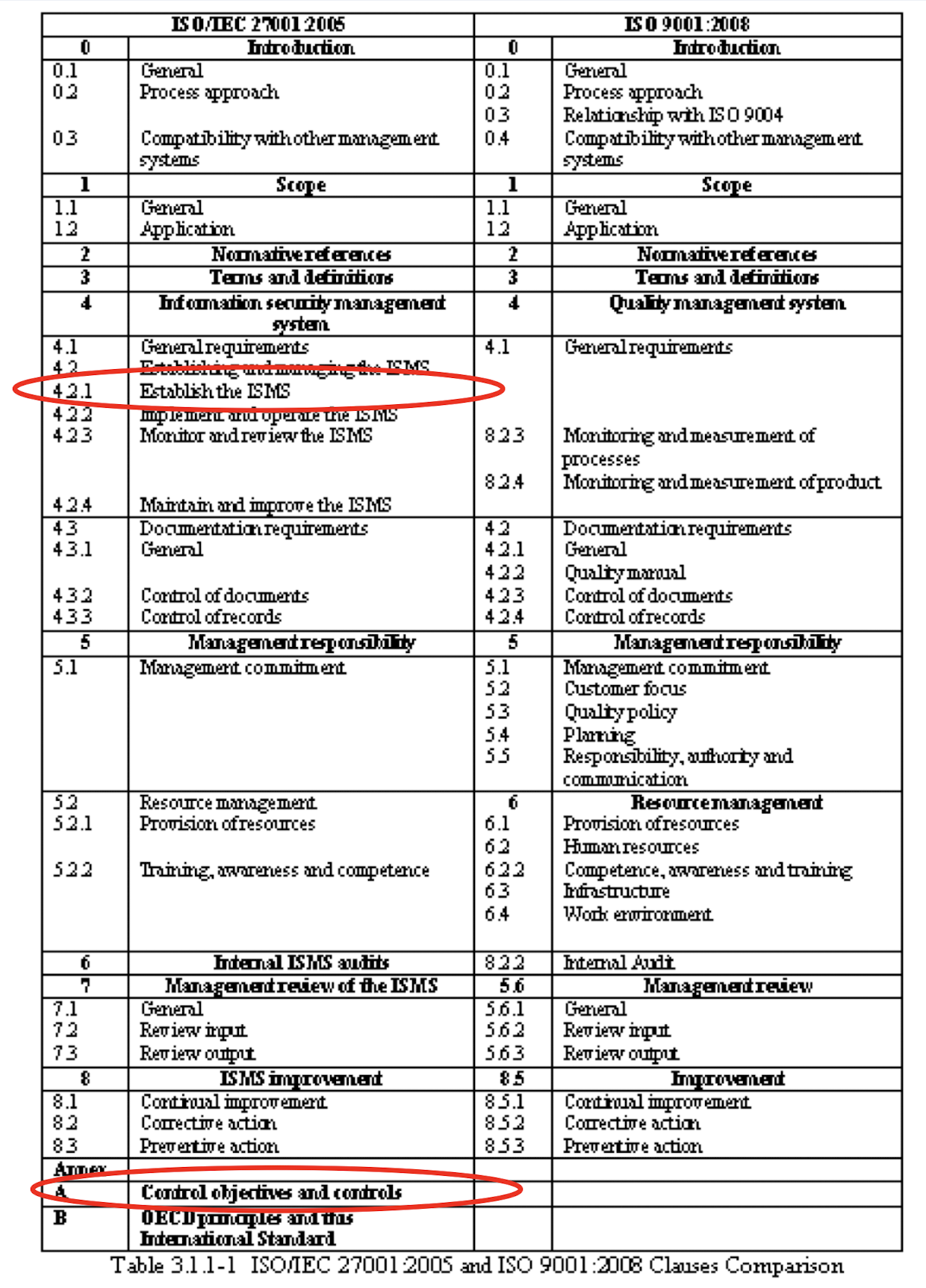
3.19 Comparison of ISO
- About 90% of the management system requirements are found to be compatible with each other.
- The two major differences between ISO 27001 and ISO 9001 are shown as follows.
- risk assessment methodology in Clause 4.2.1
- “Annex A - Control Objectives and Controls”: 133 Controls are specified.
3.19.1 Five Control Objective Group
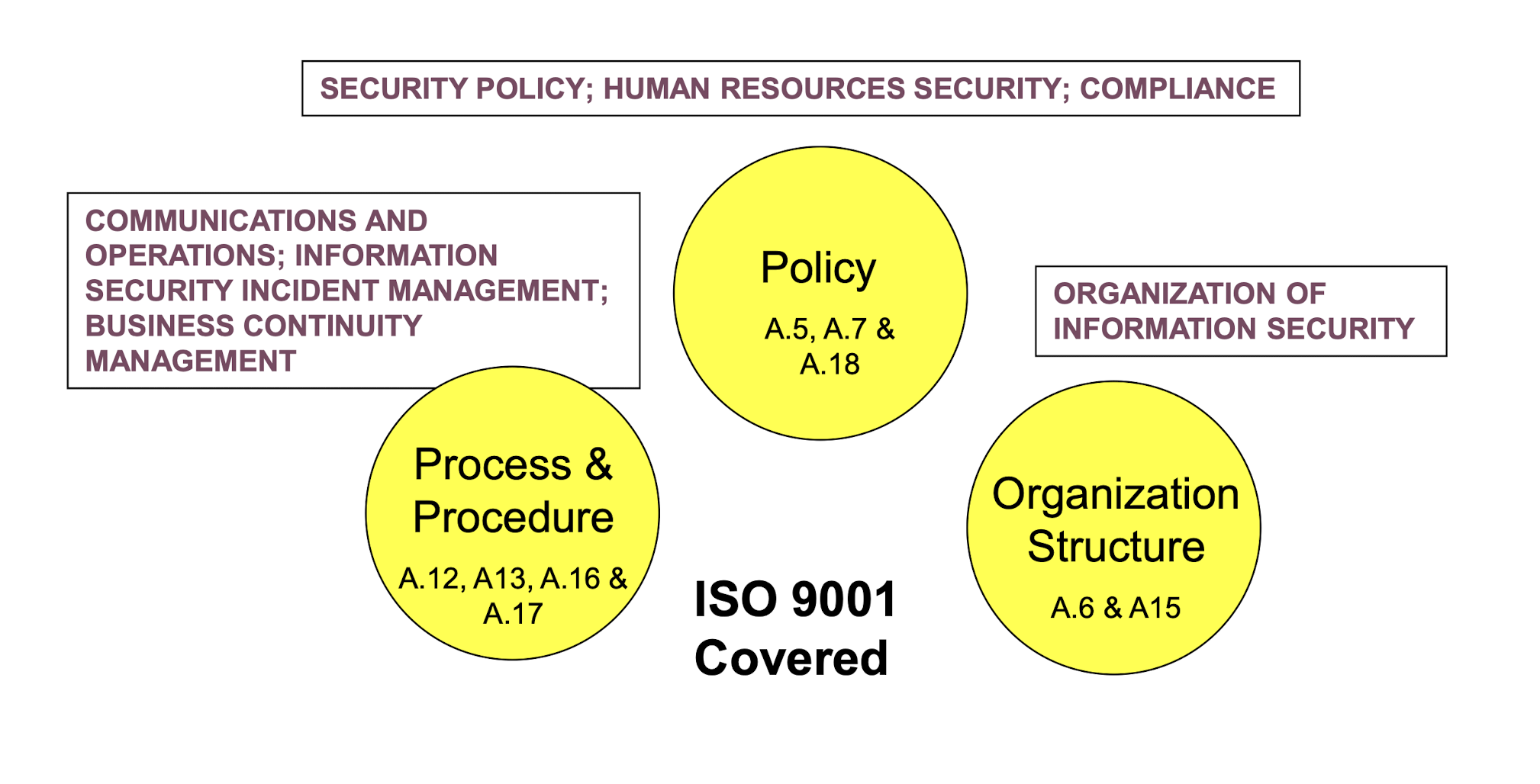
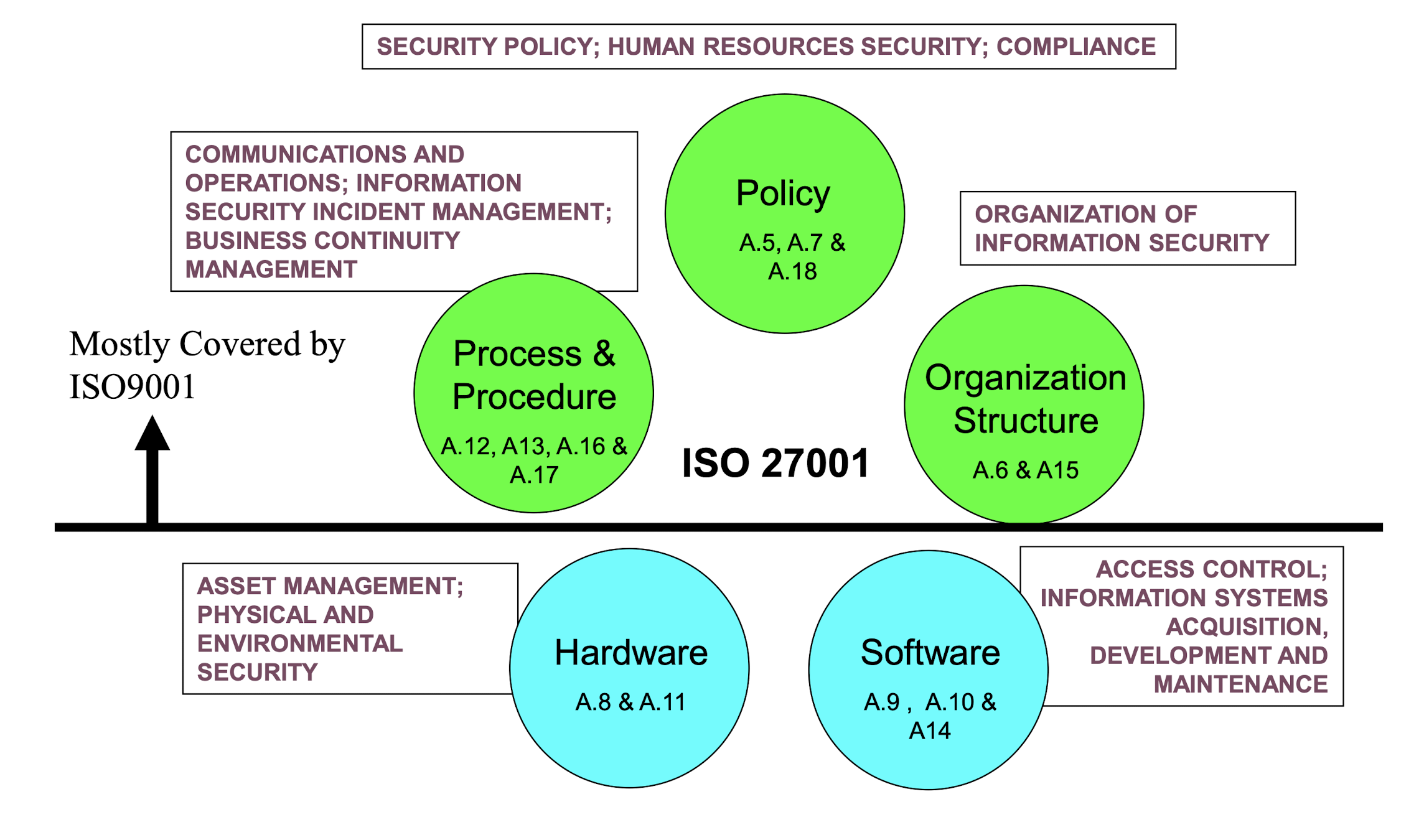
3.20 Literature Review Summary
- Fomin et al. (2008) stated the high costs in money and time of ISMS implementation are definite barriers for smaller size companies to adopt the standard. (QISM model is used to implement ISO 27001 for the existing ISO 9001 certified company.)
- A quantitative FMEA-based risk assessment tools was selected.
- TQM stepwise approach was adopted to overcome ISMS implementation deficiency to development the implementation roadmap.
- FMEA: Failure Mode and Effects Analysis
3.21 QISM Implementation Model Development
- The first objective of this study aims to develop QMS based Information Security Management (QISM) Model for assisting ISO 9001 certified companies to implement ISO 27001 ISMS.
- Development of the QISM model is divided into 4 steps
- Step 1: Review quality management system model and extract the core elements
- Step 2: Review information security management system model and combine its core elements with those in the QMS model
- Step 3: Review security element relationships (SER) model and develop conceptual security model framework
- Step 4: Combine all elements to form QISM model
Step 1: Review Quality Management System Model & Extract the Core Elements
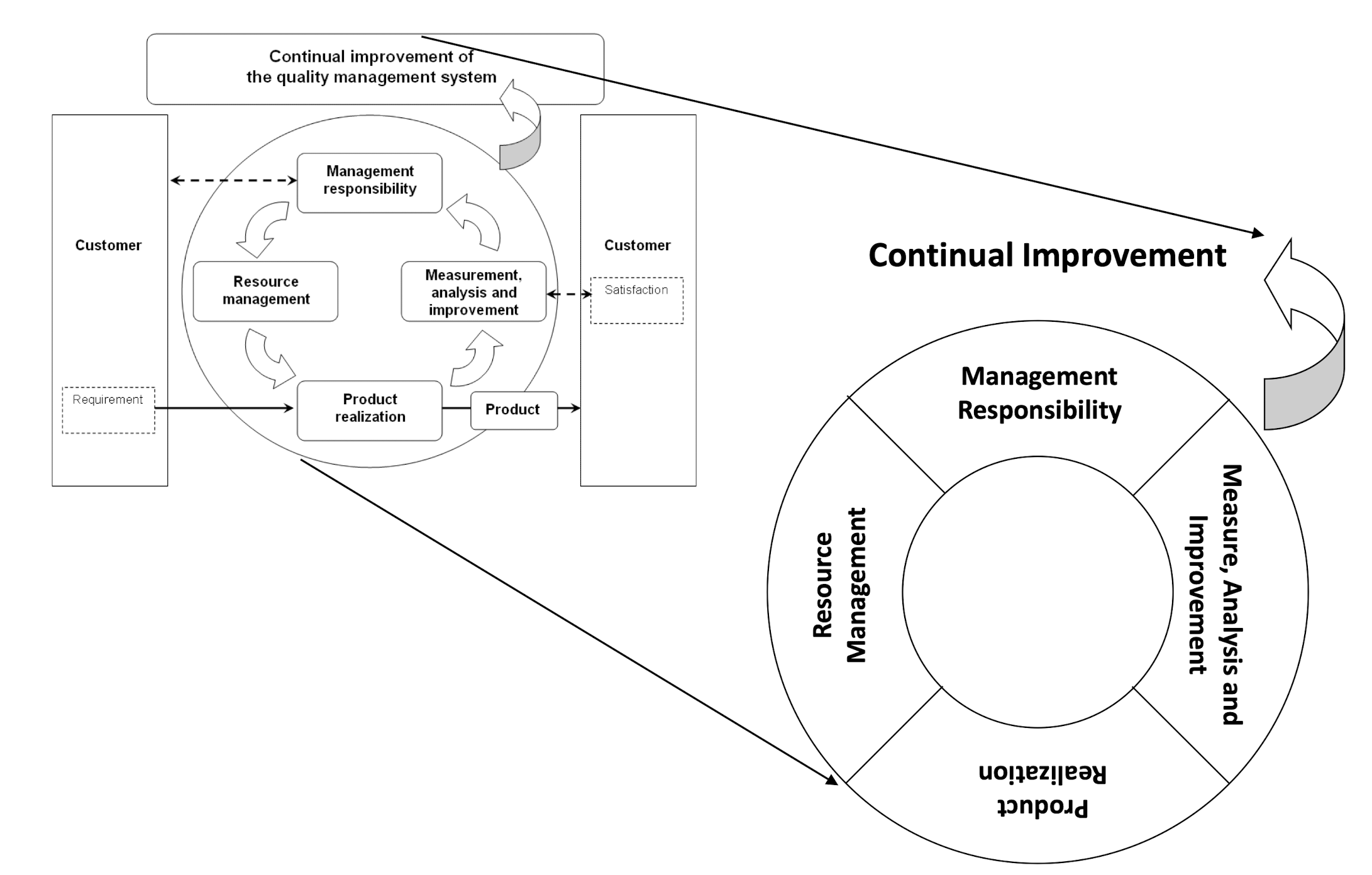
Step 2: Review ISMS Model & Combine its Core Elements with those in the QMS Model
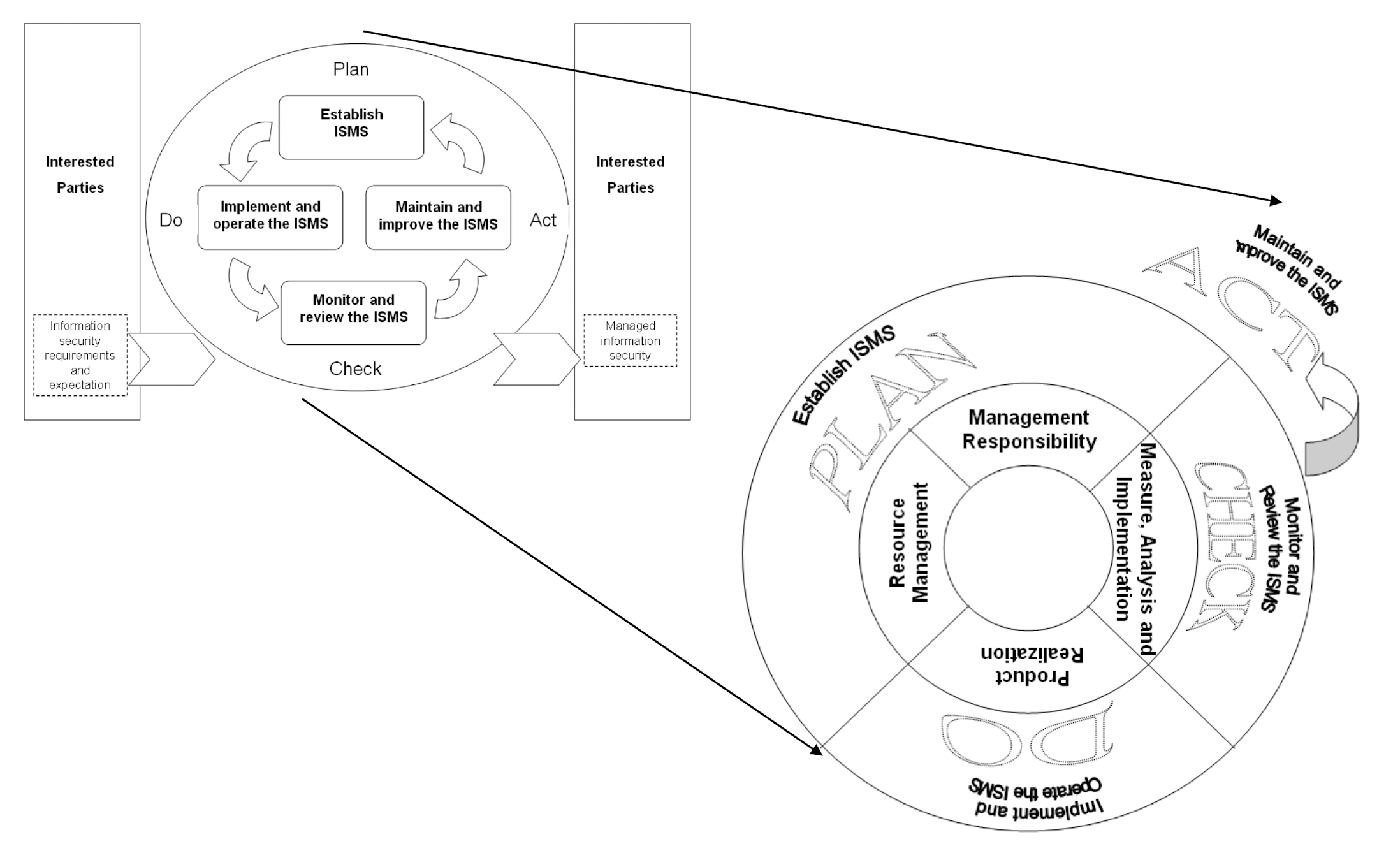
Step 3: Review Security Element Relationships Model & Develop Conceptual Security Model Framework
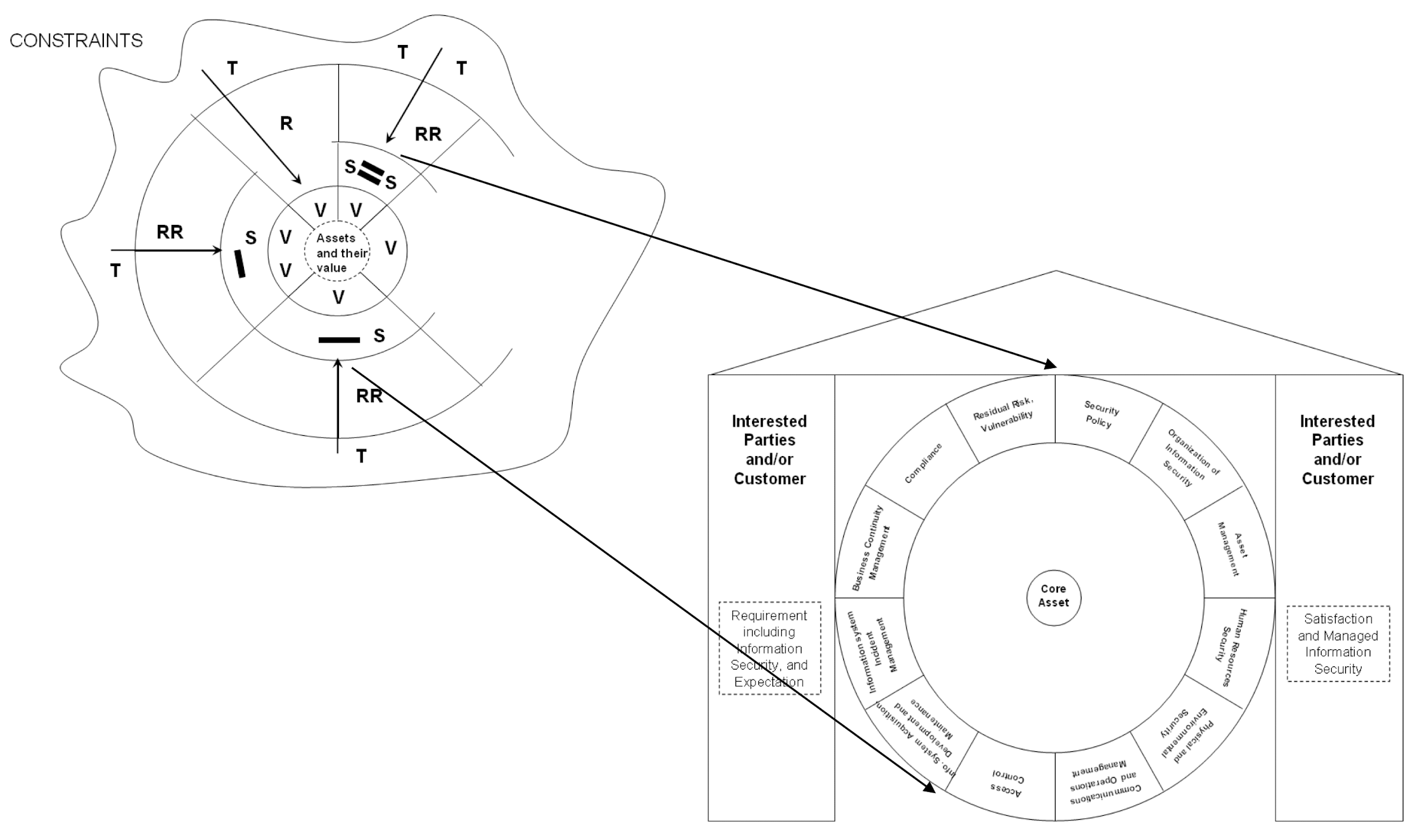
Step 4: Combine all Elements to form QISM Model
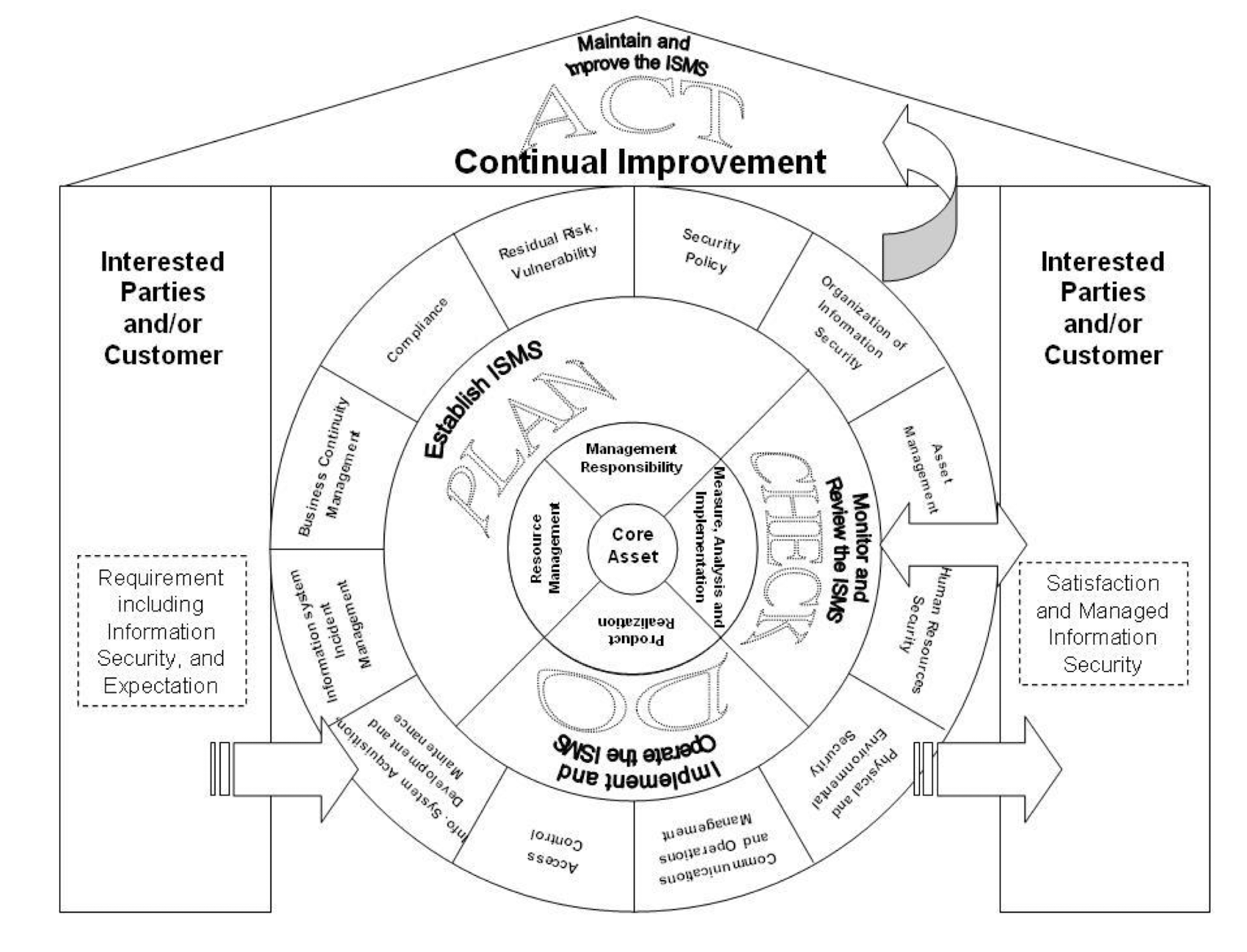
3.22 Information Security FMEA-based Risk Assessment Process
- Information Security FMEA (InfoSec FMEA) Circle is formulated by combining:
- PDCA (ISO 9001:2008, ISO 27001:2005),
- Risk Management Process (AS/NZS 4360:1999, ISO 27005:2008, ISO 31000:2009), and
- FMEA (IEC 60812)
- The development of “InfoSec FMEA Circle” can provide solutions to overcome the insufficiencies of FMEA stated by different scholars (Chin et al. , 2009; Chin et al. , 2008; Wang et al., 2009 Ahsen, 2008; Segismundo & Miguel, 2008; IEC 60812:2006)
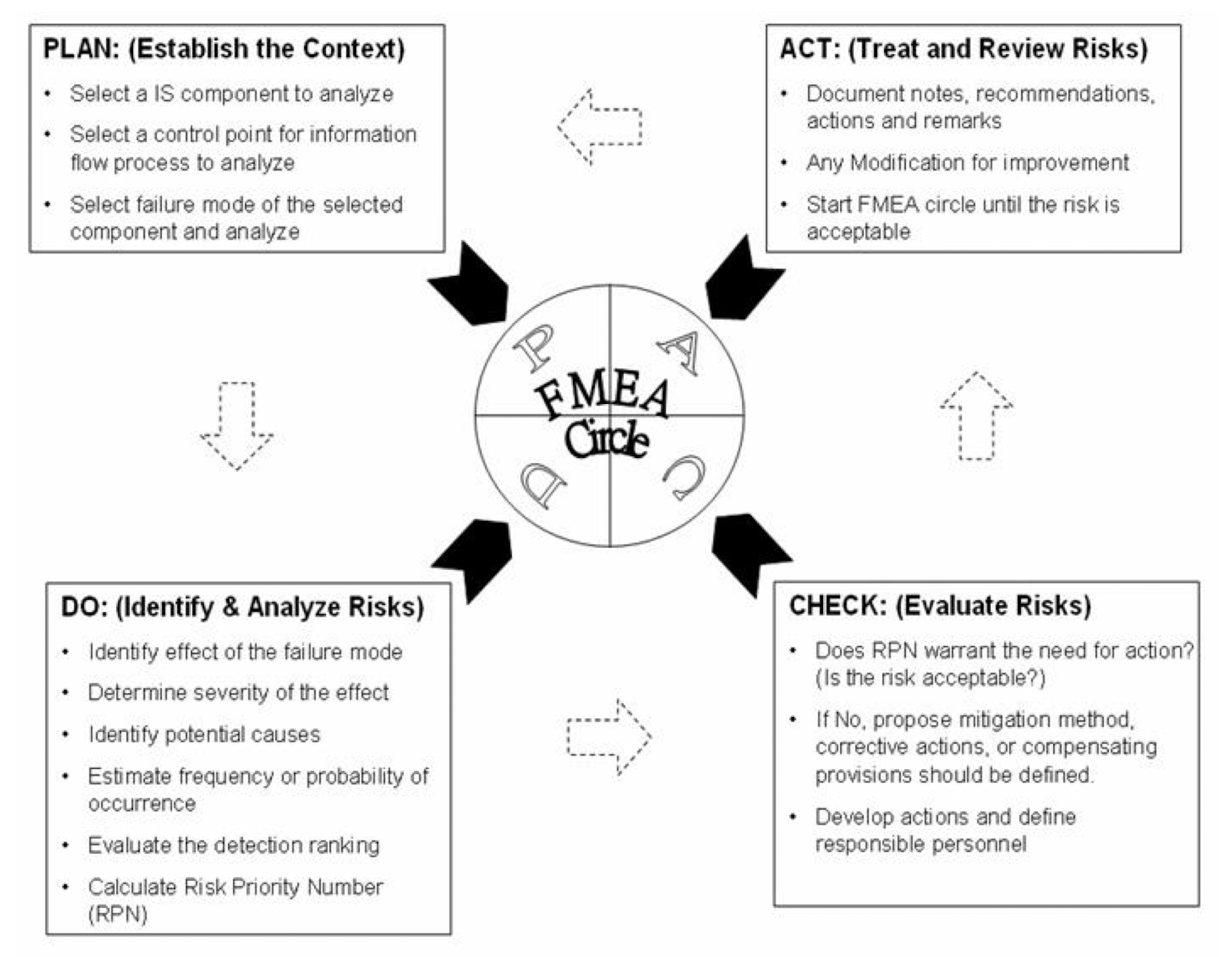
3.22.1 InfoSec FMEA Circle
3.22.2 PDCA Framework (I)
- STEP 1: Plan (Establish the Context)
- Selection of Information Security Component for analysis
- Selection of Control Point for Information Flow Processes
- Selection of the Potential Failure Mode on the Selected Control Points / Processes
- STEP 2: Do (Identify & Analyze Risks)
- Identification of the Effect of the Potential Failure Mode
- Determination of the “Severity” of the Effect on each Potential Failure Mode
- Identification of the Potential Clause
- Estimation of the Frequency or the Probability of Occurrence of each Potential Failure Mode
- Evaluating the ability to detect a Potential Failure Mode
- Calculation of the Risk Priority Number (RPN)
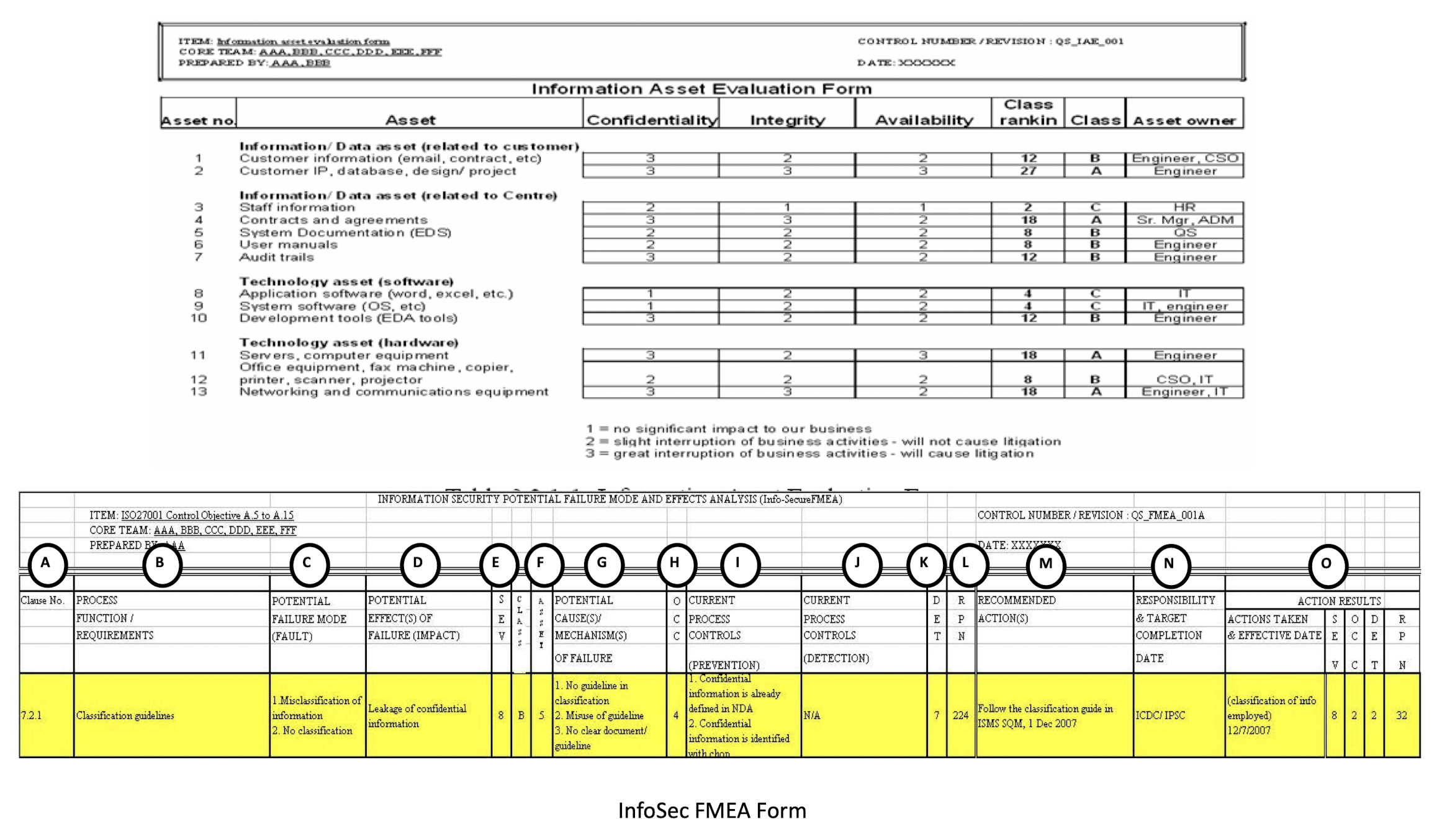
3.22.3 Information Asset Evaluation
3.22.4 Calculation of Risk Priority Number (RPN)
- Risk Priority Number (RPN) is the product of Severity (S), Occurrence (O) and Detection (D) rankings (See Table 3.2.1- 2 - Item L).
- RPN = Severity (S) x Occurrence (O) x Detectability (D) …………….(Eq.1)
- RPN is calculated for each potential failure mode and the most important failure mode with the highest RPN number can be subsequently found.
3.22.5 PDCA Framework (II)
- STEP 3: Check (Evaluated Risks to be accepted or not)
- There are two decisions to be made based on RPN level. They are shown as follows.
- If RPN > acceptable risk level, recommended actions should be performed for control purpose; If RPN < acceptable risk level, management needs to acknowledge the risks and accepts them (See Table 3.2.1- 2 - Item M).
- If RPN > acceptable risk level but cost is too high to avoid it, some structural change may be required to mitigate them for keeping the cost acceptable.
- The highest score of RPN is 1000 (10x10x10) and the acceptable level of RPN is set to 100 (means 10%).
- STEP 4: Act (Treat and Review Risks)
- After rating each potential failure mode based on RPN, any items which were over the risk acceptance level (larger than 100) were used to establish a Risk Treatment Plan (RTP) for follow-up actions.
- This acceptable risk level of InfoSec FMEA circle is part of the continual improvement process.
3.22.6 Implementation of InfoSec FMEA circle
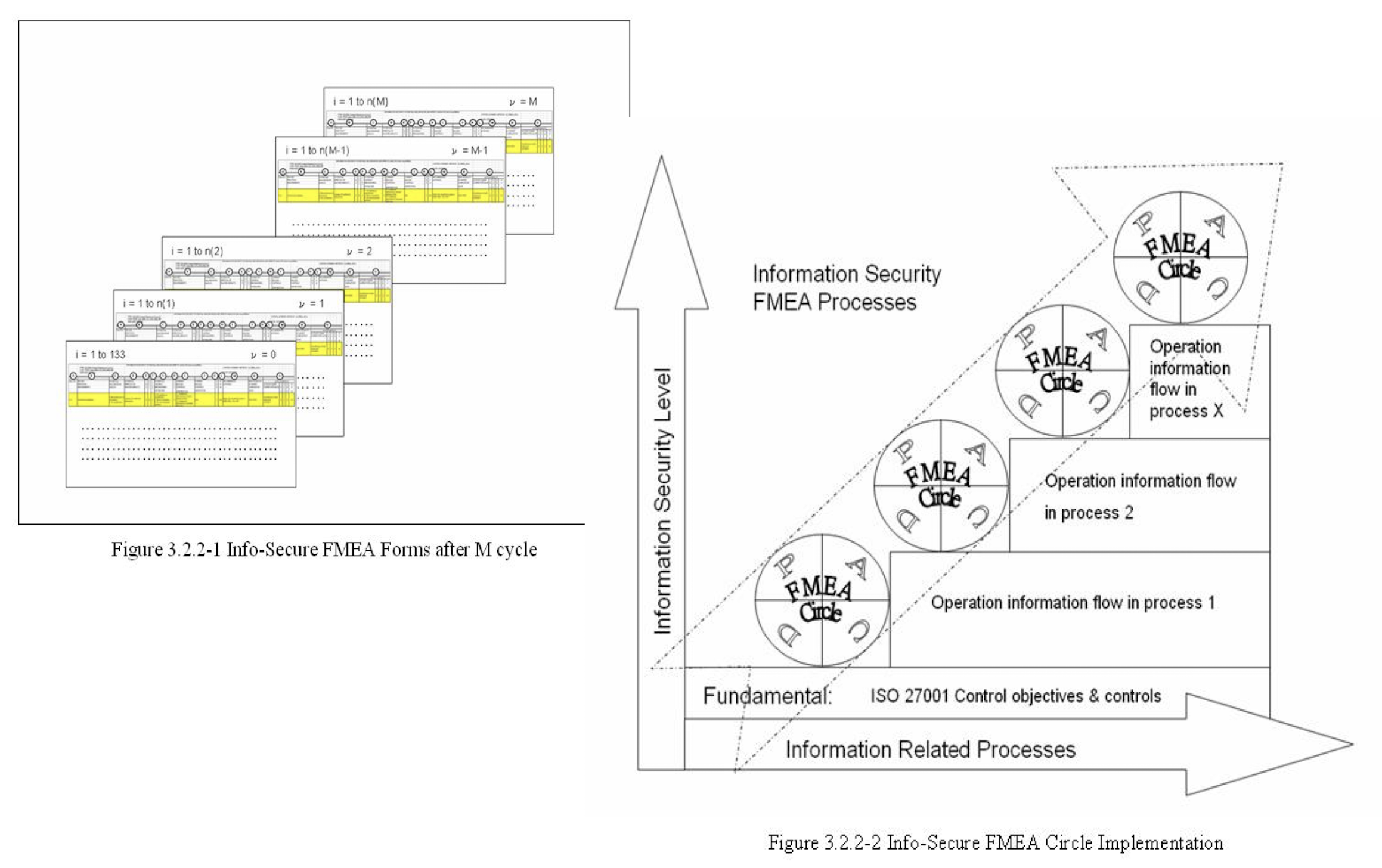
3.23 QISM Implementation Roadmap
QISM Implementation Roadmap is an implementation guideline for ISO 9001 certified companies to implement ISO 27001 management systems.
24-step guideline was developed to facilitate QMS based Information Security Management (QISM) adoption through the Awareness-Preparation-Implementation phases.
3.23.1 Reference to TQM Roadmap
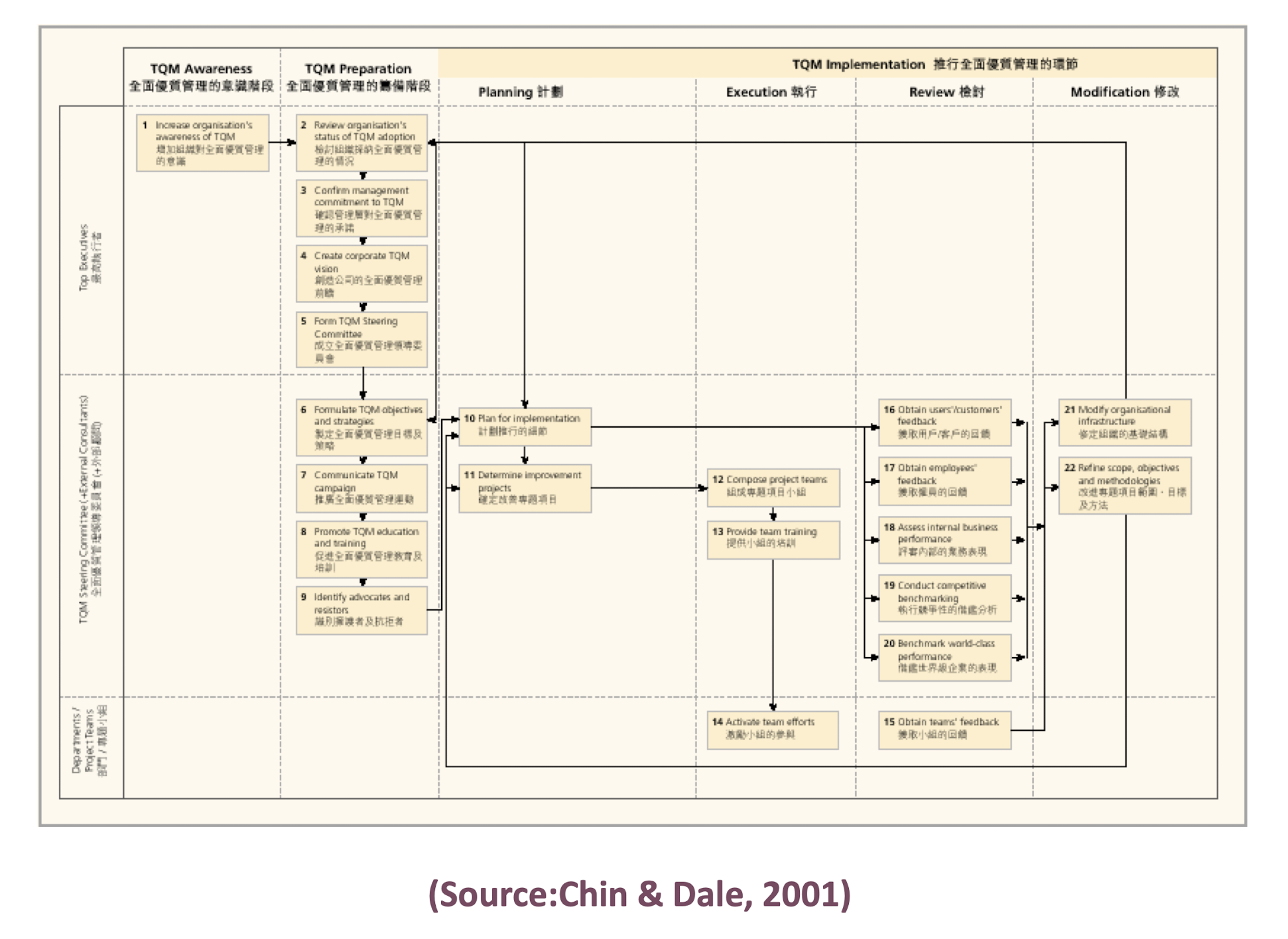
(Source:Chin & Dale, 2001)
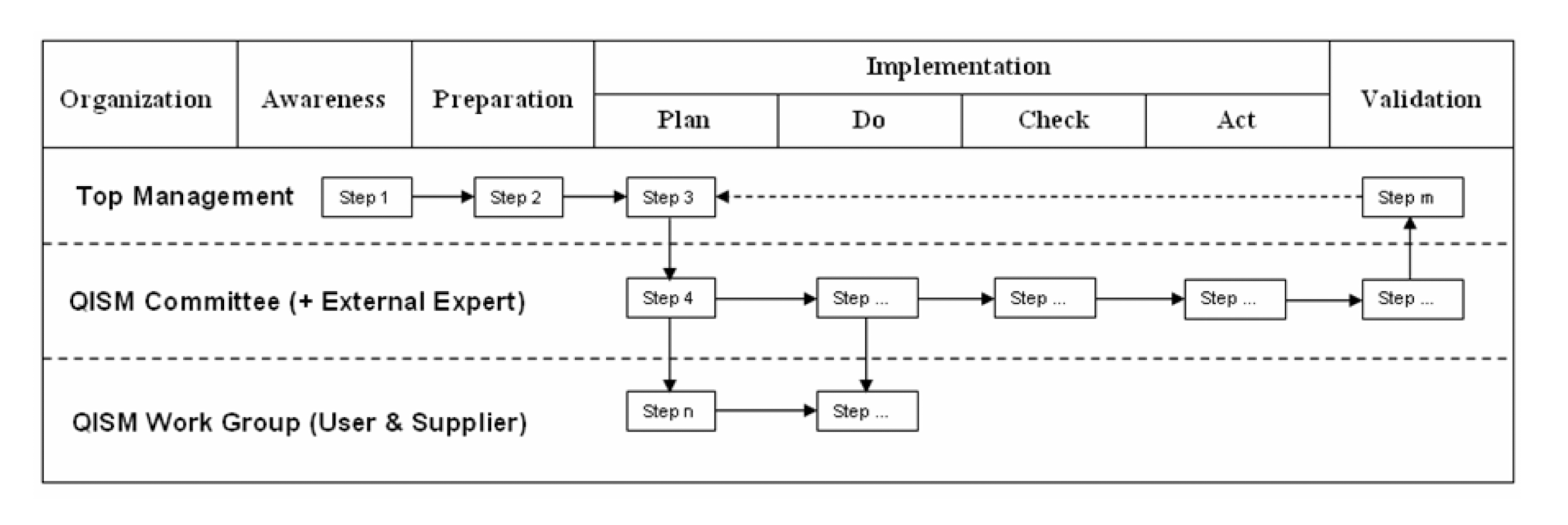
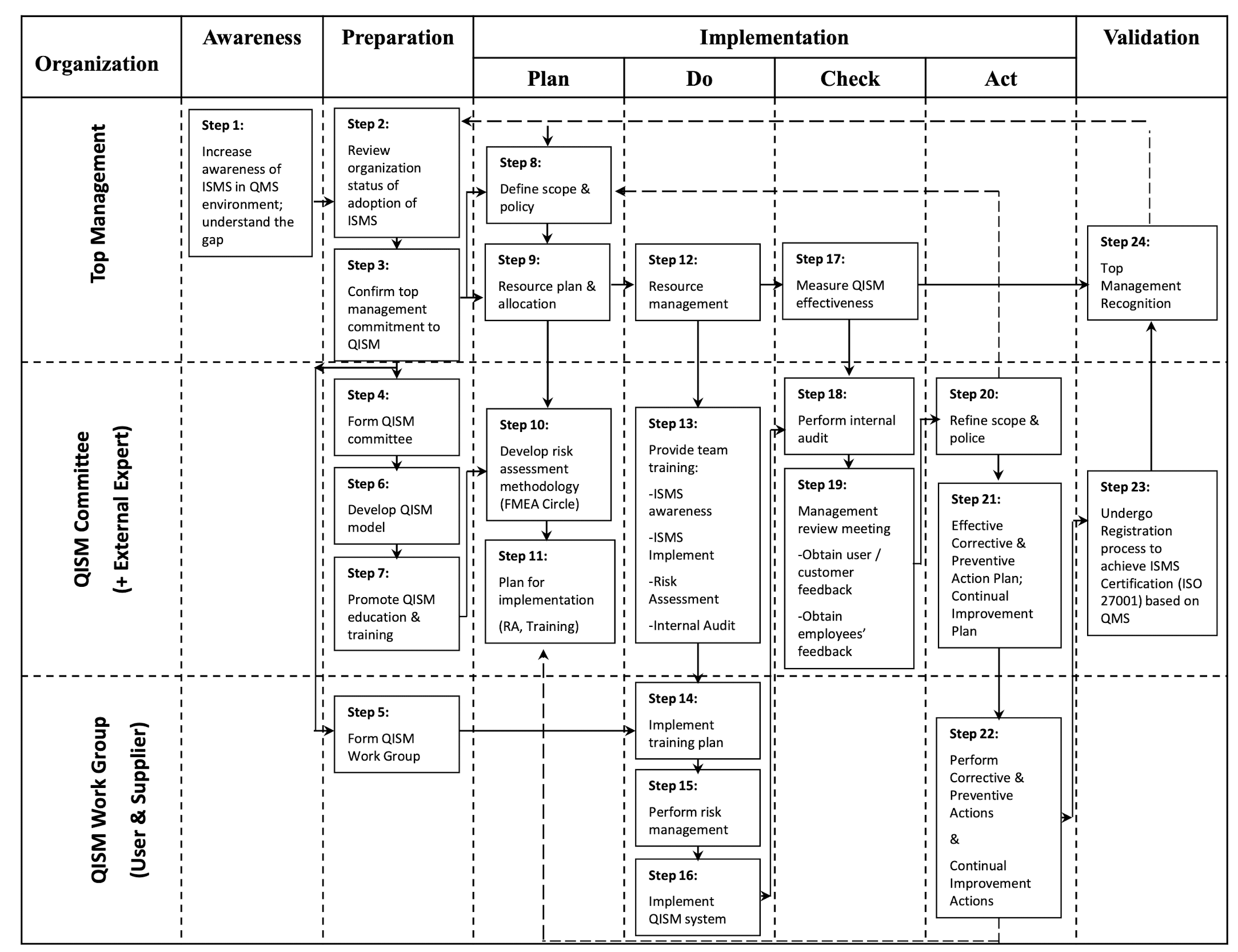
3.23.2 A 24-step Implementation Guideline of QISM Roadmap
- Throughout the execution of QISM implementation roadmap, top management, QISM committee members, work group members, users, suppliers, as well as external experts, as appropriate, were involved.
3.24 HKSTP Case Study
3.24.1 Information Security Incident
Description of the Security Incident
- A company “SkiYYY.com” reported that they received a DDoS attack from our IP ( 202 .XX.xxx.YYY) on 11 May 201 X (at HK time 2 : 55 PM, Saturday) and sent email to PCCW (ISP) on 12 May 201 X (at HK time 8 : 10 PM, Sunday). Our FTP server was placed in Data Centre (Unit 30 X, 3 /F., IT Centre) which was managed by T engineer.
- We received PCCW email alert on 13 May 201 X at 2 : 31 PM and informed Lab Manager and IT Security Officer at 3 : 46 PM
- T engineer investigation and owner identification, IT Security Officer decided to escalate the incident to Sr. Manager of Lab and seek Corp IT specialist for advice and assistant on 14 May 201 X at 4 : 35 PM. Corp IT advice was received at 6 : 40 PM.
- Finally, the incident was escalated to VP on 15 May 201 X at 10 : 00 am.
3.24.2 Information Security Incident
Correction
1) T engineer investigate the problem with PCCW staff on 13 May 201 X
2) T engineer corrected software holes in the morning on 14 May 201 X and IT security officer decided to disconnect the physical network at afternoon on 14 May 201 X.
3) Check outbound and inbound traffic through PCCW (ISP) on 15 May 201 X.
4) IT Security Officer registered the case to Hong Kong Police on 16 May 201 X.
5) The PO for Forensics Analysis Service was issued on 30 May 201 X. And awarded vendor (JOS / e-Cop) performed the investigation on 3 Jun 201 X.
Details action by T Engineer :
- Remote login to the FTP server, and stopped the SNMP service (by 14 May morning)
- Unplugged the network from the FTP server (by 14 May afternoon)
- Tried to login to the FTP server on console but failed. Rebooted the FTP server (by 15 May morning). Checked the message log files and noticed the SNMP DDoS attacks from other internet machines started from early May 201 X (most recent).
- Login to the FTP server on console. Checked the customer folders/files (by 16 May).
3.25 Conclusion
- In this investigation, based on the vulnerability scanning result and review system logs contents that any critical security loop-hole and evidence unauthorized break- in by other party is not possible. There is no evidence that any information leakage or deletion on customers’ data.
- A Simple Network Management Protocol (SNMP) reflection/amplification attack is a distributed denial of service (DDoS) technique that is very common on Internet but can be avoid if proper protection in-place such as firewall.
- However, there are some deficiencies on the FTP Server and the Internet firewall, of which there are rooms for improvement.
3.26 Recommendations (I)
Firewall Security
- Reviewing and reconfiguring the Internet firewall policies by industrial best practices;
- Block any external connection but allowed service/services only on ingress/inbound traffic;
- Block or control egress/outbound traffic on external interface;
- Assess traffic to any policy if necessary;
- Periodically review firewall policy;
- All systems and servers shall be protected by firewall;
- Firewall logs should be recorded and periodical review by the security team.
Servers and Systems
- Critical systems must be added to patch management policies avoid organizations risk costly compromises.
- Unnecessary services shall be turned off ; only authorized services running on the system;
- Perform security risk assessment on new system before launch to public;
- Production servers and workstations should apply update patches in a timely manners ;
- System logs should be recorded and periodical review by Lab team.
Password Policy
- Vendor-supplied defaults password shall be changed before deploy system to production;
- Enforcing strong password usage throughout the organization
3.27 Conclusion
“ SECURE “ is the Key to implement Information Security Management System.
“ S “ - Standardization
- by IT Security Policy, Organization Structure, Manual and SOA.
“ E “ - Effectiveness
- by Process & Procedure
“ C “ - Clearance
- clean database / user account record / review regularly and systematically
“ U “ - Unique Identification
- Unique identity of each authorized user for traceability
“ R “ - Recovery
- Disaster Recovery Site & Business Continuity Plan
“ E “ - Efficiency
- Sustainable discipline, continuous improvement
3.28 Cost of Information Security (InfoSec)
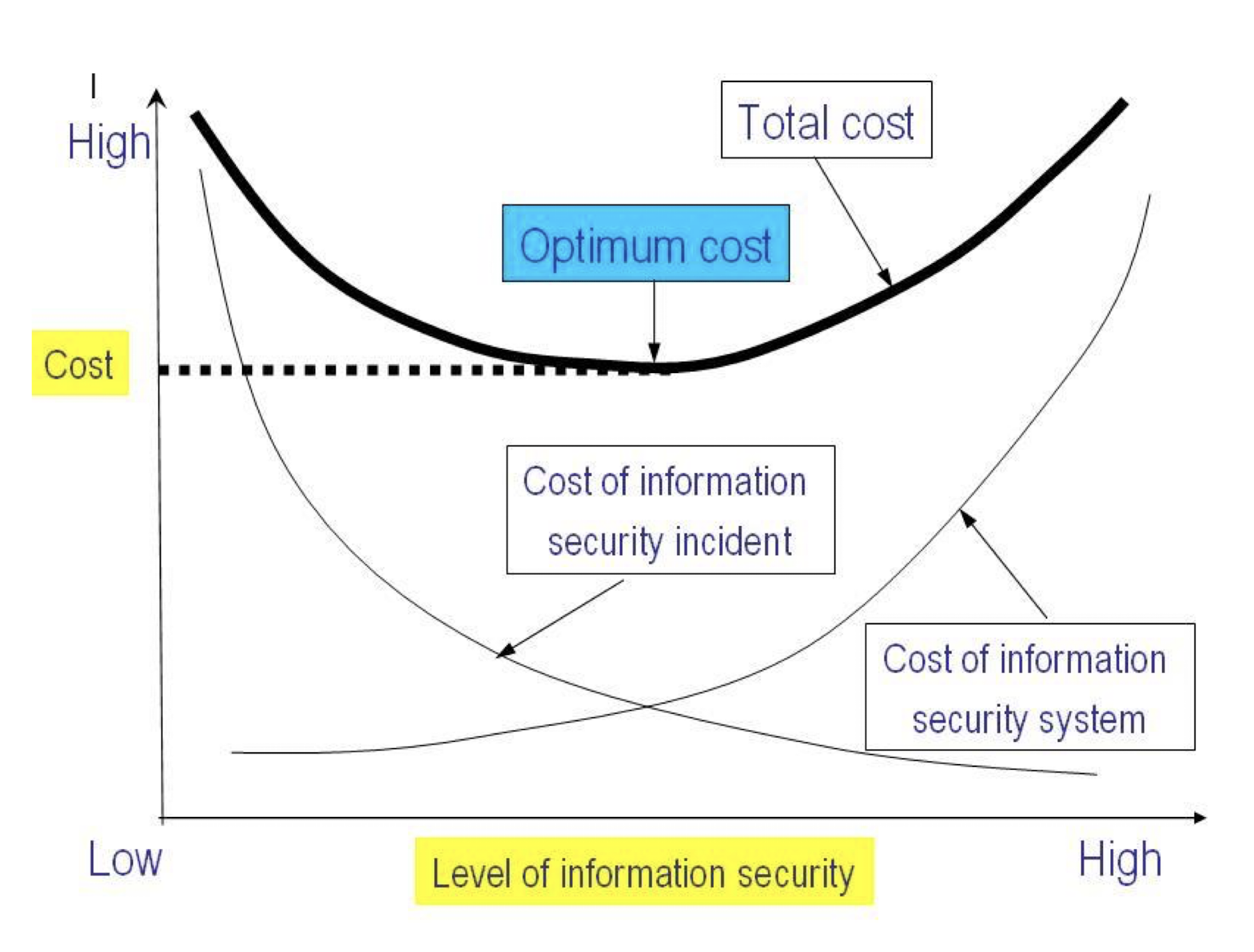
4 AI Ethics
4.1 What is AI?
4.1.1 Three key factors enable AI success
4.1.2 Artificial Intelligence vs Human Intelligence
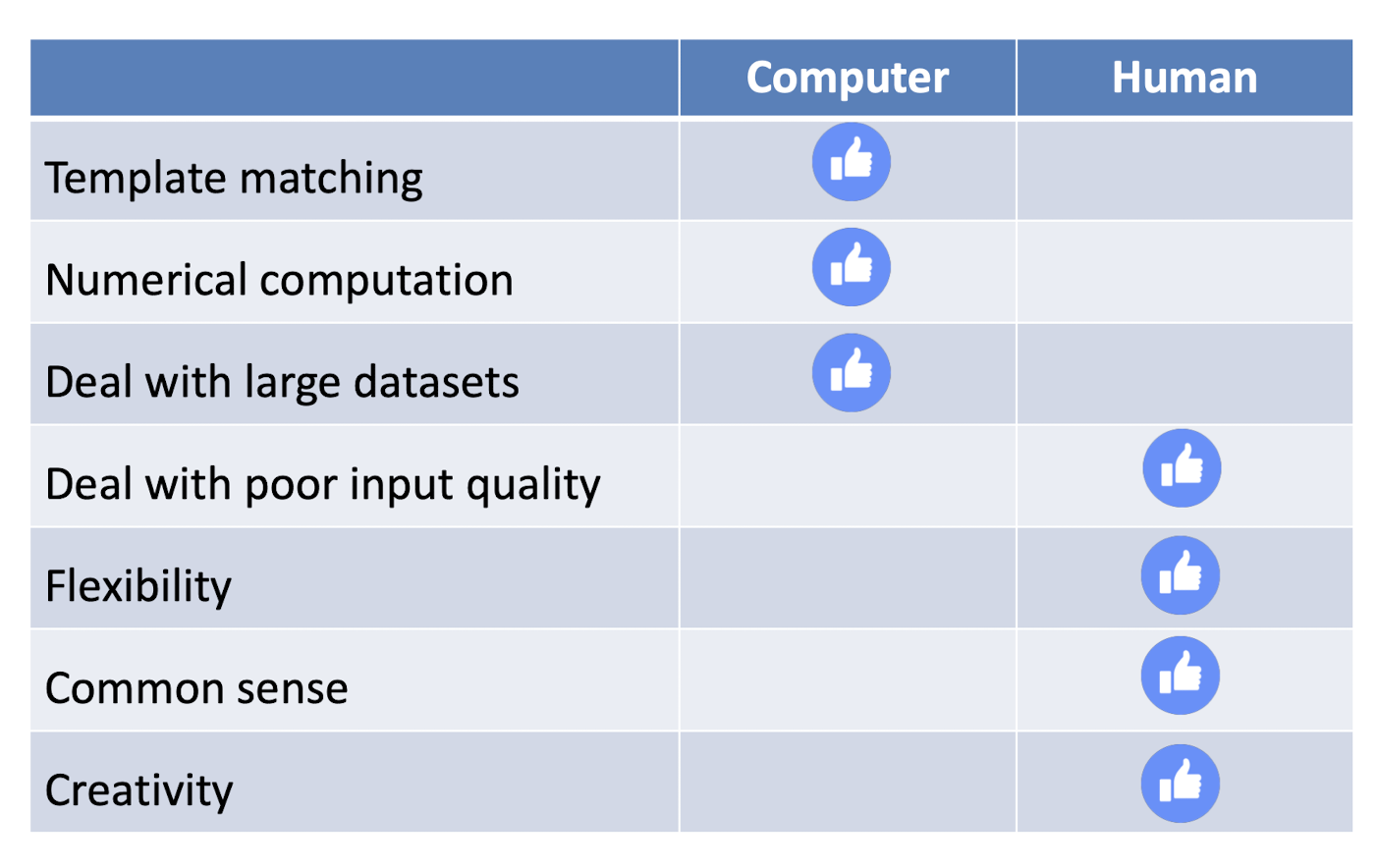
4.1.3 Some Useful Terms about AI
Weak AI: the attempt to build programmes that demonstrate capabilities of intelligence, without necessarily being ‘intelligent’ themselves.
Strong AI: the attempt to build programmes that have intelligence in the form of understanding and/or that are conscious.
Artificial General Intelligence (AGI): the attempt to build programmes that demonstrate the full range of intelligence capabilities exhibited by human beings.
Superintelligence: a notion of artificial intelligence that vastly exceeds human intelligence and hence may be hard or impossible for us to understand. Superintelligent AI is presumed capable of recursive self-improvement and of the creation of technologies of greater and greater intelligence.
4.2 AI Ethics and AI Safety
- Safety necessitates ensuring that systems reliably achieve the goals that we wish them to achieve, without unacceptable dangers , including both long-term and short-term risks.
- The complexity of AI means that considerable work is involved in ascertaining and checking safety, much of which is highly technical.
- The ‘Blackbox’ nature of much AI is one cause for particular concerns, resulting in considerable efforts in technical work to ensure as much transparency in systems as possible.
4.2.1 ‘Normal Accidents’ and AI Safety
- Charles Perrow developed a theory of ‘ Normal Accidents ‘ in his book Normal Accidents: Living with High-Risk Technologies (1984) after examining the causes of the Three Mile Island nuclear accident, a partial melt down of a nuclear power station in 1979.
- ‘Normal Accidents’ are inevitable in technological systems which are highly complex and where the interacting elements are tightly coupled, and where the potential for error could be catastrophic.
- The role of organizations surrounding technologies in creating and mitigating risk is emphasized.
- Perrow’s theory has been influential in contributing to understandings of safety and risk in technological systems. It has been claimed that AI systems are prone to ‘normal accidents’.
- This illustrate show tightly connected are technical safety issues to questions of regulation and organization which involve human elements, judgements of value, and ethics.
4.2.2 Ethics, Action and Application
Ethics is strongly linked to action.
On some philosophical views, the making of a moral judgement , the appreciation of what is the best thing to do, leads immediately to such action, although a view more commonly held is now that the motivation to act morally arises with a degree of independence from judgement.
If ethics is purely theoretical, it seems to lack a central aspect.
Suggested by Virginia Dignum, a computer scientist who has worked extensively in AI ethics, that talk of ethics focuses too much on the theory of what should be done, rather than on its implementation , and that it would be better to focus on the notion of responsibility, to emphasize the need for translation in to practice.
4.2.3 AI Alignment (Human Value)
- AI alignment represents the critical challenge of ensuring that AI systems understand and align with human values and intentions.
- Value Alignment: Programming AI to align with human ethics.
- Inverse Reinforcement Learning: Understanding human preferences.
- Interpretable AI: Models that humans can understand and control. (Not Blackbox!)
- Four methodologies encompass broader strategies:
- Top-Down Approach: Modeling values directly in design
- Bottom-Up Approach: Learning values from human reactions and data.
- Hybrid Approach: Mixing top-down and bottom-up strategies.
- Collaborative Approaches: Ongoing human oversight and collaboration.
4.2.4 General Ethical Concerns Surrounding AI
Highlights general ethical concerns about AI and explores why organizations should care about AI ethics.
How to balance the benefits and risks of AI.
How people have been addressing these problems by using “human-in-the-loop”.
The regulation of human behavior and then examines the challenges involved with regulating the machine behavior.
4.2.5 AI Benefits vs Risks
| Benefits | Risk | |
|---|---|---|
| Better recommendations | Filter bubbles | |
| Safer cars | Fake news | |
| Better medical diagnosis | Unfair matching | |
| Many other benefits |
4.2.6 “Human-in-the-loop”
4.2.7 Concept Review (I)
- Why should businesses care about AI ethics?
Human-in-the-Loop (HITL)
- That operates as part of the systems operation, and monitors it in case it misbehaves, and is able to intervene in such cases.
Society-in-the-Loop (SITL = Human-in-the-Loop (HITL) + Social Contract)
- As HITL oversight over an intelligent system combined with a social contract determines what society would like this system to fulfill.
- Regulating AI systems
- Preconditions to public trust
4.2.8 Autonomous Vehicles
- Case study of the ethics of autonomous vehicles
- Scenario:
- What if an autonomous vehicle’s brakes become inoperable, and the car is heading toward a group of pedestrians who would be killed if the car hit them.
- The car has a choice to swerve and hit only one pedestrian rather than the group.
- Should the car swerve?
- What if the car could swerve and avoid the pedestrians, but would thereby harm the occupant(s) in the car?
- At issue is that a machine would be making a moral decision.
4.2.9 Autonomous driving - German ethics commission
- Legal scholars
- Ethics experts
- Engineers
- Consumer protection groups
- Religious leaders
- They’ve come up with a set of recommendations or guideline for autonomous vehicles.
4.2.10 Review (II)
- Ethical dilemma case study
- “If you could save one person, save the one in the car.” by major car manufacturers.
- The social dilemma
- Adaptation and opacity
- Irrationality around risk
- Public engagement
4.2.11 Asimov’s Three Laws of AI Ethics



4.2.12 Conclusion
AI raises serious ethical concerns, as smart machines will make decisions that may have life-and-death implications.
Many AI system also rely on low-paid workers who labor behind the scenes.
AI has the potential to exacerbate and amplify the negative qualities of humans.
Thus, executives considering adoption of AI systems need to reflect thoughtfully on the ethical aspects of their choices.
4.3 AI Management System (ISO 42001):
4.3.1 WHAT IS ISO/IEC 42001?
With the rise of artificial intelligence (AI), the ISO and IEC have created the ISO/IEC 42001 standard.
It provides a certifiable AI management system (AIMS) framework in which AI systems can be developed and deployed as part of an AI assurance ecosystem.
The goal is to help organizations and society benefit the most from AI while reassuring stakeholders that systems are being developed and used responsibly.
4.3.2 WHY IS ISO/IEC 42001 IMPORTANT?
AI is developing and being adopted rapidly in many industries, products and services.
Undoubtedly, AI is influencing , and will further influence, society and our lives.
Due to this progress and influence, trust, ethics and social concerns must be addressed.
AI must be reliable, fair and transparent - it must be trustworthy.
Because AI systems are complex , implementing an AIMS requires a truly multidisciplinary approach.
Depending on the use case, this may include legal, privacy, operations, marketing, R&D, sales, HR, IT and risk managers.
4.3.3 Key Benefits of AIMS
- Implement AI safely, with evidence of responsibility and accountability
- Consider security, safety, fairness, transparency and data and AI system quality throughout the life cycle
- Show that introducing AI is a strategic decision with clear objectives
- Indicate strong governance concerning AI
- Strike a balance between governance and innovation
- Ensure that AI is used responsibly, especially concerning its continuous learning
- Ensure that all relevant safeguards are in place
- Combine key frameworks with experience to implement crucial processes like risk, life cycle and data quality management
5. Legal Aspect - Privacy & GDPR
- What is Privacy?
- Data Privacy
- Personal Data (Privacy) Ordinance
- ISO/IEC 27701 - Privacy Information Management
5.1 What is Privacy?
5.1.1 Defining Privacy

5.1.2 Privacy and Trust
- Perhaps modern life is actually more private than life centuries ago
- Most people don’t live with extended families
- Automobile allows us to travel alone
- Challenge: we now live among strangers
- Remedy/Correct: establishing reputations
- Test, such as lie detector test or drug test
- Credential, such as driver’s license, key, ID card, college degree
- ==Establishing reputation is done at the cost of reducing privacy==
5.1.3 Few Key Definitions under the PDPO
- The Personal Data (Privacy) Ordinance (the “PDPO”)
- Personal Data means information which relates to a living individual and can be used to identify that individual. It must also exist in a form which access to or processing of is practicable.
- Data Subject is the individual who is the subject of the personal data.
- Data User is a person who, either alone or jointly with other persons, controls the collection, holding, processing or use of personal data.
- Data Processor is a person who processes personal data on behalf of another person (a data user), instead of for his/her own purpose(s). Data processors are not directly regulated under the PDPO. Instead, data users are required to, by contractual or other means, ensure that their data processors meet the applicable requirements of the PDPO.
5.1.4 Data Privacy for Data Users
Microsoft
- Data Minimization
- Data Management
- Notice
- Choice
- Consent
- Security
- Access
- Data Integrity
- …
iPhone
- Simply,
- Apps cannot collect user data without user consent
- It must be for enhancing the Apps
- Apps cannot use analytics software to collect and send user data to a third party
- …
5.1.5 Data Privacy for Data Users
- And
Complying with all applicable privacy and data collection laws and regulations with respect to any
a) Collection,
b) Transmission,
c) Maintenance,
d) Processing and
e) UseOf the user’s location data or personal information.
Privacy Covers…
- Personal Information
- Person (bodily privacy)
- Personal Behavior
- Personal Communication
5.3 Personal Data (Privacy) Ordinance (PDPO)
HK: Personal Data (Privacy) Ordinance (PDPO)
One of the eriliset comprehensive data protection laws in Asia

5.3.1 The Personal Data (Privacy) Ordinance (PDPO)
- PDPO was passed in 1995 and took effect from December 1996 (except certain provisions).
- It is one of Asia’s longest standing comprehensive data protection laws.
- It has its origins in the August 1994 Law Reform Commission Report entitled “Reform of the Law Relating to the Protection of Personal Data”1, which recommended that Hong Kong introduce a new privacy law based on the OECD Privacy Guidelines 19802 to ensure an adequate level of data protection to retain its status as an international trading centre and give effect to human rights treaty obligations.
- The PDPO underwent major amendments in 2012 , the most significant of which being the introduction of direct marketing provisions and other additional protection to cope with new privacy challenges and address public concerns.
- In 2021 , the PDPO underwent another major amendments.
- The amendments aim to combat doxxing ( 人肉搜索 ) acts that are intrusive to personal data privacy, through the criminalisation of doxxing acts, and conferring on the Privacy Commissioner for Personal Data statutory powers to issue cessation notices demanding the cessation or restriction of disclosure of doxxing content.
- The amendments also confer on the Privacy Commissioner power to conduct criminal investigation and institute prosecution for doxxing cases, so as to strengthen enforcement against doxxing cases.
https://www.pcpd.org.hk/english/data_privacy_law/ordinance_at_a_Glance/ordinance.html
5.3.2 PDPO Expected Effect
Bussiness Perspective:
- To facilitate buisness environment
- To maintain Hong Kong as a financial and trading hub
Human Rights Perspective:
- Protect individuals’ personal data privacy
5.3.3 Personal Data (Privacy) Ordinance, Cap 486
Established an independent authority, Privacy Commissioner for Personal Data
Covers both public (government) and private sectors
The Data Protection Principles outline how data users should collect, handle and use personal data
Complemented by other provisions imposing further compliance requirement
5.3.4 Characteristics of the PDPO
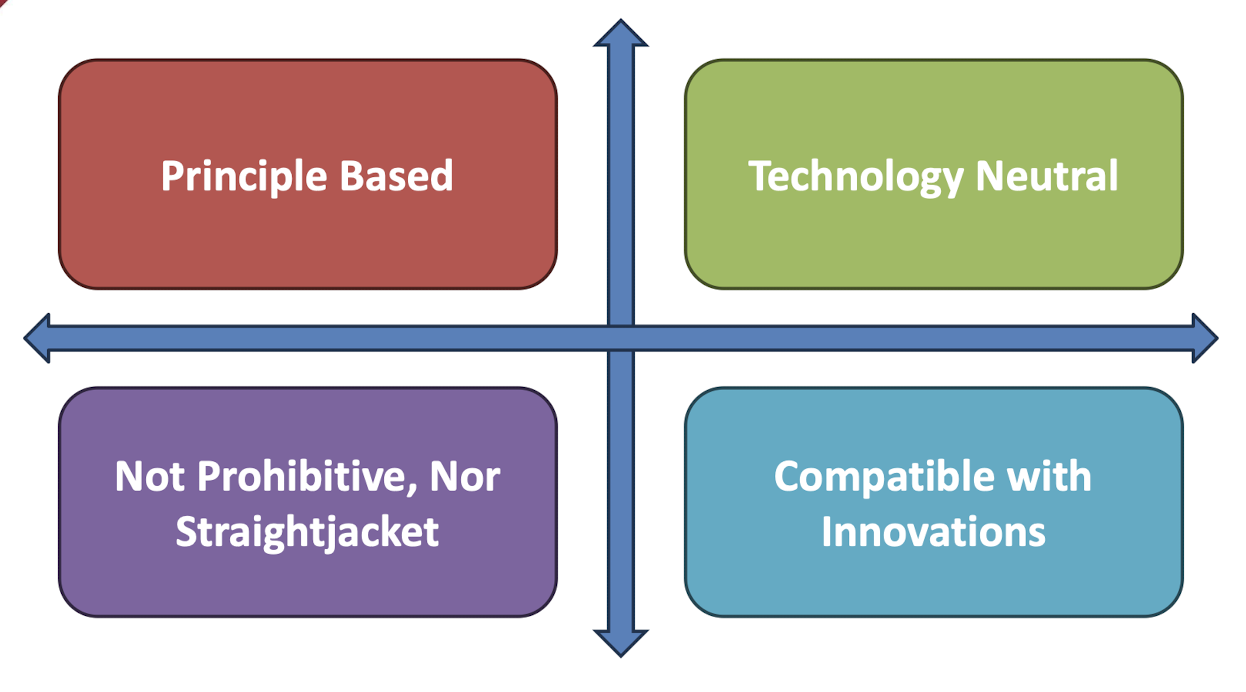
5.3.5 What is “Personal Data”?
Personal Data should satisfy three conditions:
- Relating directly or indirectly to a living individual;
- From which it is practicable for the identity of the individual to be directly or indirectly ascertained; and
- In a form in which “access to” or “processing of” the data is practicable.
5.3.6 The Ordinance Governs All Data Users
- A data user is a person who either alone or jointly or in common with other persons, controls the collection, holding, processing or use of the data.
5.3.7 Fundamental Rules of the PDPO
5.3.8 Six Data Protection Principles (DPPs)
The six data protection principles form the base of the Ordinance.
Data users must comply with the six data protection principles in the collection, holding, accuracy, retention period, security, privacy policy and access to and correction of personal data.
5.3.8.1 Principle 1 - Purpose and Manner of Collection
DPP1: personal data shall be collected for a purpose directly related to a function and activity of the data user; lawful and fair collection of adequate data; data subjects shall be informed of the purpose for which the data are collected and to be used.
Simply:
- shall be collected for purposes related to the functions or activities of the data user
- the means of collection must be lawful and fair
- the data collected should be adequate but not excessive
Example of unfair collection - blind advertisement
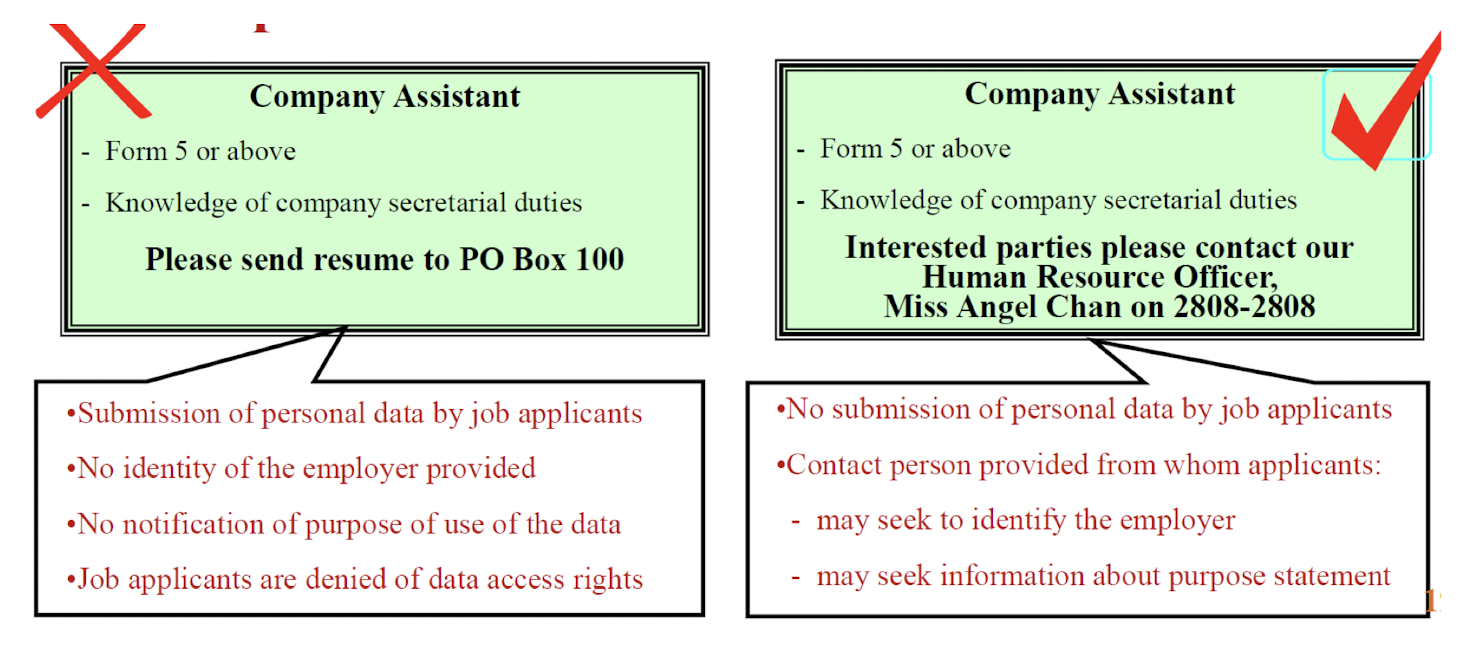
Advice to Data Subjects
- Provide necessary but not excessive personal data to organizations for the prescribed purpose
- For example, when being asked to provide personal data for applying for credit cards, data subjects should consider if the required personal data are necessary
Personal Information Collection Statement (PICS):
- Inform the data subject of the following immediately or in advance
a) the purposes of data collection
b) the classes of persons to whom the data may be transferred
c) whether it is obligatory or voluntary for the data subject to supply the data
d) where it is obligatory for the data subject to supply the data, the consequences for him if he fails to supply the data and
e) the name or job title and address to which access and correction requests of personal data may be made
5.3.8.2 Principle 2 - Accuracy and duration of retention
- DPP2: all practicable steps shall be taken to ensure the accuracy of personal data; data shall be deleted upon fulfillment of the purpose for which the data are used.
- Data users shall take practicable steps to ensure the accuracy of personal data held by them
- All practicable steps must be taken to ensure that personal data is not kept longer than is necessary for the fulfillment of the purpose
- If a data user engages a data processor to process personal data on the data user’s behalf, the data user must adopt contractual or other means to prevent any personal data transferred to the data processor from being kept longer than is necessary for processing of the data
5.3.8.3 Principle 3 - Use of Personal Data
DPP3: unless the data subject has given prior consent, personal data shall be used for the purpose for which they were originally collected or a directly related purpose.
Personal data shall not, without the prescribed consent of the data subject, be used for a new purpose.
*New purpose means any purpose other than the purposes for which they were collected or directly related purposes
- Allow a “relevant person” to give prescribed consent for the data subject under specified conditions
5.3.8.4 Principle 4 - Security of Personal Data
- DPP4: all practicable steps shall be taken to ensure that personal data are protected against unauthorized or accidental access, processing or erasure.
- All practicable steps shall be taken to ensure that personal data are protected against unauthorized or accidental access, processing, erasure, loss and use
- Security in the storage, processing and transmission of data
- If a data user engages a data processor to process personal data on the data user’s behalf, the data user must adopt contractual or other means to prevent unauthorized or accidental access, processing, erasure, loss or use of the data transferred to the data processor for processing
Data Breach Handling Action

What is a data breach notification?
- A formal notification given by the data user to the data subjects affected and the relevant parties and regulators in a data breach.
- It is not a statutory requirement on data users to inform the PCPD about a data breach incident concerning the personal data held by them, but data users are advised to do so as a recommended practice for proper handling of such incident.
- If a data user decides to report a data breach to the
Commissioner, the data user may complete a Data Breach
Notification Form and submit the completed form to us
online, by fax, in person or by post.
5.3.8.5 Principle 5 - Information to be generally available
DPP5: formulates and provides policies and practices in relation to personal data.
Data users have to provide
a) policies and practices in relation to personal data;
b) the kind of personal data held;
c) the main purposes for which personal data are used.
Advice to Wifi Service Provider
- Privacy Policy Statement of Wifi service should not be made in unreasonably small fonts
- Wi fi service provider should ensure that the Privacy Policy is effectively communicated to Wi fi users Considerations include the font size, layout and language used in the Privacy Policy
5.3.8.6 Principle 6 - Access to Personal Data
DPP6: individuals have rights of access to and correction of their personal data. Data users should comply with data access or data correction request within the time limit, unless reasons for rejection prescribed in the Ordinance are applicable.
A data subject shall be entitled to
a) request access to his/her personal data;
b) request correction of his/her personal data.- Data user may charge a fee for complying with the data access request
5.3.9 Use of Personal Data in Direct Marketing
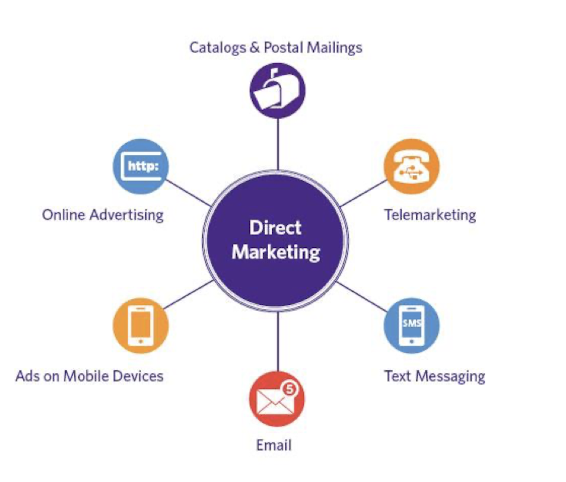
- Major amendments in 2012, introduction of direct marketing.
- Direct Marketing means sending promotional information of goods or services, addressed to specific persons by name by mail, fax, email or phone
- Under the existing Ordinance, data user must notify a data subject of his optout right when using his personal data in direct marketing for the first time
- Upon receiving an opt out request, the data user must cease using the data
https://eunikeagintas.wordpress.com/2015/03/15/direct-marketing/
5.3.10 Regulatory Regime (System) of Direct Marketing
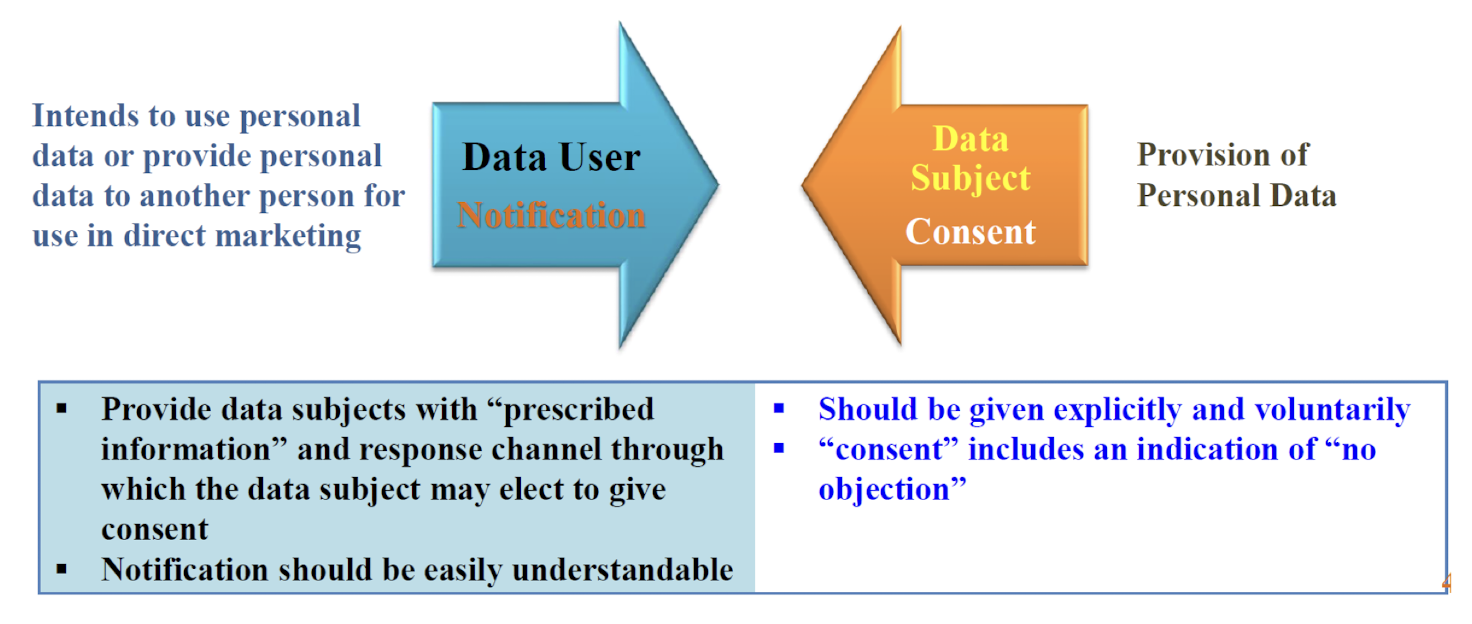
5.3.11 Higher Penalties for Non-Compliance
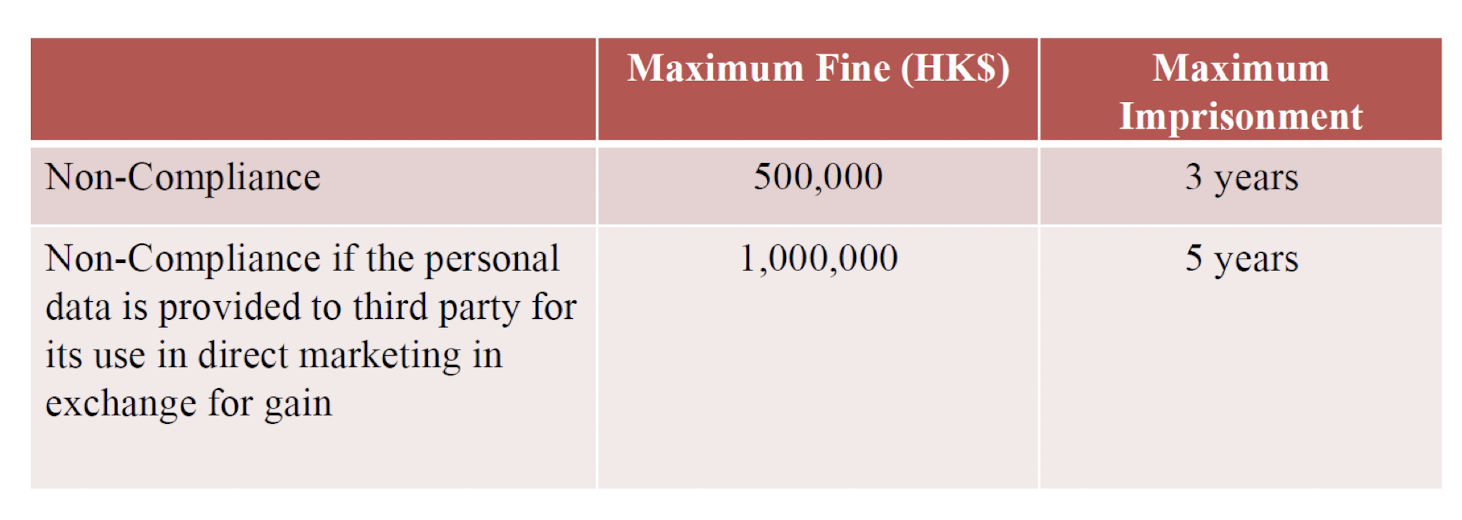
5.3.12 Examples of Criminal Offences under PDPO
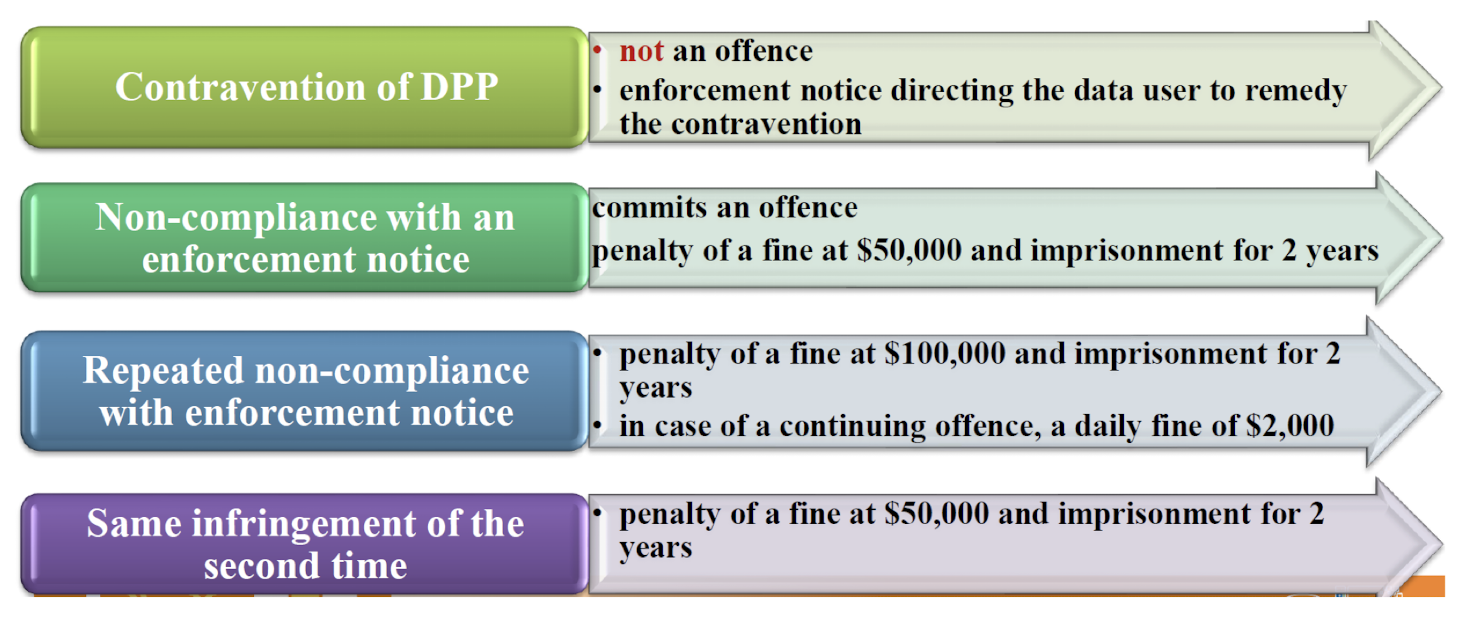
5.3.13 Quiz

C

C

A
5.3.14 GDPR Data Processing/Protection Principles
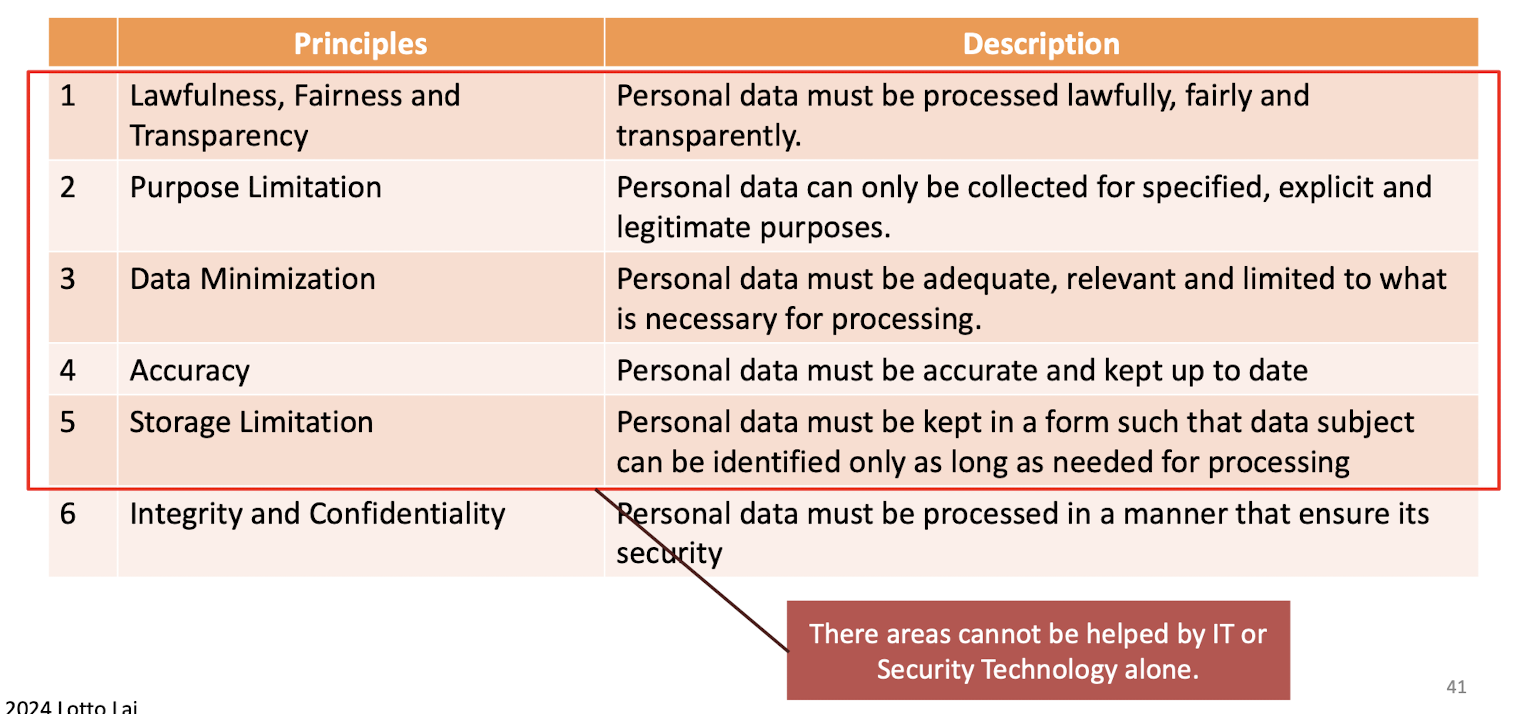
5.3.15 GDPR Data Subject (PII Principal) Rights
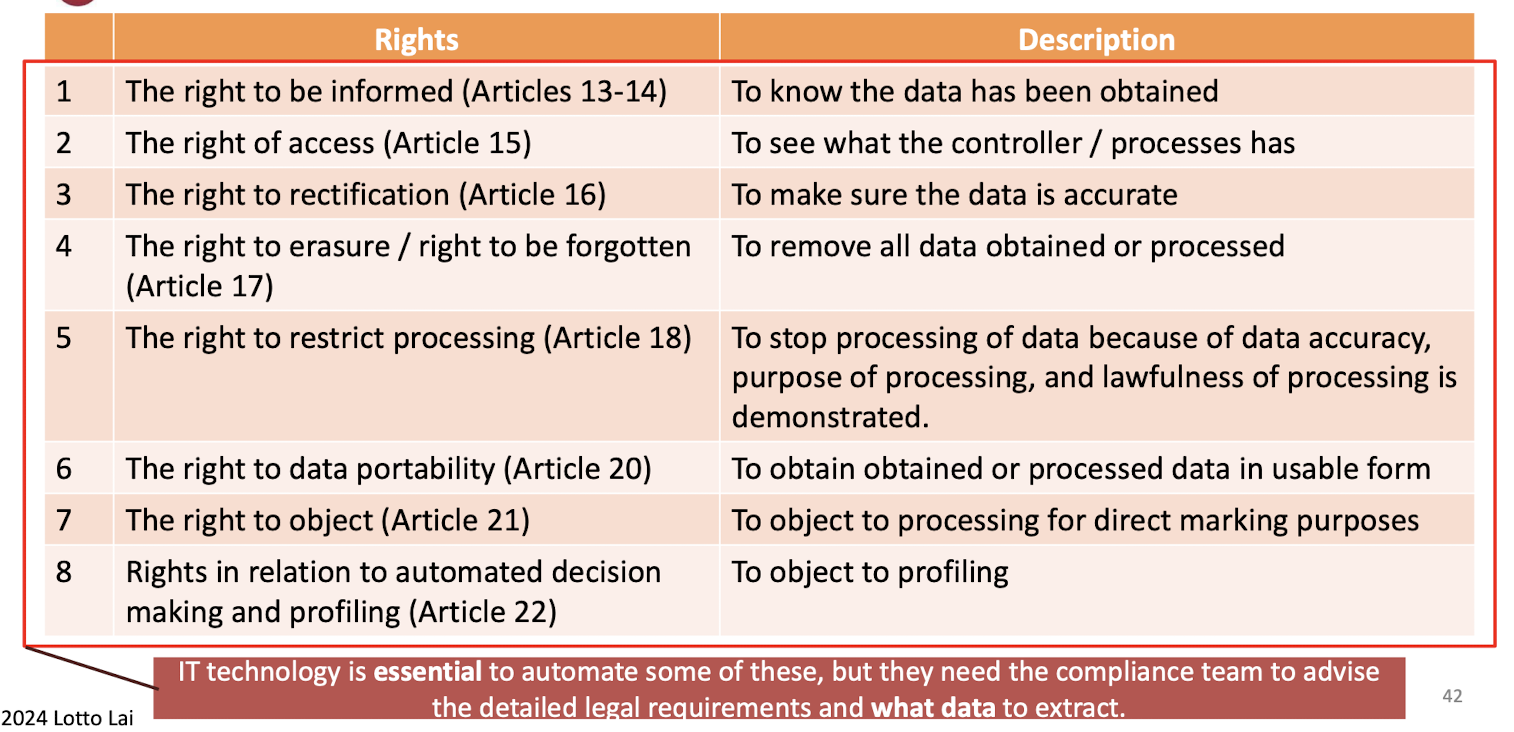
5.3.16 GDPR Other important requirements
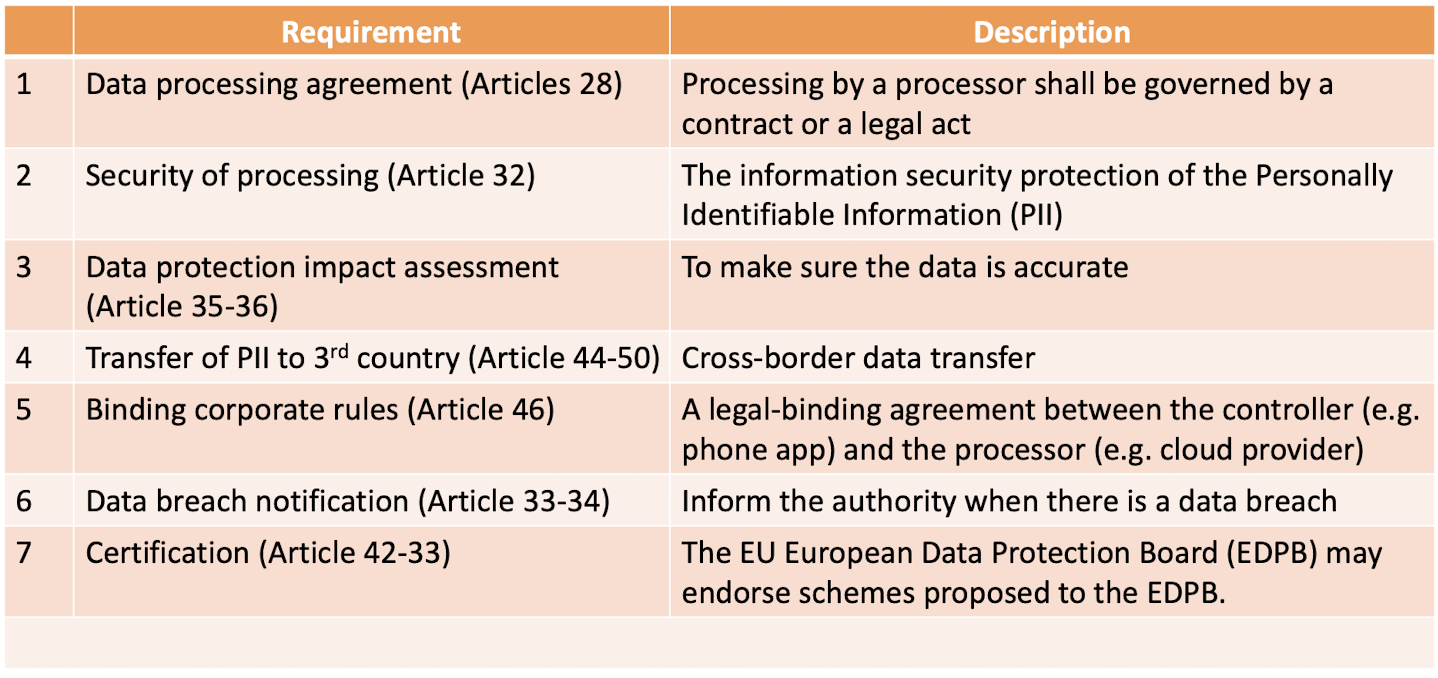
5.4 Privacy Management
- Privacy is a collaborative effort of IT, Compliance Team, and others.
- Privacy management should be an integral part of an organization’s overall management strategy
5.4.1 Common Pitfalls
- Many people regard personal data privacy as data security only.
- They thought data privacy is about
- Data is stored security (password protected or encrypted)
- Not accessible by unauthorized persons
- Not transferred to the 3rd party
- Treat personal data as simply an asset in information security management
- Privacy needs to be managed systematically!
5.4.2 ISO/IEC 27701:2019 (Privacy Information Management)
- Released in Aug 2019
- Specifies requirements and provide guidance for establishing, implementing and continually improving a Privacy Information Management System (PIMS) in the form of ==an extension to ISO/IEC 27001 and ISO/IEC 27002==
- Can be used by Personally Identifiable Information (PII) controllers (including joint controllers) and PII processors (including subcontractors to PII processors)
- Mixture of requirements and guidelines
5.4.3 Privacy Information Management System (PIMS)
- ISO/IEC 27701:2019
- Security techniques — Extension to ISO/IEC 27001 and ISO/IEC 27002 for Privacy Information Management - Requirement and guidelines
- ISO/IEC 27701 is designed to work with ISO/IEC 27001 to form a complete Privacy Information Management System
- Organization must first possess an ISO/IEC 27001 Information Security Management System.
5.4.4 ISO/IEC 27701 Development Timeframe
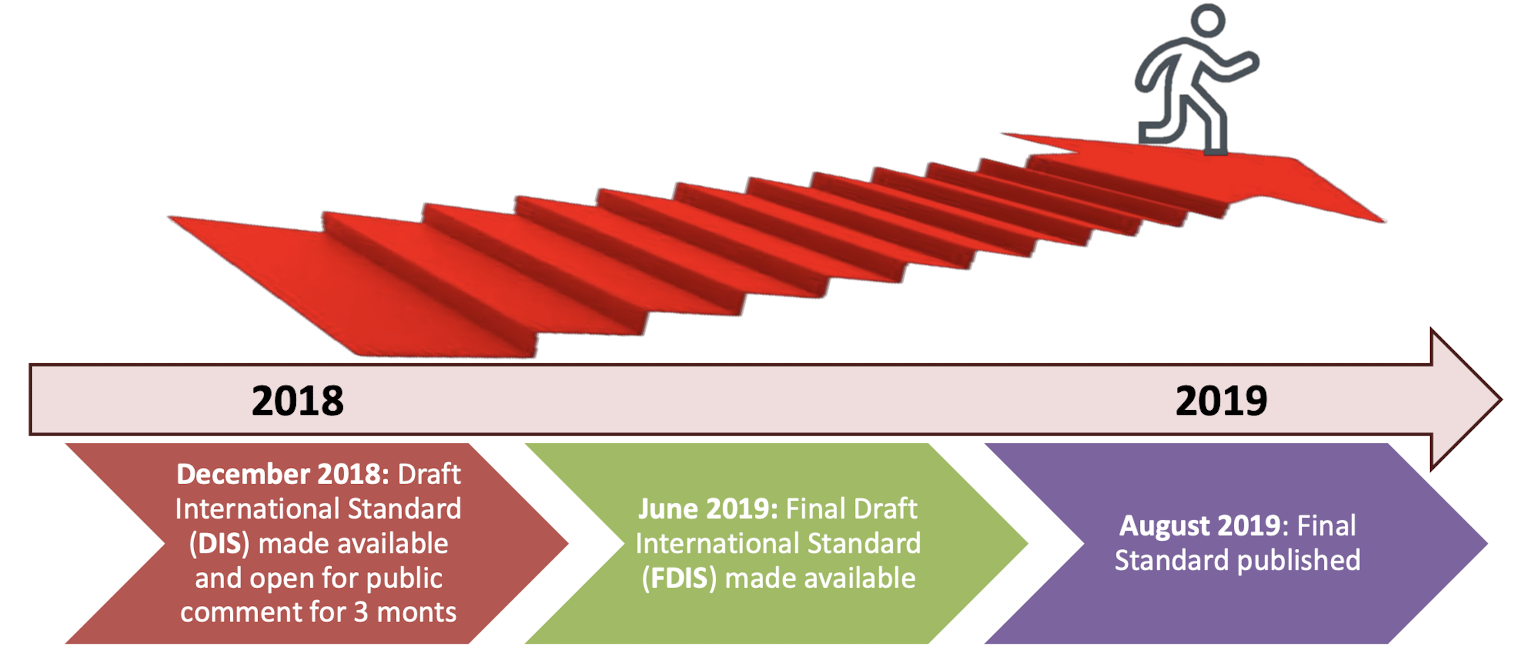
5.4.5 Benefits of Implementing ISO/IEC 27701
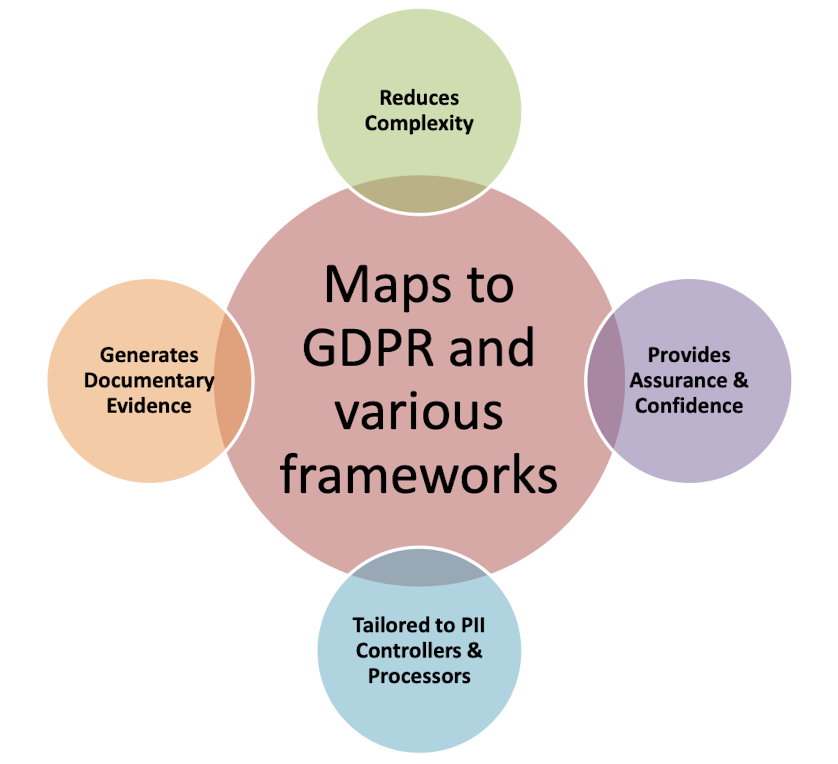
5.4.6 Key Terms and Alternative Terms
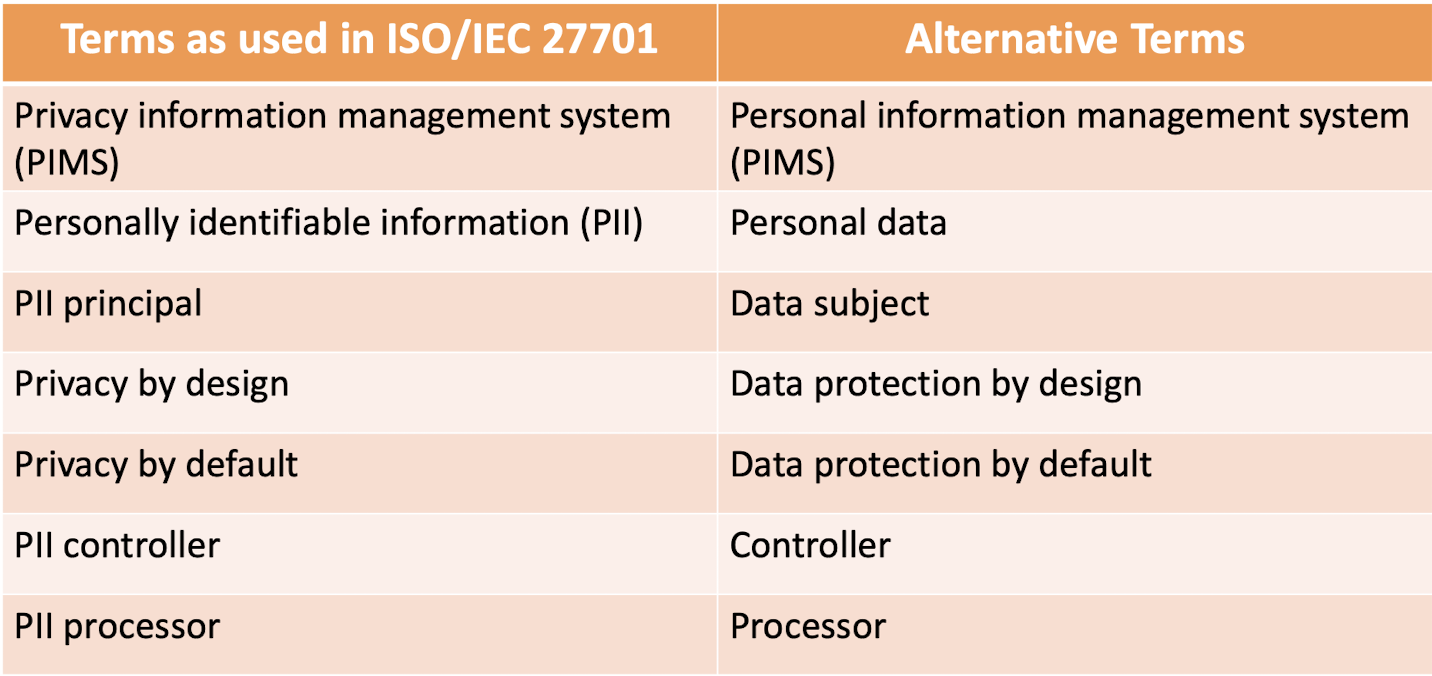
5.4.7 Key Terms Definition
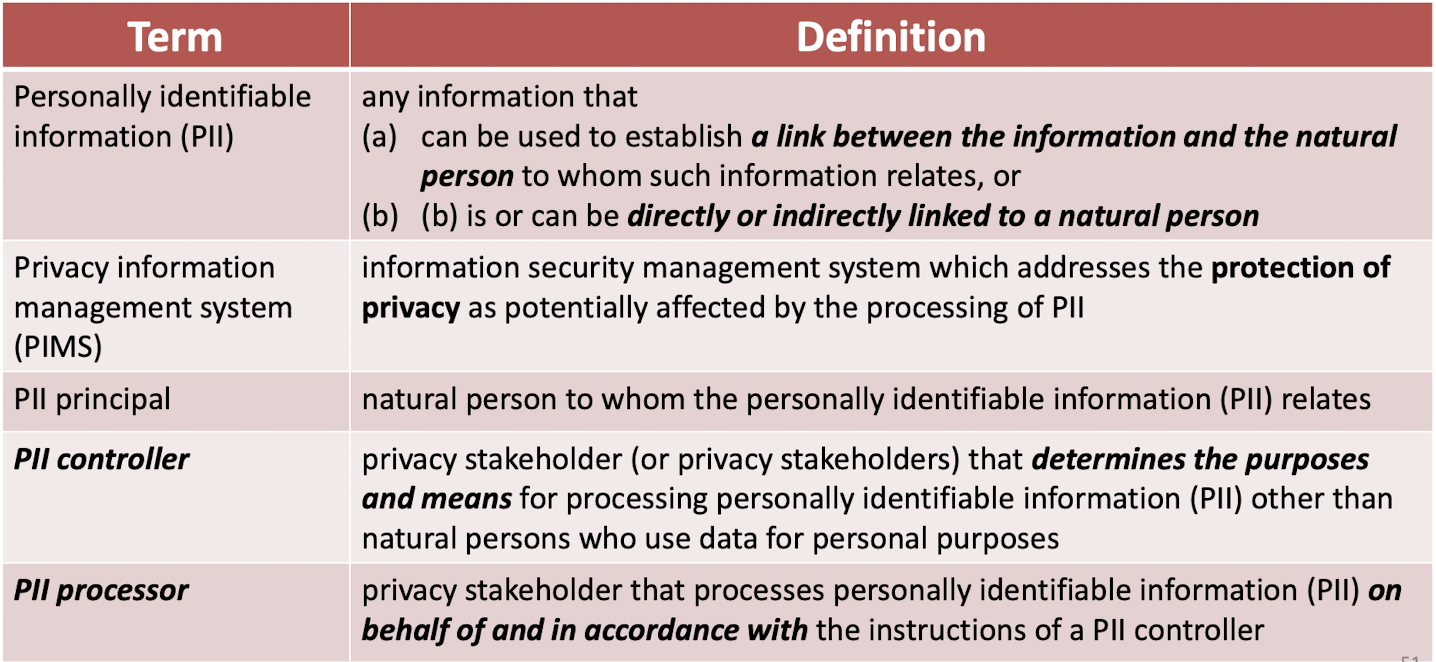
5.4.8 PII Controller vs PII Processor
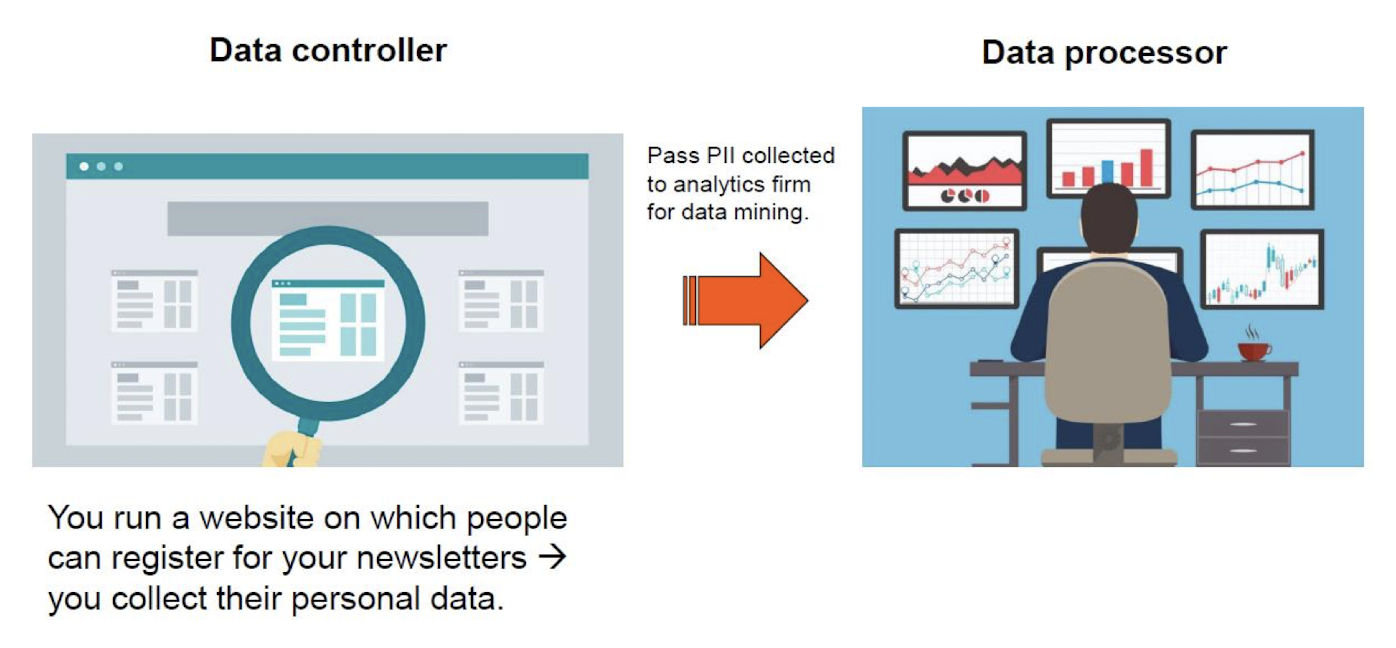
5.4.9 Integration - High Level Structure (HLS)
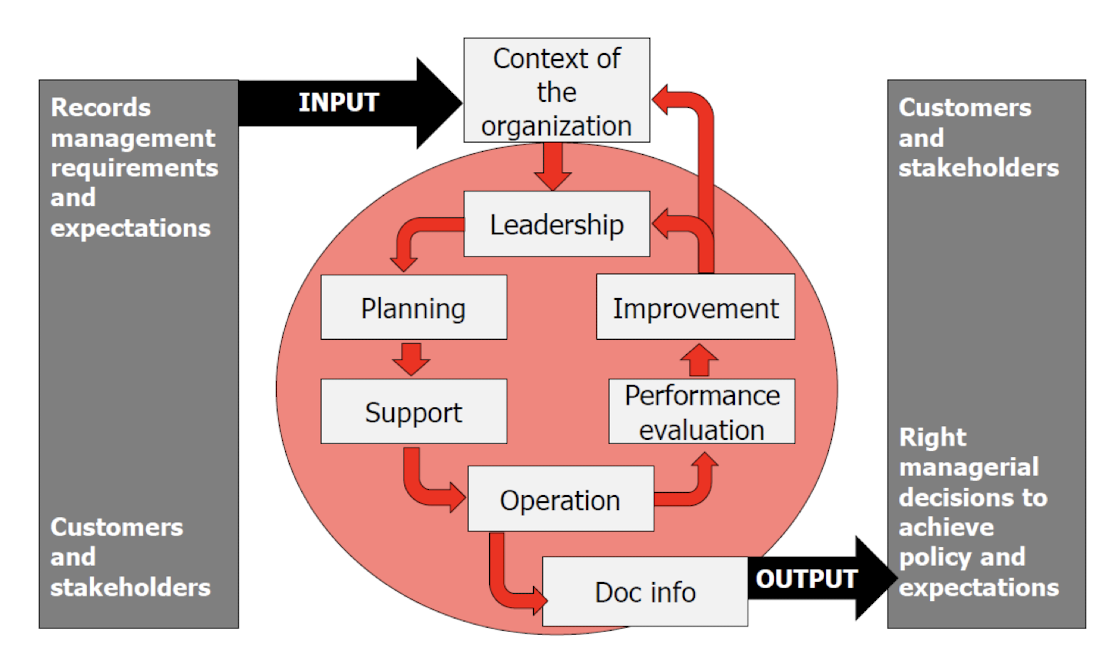
5.4.10 ISO 27701 Clauses
- Scope
- Normative references
- Terms, definitions and abbreviations
- General
- PIMS - specific requirements related to ISO/IEC 27001
- PIMS - specific guidance related to ISO/IEC 27002
- Additional ISO/IEC 27002 guidance for PII controllers
- Additional ISO/IEC 27002 guidance for PII processors
Annex A (PIMS-specific reference control objectivs and
controls) (PII Controllers)
Annex B (PIMS-specific reference control objectivs and
controls) (PII Processors)
Annex C (Mapping to ISO/IEC 29100)
Annex D (Mapping to the GDPR)
Annex E (Mapping to ISO/IEC 27018 & ISO/IEC 29151)
Annex F (How to apply ISO/IEC 27701 to ISO/IEC 27001 &
ISO/IEC 27002)
Bibliography
5.4.11 ISO/IEC 27701 works with ISO/IEC 27001
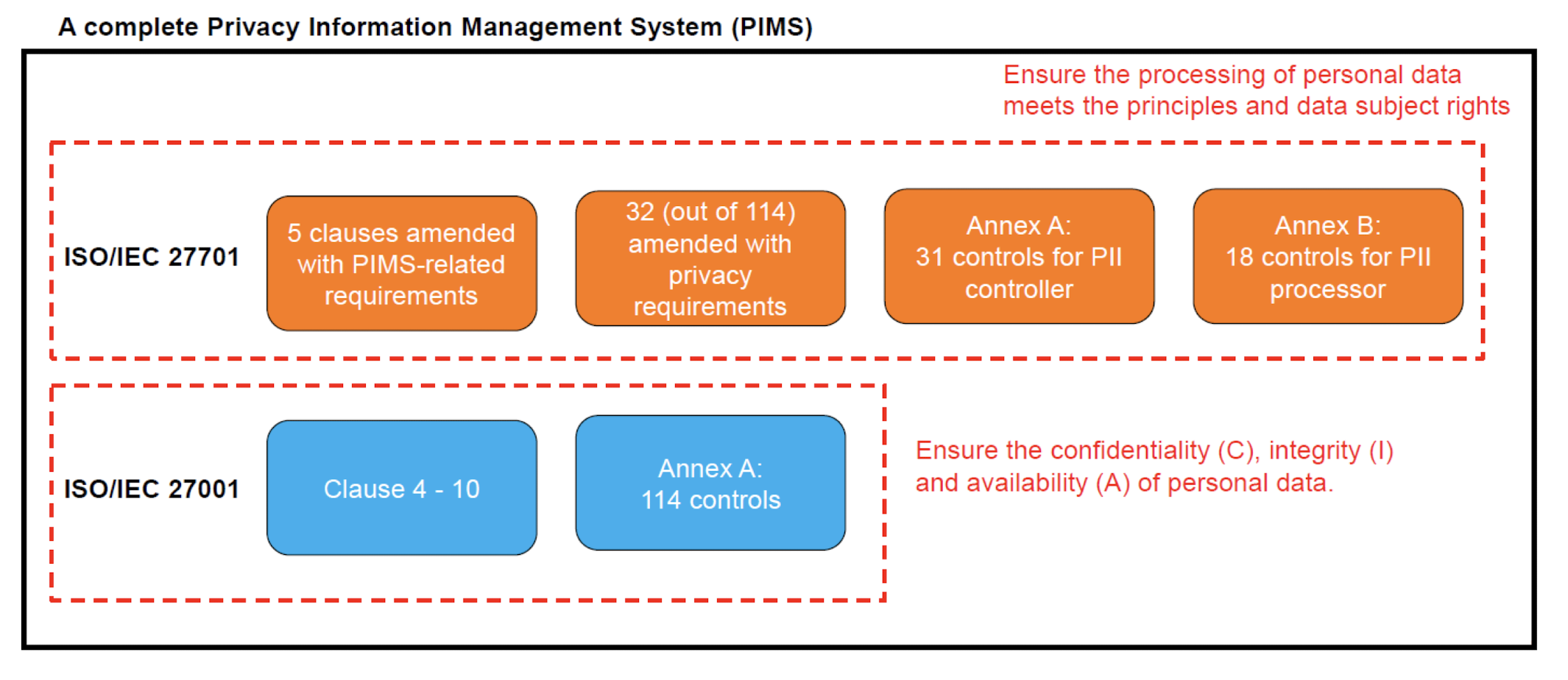
6. Computer Related Law & International AI
6.1 China related law and guideline
6.1.1 General Data Protection in China
The PRC Cybersecurity Law (promulgated and effective from 1 June 2017) adopted by the Standing Committee of the National People’s Congress has become the first national-level law that addresses cybersecurity and data privacy protection.
The Decision on Strengthening Online Information Protection (Promulgated and effective on 28 December 2012; the ‘Decision’) adopted by the Standing Committee of the National People’s Congress; and
- The purpose of the Decision is to protect online information security, safeguard the lawful rights and interests of citizens, legal entities or other organizations , and ensure national security and public interests. The Decision has the same legal effect as a law.
- National Standard of Information Security
Technology - Guideline for Personal Information Protection within Information System for Public and Commercial Services (promulgated 05 Nov 2012 and effective on 01 February 2013, GB/Z 28828- 2012 ; the ‘Guideline’) as published by General Administration of Quality Supervision, Inspection and Quarantine of China and Standardization Administration of China,
- the Guideline is only a technical guide and thus not legally binding, it is considered important because its scope extends to any “ processing of personal information through information systems “ (not necessarily connected to the Internet), and because of the fact that it covers in detail key issues such as data exports, sensitive data, data subject access and the right to rectification.
Information Security Techniques - Personal Information Security Specification , which was issued on 29 December 2017 and comes into force on 1 May 2018, then updated on 6 March 2020 and implemented on 1 Oct 2020 (the “PI National Standards”).
While the formal text of these standards have not been made available to the public, the draft versions indicate that they set out key data protection concepts and principles which until now remain elusive and have not been properly developed or explained in key laws and regulations, including the Cybersecurity Law.
The PI National Standards may not necessarily replace the Guideline issued in 2012 in theory, but they are expected to be the new national standards on personal data protection in China.
6.1.2 Overview of China’s Cybersecurity Law
Prior to the enactment of the Cybersecurity Law, China already had some laws, rules and regulations relating to information security, such as Administrative Measures for Prevention and Treatment of Computer Viruses and Administrative Measures for Hierarchical Protection of Information Security.
The Cybersecurity Law, which indicates that China is increasingly focusing on cybersecurity, was adopted by the National People’s Congress (NPC) in November 2016 after a year of legislative proceedings, and will come into effect on 1 June 2017.
https://assets.kpmg.com/content/dam/kpmg/cn/pdf/en/2017/02/overview-of-cybersecurity-law.pdf
6.1.3 Key Consideration under the Cybersecurity Law
Personal information protection
- The Law pays more attention to the protection of personal information and individual privacy
- The Law standardises the collection and usage of personal information
- Enterprises should focus not only on “data security”, but also on “individual privacy protection”, which is of greater significance
Security requirements for network operators
- The Law presents clear definitions of network operators and security requirements
- Most of the largerfinancial institutions may become “network operators”
Critical information infrastructure
- The Law places greater demands on the protection of key information infrastructure
- The Law specifies the scope of key information infrastructure
Restrictions on the transfer of personal information and business data overseas
- Foreign enterprises and organisations normally need to transfer information outside China
- The Cybersecurity Law stipulates that sensitive data must be stored domestically
Penalties
- Penalties for violating the Law are clearly stated, and include the suspension of business activities
- Serious illegal action may lead to the closing of businesses or the revocation of licenses
- The maximum fine may reach RMB1,000,
6.1.4 Highlights of the Cybersecurity Law
Comprising 79 articles in seven chapters , the Cybersecurity Law contains a number of cybersecurity requirements, including safeguards for national cyberspace sovereignty, protection of critical information infrastructure and data and protection of individual privacy.
The Law also specifies the cybersecurity obligations for all parties.
Enterprises and related organizations should priorities the following highlights of the Cybersecurity Law:
6.1.5 Definition of Personal Data
Personal data (which is referred to as ‘ personal information ’ in the Decision) means any electronic information which can enable identification of a citizen’s individual identity and which relates to personal privacy.
- This definition was further clarified in the Guideline as any data or information in connection with a specific individual, which can be used, separately or in combination with other data, to identify the individual.
Under the Cybersecurity Law, personal information is defined as including all kinds of information, recorded electronically or through other means, that taken alone or together with other information, is sufficient to identify a natural person’s identity , including, but not limited to, the natural persons’ full name, date of birth, identification numbers, personal biometric information, addresses, telephone numbers and so forth.

6.1.6 Definition of Sensitive Personal Data
In the PI National Standards, sensitive personal information is defined as personal information the leakage, illegal provision or abuse of which may harm personal/property safety and personal reputation or physical/mental health , or result in discrimination towards the data subject.
Examples may include personal identification number, individual biometric information , bank account number, correspondence records and contents, property information, credit information, location tracking, lodging information, health and physiological information and transaction information etc.
6.1.7 Highlights of Personal Information Protection (I)

Interpretation:
The articles above emphasize that personal information can only be collected when individuals are informed and agree to the aims and scope of the collection.
Citizens provide personal information for many purposes, including for education, healthcare, public transportation and online-to-offline transactions. These articles standardize approaches and methods for enterprises and related institutions to obtain personal information.

Interpretation:
The articles above stipulate requirements for the protection of personal information, especially for avoiding disclosure, damage and loss of personal information.
Amidst a growing focus on telecom fraud and personal information leaks, the Cybersecurity Law introduces stricter requirements on the protection of personal information owned by organizations.
Accurately identifying personal information owned by organizations, protecting the information using technology and identifying potential information leak risks are becoming key priorities for enterprises.
6.1.8 Definition of Network Operators
Article 76 of the Cybersecurity Law: “Network operators” refers to owners and administrators of networks and network service providers.
Since the applicable scope of “network operators” has expanded significantly, enterprises and institutions that provide services and conduct business activities through networks may also be defined as “network operators”.
In addition to traditional telecom operators and internet firms, network operators may also include:
- Financial institutions that collect citizens’ personal information and provide online services, such as banking institutions, insurance companies, securities companies and foundations.
- Providers of cybersecurity products and services.
- Enterprises that have websites and provide network services.
6.1.9 Highlights of Network Operators (I)

Interpretation:
Security administration: Network operators are required to clarify responsibilities within their organisations, and ensure network security by implementing sound rules and regulations and operational processes.
Technology: Network operators shall adopt various technologies to prevent, combat and investigate cyber-attacks to mitigate network risks.
Data security: Network operators shall ensure data availability and confidentiality by backing up and encrypting data.
Building an effective security administration system, finding rational technical solutions and improving data protection capabilities are expected to be key priorities for network operators.

Interpretation:
This article is applicable to cybersecurity product manufacturers, security service suppliers and other organizations that provide services through networks. These network operators are required to respond to security flaws in their products and services and provide security maintenance.
Currently, some network security product and service providers do not respond quickly and effectively to flaws in their products and services, which also impacts security maintenance. This may create cybersecurity risks for users of their products and services.
6.1.10 Critical Information Infrastructure (CII)
Critical Information Infrastructure (CII):
- Financial, energy, water, public utilities, telecom and information services, transportation, e-government AND “OTHER KEY INDUSTRIES”
Personal Data and Important Data
- collected/generated during business operation in China should be stored in China
- Cross-border transfer of data is only allowed on the ground of necessary and has passed security assessment
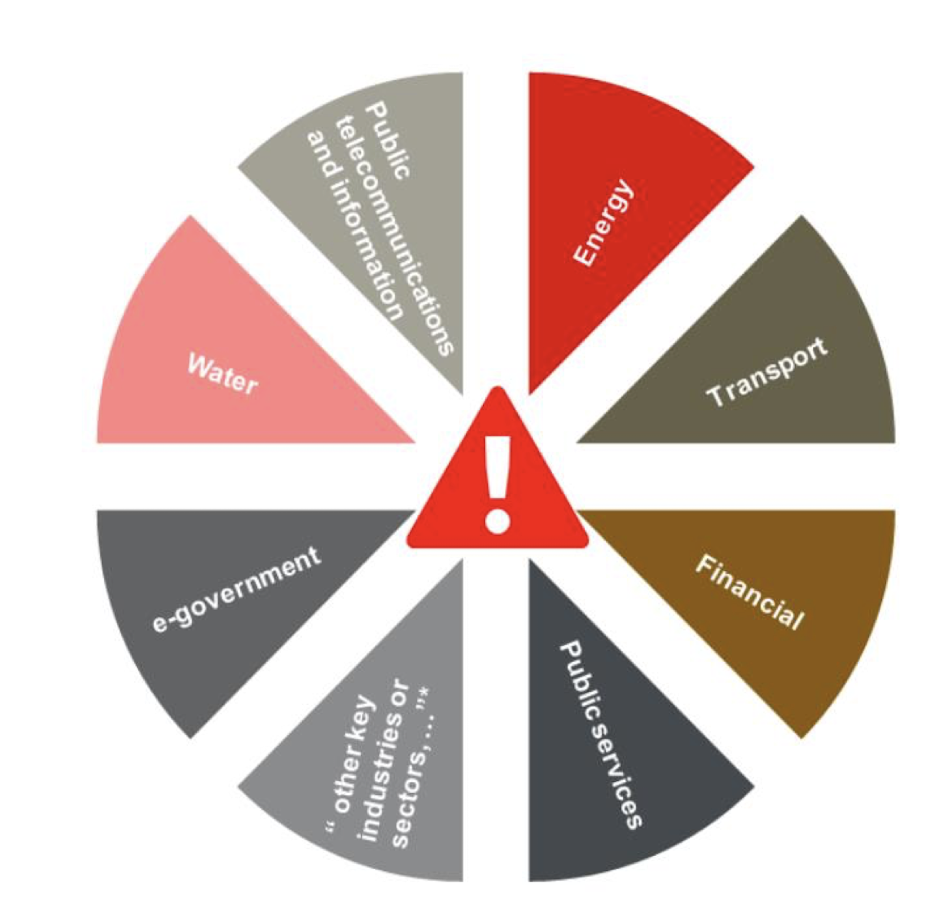
6.1.11 Highlights of Critical Information Infrastructure
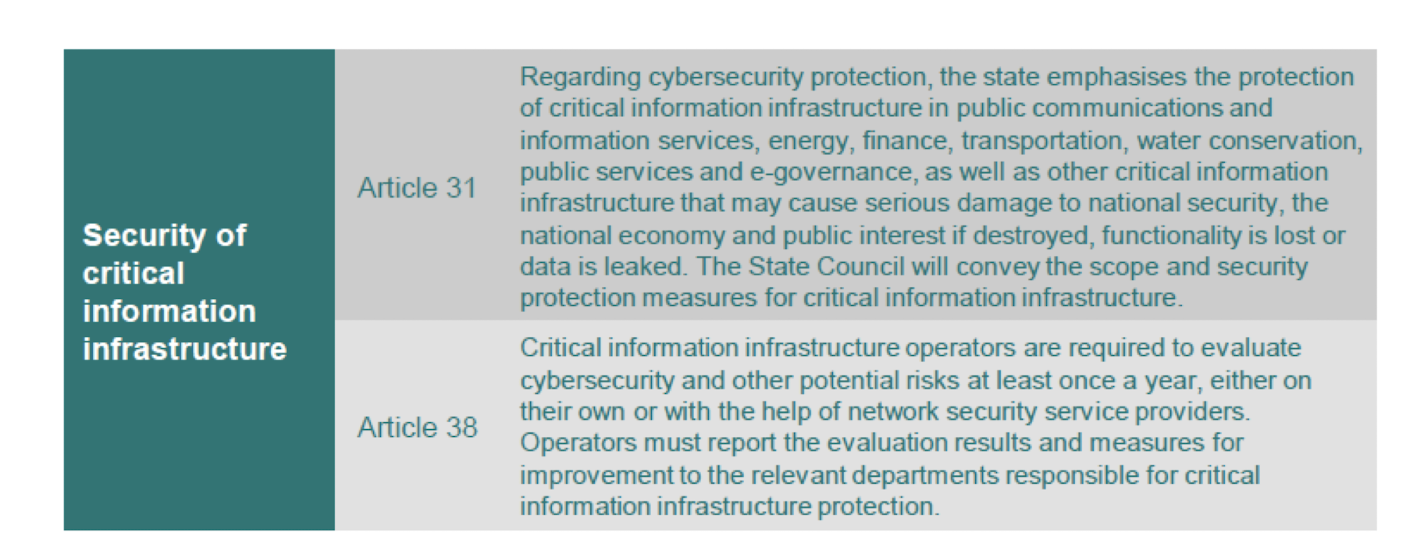
Interpretation:
- The Cybersecurity Law mentions that the scope of critical information infrastructure and protection procedures will be defined by the State Council, but the scope has not yet been clarified officially.
Enterprises can estimate the scope by considering factors like the number of users, information leak risks, potential implications and the size of data centers.
- Enterprises that are qualified to operate critical information infrastructure must regularly assess their cyber risks in accordance with Article 38 of the Cybersecurity Law.
6.1.12 Highlights of Preservation of Sensitive Information

Interpretation:
Potential implications: Some enterprises need to transmit data to their headquarters, partners and/or suppliers overseas. If these enterprises are qualified to operate critical information infrastructure, they will need to reassess their approach regarding data transfers.
Response: For personal information/important data that is stored overseas, the most direct and effective way is to transfer and store the data locally in China. For personal information/important data that is stored in China but needs to be transferred overseas, the content and approach of the transfer should be adjusted to meet the new requirements.
Implementation of the article: China’s cyberspace administrative bodies and other regulatory bodies will introduce policies to clarify the requirements for domestically stored data. At present, there are no official rules and regulations to support the implementation of the article.
6.1.13 Highlights of Certification of Security Products

Interpretation:
The articles above stipulate that providers can only sell their critical network equipment, products or services after receiving security certifications. They may also need to pass a national security review.
The security review/assessment is designed to ensure the security of personal information and support the secure operations of critical information infrastructure described in the Cybersecurity Law.
Providers of network equipment, products or services should actively respond to national security reviews to avoid negative business implications as a result of failing to obtain security certifications.
6.1.14 Highlights of Legal Liabilities

Interpretation:
The article above specifies the penalties that network operators, network product or service providers and operators of critical information infrastructure may face if they violate certain articles of the Cybersecurity Law.
Network operators, network product or service providers and operators of critical information infrastructure should carefully follow the related provisions of the Cybersecurity Law to avoid being penalized.
6.1.14 Recap of Personal Information Protection Law (PIPL)
- Personal Information Protection Law of the People’s Republic of China (hereinafter referred to as “ PIPL “) was approved at the 30 th meeting of the Standing Committee of the 13th National People’s Congress on August 20, 2021, and would come into effect on November 1,2021, after nearly two years of preparation and three rounds of review.
- Compared with the 1 st and the 2 nd draft, key updates in the approved version are covering legal basis of personal information processing, protection obligations of personal information processors , personal information cross-border transfer , legal liability , etc.
https://kpmg.com/cn/en/home/insights/2021/08/establishing- comprehensive-personal-information-protection-management-system.html
6.1.15 Personal Information Protection Law (PIPL)
Scope of Application
- Personal information processing activities conducted within China
- Certain processing activities conducted outside of China, of domestic natural persons’ personal information
Processor
- Organizations and individuals who independently decide the purpose and method of processing personal information.
- “Special” processors: joint processing, entrust and entrusted processing, third parties, etc
Legal Basis
- Obtain personal consent
- Signing or performing contracts, or conducting human resources management based on legal documentation ;
- Processing disclosed personal information within a reasonable scope within PIPL ; or
- Performing legal duties or obligations, responding to emergencies, implementing news reports and public opinion supervision for public interests, and other circumstances stipulated by laws and administrative regulations.
Protection Obligations
- Protection from organization & people, policy & procedure, and technology enabled etc.
Additional requirements in processing sensitive personal information, establishment of specific personal information processing rules when processing personal information of children under 14
Responding and addressing individual’s applications for the exercise of rights, and the right of personal information portability, the exercise of rights when a natural person is deceased, etc.
- Pre-event personal information protection impact assessment and regular compliance audit
Cross-border Transfer
- Critical Infrastructure Information Operator (CIIO) and personal information processors who reach the number prescribed by the State
- Cyberspace Administration shall store the personal information collected and generated within China
Pre-conditions: Passed the security assessment organized by the authority, achieved personal information protection certification by authorized agencies, signed a standard contract formulated by the authority with the overseas receiver(s) to agree upon the rights and obligations, etc.
Pre-event personal information protection impact assessment and separate consent, and the personal information protection capabilities of the overseas receiver(s) up to the standards in PIPL
Legal Liability
- Ordering rectification, confiscating illegal gains, fines for organizations and people, recording in the credit profiles, compensating for losses, etc.
- Ordering to suspend or terminate the services provided by the applications illegally processing personal information
- The maximum fine is not more than 50 million yuan or not more than 5% of its turnover of the previous year
- The fine to the directly responsible person is 100,000 to 1 million, and the person could be prohibited to be a director, supervisor, senior manager, or personal information protection officer of relevant enterprises within a certain period.
6.1.16 Different roles of a Company in Cybersecurity and Data Protection
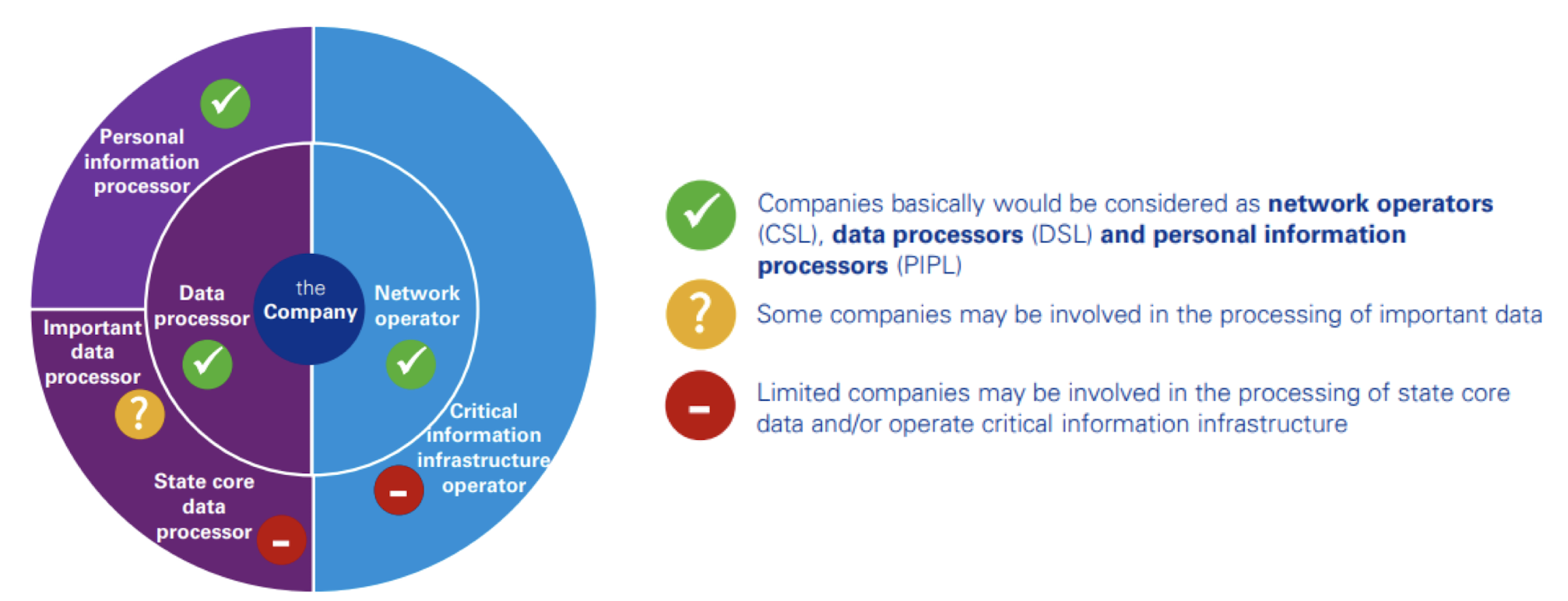
6.1.16 Different roles of a Company in Cybersecurity and Data Protection
To address basic compliance requirements, Companies shall establish and improve the following:
- Information Security Management System (ISO 27001)
- Data Security Management System; and
- Personal Information Management System (ISO 27701)
6.1.17 Overall Summary of PIPL Requirements
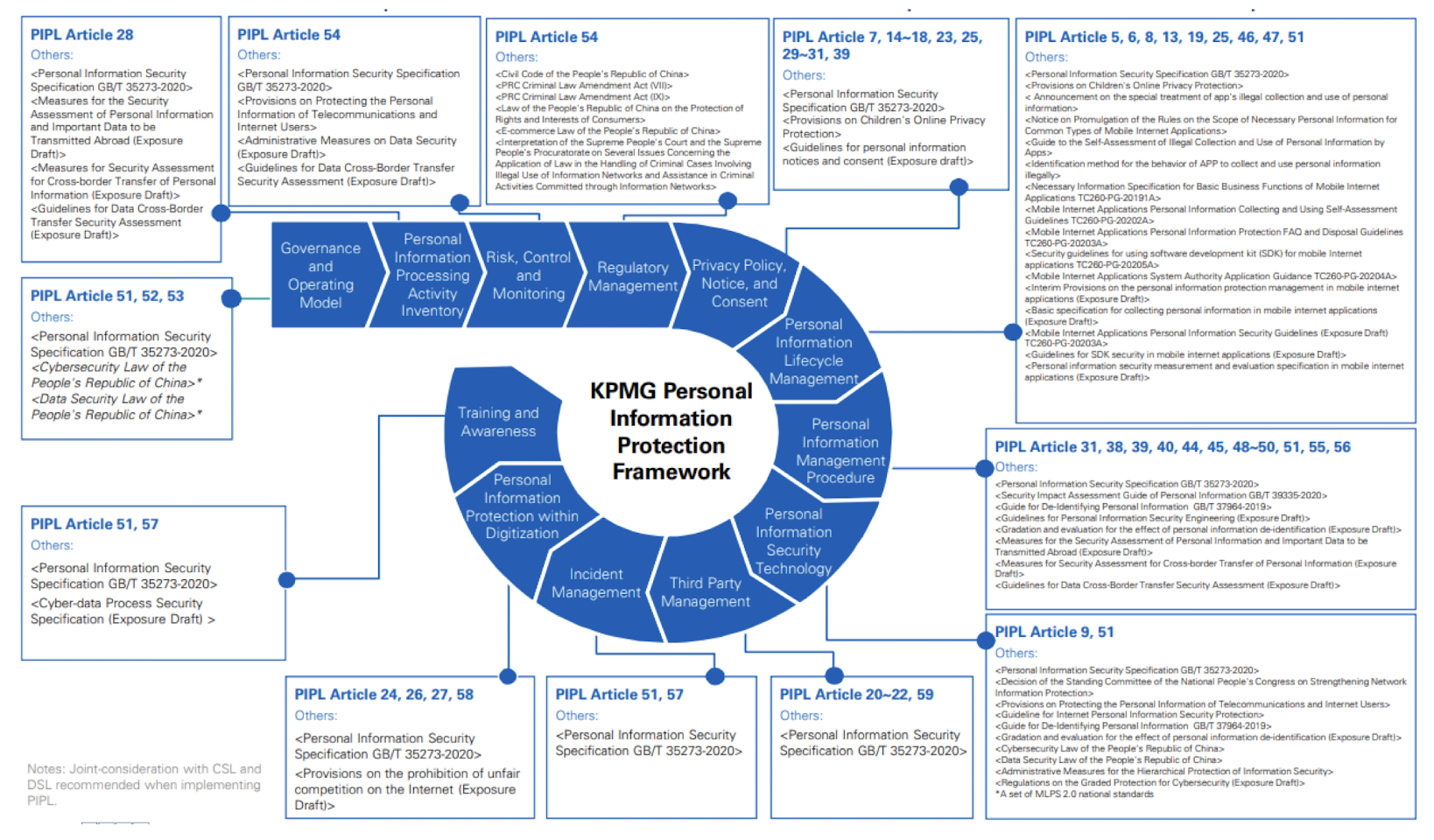
6.2 PIPL vs EU GDPR
6.2.1 Summary of PIPL vs EU GDPR (I)
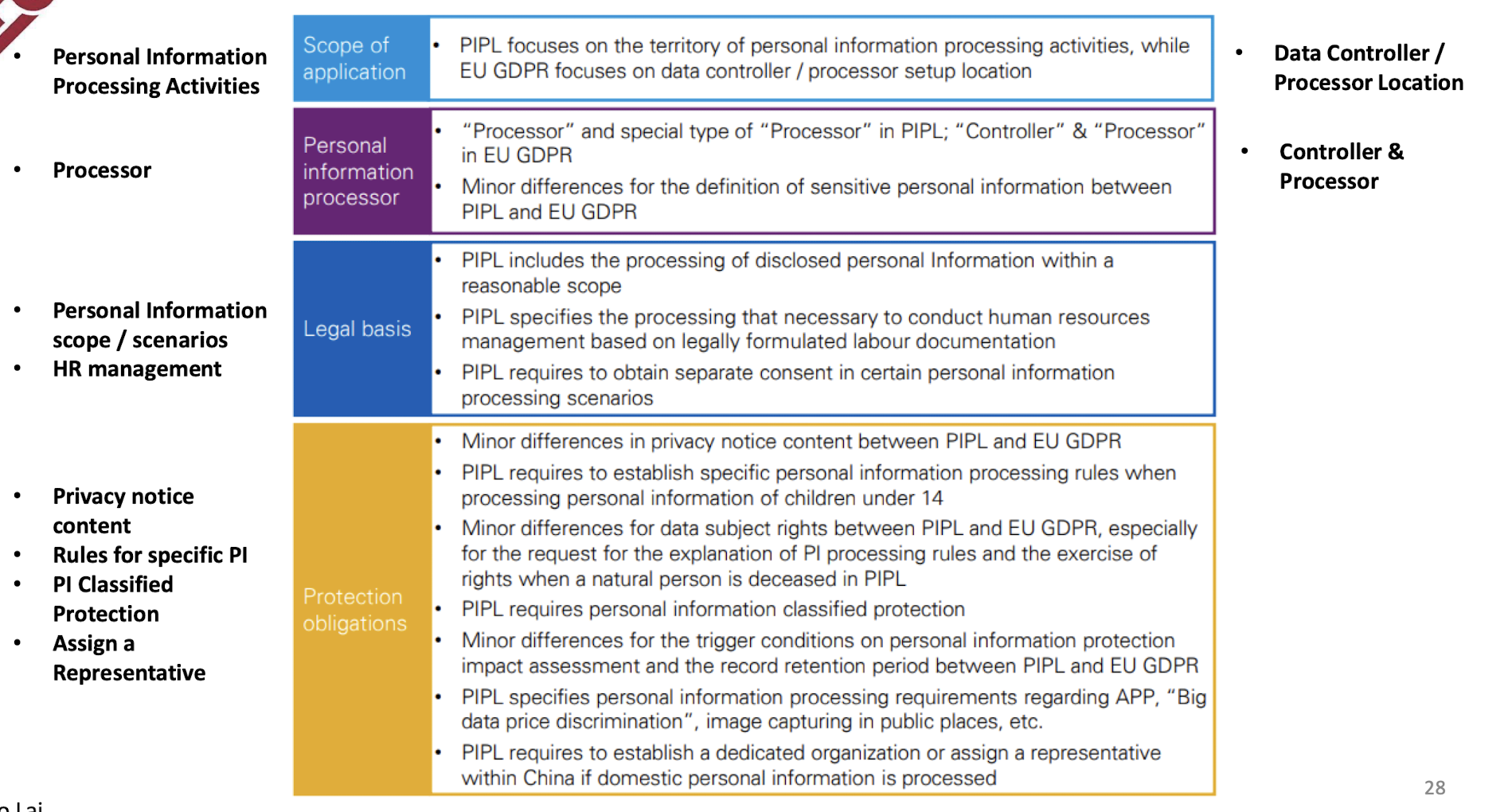
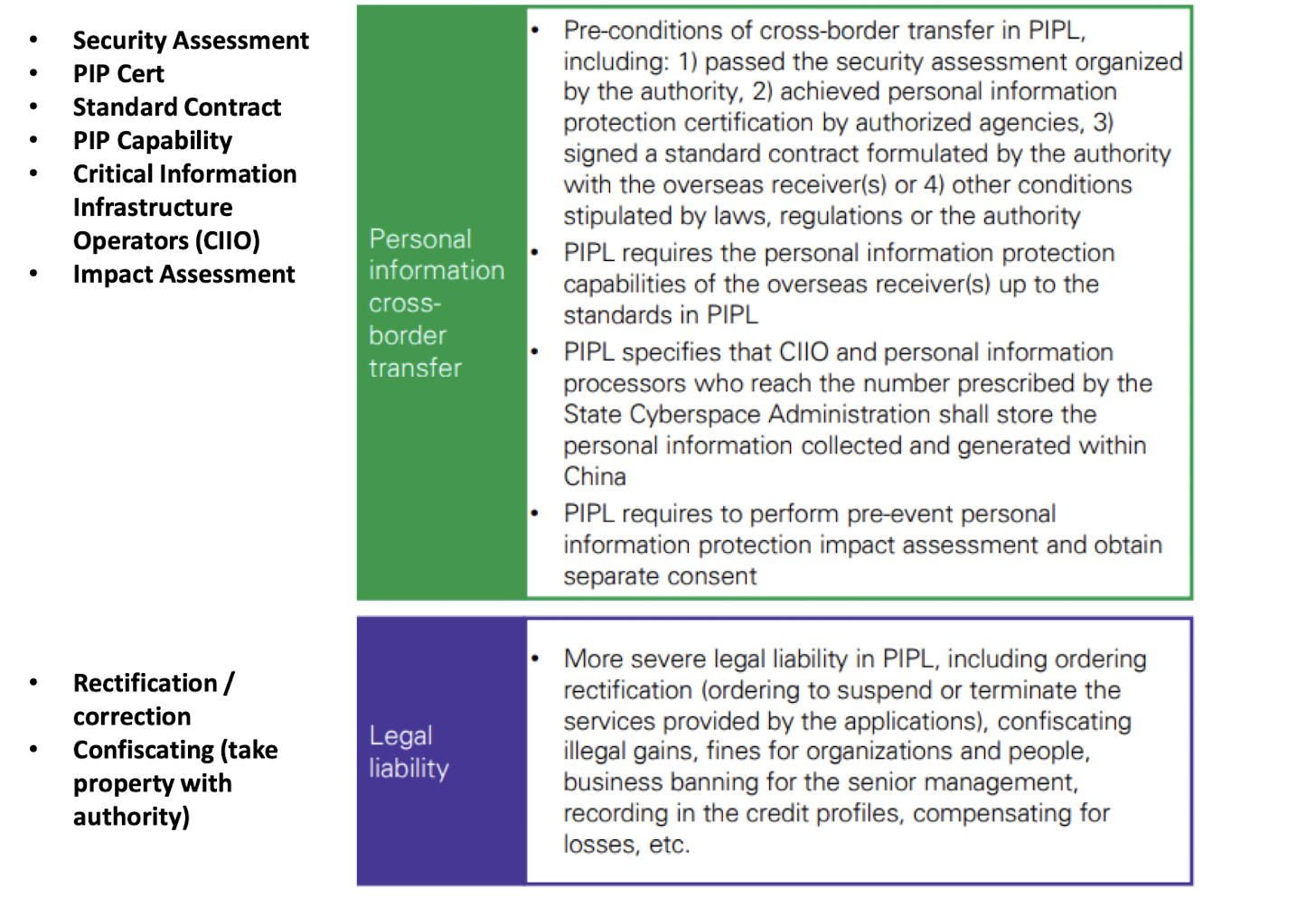
6.3 AI Related Regulations
- President Biden Issues Executive Order on Safe, Secure, and Trustworthy Artificial Intelligence
- Additionally, more than 200 AI related laws have been introduced in varies state legislatures.
- Source: 5 Trends to Watch: 2024 Artificial Intelligence
- EU AI Act: first regulation on artificial intelligence
- Chinese AI governance policy documents
- Source: China’s AI Regulations and How They Get Made (20230710)
6.3.1 President Biden Issues Executive Order for AI Safety (I)
(October 30, 2023)
New Standards for AI Safety and Security
- Require that developers of the most powerful AI systems share safety test results and other critical information with the US government.
- Ensure AI system are safe, secure and trustworthy before companies make them public.
- Develop standards, tools, and tests to help ensure that AI systems are safe, secure, and trustworthy
- NIST will set the strict standards for extensive red-team testing to ensure safety before public release.
- Dept. of Energy & Homeland Security will address AI systems’ threats to critical infrastructure, as well as chemical, biological, radiological, nuclear & cybersecurity risks.
- Protect against the risks of using AI to engineer dangerous biological materials
Protect Americans from AI-enabled fraud and deception by establishing standards and best practices for detecting AI-generated content and authenticating official content.
Establish an advanced cybersecurity program to develop AI tools to find and fix vulnerabilities in critical software
- To make software and networks more secure.
- Order the development of a National Security Memorandum that directs further actions on AI and security
- Ensure to use AI safely, ethically and effectively in their mission (military use).
Protecting Americans’ Privacy
- By prioritizing federal support for accelerating the development and use of privacy-preserving techniques (cutting-edge AI)
- Strengthen privacy-preserving research and technology
- Evaluate how agencies collect and use commercially available information
- Develop guideline for federal agencies to evaluate the effectiveness of privacy-preserving technology (AI systems)
Advancing Equity and Civil Rights
- Provide clear guidance to landlords, Federal benefits programs and federal contractors.
- Address algorithmic discrimination
- Ensure fairness throughout the criminal justice system
- Standing Up for Consumers, Patients and Students
- Advance the responsible use of AI
- Shape AI’s potential to transform education
- Supporting Workers
- To mitigate these risks, support worker’s ability to bargain collectively, and invest in workforce training and development.
- To produce a report on AI’s potential labor-market impacts
- Promoting Innovation and Competition
- Catalyze AI research across the United States
- Promote a fair, open and competitive AI ecosystem
- To expand the ability of highly skilled immigrants and nonimmigrants with expertise in critical areas to study, stay and work in USA.
- Advancing American Leadership Abroad
- Expand bilateral, multilateral and multistakeholder engagements to collaborate on AI.
- Accelerate development and implementation of vital AI standards with international partners and in standards organizations, ensuring that the technology is safe, secure, trustworthy, and interoperable.
- Promote the safe, responsible and rights-affirming development and deployment of AI abroad to solve global challenges
- Ensuring Responsible and Effective Government Use of AI
- Issue guidance for agencies’ use of AI
- Help agencies acquire specified AI products and services faster, more cheaply and more effectively
- Accelerate the rapid hiring of AI professionals
6.3.2 USA AI Legislations and Proposed Bills
- AI Training Act
- National AI Initiative Act
- Algorithmic Accountability Act (proposed)
- Transparent Automated Governance Act (proposed)
- Global Technology Leadership Act (proposed)
6.3.3 5 Trends to Watch: 2024 Artificial Intelligence
Banner Year for Artificial Intelligence (AI) in Health
- Continued innovation and investment in AI in areas from drug design to new devices to clinical decision support to documentation and revenue cycle management (RCM) to surgical augmented reality (AR) and more, in 2024
Congress and AI Regulation
- Congress will also debate legislation relating to the use of AI in elections, intelligence operations, military weapons systems, surveillance and reconnaissance, logistics, cybersecurity, health care, and education.
New State and City Laws Governing AI’s Use in HR Decisions
- mandating notice to employees regarding the use of AI in HR-function software as well as restricting its use absent human oversight.
Data Privacy Rules Collide with Use of AI
- a key issue as companies apply transparency, consent, automated decision making, and risk assessment requirements in existing privacy laws to AI personal information processing
Continued Rise in AI-Related Copyright & Patent Filings, Litigation
- including patent eligibility and inventorship for AI-related innovations, the scope of protection for works produced using AI, and the treatment of copyrighted works in AI training
- IP holders are likely to become more sophisticated in how they integrate AI into their innovation and authorship workflows.
6.3.4 EU AI ACT
In April 2021 , the European Commission proposed the first EU regulatory framework for AI. It says that AI systems that can be used in different applications are analyzed and classified according to the risk they pose to users.
The different risk levels will mean more or less regulation. Once approved, these will be the world’s first rules on AI.
The European Union has made a momentous decision when it approved the AI Act, the first legislation to regulate the much-discussed artificial intelligence (AI) that promises to revolutionize our lives.
After a marathon three-day negotiation by the trialogue composed of the European Commission, Council, and Parliament, on December 8, 2023 , they approved the AI Act to regulate the use of artificial intelligence systems in the European Union.
6.3.5 The Milestone of the AI ACT Implementation
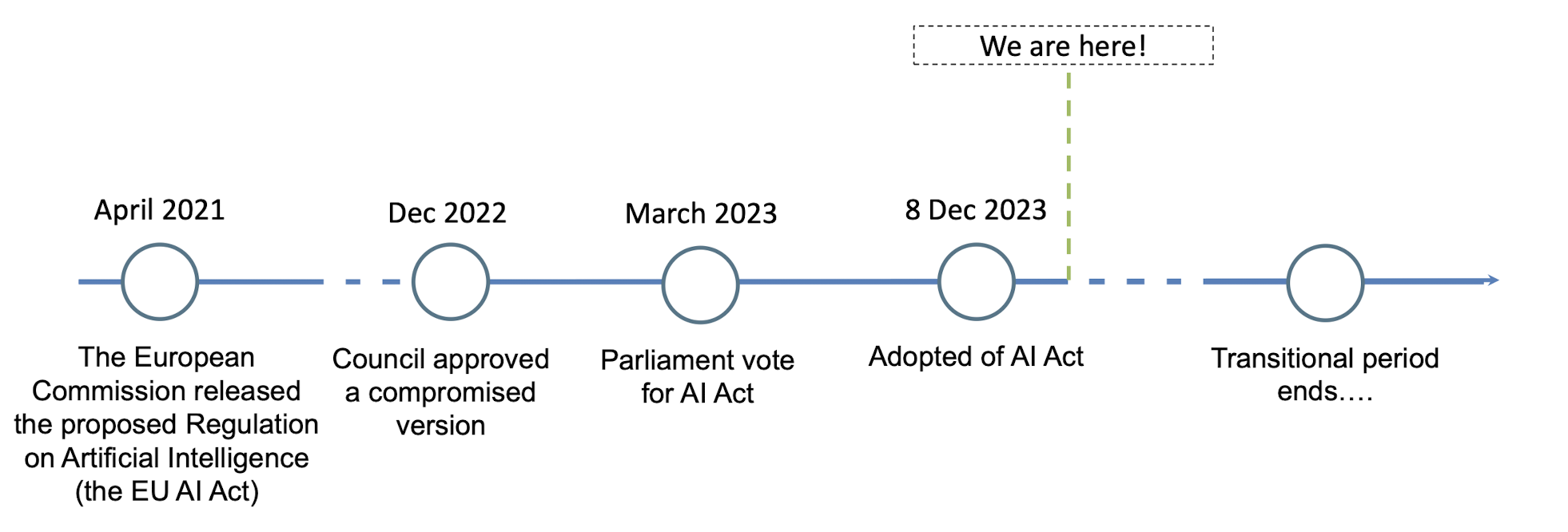
6.3.6 Two Key Concepts in EU AI ACT: (I) AI & AIS Definition
Definition of AI
- The EU AI Act defines AI as “software that is able to perform tasks that would normally require human intelligence, such as understanding natural language, recognizing images, or making decisions.”
- This definition is broad and includes a wide range of AI applications, from simple chatbots to more complex systems like self-driving cars.
Definition of AI System
- The definition of artificial intelligence systems in the AI Act aligns with internationally recognized criteria, following OECD guidelines, which defines an AI system as the following:
- a machine-based system that, for explicit or implicit objectives, infers, from the input it receives, how to generate outputs such as predictions, content, recommendations, or decisions that can influence physical or virtual environments.
6.3.7 Two Key Concepts in EU AI ACT: (II) Risk Based Approach
- Risk-based approach:
- The EU AI Act takes a risk-based approach to regulating AI, meaning that the level of regulation will depend on the level of risk posed by the AI system in question.
- High-risk AI systems, such as those used in critical infrastructure or healthcare, will be subject to more stringent regulations than low-risk systems, such as those used in marketing or customer service.
6.3.8 AI Act: Different Rules for Different Risk Levels
- The new rules establish obligations for providers and users depending on the level of risk from artificial intelligence. While many AI systems pose minimal risk, they need to be assessed.
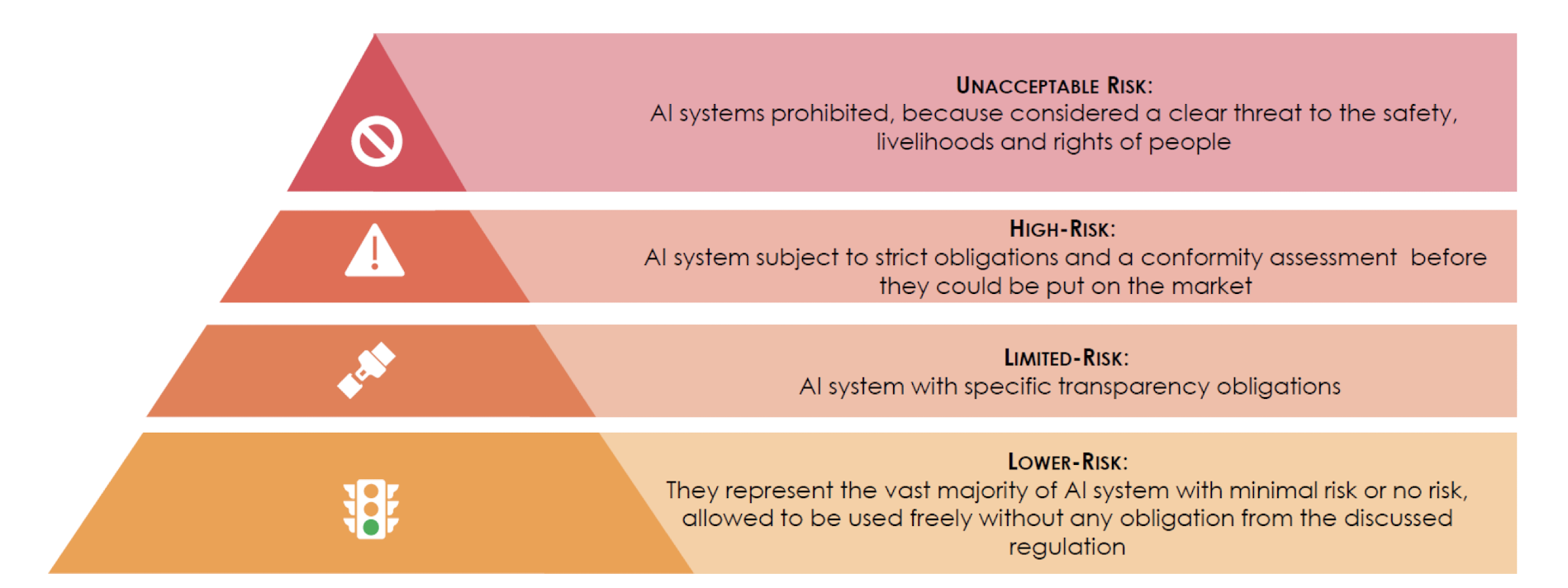
6.3.9 Unacceptable Risk
Unacceptable risk AI systems are systems considered a threat to people and will be banned. They include:
- Cognitive behavioral manipulation of people or specific vulnerable groups: for example voice-activated toys that encourage dangerous behavior in children
- Social scoring: classifying people based on behavior, socio-economic status or personal characteristics
- Biometric identification and categorization of people
- Real-time and remote biometric identification systems , such as facial recognition
Some exceptions may be allowed for law enforcement purposes.
- “Real-time” remote biometric identification systems will be allowed in a limited number of serious cases, while “post” remote biometric identification systems, where identification occurs after a significant delay, will be allowed to prosecute serious crimes and only after court approval.
6.3.10 High Risk
- AI systems that negatively affect safety or fundamental rights will be considered high risk and will be divided into two categories:
AI systems that are used in products falling under the EU’s product safety legislation. This includes toys, aviation, cars, medical devices and lifts.
AI systems falling into specific areas that will have to be registered in an EU database:
- Management and operation of critical infrastructure
- Education and vocational training
- Employment, worker management and access to self-employment
- Access to and enjoyment of essential private services and public services and benefits
- Law enforcement
- Migration, asylum and border control management
- Assistance in legal interpretation and application of the law.
- All high-risk AI systems will be assessed before being put on the market and also throughout their lifecycle.
6.3.11 General purpose and generative AI
- Generative AI, like ChatGPT, would have to comply with transparency requirements:
- Disclosing that the content was generated by AI
- Designing the model to prevent it from generating illegal content
- Publishing summaries of copyrighted data used for training
- High-impact general-purpose AI models that might pose systemic risk, such as the more advanced AI model GPT-4, would have to undergo thorough evaluations and any serious incidents would have to be reported to the European Commission.
6.3.12 Limited Risk and Lower Risk
- Limited risk AI systems should comply with minimal transparency requirements that would allow users to make informed decisions.
- After interacting with the applications, the user can then decide whether they want to continue using it.
- Users should be made aware when they are interacting with AI.
- This includes AI systems that generate or manipulate image, audio or video content, for example deepfakes.
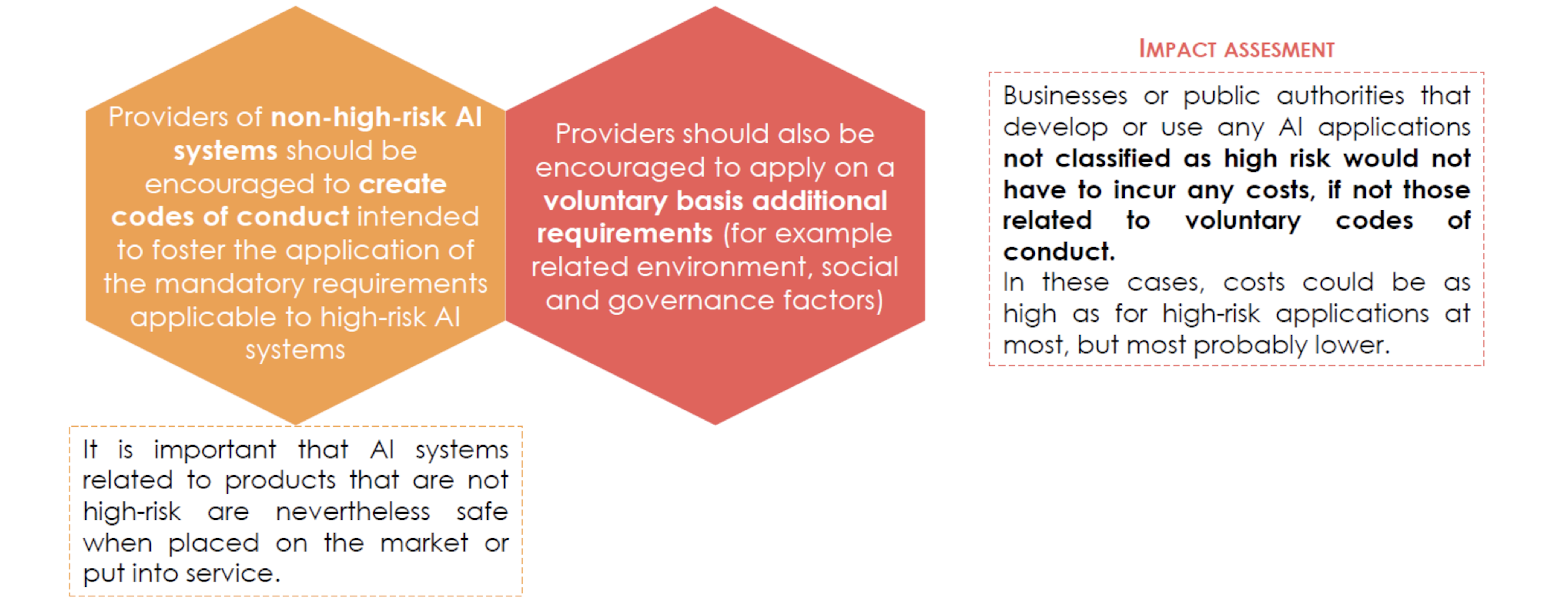
6.3.13 Banned Applications
- Recognizing the potential threat to citizens’ rights and democracy posed by certain applications of AI, the co-legislators agreed to prohibit:
- biometric categorization systems that use sensitive characteristics (e.g. political, religious, philosophical beliefs, sexual orientation, race);
- untargeted scraping of facial images from the internet or CCTV footage to create facial recognition databases;
- emotion recognition in the workplace and educational institutions;
- social scoring based on social behavior or personal characteristics;
- AI systems that manipulate human behavior to circumvent their free will ;
- AI used to exploit the vulnerabilities of people (due to their age, disability, social or economic situation).
6.3.14 Law Enforcement Exemptions
Negotiators agreed on a series of safeguards and narrow exceptions for the use of biometric identification systems (RBI) in publicly accessible spaces for law enforcement purposes, subject to prior judicial authorization and for strictly defined lists of crime.
“Real-time” RBI would comply with strict conditions and its use would be limited in time and location, for the purposes of:
- targeted searches of victims (abduction, trafficking, sexual exploitation),
- prevention of a specific and present terrorist threat , or
- the localization or identification of a person suspected of having committed one of the specific crimes mentioned in the regulation (e.g. terrorism, trafficking, sexual exploitation, murder, kidnapping, rape, armed robbery, participation in a criminal organization, environmental crime).
6.3.15 Obligations for High-Risk Systems
For AI systems classified as high-risk (due to their significant potential harm to health, safety, fundamental rights, environment, democracy and the rule of law), clear obligations were agreed.
Members of the European Parliament (MEPs) successfully managed to include a mandatory fundamental rights impact assessment , among other requirements, applicable also to the insurance and banking sectors.
AI systems used to influence the outcome of elections and voter behavior , are also classified as high-risk.
Citizens will have a right to launch complaints about AI systems and receive explanations about decisions based on high-risk AI systems that impact their rights.
6.3.16 Guardrails for General Artificial Intelligence Systems
- To account for the wide range of tasks AI systems can accomplish and the quick expansion of its capabilities, it was agreed that general-purpose AI (GPAI) systems, and the GPAI models they are based on, will have to adhere to transparency requirements as initially proposed by Parliament.
- These include drawing up technical documentation , complying with EU copyright law and disseminating detailed summaries about the content used for training.
- For high-impact GPAI models with systemic risk , Parliament negotiators managed to secure more stringent obligations.
- If these models meet certain criteria they will have to conduct model evaluations, assess and mitigate systemic risks , conduct adversarial testing , report to the Commission on serious incidents, ensure cybersecurity and report on their energy efficiency.
- MEPs also insisted that, until harmonized EU standards are published, GPAIs with systemic risk may rely on codes of practice to comply with the regulation.
6.3.17 Measures to Support Innovation and SMEs
MEPs wanted to ensure that businesses, especially SMEs, can develop AI solutions without undue pressure from industry giants controlling the value chain.
To this end, the agreement promotes so-called regulatory sandboxes and real-world-testing , established by national authorities to develop and train innovative AI before placement on the market.
6.3.18 Sanctions and Entry into Force
- Non-compliance with the rules can lead to fines ranging from
35 million euro
or
7% of global turnover to 7.5 million
or
1.5 % of turnover ,
- depending on the infringement and size of the company.
6.3.19 AI ACT’s Main Requirements Overview

6.3.20 Notable Chinese AI Governance Policy Documents
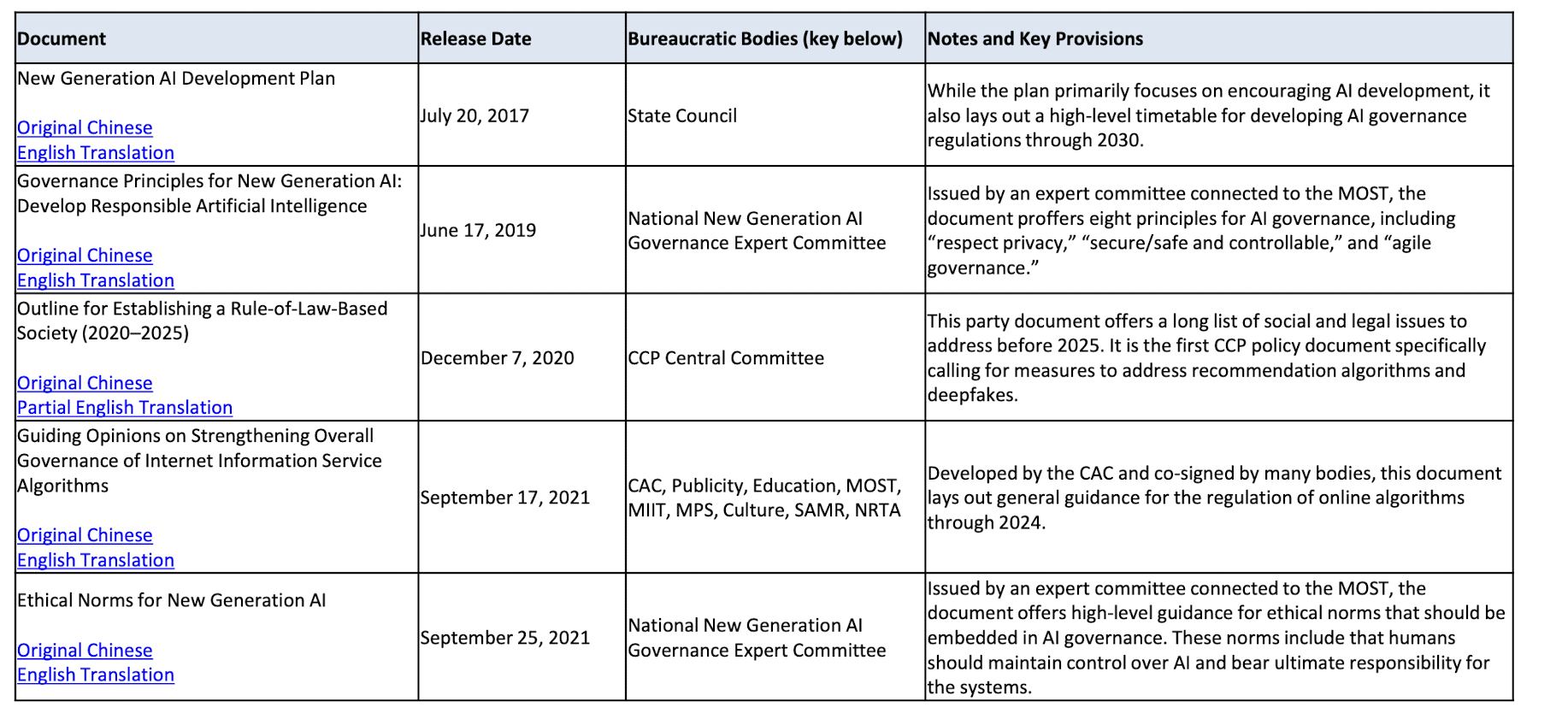
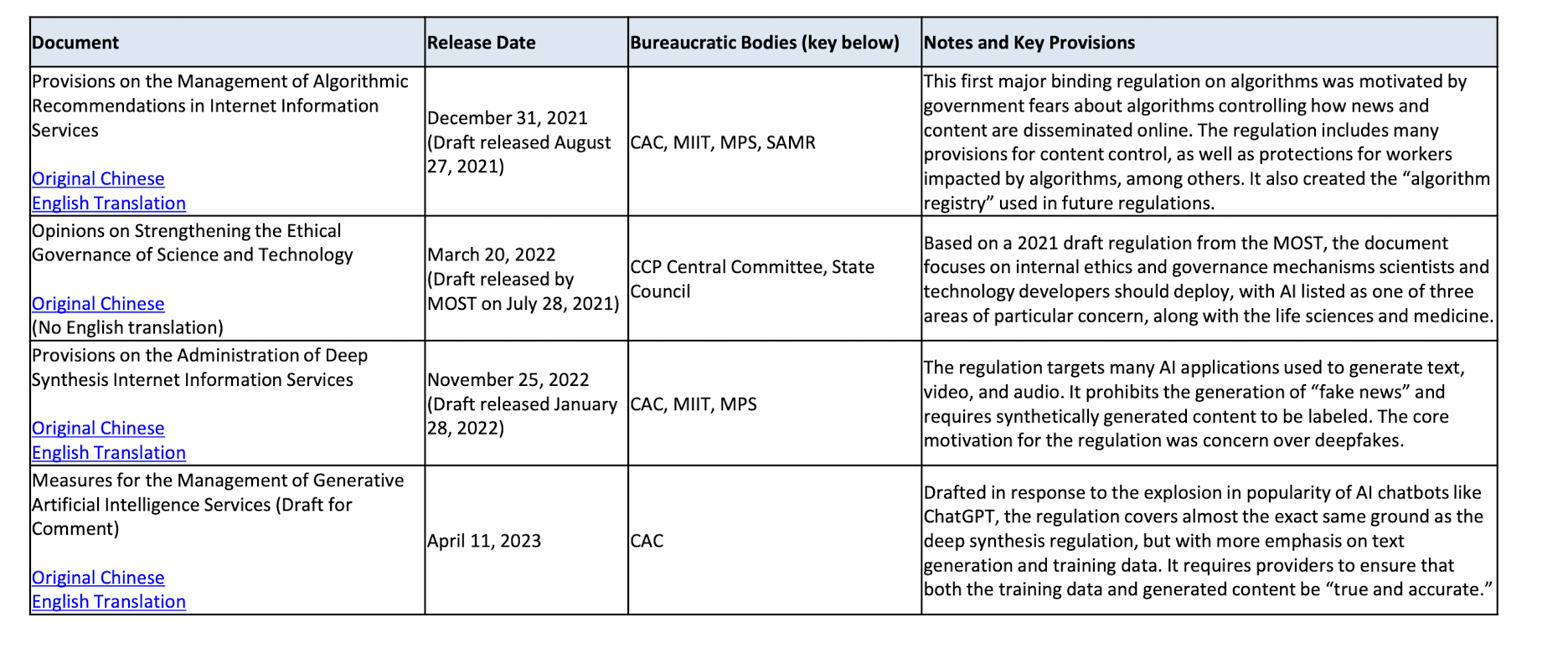
6.3.21 China’s AI Regulations and How They Get Made
China is in the midst of rolling out some of the world’s earliest and most detailed regulations governing artificial intelligence (AI).
These include measures governing recommendation algorithms—the most omnipresent form of AI deployed on the internet—as well as new rules for synthetically generated images and chatbots in the mold of ChatGPT.
China’s emerging AI governance framework will reshape how the technology is built and deployed within China and internationally, impacting both Chinese technology exports and global AI research networks.
6.3.22 The Policy Funnel of China’s AI Governance
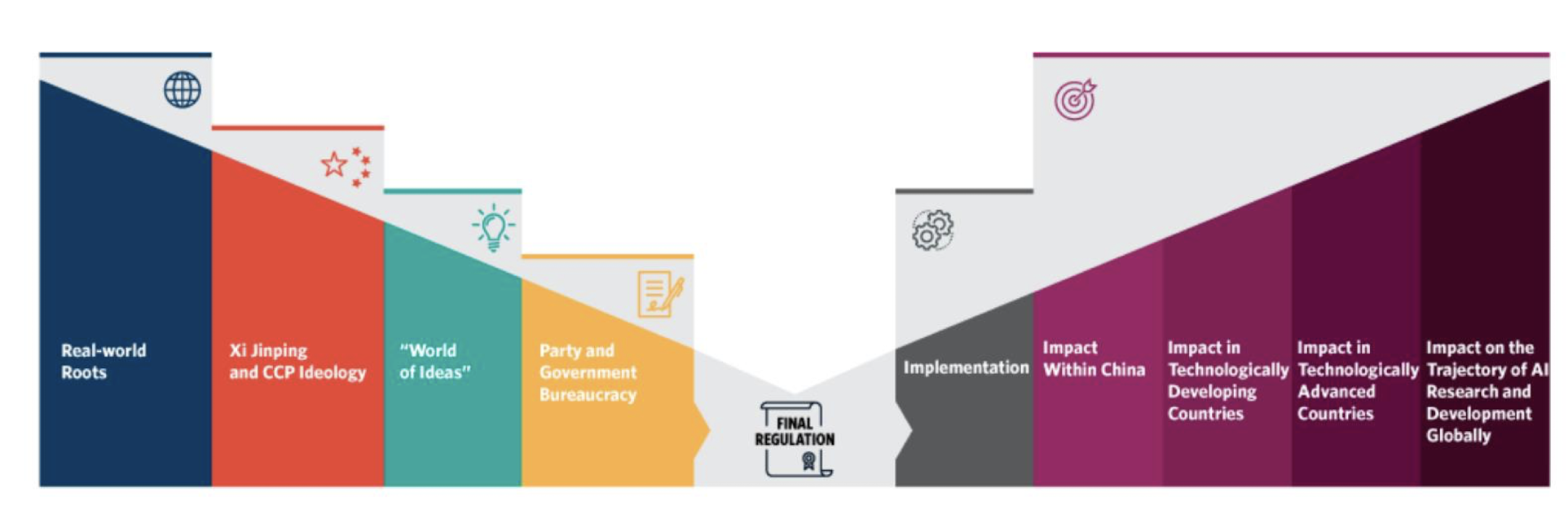
- China’s three most concrete and impactful regulations on algorithms and AI are its 2021 regulation on recommendation algorithms , the 2022 rules for deep synthesis (synthetically generated content), and the 2023 draft rules on generative AI.
6.3.23 Ethical Norms for New Generation Artificial Intelligence
《新一代人工智能伦理规范》
- On 25 Sep 2023 , the National New Generation Artificial Intelligence Governance Specialist Committee published Ethical Norms for New Generation Artificial Intelligence ( Ethical Norms ), whose purpose is to incorporate ethics into the entire artificial intelligence (AI) life cycle and to provide ethical guidance to natural persons, legal persons, and other related institutions engaged in AI-related activities.
- Full consideration was given to the ethical concerns of all sectors of today’s society about privacy, bias, discrimination, fairness , and so on.
- Ethical Norms puts forward six basic ethical requirements , namely:
- the advancement of human welfare,
- the promotion of fairness and justice,
- the protection of privacy and security,
- the assurance of controllability and trustworthiness,
- the strengthening of accountability, and
- improvements to the cultivation of ethics.
7. Computer Related Crime Case Studies
7.1 Ordinances Covering Computer-Related Crimes
- To cover computer-related crimes, Telecommunications Ordinance (Cap. 106), Crimes Ordinance (Cap. 200) and Theft Ordinance (Cap. 210) have been amended to create some new offences and broaden the coverage of existing offences.

Theft Ordinance (Cap. 210) deals with offences of destroying, defacing, concealing or falsifying records kept by computer.
Personal Data (Privacy) Ordinance (Cap. 486) deals with protection of personal privacy.
Gambling Ordinance (Cap. 148) combat illegal gambling conducted on the Internet.
Unsolicited Electronic Messages Ordinance (Cap. 593) prohibits fraud activities related to the sending of multiple commercial electronic messages.
7.1.1 Access to Computer with Criminal or Dishonest Intent
Cap. 200 Crimes Ordinance
- Section 161 Access to computer with criminal or dishonest intent (有犯罪或不誠實意圖而取用電腦) ;
- Any person who obtains access to a computer—
a) with intent to commit an offence;
b) with a dishonest intent to deceive;
c) with a view to dishonest gain for himself or another; or
d) with a dishonest intent to cause loss to another,
- Any person who obtains access to a computer—
- whether on the same occasion as he obtains such access or on any future occasion, commits an offence and is liable on conviction upon indictment to imprisonment for 5 years.
- For the purposes of subsection (1) gain ( 獲益 ) and loss ( 損失 ) are to be construed as extending not only to gain or loss in money or other property, but as extending to any such gain or loss whether temporary or permanent; and—
a) gain ( 獲益 ) includes a gain by keeping what one has, as well as a gain by getting what one has not; and
b) loss ( 損失 ) includes a loss by not getting what one might get, as well as a loss by parting with what one has.
7.2 Electronic Transactions Ordinance
Enacted on 7 January 2000 to facilitate the use of electronic transactions for commercial and other purposes.
It gives electronic records and digital signatures used in electronic transactions the same legal status as that of their paper-based counterparts.
It also enables the Postmaster General to provide the services of a certification authority.
Please visit https://www.elegislation.gov.hk/hk/cap553!en for more information.
7.3 The Unsolicited Electronic Messages Ordinance
( 非應邀電子訊息條例 )
- The Unsolicited Electronic Messages Ordinance(UEMO) was enacted in May 2007 with an aim to regulate the sending of all forms of commercial electronic messages (CEMs) with the “Hong Kong link”.
- It establishes the rules for sending CEMs such as providing accurate sender information and unsubscribe facilities as well as the launch of the do-not-call registers, and prohibits professional spamming activities such as the use of unscrupulous means to gather/generate recipient lists for sending CEMs without the consent of recipients, and fraudulent activities related to the sending of multiple CEMs.
- For detail, please visit OFCA website and
- https://www.elegislation.gov.hk/hk/cap593!en.
7.4 Personal Data (Privacy) Ordinance
- To protect the privacy interests of living individuals in relation to personal data.
- The Ordinance covers any data relating directly or indirectly to a living individual (data subject), from which it is practicable to ascertain the identity of the individual and which are in a form in which access or processing is practicable.
- It applies to any person (data user) that controls the collection, holding, processing or use of personal data.
- Please visit Privacy Commissioner for Personal Data for more information.
7.5 ==Copyright Ordinance==
Hong Kong’s new Copyright Ordinance came into effect on 27 June 1997.
It provides comprehensive protection for recognized categories of literary, dramatic, musical and artistic works, as well as for films, television broadcasts and cable diffusion, and works made available to the public on the Internet.
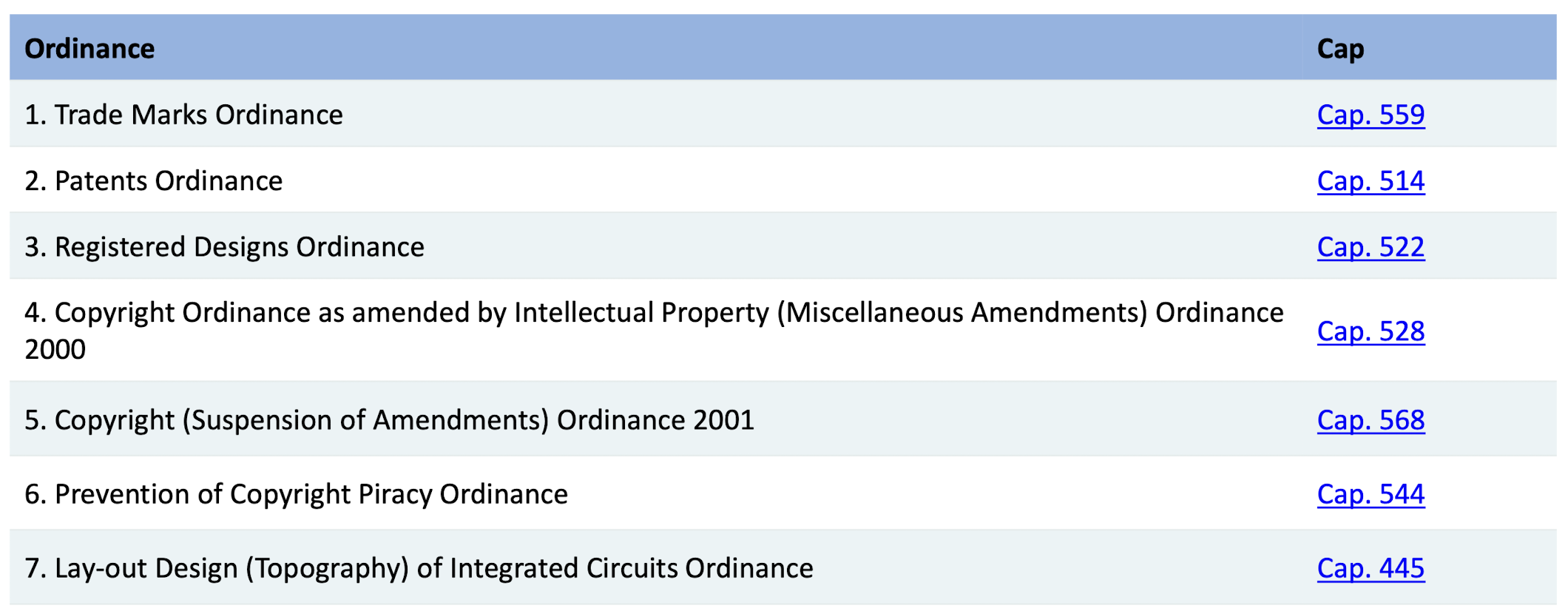
7.6 Other Related Ordinances (I)
In many cases, although no explicit reference to the cyber environment is made, the relevant legislation may be interpreted to cover both the physical and the virtual worlds. For example, the provisions of the Personal Data (Privacy) Ordinance are equally applicable to the cyber environment as the physical environment.
Many other legislative provisions refer to “computer” or similar terms.

7.6.1 Monitoring and Personal Data Privacy at Work
The use of video cameras to monitor domestic helpers’ activities is in general an intrusion of privacy. Before using this monitoring method, employers must seriously consider whether it is necessary to do so, and whether there are alternative means available.
In the event of a complaint made to the Privacy Commissioner, the alleged employers may be called upon to explain and prove the initial evidence or suspicion which justifies the use of video monitoring.
If you decide to implement video monitoring at home, you should note 3 important points:
a) reasonableness of the monitoring practice,
b) openness of the monitoring practice, and
c) use and retention of video records.
https://www.pcpd.org.hk/english/publications/files/DH_e.pdf
7.6.1.1 a) Reasonableness of the Monitoring Practice
The existence of the following situations may justify covert monitoring:
- there is a reasonable suspicion that a child or an elderly person has suffered (or is likely to suffer) from abuse or neglect, e.g. there are signs of unexplained injuries found on the body of that person, or where abnormal behaviors are observed in the domestic helper;
- it is highly likely that the suspected abuse occurred at home ; and
- there is no realistic alternative to obtaining evidence of these abusive acts other than by way of covert monitoring.
However, employers should note that no cameras (whether hidden or not) should capture images showing activities inside the private area where the domestic helper rests after work.
7.6.1.2 b) Openness of the Monitoring Practice
It is important that domestic helpers be notified of the presence of any video monitoring system in the premises where they work.
This notification should not be omitted except in very exceptional situations such as to collect evidence of abuse based on reasonable suspicion. It is recommended that a written notification should be given instead of an oral one.
Employers are reminded that such notification does not confer upon them a legal right to adopt employee monitoring under all circumstances nor does it release them from their obligations under the Ordinance to observe the six data protection principles.
7.6.1.3 c) Use and Retention of Video Records
Employers must ensure that video records are only used for the purposes stated in the notification given to domestic helpers or a directly related purpose , unless otherwise permitted by law.
It is recommended that video records which contain the personal data of domestic helpers be retained for not more than 7 days.
A longer retention period may be considered if the recorded data are required for evidentiary purposes (e.g. to assist an investigation conducted by the Privacy Commissioner or the police).
7.6.2 Background
The complainant was photographed on a street by a photographer working for Eastweek magazine (“Eastweek”).
The complainant’s photograph, together with some other women being photographed, was published in an article in Eastweek with unflattering and negative comments about her fashion style.
The photograph was taken and published without the complainant’s knowledge or consent.
The Privacy Commissioner initially found that there was a breach of DPP1(2)(b) on the part of Eastweek in collecting the complainant’s personal data by an unfair means. Eastweek applied for a judicial review of the Privacy Commissioner’s decision, the application for which was dismissed by the Court of First Instance.
Eastweek further appealed to the Court of Appeal against the dismissal of the judicial review application and the appeal was allowed.
7.6.3 Collecting Personal Data and Relevance of Identity
The Court held that in the act of personal data collection, the data user must be compiling information about an identified person or about a person whom the data user intends to or seeks to identify.
What was crucial in the case was the complainant’s anonymity and the irrelevance of her identity to the photographer, the reporter and Eastweek.
The Court held that taking photograph of the complainant in the circumstances of the case did not constitute an act of collection of personal data of the complainant.
The Court stressed that the press or other media organisations do not fall outside the scope of the PDPO. If an organization engages in collecting personal data, the provisions of the PDPO squarely apply.
The Court further emphasized that while the complainant would be entirely justified in regarding the article and the photograph.
7.6.4 Implications in the Digital Era
If a person’s image is captured by AI installed in the CCTV system with intent to ascertain his identity , this may constitute collection of personal data, presumably by the operator of the CCTV system in the first place.
When footage in a CCTV system is being used to ascertain the identities of individuals by automated means, it would amount to collection of personal data of individuals, necessitating the application of the PDPO including the notification requirement under DPP1(Collection Purpose & Means) and the limitation of use requirement under DPP3 (Use), … etc.
It advises operators of such CCTV systems to conduct a privacy impact assessment.
For details, please refer to “Guidance on CCTV Surveillance and Use of Drones”
7.7 Computer Related Crimes (HK cases)
7.7.1 Overall Technology Crime Figures
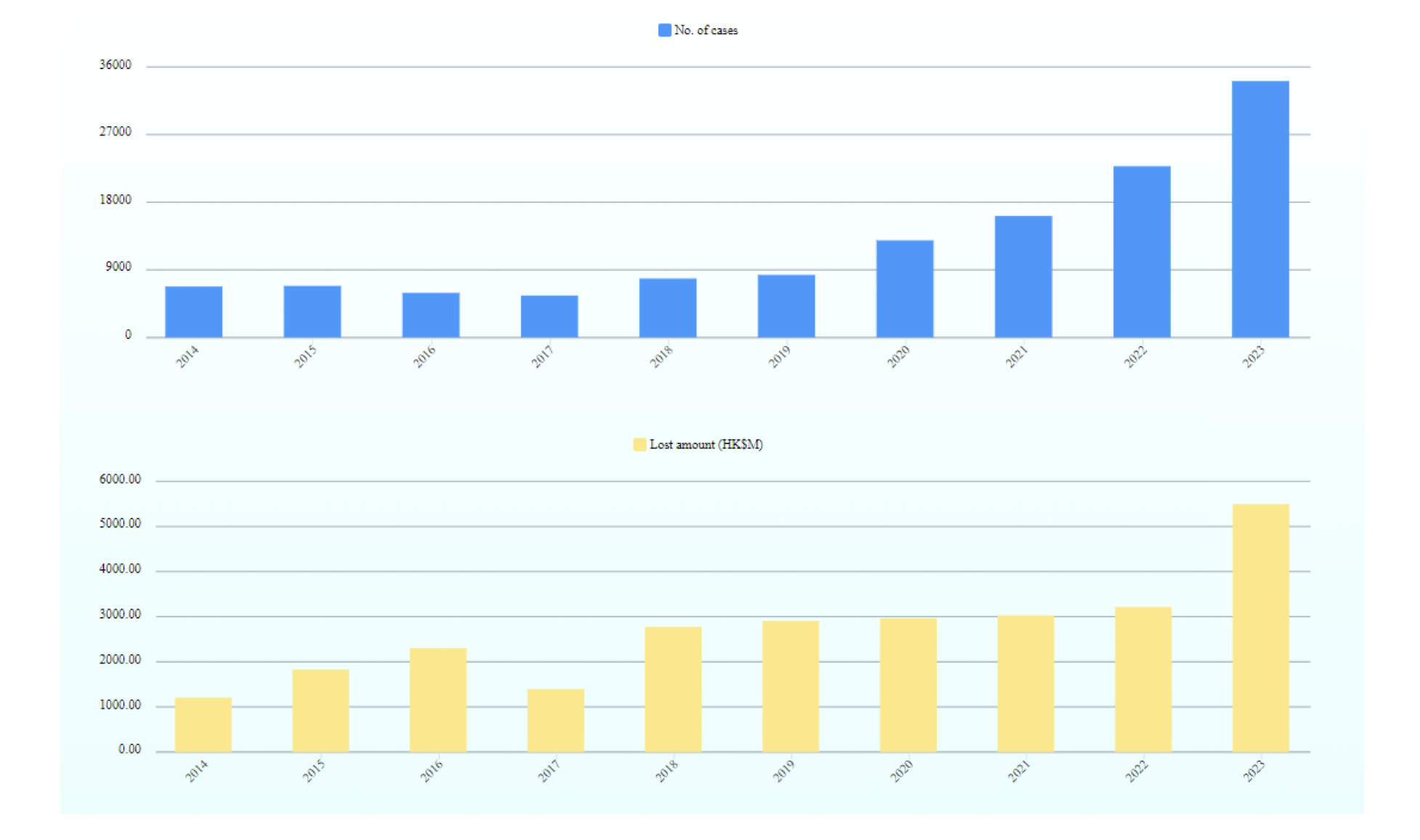
7.7.2 E-shopping Fraud
- It is a form of cybercrime that occurs with online customer transactions.
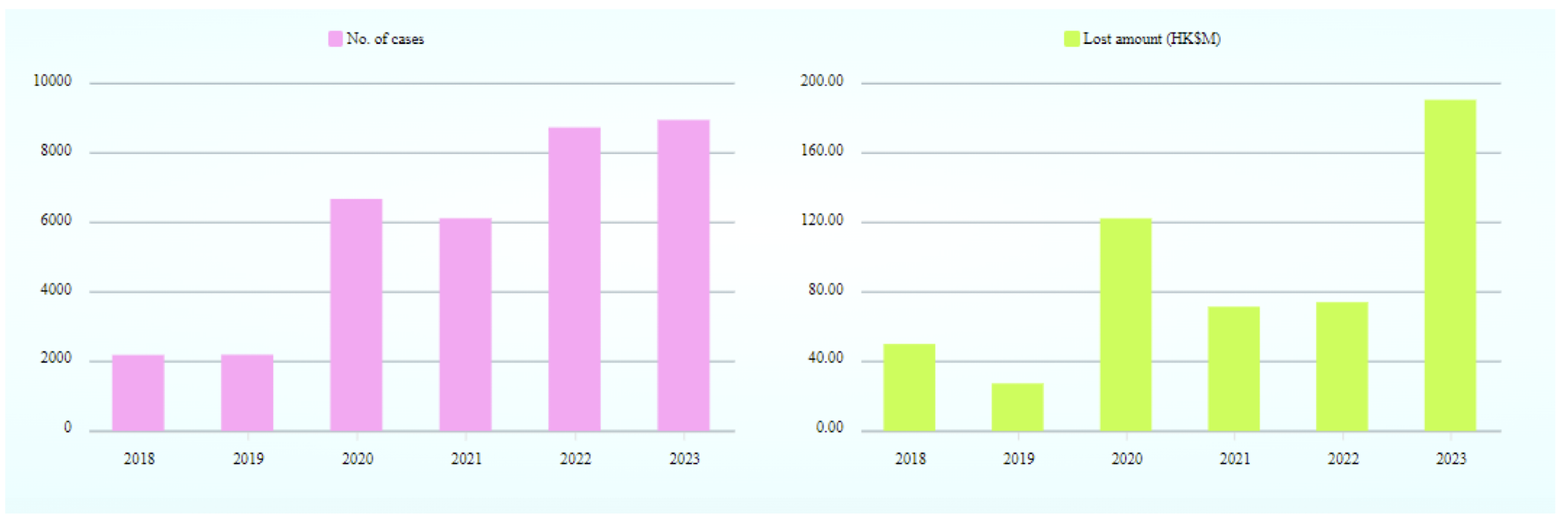
Most reports centre on sales of items such as handbags, concert tickets, travel packages and electronics
7.7.3 Email Scam
- It is a malicious email that aim to trick recipients into giving up their sensitive information, such as bank accounts and passwords.
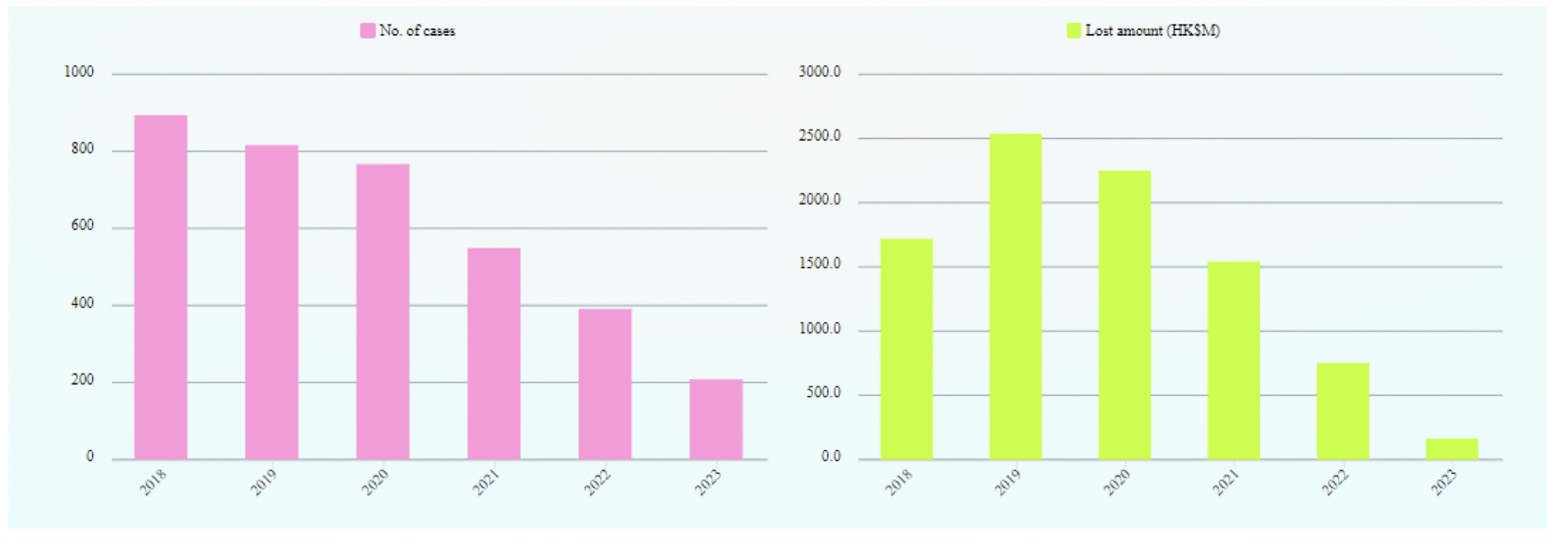
7.7.4 Theft of Online Account
- It is a crime in which an attacker uses fraud or deception to obtain personal or sensitive information from a victim and misuses it to act in the victim’s name.
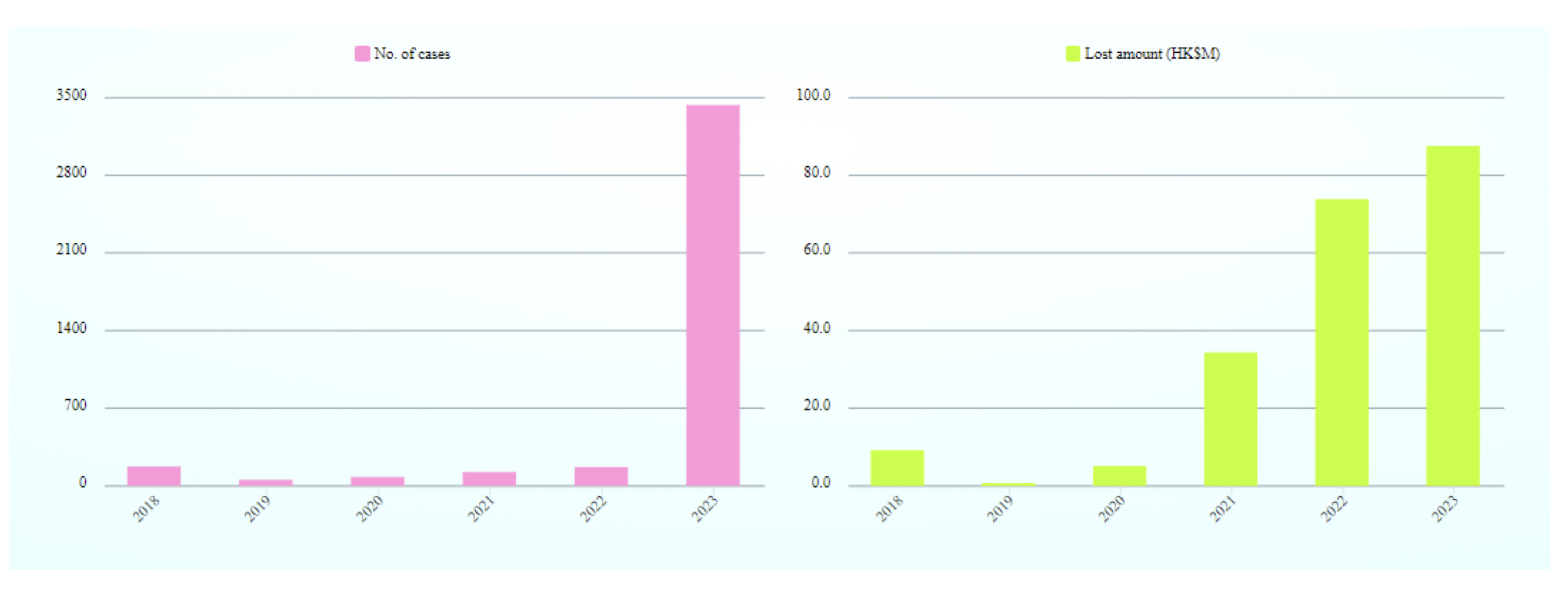
7.7.5 Social media scam
- People requesting you as a friend and asking for money. The fraudster may go so far as to pose as one of your friends, or send you a phishing link which takes you to a malicious site.
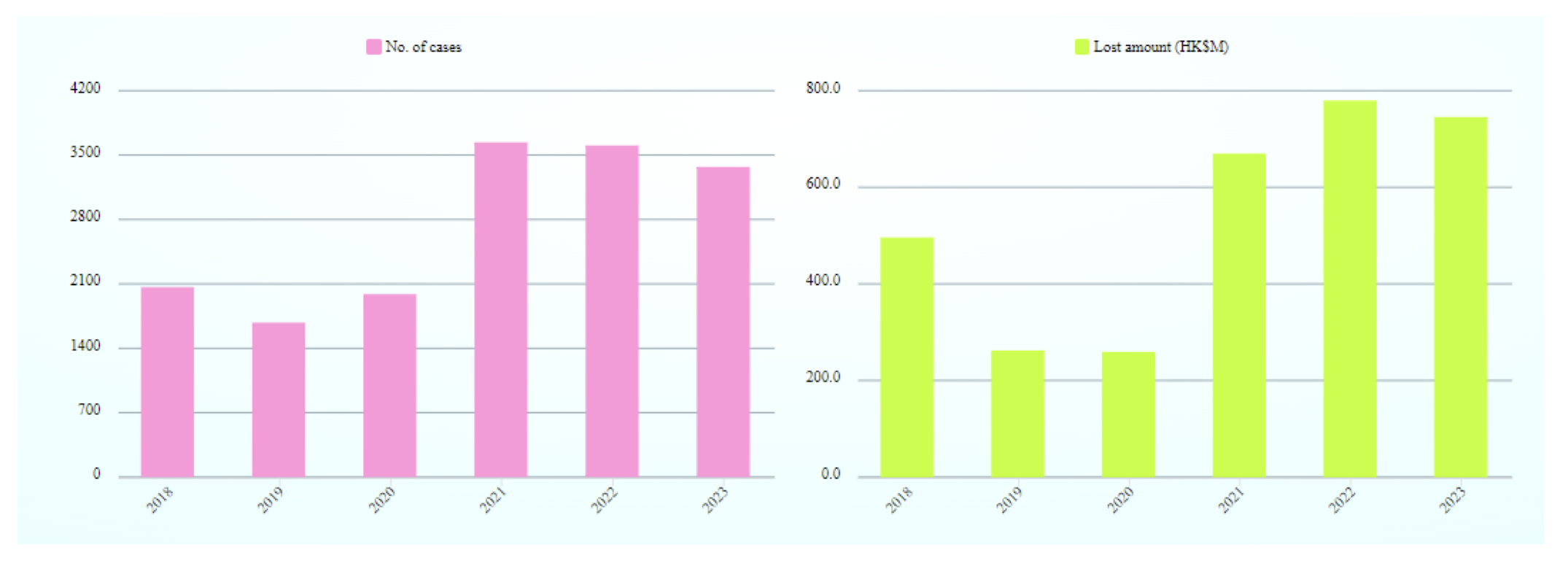
7.7.6 Romance scam
- It is a kind of scam led through social engineering techniques, used to leverage emotional relationships, to subsequently obtain financial gain or services. Scammers use dating or friendship to get your money.
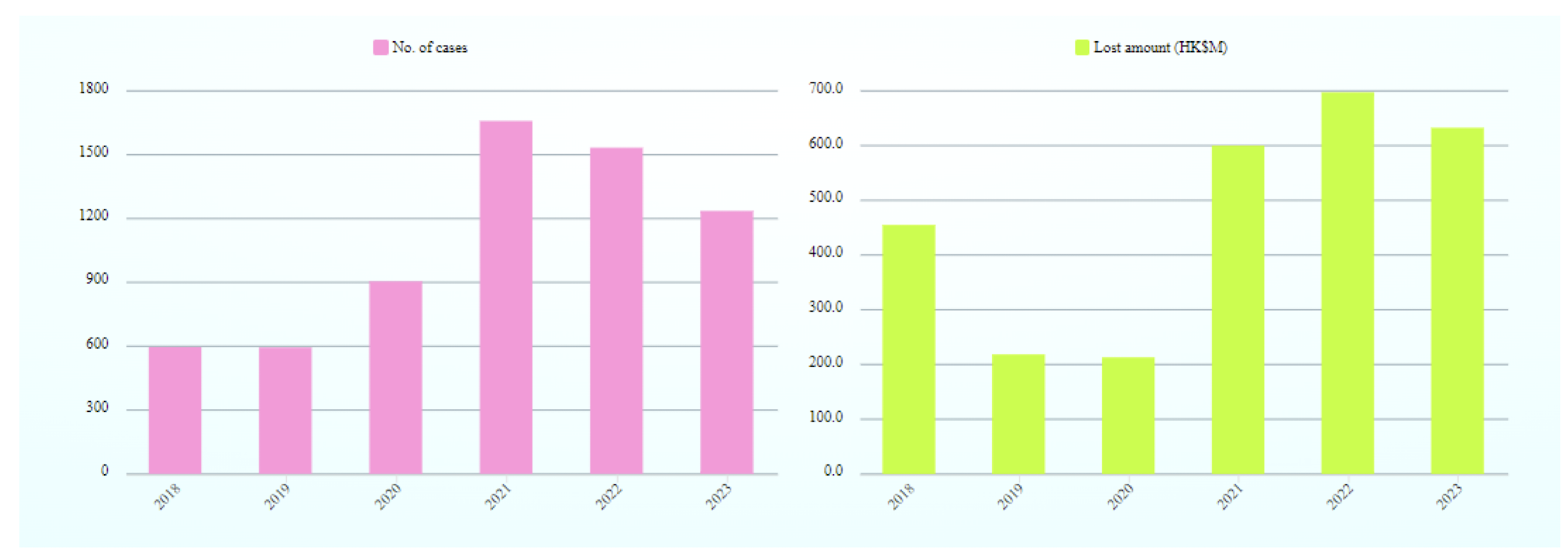
7.7.7 Naked chat related scam
- Scammers approach victims online via social networking platforms, dating apps or instant messaging software under the guise of ‘ friend making ’. Having earned the others’ trust, the scammers would sweet-talk the victims into undressing or performing indecent acts in front of a webcam.
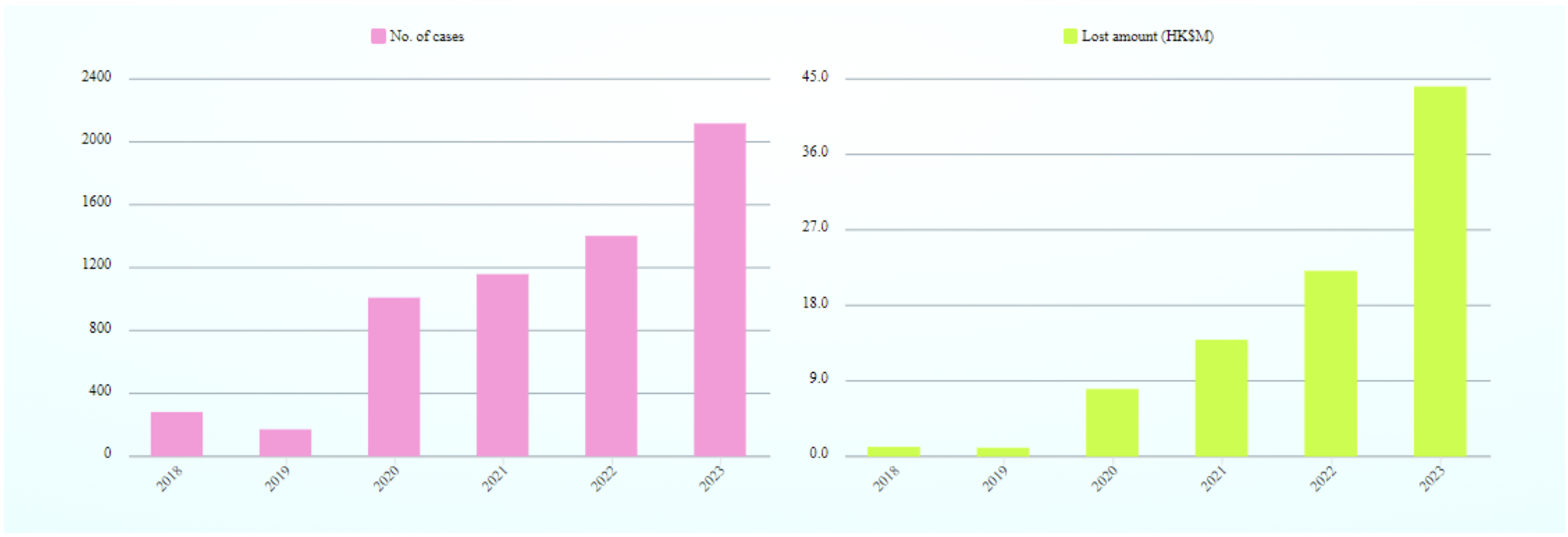
7.7.8 Compensated-dating related scam
- Compensated dating is a disguised form of prostitution in which clients pay for companionship, often including sex.
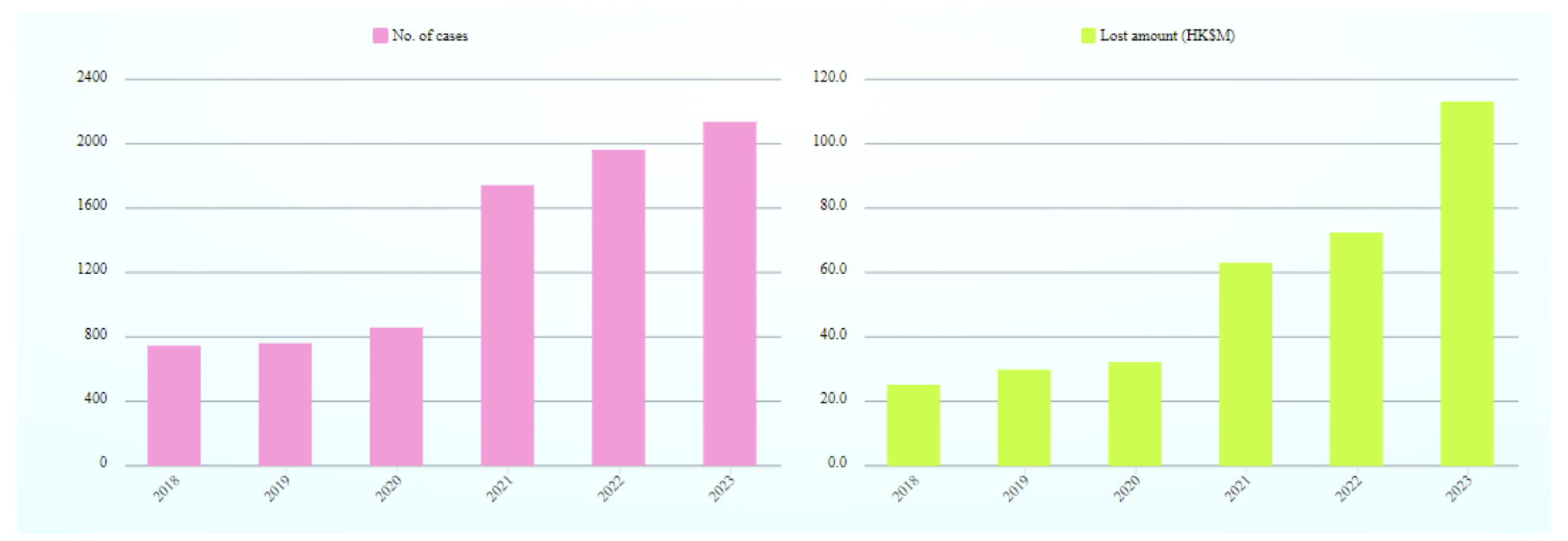
7.7.9 Online Investment Fraud
- Through online social media platform, forums or instant messengers, fraudsters promote investments with low risks and high returns and attract netizens to invest. However, most of the investment plans do not exist or are filled with traps.
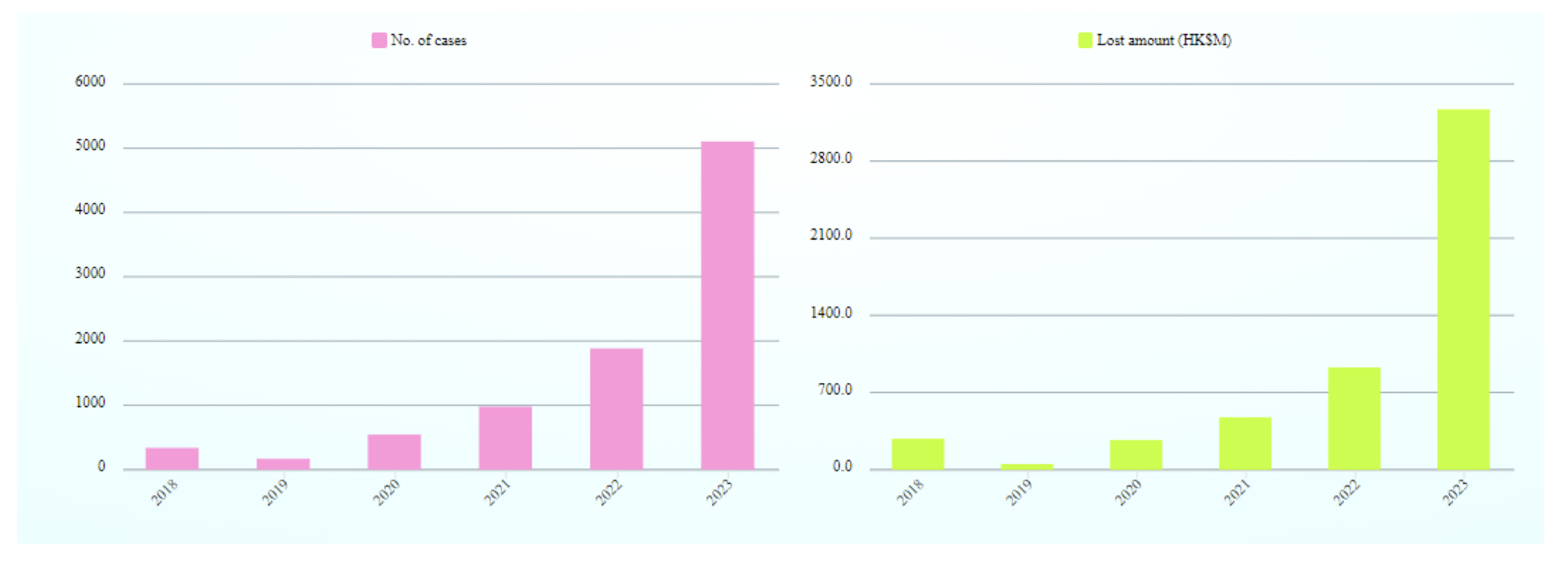
7.7.10 Online Employment Fraud
- Fraudsters post job advertisements on various social media platforms, forums or instant messengers, using various pretexts to lure job seekers into paying fees, guarantee fees or other fees. After snatching the money, fraudsters will be out of contact.
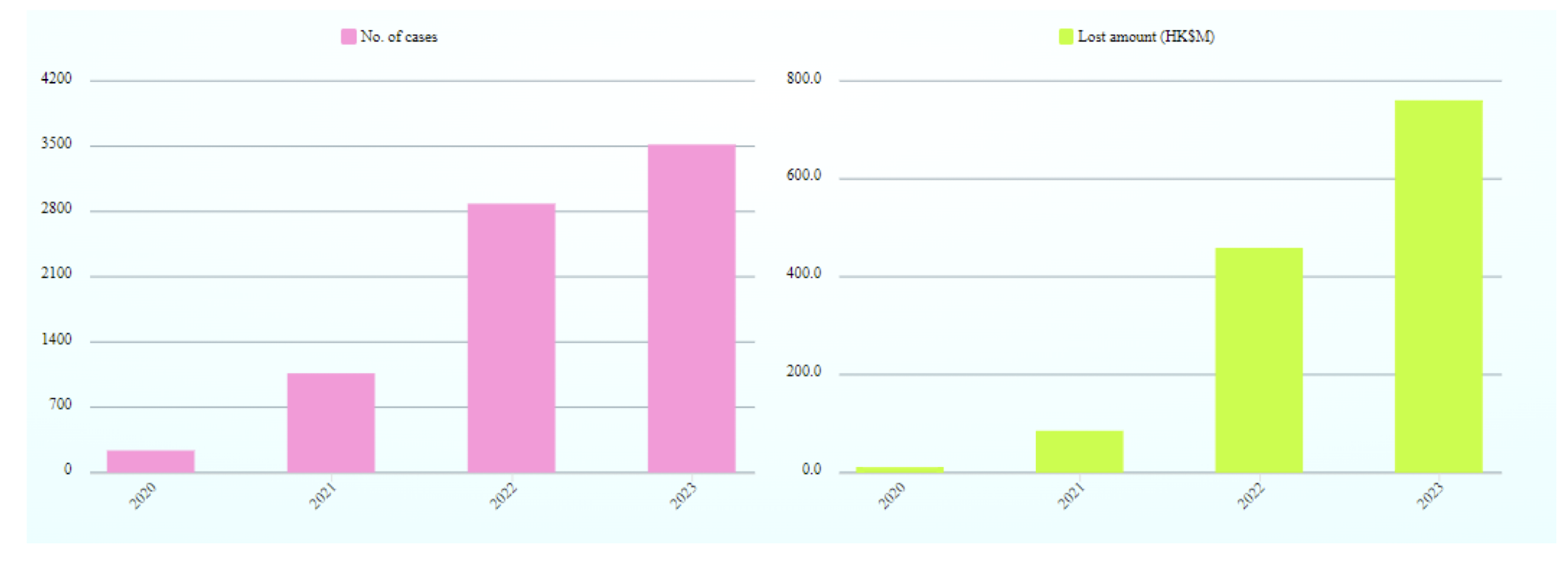
7.7.11 ==Overall No. of Cases Comparison==
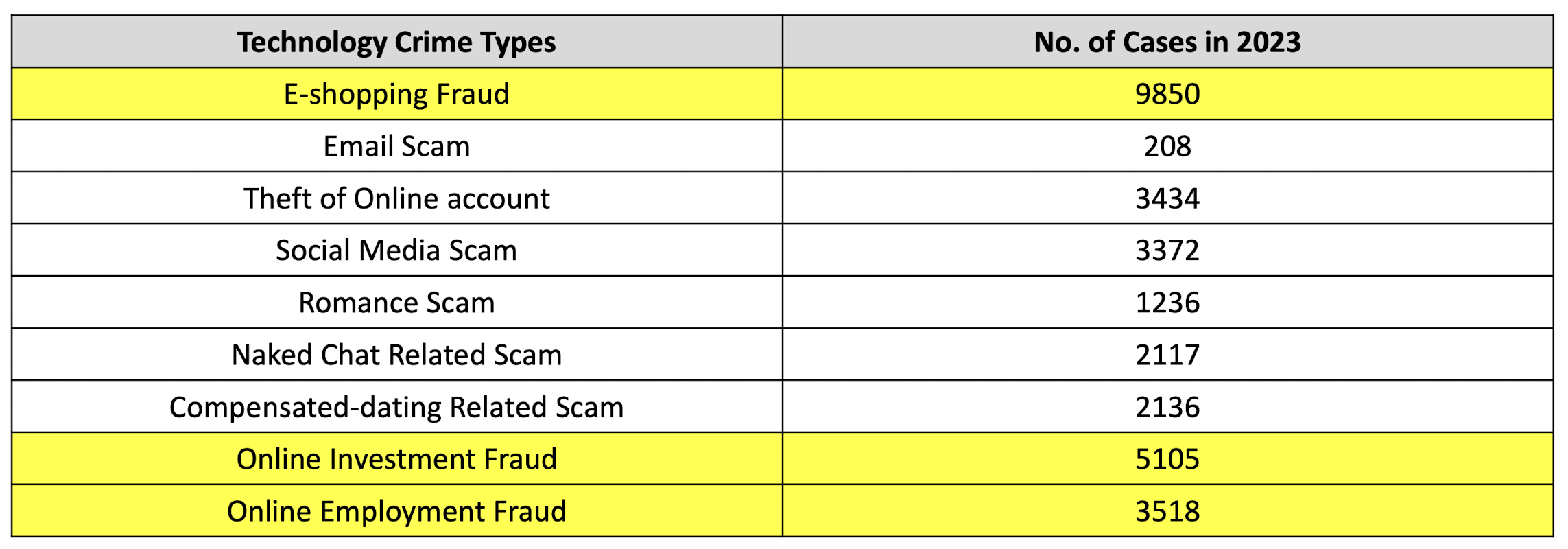
8. IP Management (ISO 56005)
8.1 Introduction of IP
8.1.1 What is Intellectual Property?
Intellectual Property exists in works including but not limited to actual products and processes; artistic, musical and literary works; and presentation of business ideas.
Intellectual Property is a collection of rights, with the major IP being copyright (protecting original creations), patents (protecting new inventions) and trademarks (protecting signs and logos).
8.1.2 IP and its sources
IP includes:
- Ideas
- Computer programs
- software programs
- designs
- research and development data
- inventions
- websites
- books
- journals
- media
- common knowledge
8.1.3 Guideline for Protecting Confidential Information

8.1.4 Four IP Protection Options
It includes:
Patents (Inventions such as processes and machines; Controversial areas such as business method and software)
Copyright (Original work of authorship and Copyrightable matter such as software, manuals and company documents)
Trademark (Word, phase or symbol for slogan, company name and product line)
Trade Secret (Any Confidential Info that gives the owner competitive benefit or economic value)
8.1.5 Patents
- A patent is granted by the patent office in each country or region to confer monopoly rights over a new invention in that country.
- Patents protect inventions of products and processes. They arise often, but not exclusively, from research in science, medicine, and engineering fields.
- The invention must be new (novel) and involve an inventive step , i.e., not be obvious to a person skilled in the art.
- Further, the invention must be useful, i.e., capable of industrial application.
- You should disclose your invention to Knowledge Transfer and Entrepreneurship Office (KTEO) , prior to any publication or presentation in any paper or electronic form, such as conference presentation, journal, posters and website, because such actions of public disclosure before filing a patent application damage novelty and thus the ability to obtain a valid patent.
8.1.6 Registered Designs (Design Patent)
A registered design, called a design patent in some jurisdictions (the official power to make legal decisions and judgments), protects the new design (the aesthetic as opposed to functional design) of an article applied by industrial process , such as furniture design, jewelry design, graphic design, etc.
Registration confers an exclusive right to manufacture and trade in articles made according to such a design or a design not substantially different from it.
You should disclose your design to the PolyU prior to any publication or presentation in any paper or electronic form, such as conference presentation, journal, posters and website, because such actions of public disclosure before filing a registration damage novelty and thus the ability to obtain a registration.
8.1.7 Copyright
- Copyright protects original work , i.e., work not copied from others.
- Copyright does not protect an idea but the form of expression of the idea. The expression can take the form of books, paintings, movies, pictures, computer programs, music and even performance.
- A copyright owner has the right to stop others from doing any of the acts restricted by copyright, such as copying his/her work in any material form, issuing copies to the public, making copies available on the internet, broadcasting works by wireless or cable, adapting it and so on.
- Copying refers also to storing a copyright work in any medium by electronic means.
- Software source code (human readable programs) is also protected as copyright.
8.1.8 Trademarks
A trademark is a distinctive sign that distinguishes the product or service associated with it from those of other entities.
A trademark is typically a name, word, phrase, logo, symbol, design image or a combination of these elements.
Some well-known examples are “Coca-Cola”, “iPad”, etc. While a user of an unregistered trademark may still enjoy some protection, a registered trademark owner holds a much stronger position to stop infringers.
“iPad” trademark story at https://www.businessinsider.com/how-apple-won-the-ipad-trademark-2015-3
8.1.9 Trade Secrets
A trade secret is also loosely referred to as “confidential information”.
A trade secret may or may not be patentable.
It is proprietary know-how which can be an invention or formula.
Unlike the IP described above, a trade secret has no expiry date as long as it can be kept confidential and still has distinctive value.
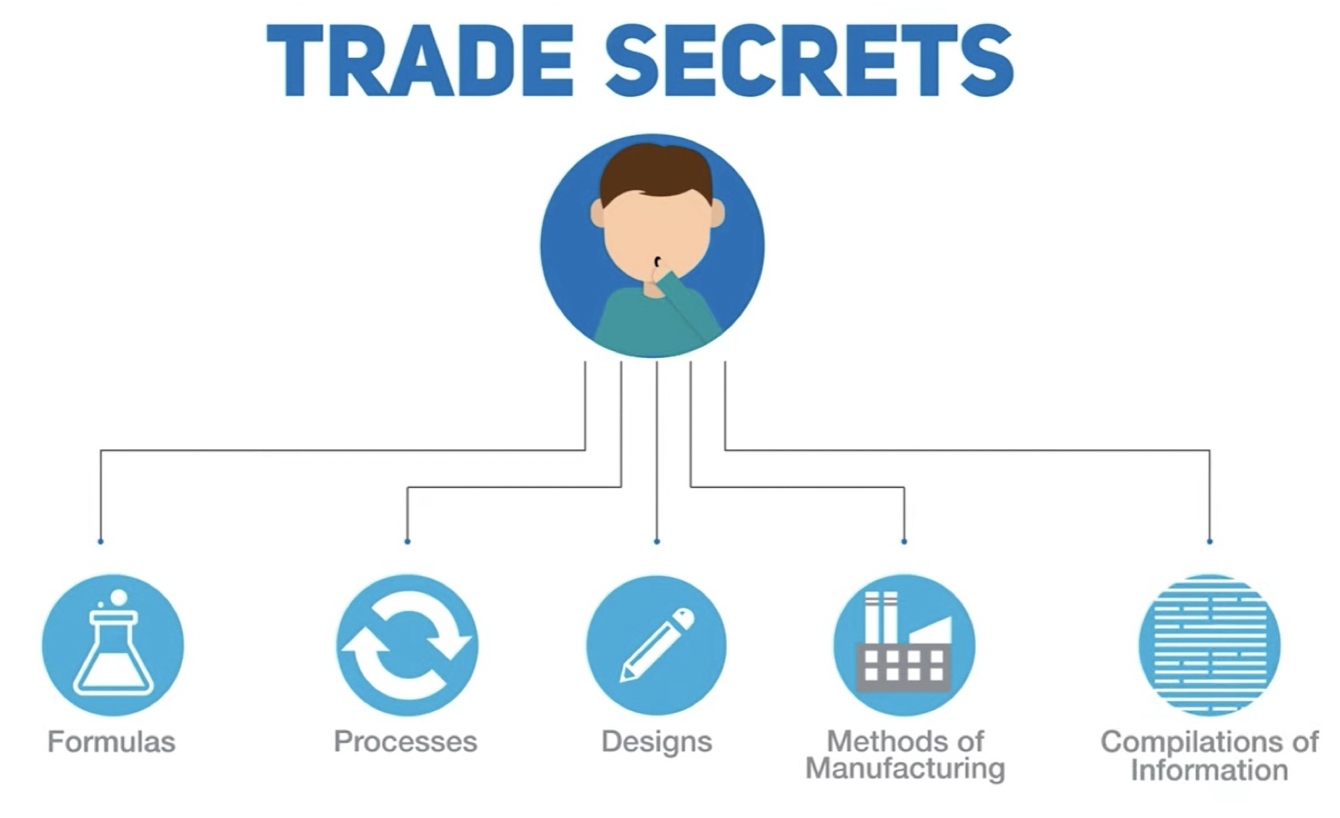
8.1.10 Excise to understand the different
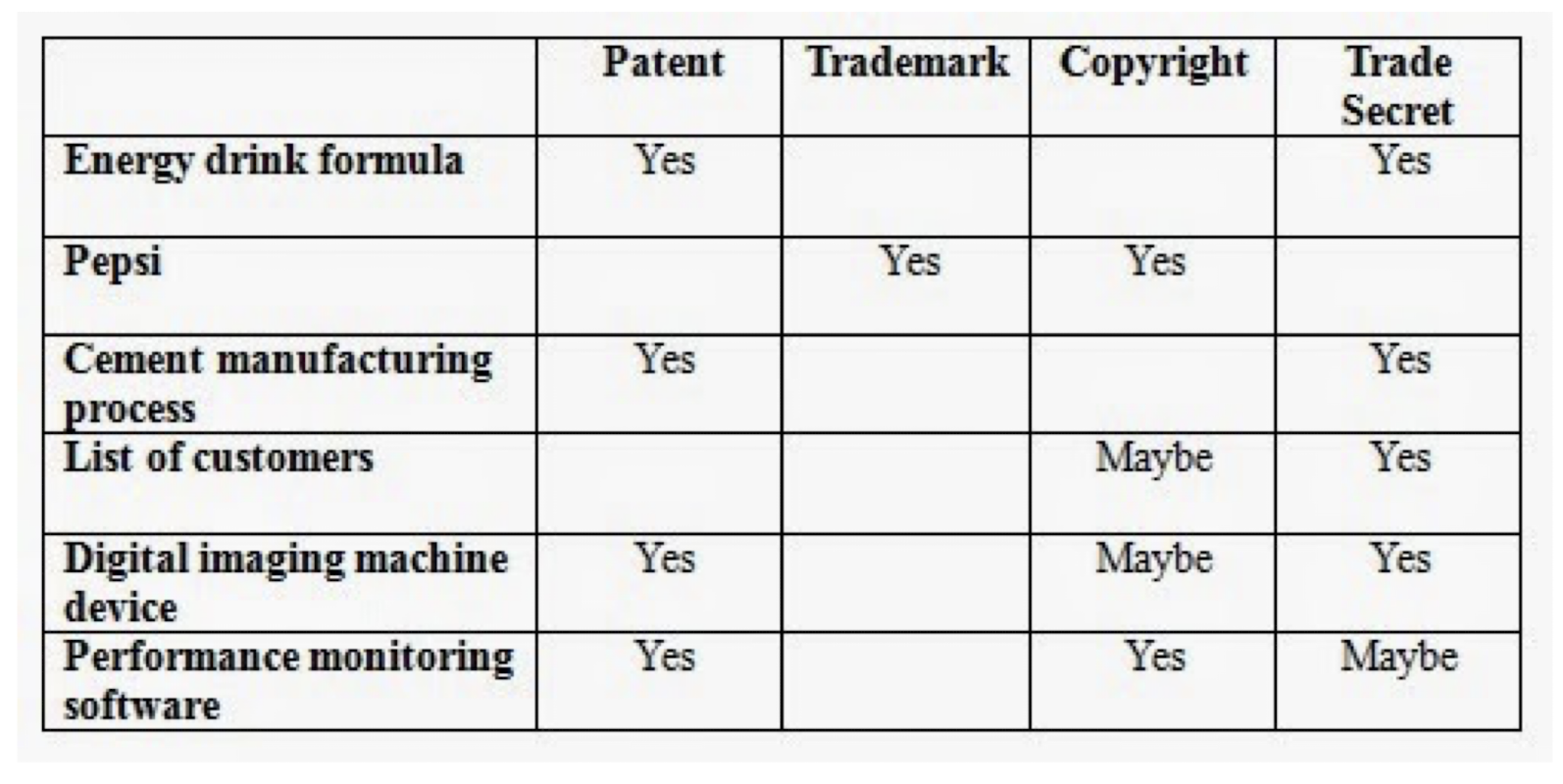
8.2 Overview Patents System in Hong Kong
8.2.1 Prior to 1 July 1997
Before 1997, a person who had obtained a patent in the UK or European patent designating the UK could have his patent registered in Hong Kong within five years of its grant.
The patent would be effective in Hong Kong for so long as the corresponding UK or European patent remained in force.
8.2.2 Since 1 July 1997
The enactment of a new Patents Ordinance (Cap. 514) in June 1997.
Under the Ordinance, there are two types of patents in Hong Kong i) Standard Patent ii) Short-term Patent
The max. term of protection of these two types of patents is 20 years and 8 years respectively.
“Re-registration” System is employed. Patent granted by one of three “designated patent offices” – SIPO, UKPO & EPO.
State Intellectual Property Office (SIPO) ( 國家知識產權局 )
UK Patent Office (UKPO) ( 英國專利局 )
European Patent Office (EPO) ( 歐洲專利局 )
8.2.3 New Patent System in Hong Kong to Launch on 19 December 2019
On 19 December 2019, a new patent system entered into force in Hong Kong. The new system introduces a so-called original grant patent (OGP) system for standard patents, allowing standard patent applications to be filed directly in Hong Kong without having to file a patent application outside Hong Kong.
原授標準專利申請
Standard patent (O) application
can be filed directly in Hong
Kong.
轉錄標準專利申請
Standard patent (R) is to file an
earlier corresponding patent
application with one of the 3
designated patent offices.
8.2.4 The Patent Laws of Hong Kong
- Principal legislation
- Patents Ordinance(Cap. 514)
- Subsidiary legislation
- Patents (Designation of Patent Offices) Notices (Cap. 514A)
- Patents (Transitional Arrangements) Rules (Cap. 514B)
- Patents (General) Rules (Cap. 514C)
8.2.5 Current Patent System in Hong Kong
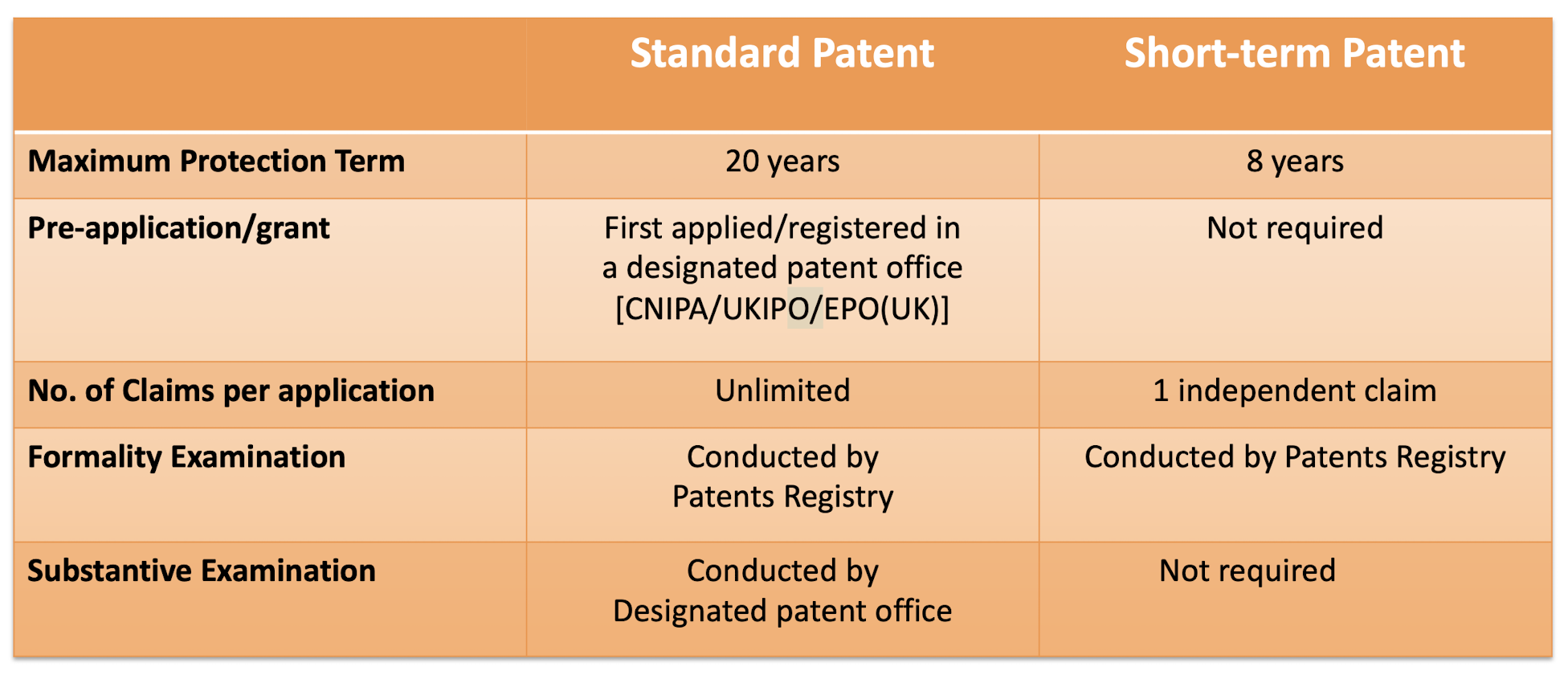
8.2.6 Current Patent System – Standard Patent
- Standard Patent Application (Re-registration)
- 1st Stage: file a request to record in HK within 6 months after publication of the designated patent application in the designated patent office
- 2nd Stage: file a request for registration and grant in HK within 6 months after -
- publication of the request to record in HK; or
- the grant of the designated patent by the designated patent office, whichever is later
8.2.7 Current Patent System – Short-Term Patent
- Short-Term Patent Application
- Limited to one independent claim
- Search report in relation to the invention
- Proprietor to establish the validity of the patent in enforcement proceedings before the court
8.2.8 Summary of New Patent System
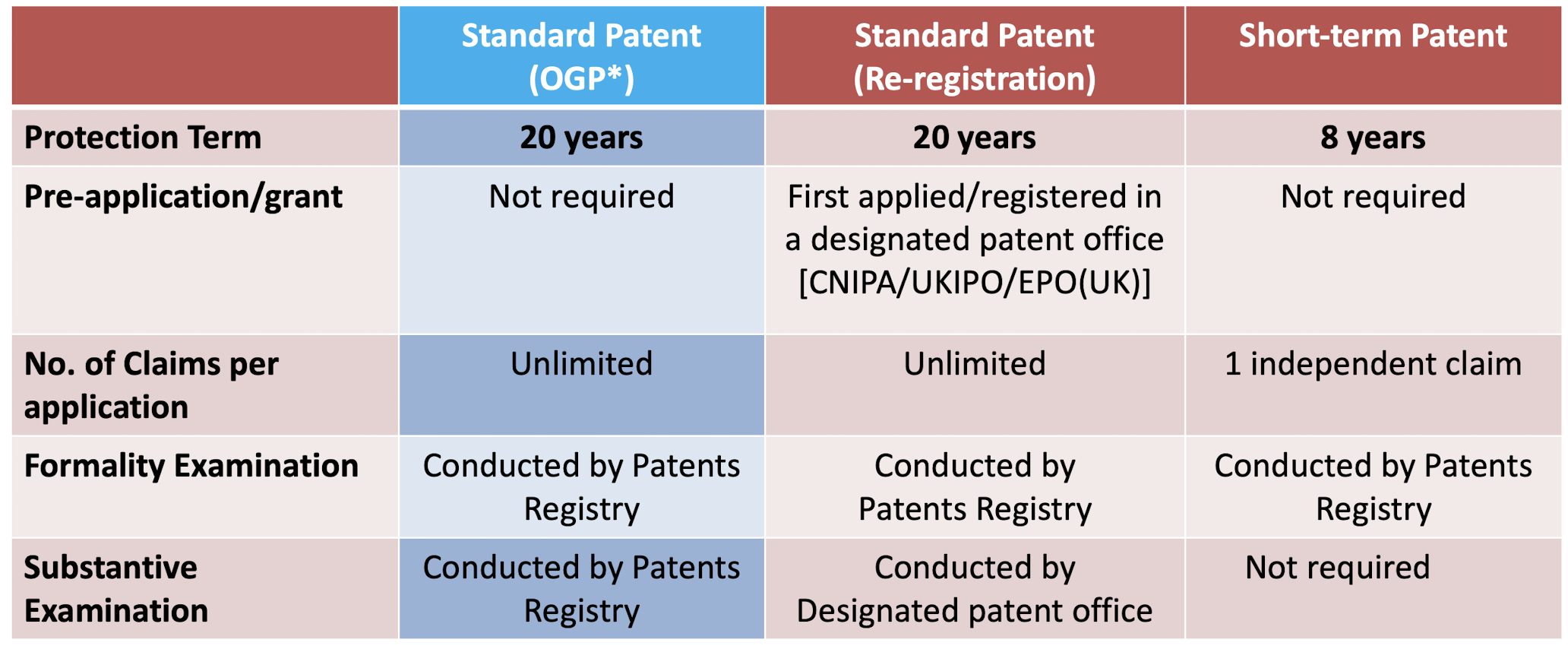
8.2.9 Preparation for New Patent System
- To finalize the examination guidelines
- To train the patent examiners for conducting substantive examination
- To set up a new IT system for filing and processing patent cases
- To publicize and promote the new patent system
- To establish a full-fledged regulatory regime for local patent practitioners with transitional measures in the medium and long terms
8.2.10 HK Patent Statistics
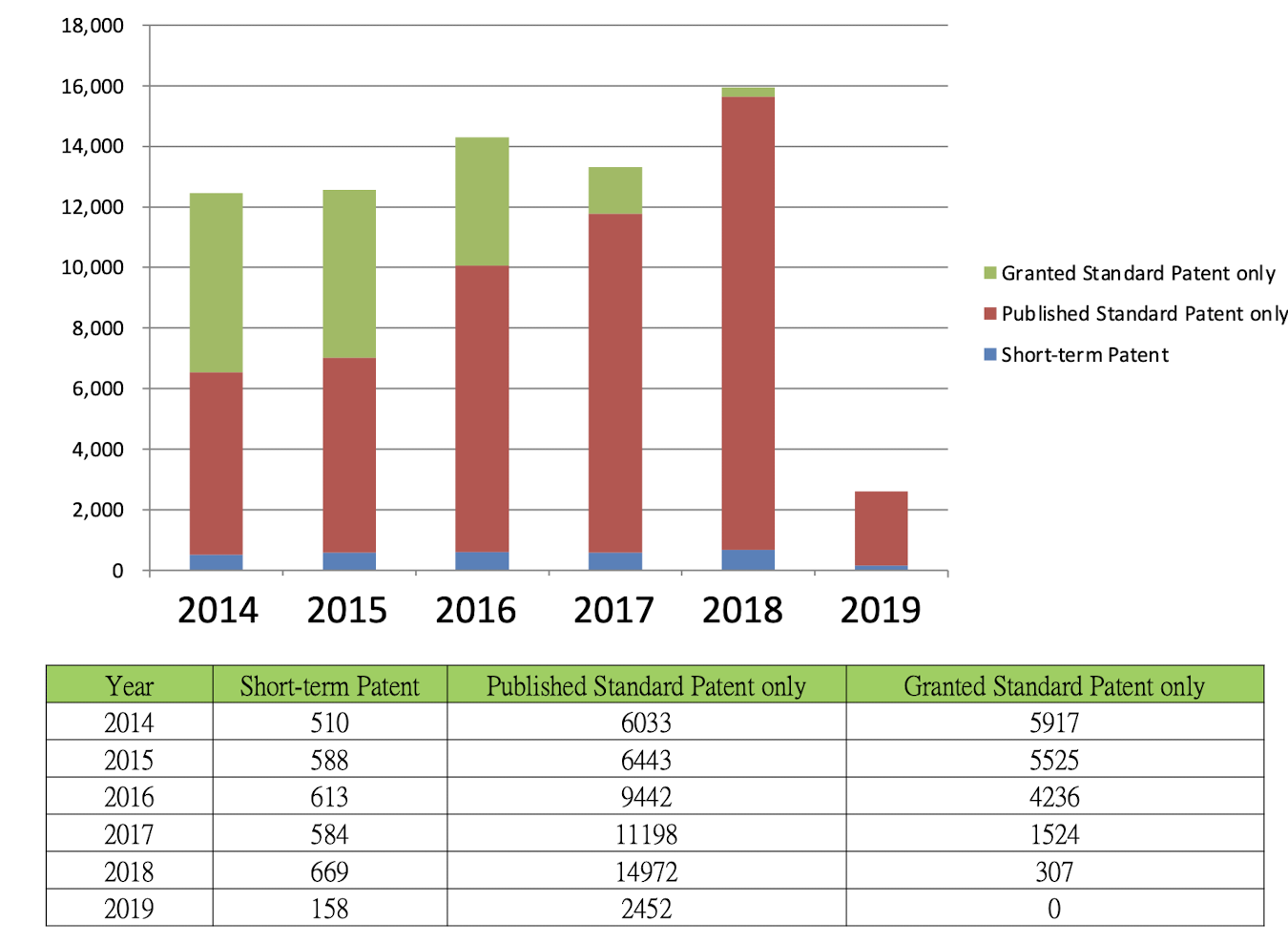
1) If your write the IP yourself, it may be many weakness point
2) If write by lawyer and cleverly, strong claim protection happen
3) Usually, we write both on product and IP system, it is more safe. (Two claim stronger than one claim)
8.2.11 IP Strategy – Use Patent Databases
- Google Patents
- Espacenet of European Patent Office (EPO)
- Patent Inspiration
8.3 An Overview of Chinese Patent System
8.3.1 Types of Patent in China
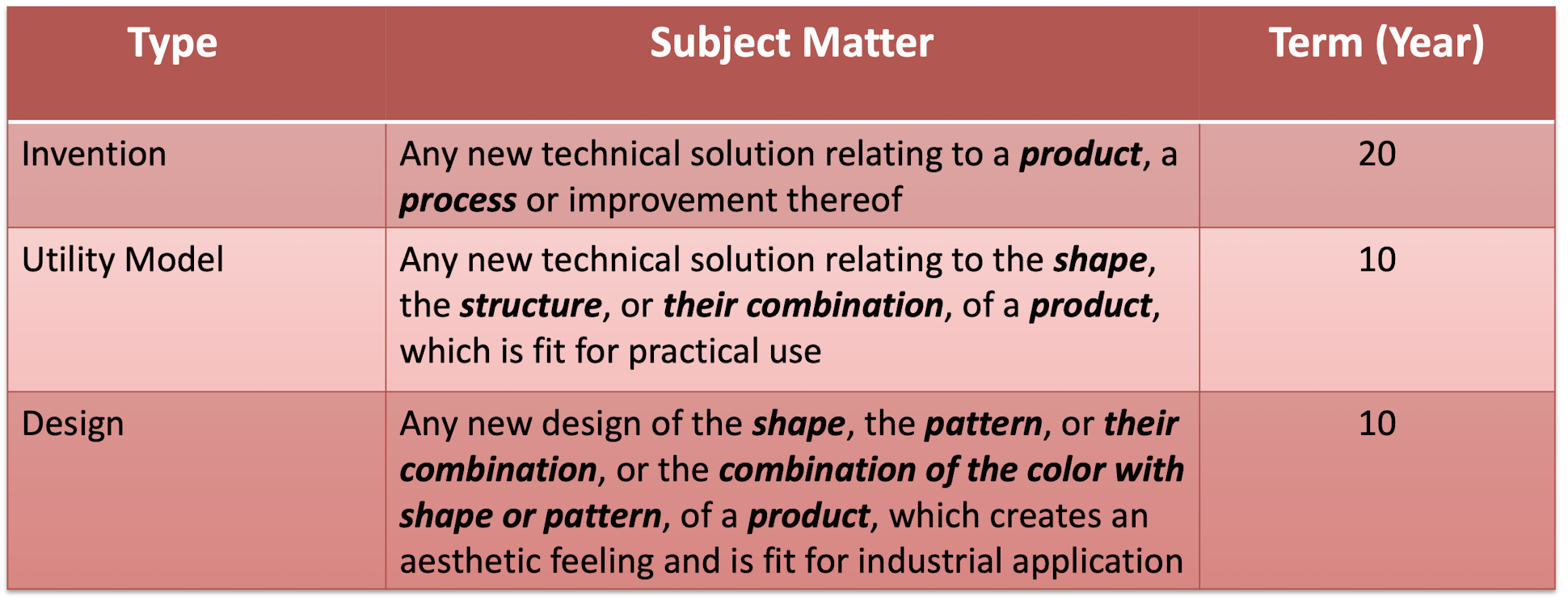
8.3.2 Comparison on Types of Patent (China vs USA)
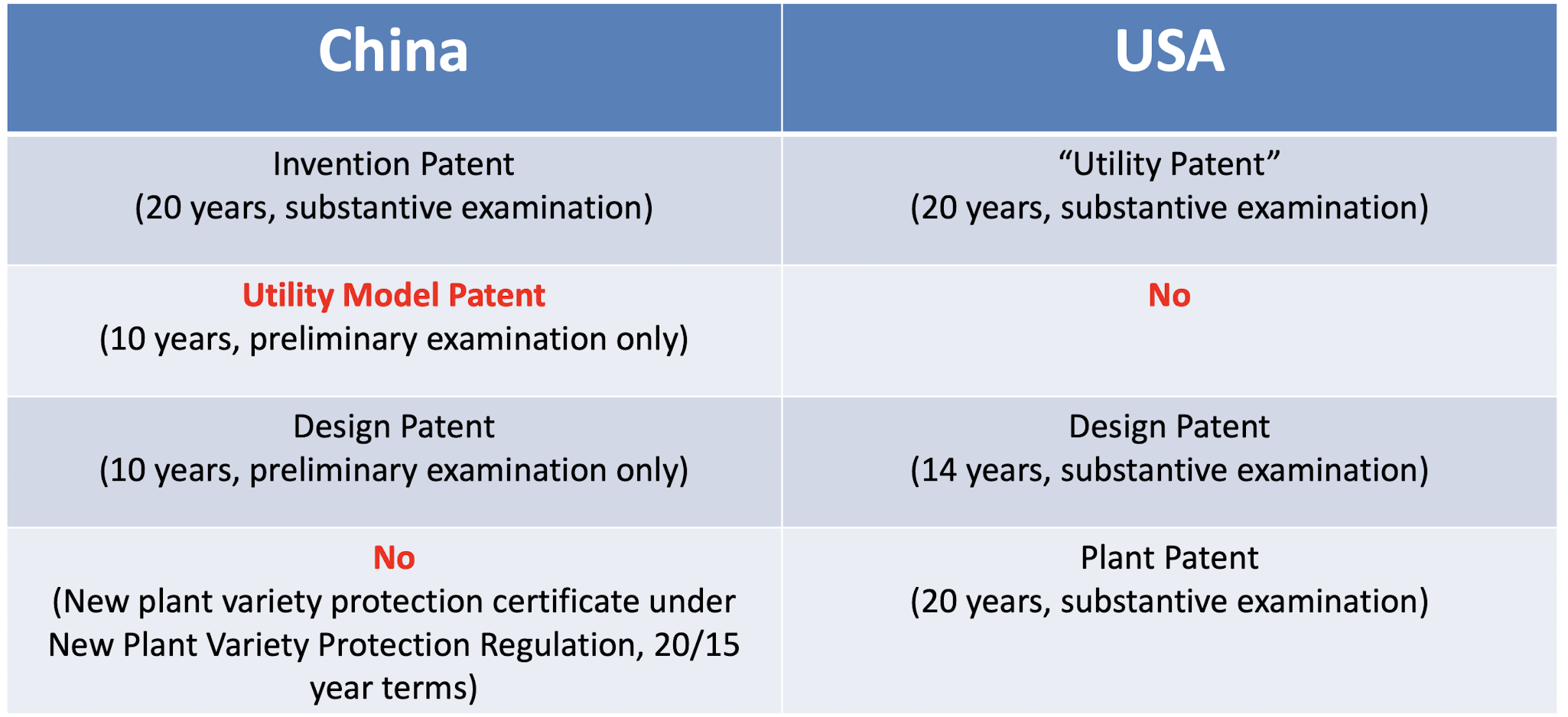
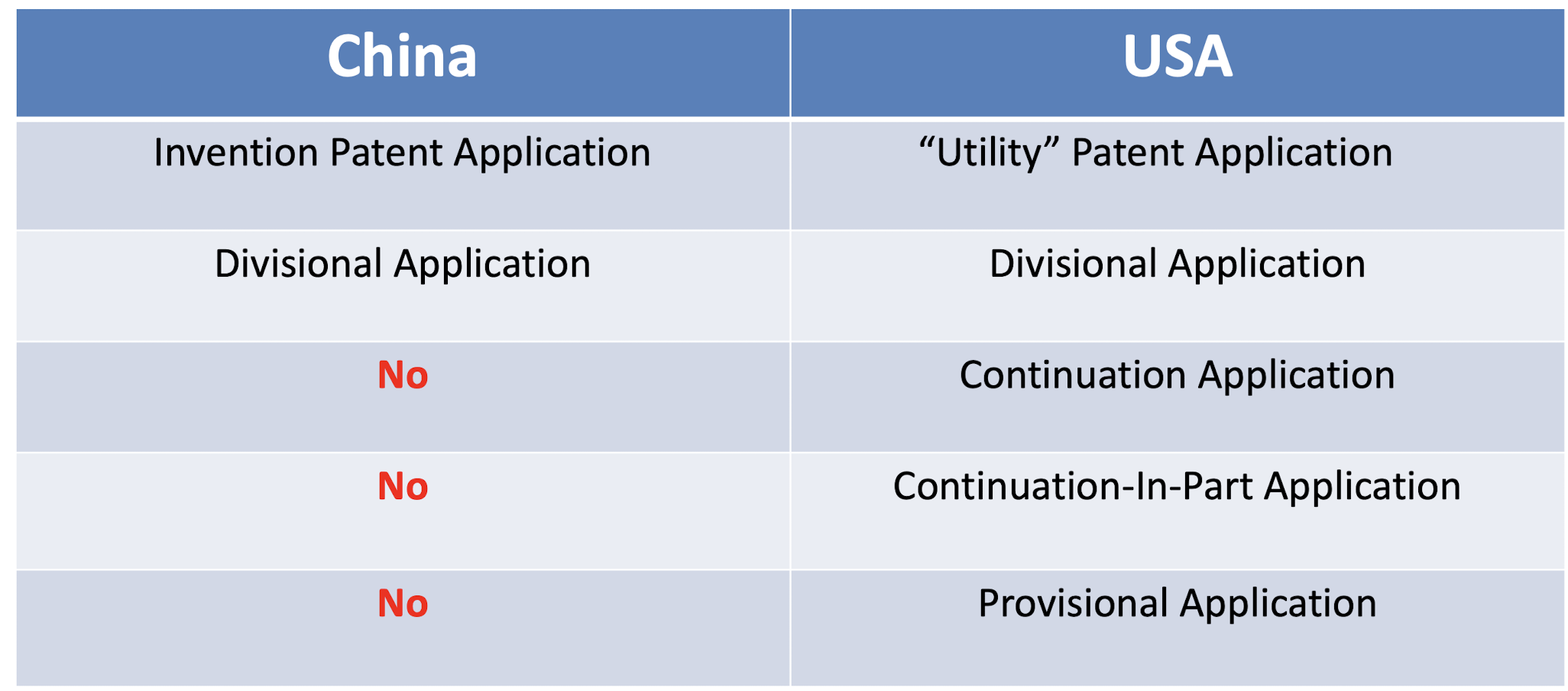
8.3.3 Utility Model Patent
- Subject Matter: Products Only
- Having definite shape and structure
- Certain structures: Coating(s) on a substrate
- Preliminary Examination
- Formality requirements: claims + description + drawings
- Obvious substantive defects: novelty
- Protection term
- 10 years
- Less pendency: generally, issued within 6 months from filing
8.3.4 Utility Model Filing Strategy
Defensive
- Immediate need in the market; same protection strength as invention patent
Aggressive
- Very important inventions
- Dual filing of both an invention application and a utility model application
Give up utility model patent when invention granted to avoid double patenting
Dual Filing Strategy
- Paris Route
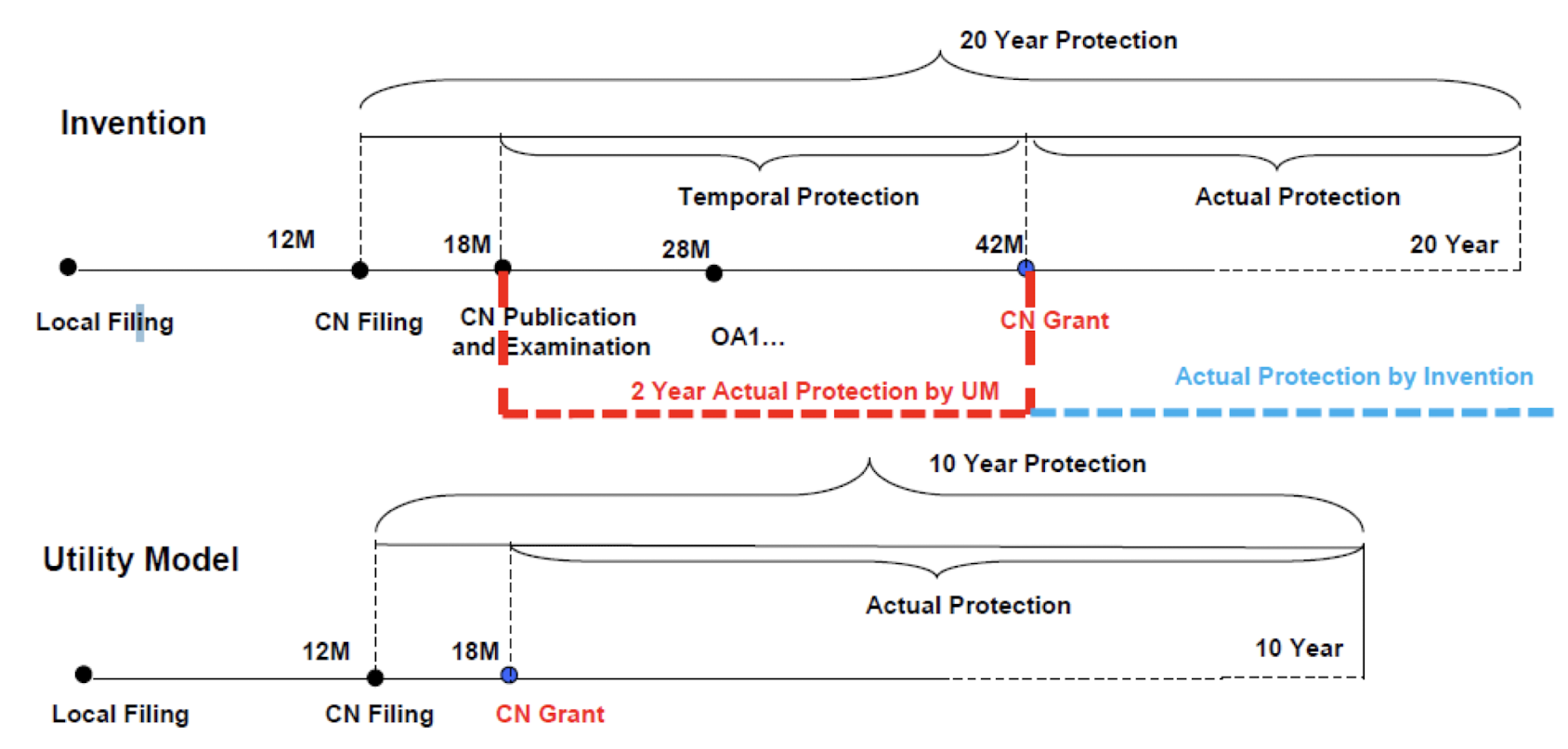
8.4 IP Strategy
8.4.1 IP Globalization in Singapore
8.4.2 Singapore IP Hub Masterplan (2014- 2024 - 2030)
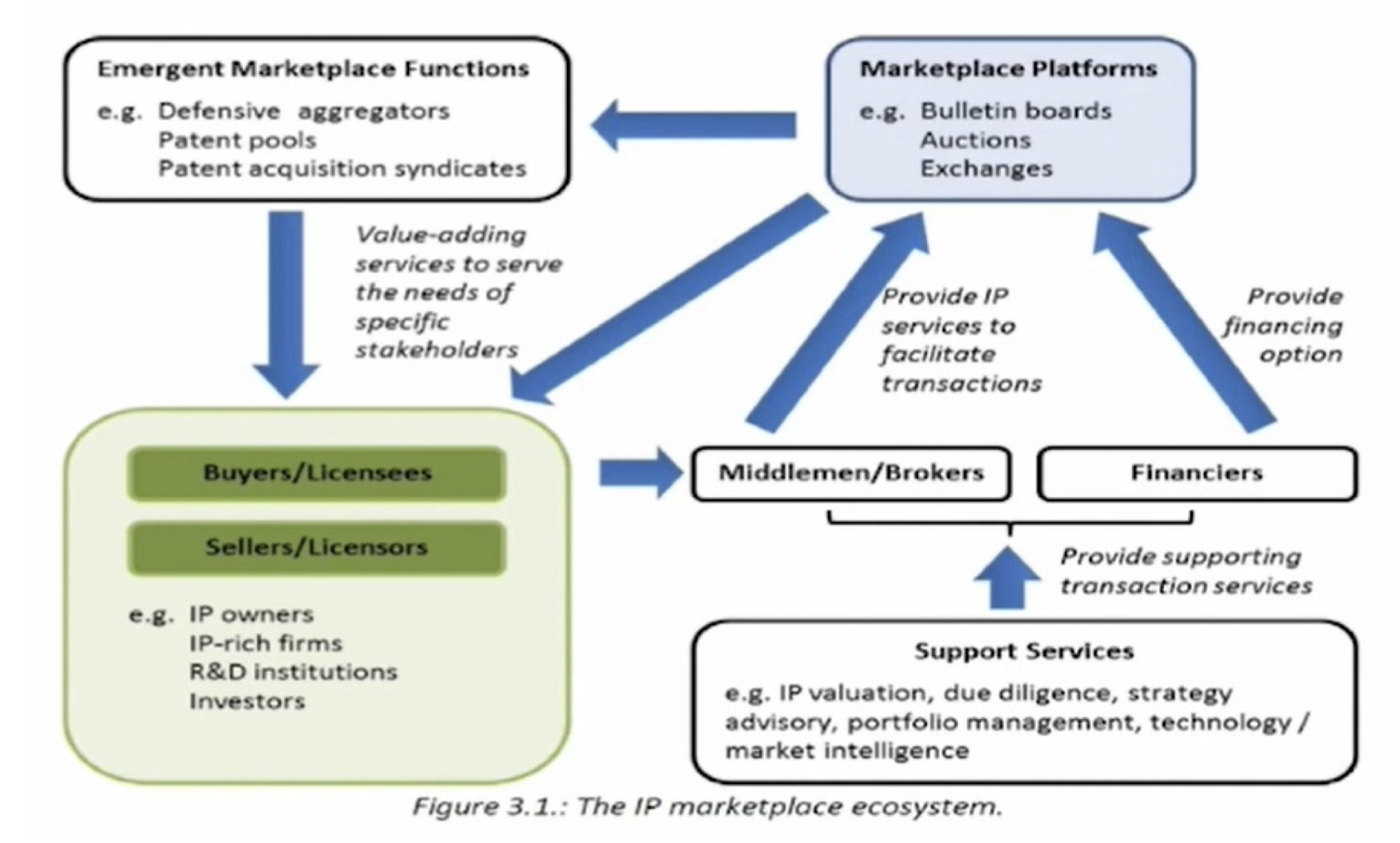
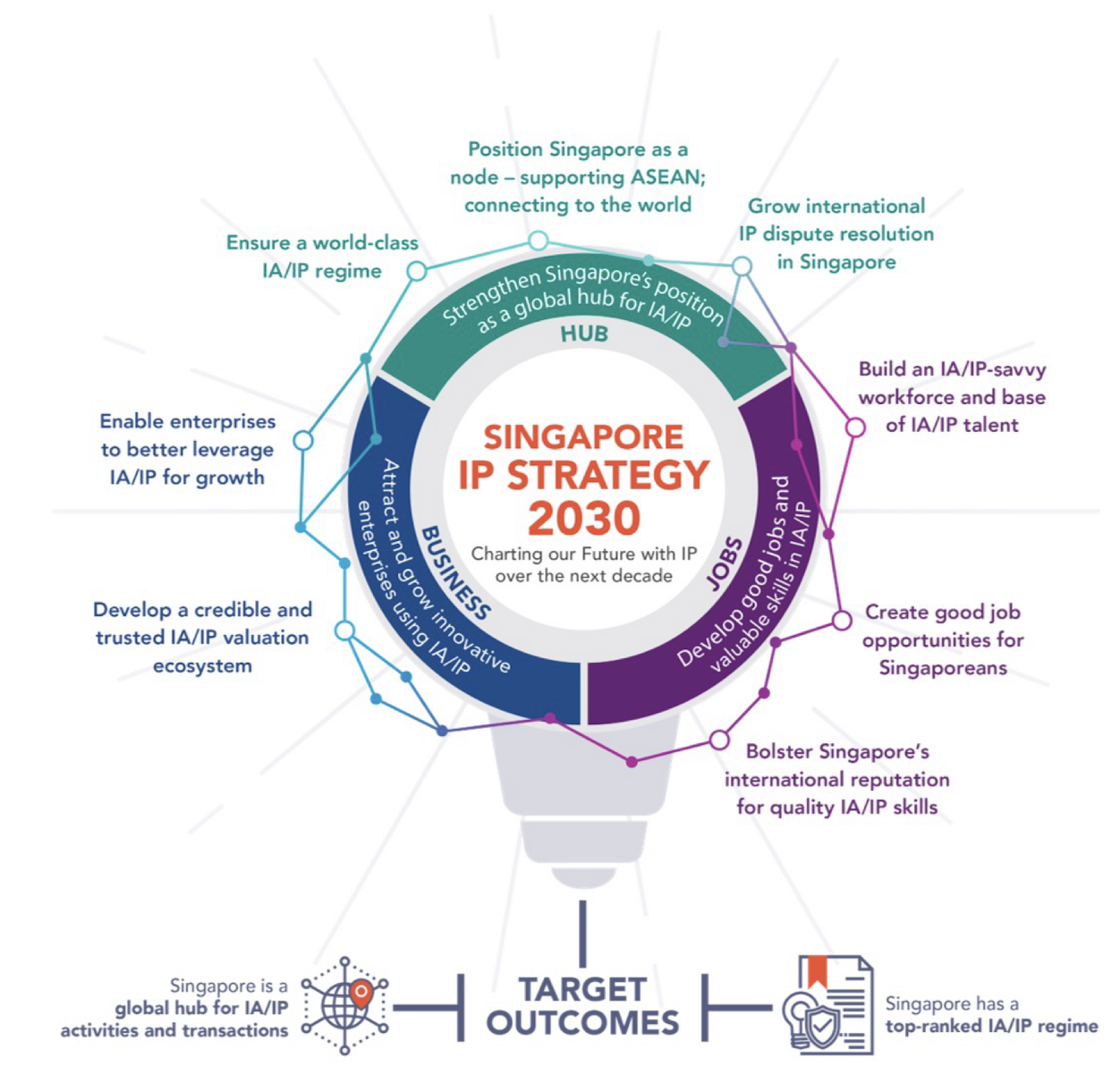
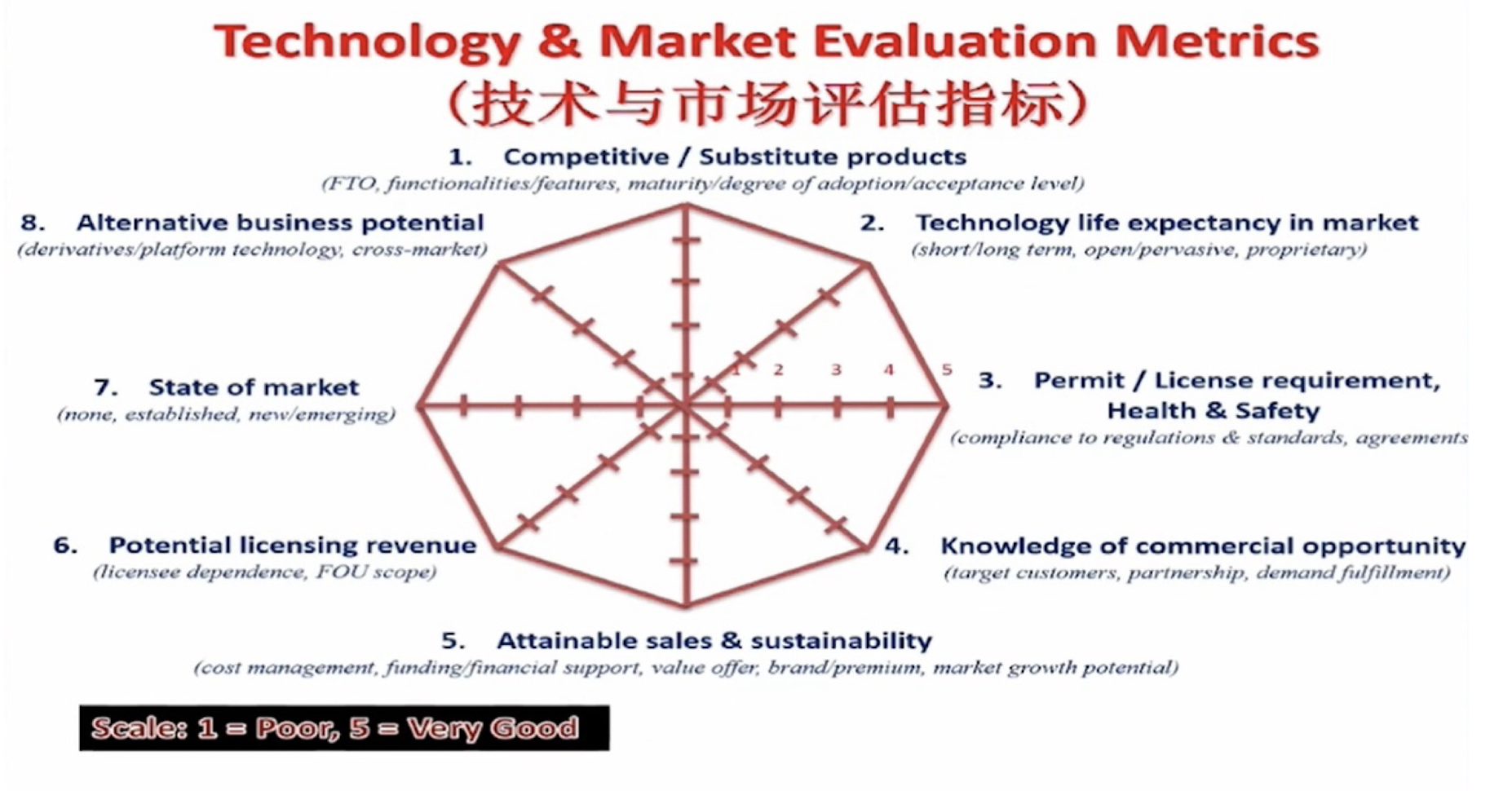
8.4.3 IP Monetization & Liability
- A company has a steady revenue stream from an IP asset.
- The right to the revenue stream is transferred to a new entity called a “special purpose vehicle (SPV) “ which holds a pool of such assets.
- The asset holder receives a lump sum representing the present value of the future cash flow of that asset.
- The pool of assets is then converted into bonds which investors buy.
- The cash flowing from the asset now flows into the SPV and is managed by the SPV for the benefit of the investors.
- The asset by being transferred is isolated from the parent company and shielded in case of bankruptcy.
8.4.4 Basic Valuation Approaches
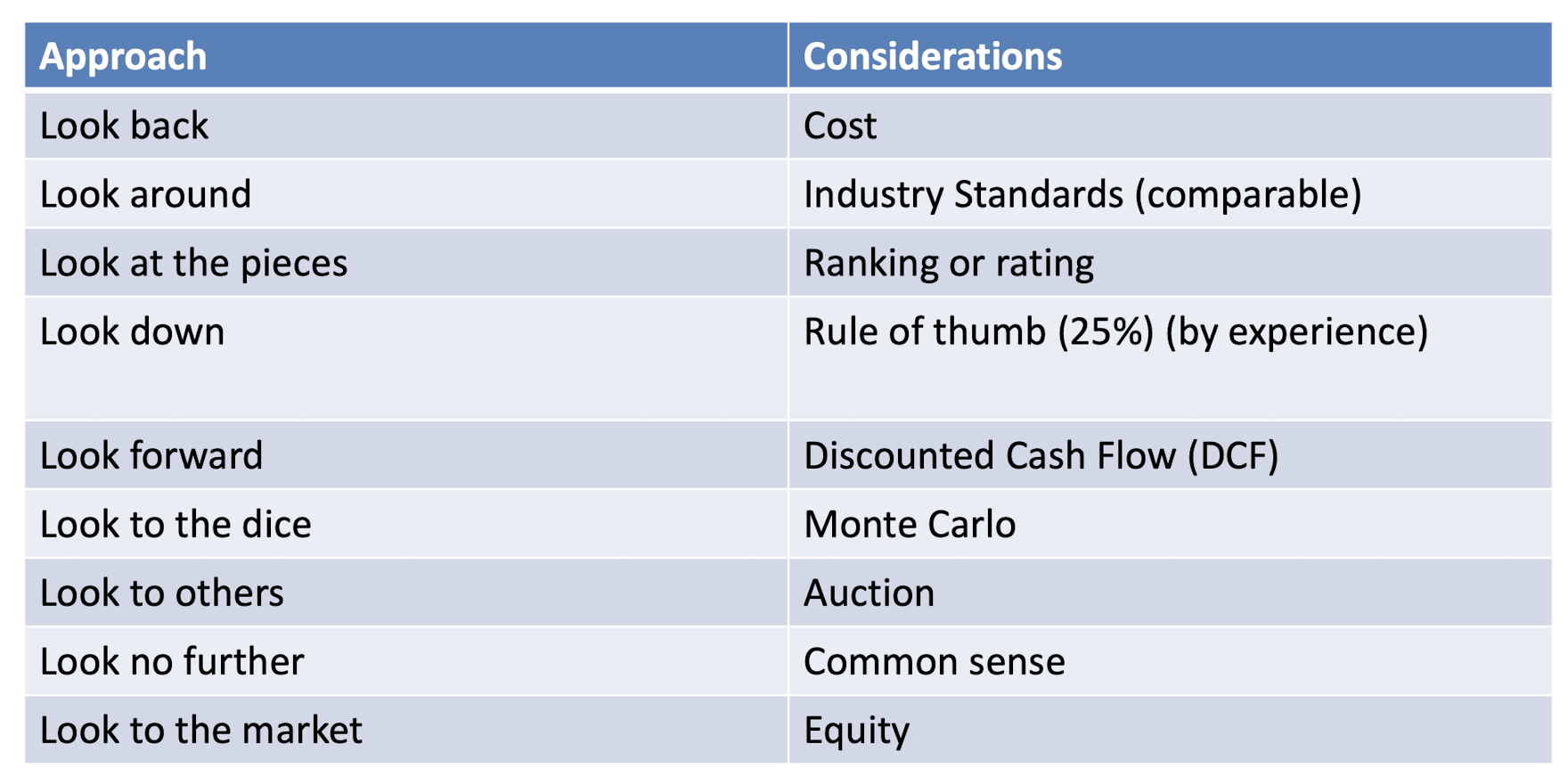
8.4.5 IP as a Strategic Tool
- In most technology related business
- IP is a significant asset
- Market has witness IP creation and exploitation over the last 30 years
- Valuation forms part of the IP value chain to ascertain IP values for greater business opportunity
8.4.6 Goals / Purpose of IP Strategy
- Integrate IP management with business & innovation strategies
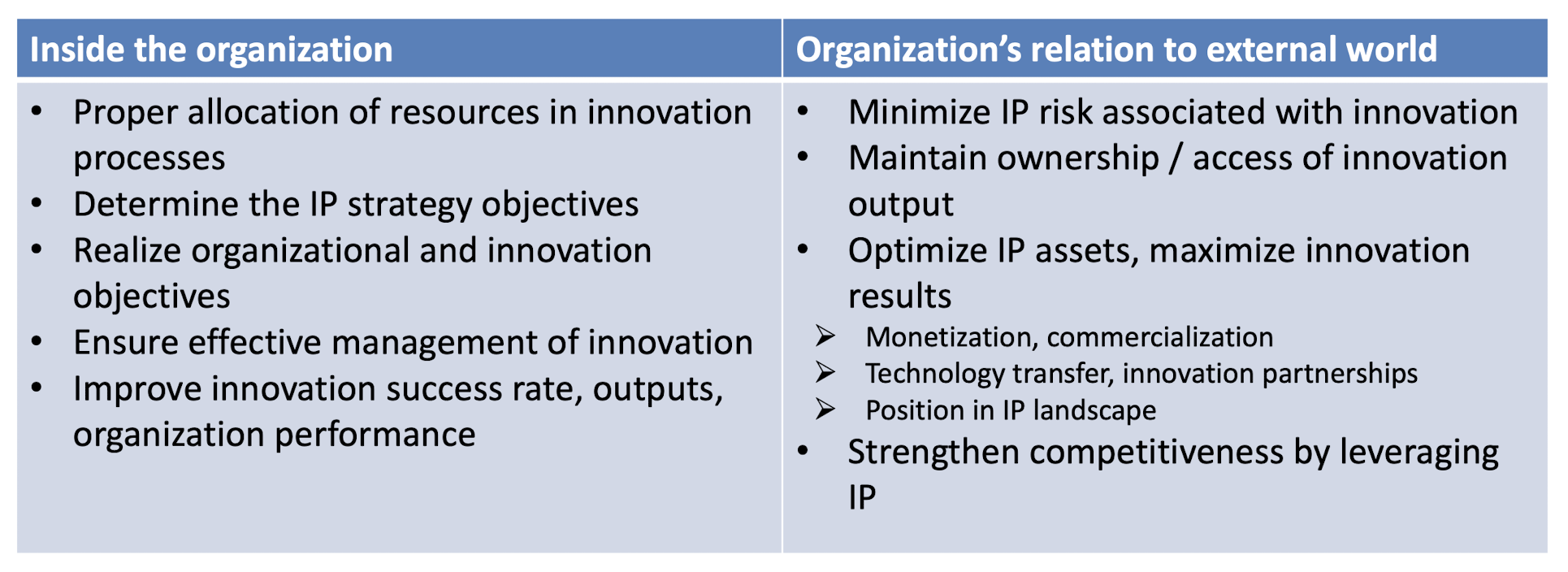
8.5 ISO 56005 – Developing IP Strategy
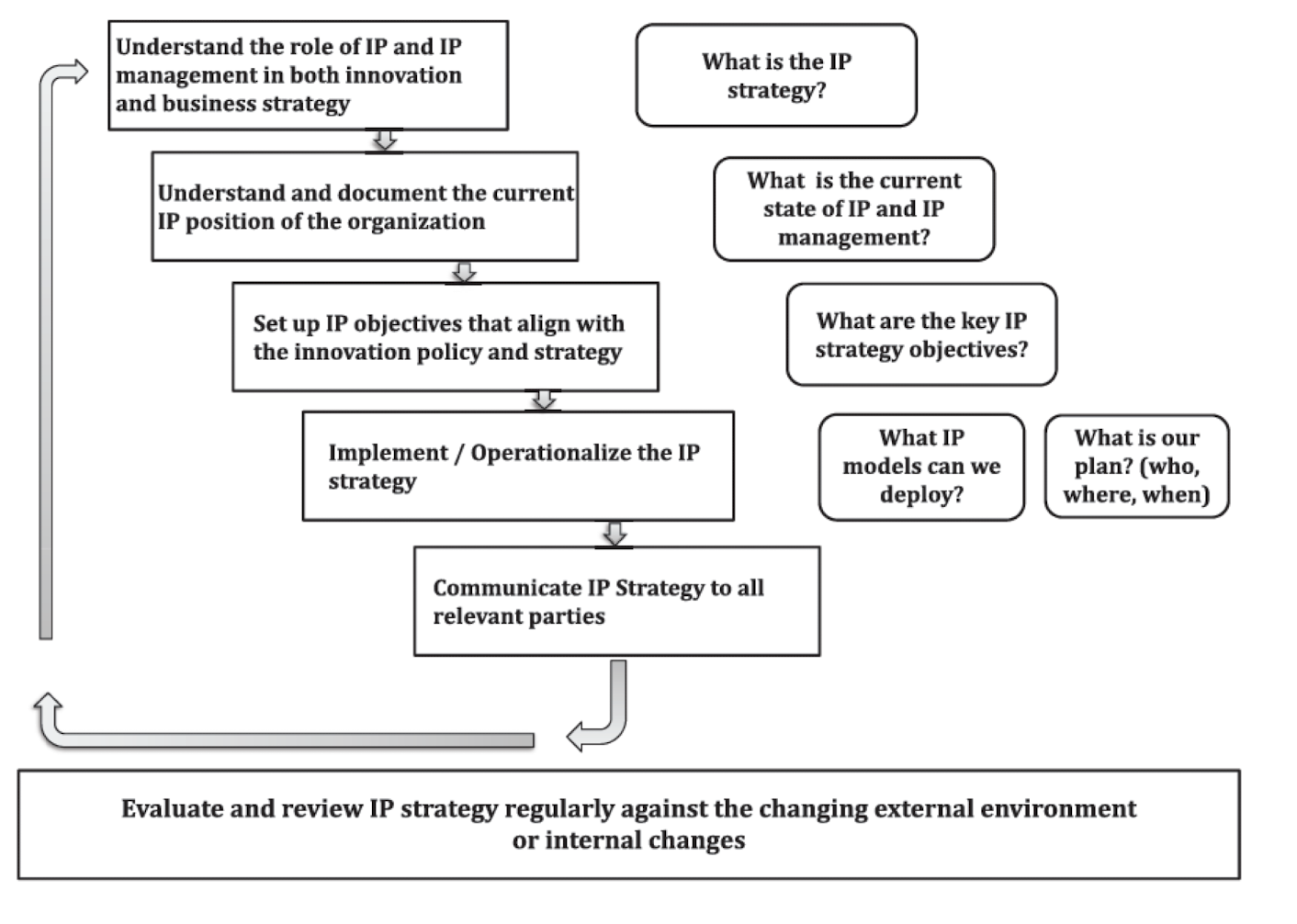
8.5.1 Relation to External World
- Use IP search and analysis for:
- Finding out where your market is
- Finding out who are your competitors
- Comparing your IP portfolio with IP portfolios of others
8.5.2 1. Where is my market?
- Do a search (in a patent database) for products like yours
- Check titles & content of results for relevance
- Look at countries / regions
- Look at classifications & keywords
- Look up text of the classification symbols
- You may discover:
- That your current market is a subset of a bigger one
- New technical areas and regions
- Increasing or decreasing activity
- … and more
- You may discover:
8.5.3 Input for IP Strategy from 1.
- Should I protect more aspects of my innovations?
- Should I innovate also in neighboring technical fields?
- Should I protect in other countries / regions?
- Is the activity in my field increasing or declining?
8.5.4 2. Who are my competitor?
- Do a search for products like yours
- Check titles & content of results for relevance
- Who applies for most of these patents?
- Who owns the most similar patents?
- Are these big or small companies?
- Where are they based?
- Are their products very similar to yours – Infringement risk?
8.5.5 Input for IP Strategy from 2.
- Are there very strong (=dangerous?) players in my area
- Should I monitor competitors’ activity?
- If a competitor dominates part of the market, can I focus on other parts?
- Are there candidates for cooperation?
8.5.6 3. Comparing my IP portfolio with others
- Use the companies / IP owners identified in the previous step
- Search for all IP they own, one by one
- Identify relevant factors:
- Which other technology do they protect?
- In which countries / regions do they protect their IP?
- Does their activity increase or decrease?
- How long do they keep their IP alive (= pay the renewal fees)?
8.5.7 Input for IP Strategy from 3.
- Should I extend my activity to other technical fields?
- Should I protect in other countries / regions?
- Should I avoid some countries / regions?
- Should I extend or shorten the lifetime of my IP?
- Should I behave like my competitor or maybe differently?
8.5.8 IP Search and Analysis for IP Strategy
- Know where your stand with your IP
- Identify risks (e.g. strong competitors)
- Find opportunities for new products
- Find potential cooperation partners
- Expand your business to other countries / regions
8.5.9 Conclusion
- Developing and maintaining an IP Strategy
8.5.10 IP Management Standard
8.5.10.1 ISO 56005 Scope
- Efficient management of IP is key to support the process of innovation, is essential for organizations’ growth and protection, and is their engine for competitiveness.
- This document proposes guidelines for supporting the role of IP within innovation management. It aims
- to address the following issues concerning IP management at strategic and operational levels:
- Creating an IP strategy to support innovation in an organization;
- Establishing systematic IP management within the innovation processes ;
- Applying consistent IP tools and methods in support of efficient IP management.
- This document can be used for any type of innovation activities and initiatives.
8.5.10.2 IP management activities contribute to innovation management
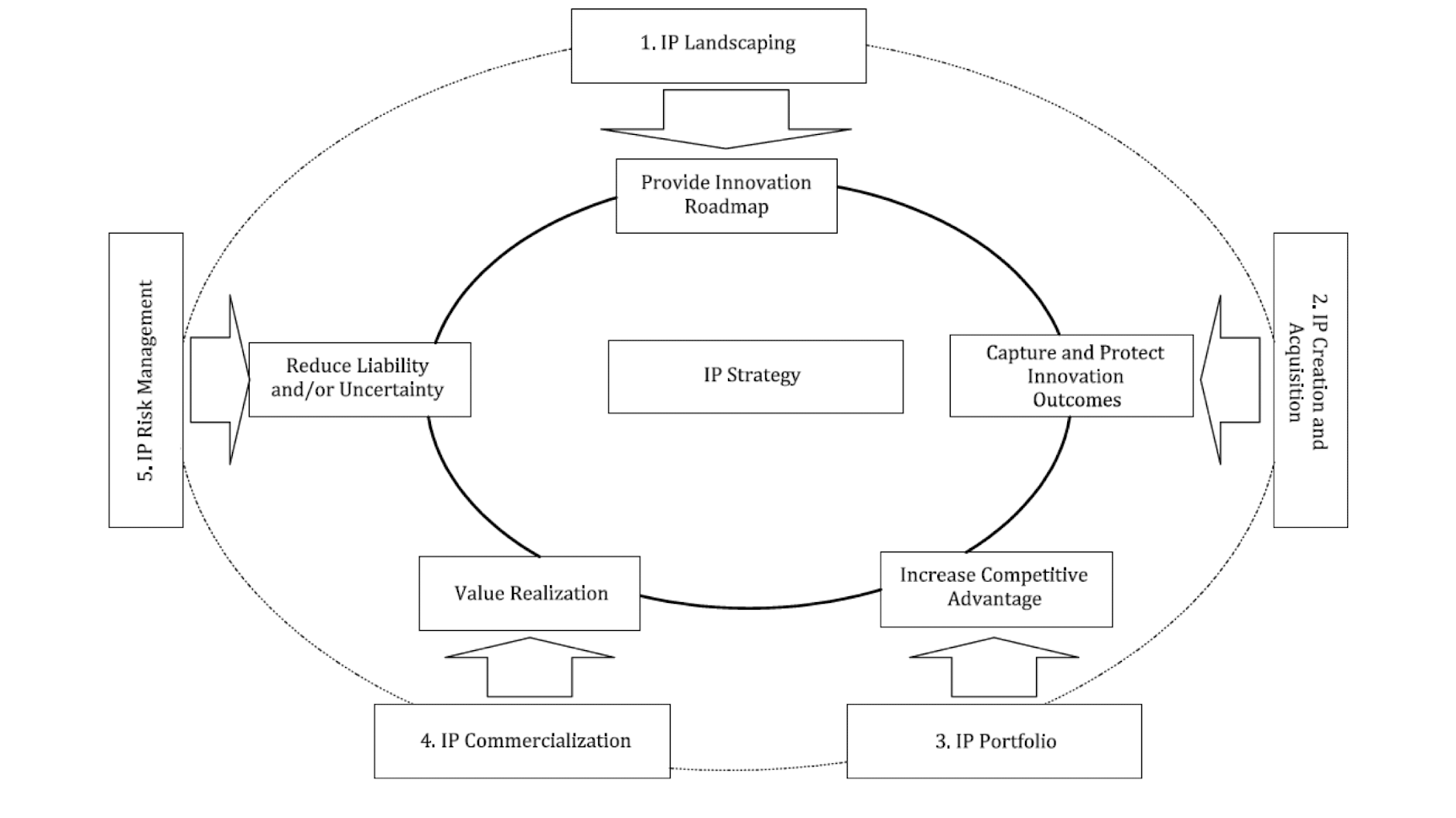
8.5.10.3 Structure of IP management in ISO 56005
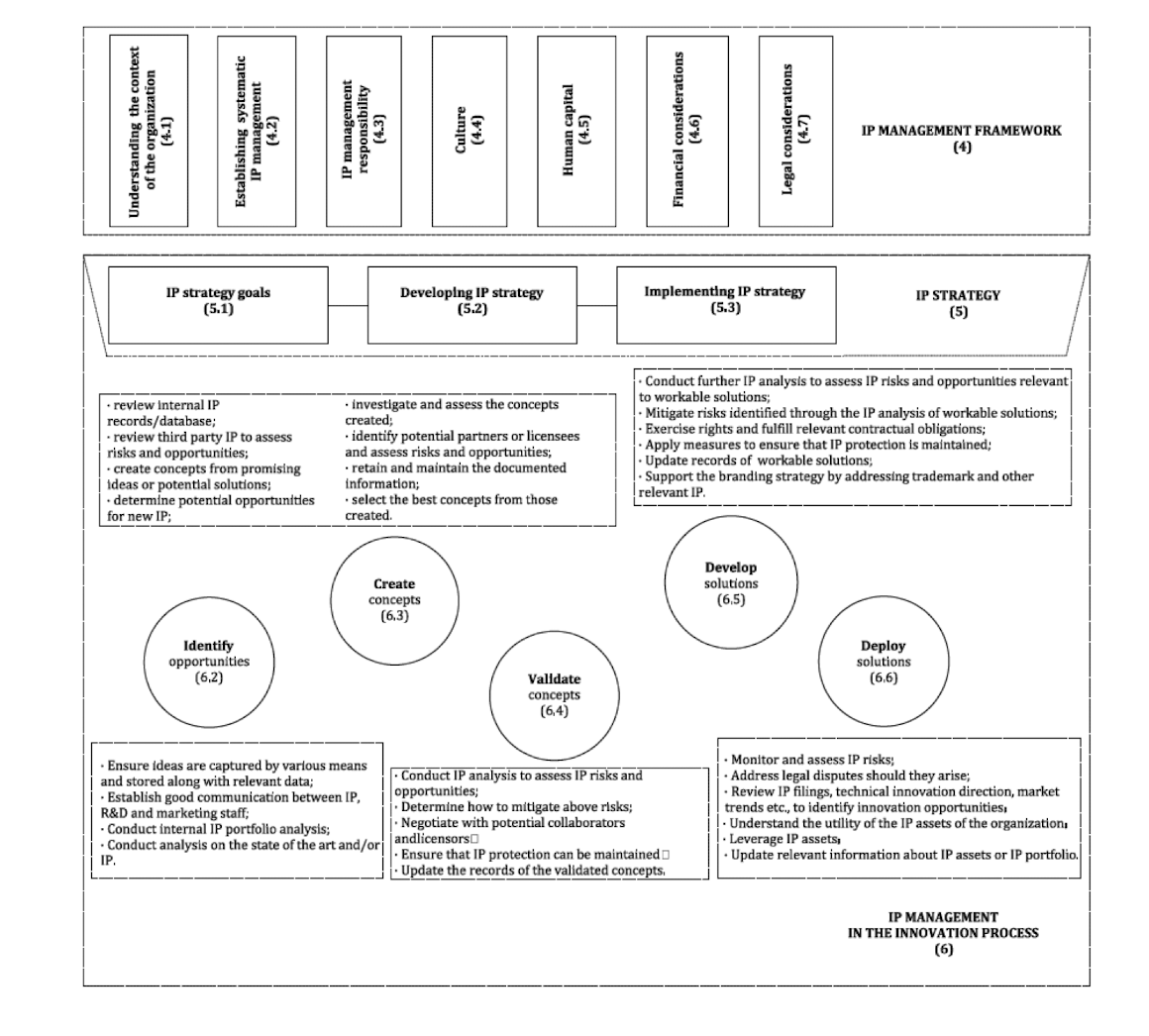
8.5.10.4 Structure of the Document
8.5.10.5 Core: Realization of Value
- The management of IP should create value for all relevant stakeholders.
- This includes
- long-term and short-term values;
- Explicit and implicit value;
- Financial and non-financial value.
8.5.10.5 IP Management Framework
- The organization should determine external and internal issues and considerations that are relevant to its organizational objectives and that affect its ability to achieve its intended IP strategic objectives.
- IP management Responsibility (4.3)
- Top management should ensure that the responsibilities and authority for relevant roles are assigned and communicated within the organization
- Culture (4.4)
- The organization should promote an organizational culture that supports the effective management of IP.
- Human Capital (4.5)
- The organization should ensure the availability of competent people to support the effective management of IP.
- Financial Considerations (4.6)
- For the effective management of IP, it is important to recognize that there are a variety of costs associated with developing and maintaining an IP portfolio.
- Legal Considerations (4.7)
- The organization should have a general understanding of legal considerations related to IP management.
8.5.10.6 IP Strategy
- The organization should have an IP strategy which should be integrated as a key element of its innovation strategy. Furthermore, the organization’s IP strategy should align with and support its business strategy.
- The relationship between an organization’s business strategy, its innovation strategy and the IP strategy shows in the fDigure.
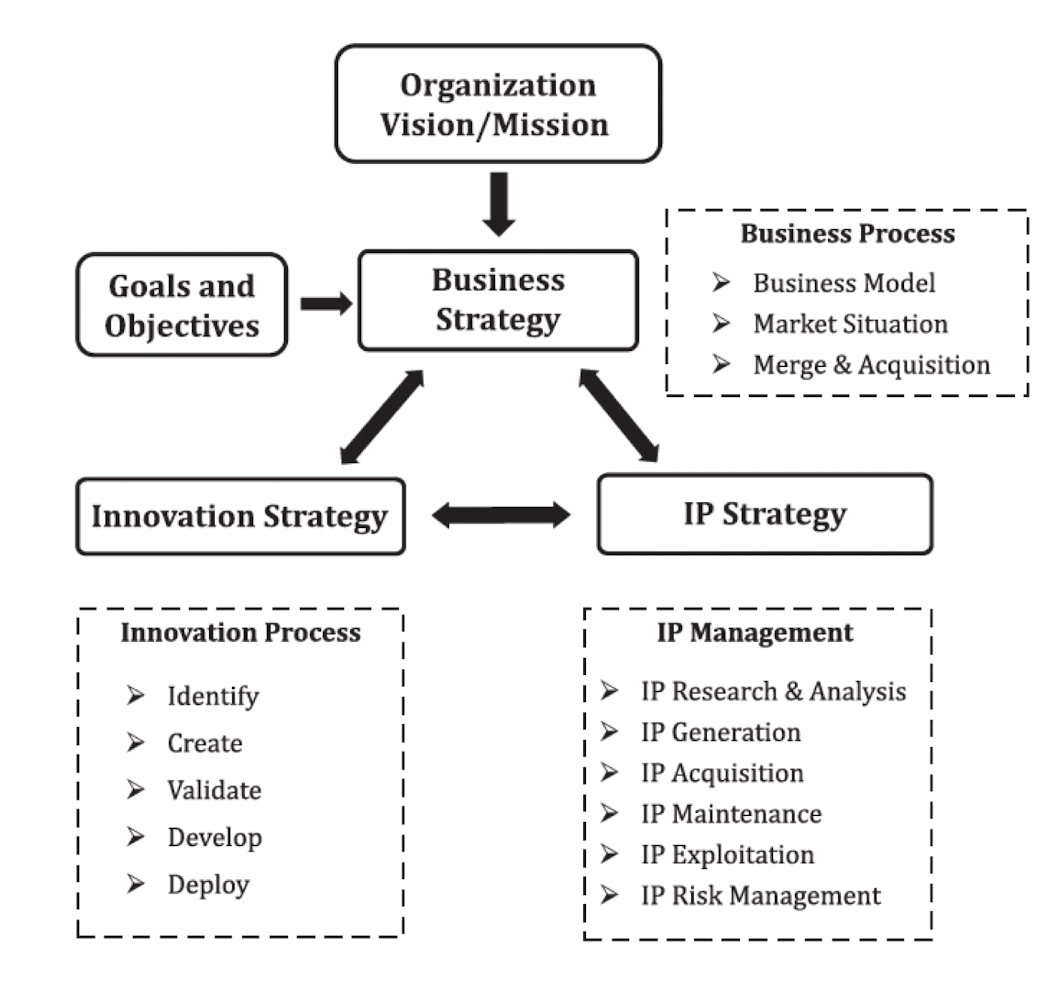
8.5.10.7 IP Management in the Innovation Process
- Innovation is non-linear and iterative, and comprises five interacting innovation processes (ISO 56002:2019)
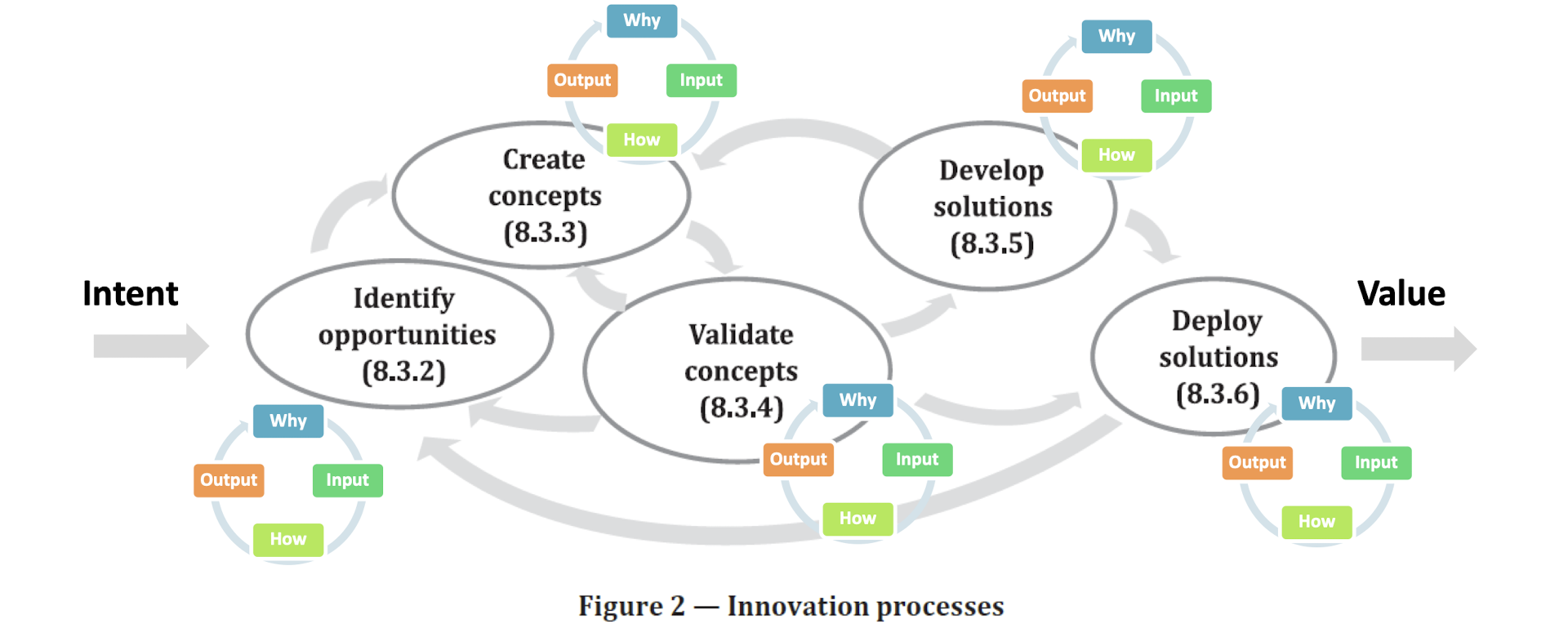
8.5.10.8 The Expected Most Popular Standard
9. Entrepreneurship - Sustainability Development
9.1 Sustainability Development
9.1.1 Professional in Sustainability - Six Principles

9.1.2 THE UN 2030 AGENDA

9.1.3 UN development agenda
- At the beginning of the 2000, world leaders gathered at the UN to shape a broad vision to fight poverty in its many dimensions
- That vision was translated into 8 Millennium Development Goals (MDGs)
- The MDG framework has guided development work across the world for the past 15 years
- Significant achievements had been made but many people are being left behind.

9.1.4 The origins of the UN 2030 Agenda
- 2012 UN Conference on Sustainable Development in Rio de Janeiro (Rio+20)
- Appeal made to formulate common goals and include these in the post-2015 development agenda
- The MDGs did not consider environmental issues , e.g.
- Emissions of greenhouse gasses
- Access to clean drinking water
- Management of water resources
- New focus on the concept of ‘ sustainable development ’
- Need to consider the relationship between nature and society
- Social, environmental and economic dimensions
https://sustainabledevelopment.un.org/sdgs
International Proposal: ‘Transforming our world’
- 17 goals
- 169 targets
9.1.5 The main goals focus on the 5 Ps
- People : the wellbeing of all people
- Planet: protection of the earth’s ecosystems
- Prosperity: continued economic, social & technological growth
- Peace: securing peace
- Partnership: improving international cooperation
- They are interdependent.
- SDGs need integrated thinking and approaches to achieve it.
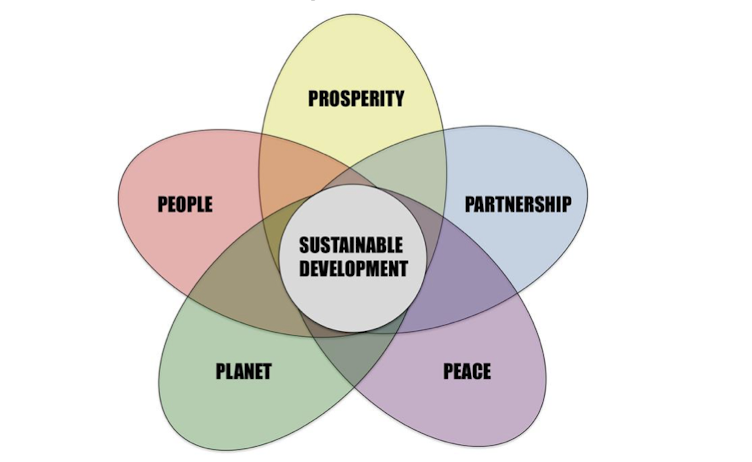
9.1.5.1 Goal 1. No Poverty
- End poverty in all its forms everywhere
- Poverty = Income less than 1.25USD per day
- Aims:
- Eliminate extreme poverty by 2030
- The poor have equal rights to economic resources
- The poor are not easily affected by climate change
Millennium Development Goals (MDGs)
Achieved in 2015 to reduce poverty to 18% and we excess it.
9.1.5.2 Goal 2. Zero Hunger
- End hunger, achieve food security and improved nutrition and promote sustainable agriculture
- By 2030, double the agricultural productivity and incomes of small-scale food producers
- Aims:
- End malnutrition
- Protect small farmers
- Protect genetic diversity of crops produced
- Invest in more research to make farming higher productivity

9.1.5.3 Goal 3. Good Health and Well-Being
- Ensure healthy lives and promote well-being for all at all age
- By 2030, reduce the global maternal mortality ratio to less than 70 per 100,000 live births
- Aims:
- Call for universal health coverage
- Increase healthcare workforce
- Reduce illness and death
- Tackle global challenges (e.g. AIDS, Covid-19, etc.)

9.1.5.4 Goal 4. Quality Education
- Ensure inclusive and equitable quality education and promote lifelong learning opportunities for all
- By 2030, ensure that all girls and boys complete free, equitable and quality primary and secondary education leading to relevant and effective learning outcomes
- Aims:
- Need for access to university level education
- Vocational training
- Entrepreneurial skills
- Help the children in your community for studying

9.1.5.5 Goal 5. Gender Equality
- Achieve gender equality and empower all women and girls
- A fundamental human right and a foundation for a peaceful, prosperous and sustainable world
- Aims:
- Freedom form discrimination and violence
- Ensure equal share of leadership opportunities and responsibilities for women

9.1.5.6 Goal 6. Clean Water and Sanitation
- Ensure availability and sustainable management of water and sanitation for all
- By 2030, achieve universal and equitable access to safe and affordable drinking water for all
- Water scarcity affects 40% of the world’s population
- Aims:
- Provide access to basic technologies
- Avoid water wastage
9.1.5.7 Goal 7. Affordable and Clean Energy
- Ensure access to affordable, reliable, sustainable and modern energy for all
- By 2030, ensure universal access to affordable, reliable and modern energy services
- About 1.3 billion of people globally do not have access to electricity
- Aims:
- Encourage renewable sources
- Use energy efficient light bulbs and appliances

9.1.5.8 Goal 8. Decent Work and Economic Growth
- Promote sustained, inclusive and sustainable economic growth, full and productive employment and decent work for all
- Sustain per capita growth (at least 7% GDP growth per annum in the least developed countries)
- About 75 million people between age 15 and 24 are unemployed and out of school globally
- Aims:
- Close the gap of unemployment
- Apply innovation to enhance economic growth

9.1.5.9 Goal 9. Industry, Innovation and Infrastructure
- Build resilient infrastructure, promote inclusive and sustainable industrialization and foster innovation
- Develop quality, reliable, sustainable and resilient infrastructure
- Promote inclusive and sustainable industrialization and increase the access of small-scale industrial and other enterprises
- By 2030, upgrade infrastructure and retrofit industries to make them sustainable Hong Kong–Zhuhai–Macau Bridge
- Aims:
- Fostera more innovative and environmentally sound approach to industrial development
- Brainstorm innovative ways to repurpose old materials

9.1.5.10 Goal 10. Reduced Inequalities
- Reduce inequality within and among countries
- By 2030, achieve and sustain income growth of the bottom 40% of the population
- Aims:
- Adopt policies to pay more attention to the needs of disadvantaged and marginalized populations
- Develop a safe and responsible environment
Equal Opportunities Commission, Hong Kong
The Equal Opportunities Commission (EOC) is a statutory body set up in 1996 to implement anti-discrimination legislation. Currently there are four ordinances dealing with anti-discrimination, namely the Sex Discrimination Ordinance (SDO), the Disability Discrimination Ordinance (DDO), the Family Status Discrimination Ordinance (FSDO) and the Race Discrimination Ordinance (RDO).
Our Vision
To create a pluralistic and inclusive society free of discrimination where there is no barrier to equal opportunities.
Mission
We seek to achieve our vision by establishing partnerships with all sectors in the community; promoting awareness, understanding and acceptance of diversity and equal opportunities and providing education to prevent discrimination; enforcing compliance with provisions in the anti-discrimination legislation; and providing access to redress for discrimination.
https://www.eoc.org.hk/

9.1.5.11 Goal 11. Sustainable Cities and Communities
- Make cities and human settlements inclusive, safe, resilient and sustainable
- By 2030, ensure access for all to adequate, safe & affordable housing, basic services and upgrade slums (貧民窟).
- Aims:
- Address issues, e.g. transportation, disaster preparedness, preservation of cultural and natural heritage
- Encourage use of public transportation and cycling to keep our cities air clean
Hong Kong Smart City Blueprint
https://www.smartcity.gov.hk/
Smart Mobility
Smart Living
Smart Environment
Smart People
Smart Government
Smart Economy

9.1.5.12 Goal 12. Responsible Consumption and Production
- Ensure sustainable consumption and production patterns
- By 2030, achieve the sustainable management and efficient use of natural resources
- Promote Public Sustainable Procurement
- Aims:
- Reduce food waste
- Exercise sustainability practice and educate people on the impact of their lifestyle choices
- Reduce waste generation through prevention and 3R (Recycle, Reuse and Reduce)
Responsible Consumption and Production Approach & Policies
9.1.5.13 Goal 13. Climate Action
- Take urgent action to combat climate change and its impacts
- Integrate climate change measures into national policies, strategies and planning
- Paris Agreement guides nations to commit to limit global warming
- Aims:
- Educate young people on climate change
- Work together with different stakeholders in achieving the goal of the Paris Agreement

9.1.5.14 Goal 14. Life Below Water
- The world’s oceans are over-fished, under protected and stressed from climate change and pollution
- Conserve and sustainably use the oceans, seas and marine resources for sustainable development
- By 2030, sustainable management of fisheries, aquaculture and tourism
- Aims:
- Avoid plastic bags to keep the oceans safe and clean
- Conserve the under water environment

9.1.5.15 Goal 15. Life on Land
- Protect, restore and promote sustainable use of terrestrial ecosystems, sustainably manage forests, combat desertification, and halt and reverse land degradation and halt biodiversity loss
- By 2030, combat desertification, restore degraded land and soil
- Aims:
- Stop the threat to living ecosystems and biodiversity on land
- Protect the environment through tree planting

9.1.5.16 Goal 16. Peace, Justice and Strong Institutions
- Promote peaceful and inclusive societies for sustainable development, provide access to justice for all and build effective, accountable and inclusive institutions at all levels
- By 2030, significantly reduce unlawful financial and arms flows
- Aims:
- Reduce Violence
- End to Torture (折磨)
- Reduce Corruption

9.1.5.17 Goal 17. Partnerships for the Goals
- Strengthen the means of implementation and revitalize the Global Partnership for Sustainable Development (Every country has a role on SDGs)
- Aims:
- Ensure countries have what is needed in achieving the rest of the SDGs, (e.g. Funds, Capabilities & Technologies)
- Emphasize the need for partnership and collaboration


9.1.6 Portfolio Analysis
9.1.7 SDG Overview

9.2 Circular Economy
9.2.1 Current Economic Practice
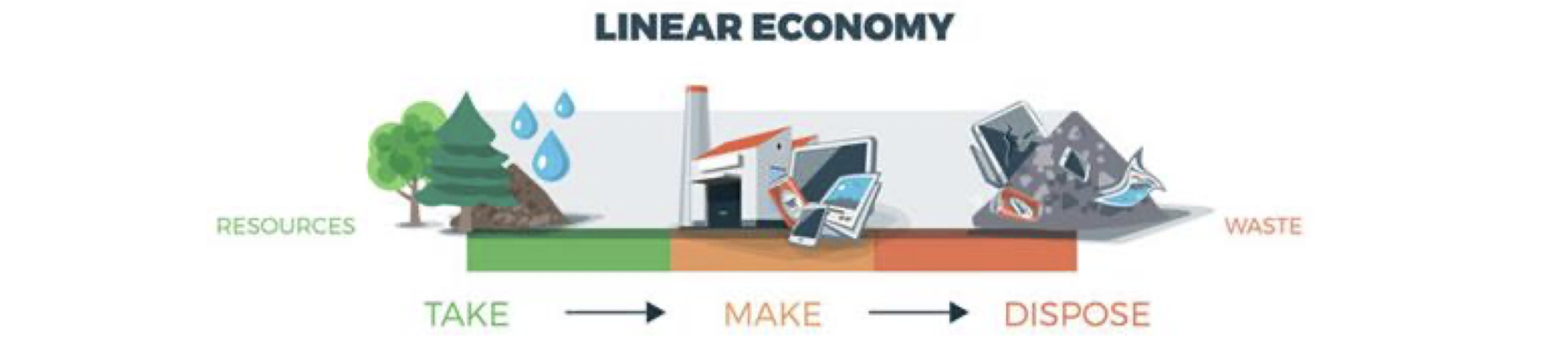
- Wasted Resource
- Wasted Lifecycles
- Wasted Capability
- Wasted Embedded Values
9.2.2 Opportunity
- Today’s business practices will contribute to a global gap of eight billion tons between the supply and demand of natural resources by 2030.
- Translates to $4.5 trillion of lost economic growth by 2030 and as much as $25 trillion by 2050.
- Five business models that will drive the circular economy:
- Sharing Platforms use digital technologies to max the use of underused assets
- Products-as-a-Service replace ownership-based models
- Product Life Extension relies on remanufacturing and repairing
- Circular Supply Chains allow suppliers and partners to use recycled materials repeatedly
- Recovery and Recycling saves costs and reduces the volume of waste and landfill
9.2.3 Introduction of Circular Economy
- The linear economy is based on a linear process, optimized towards high throughput and low production costs relying on the abundant availability of raw materials at relatively low cost. ( take-make-consume-dispose model )
- The circular economy , on the other hand, aims at low environmental impact by minimizing waste and excessive resource use by turning goods at the end of their lifespan into resources for others through re-use, re-manufacture, re-cycle, waste reduction and other practices. ( restorative by design and intention model )
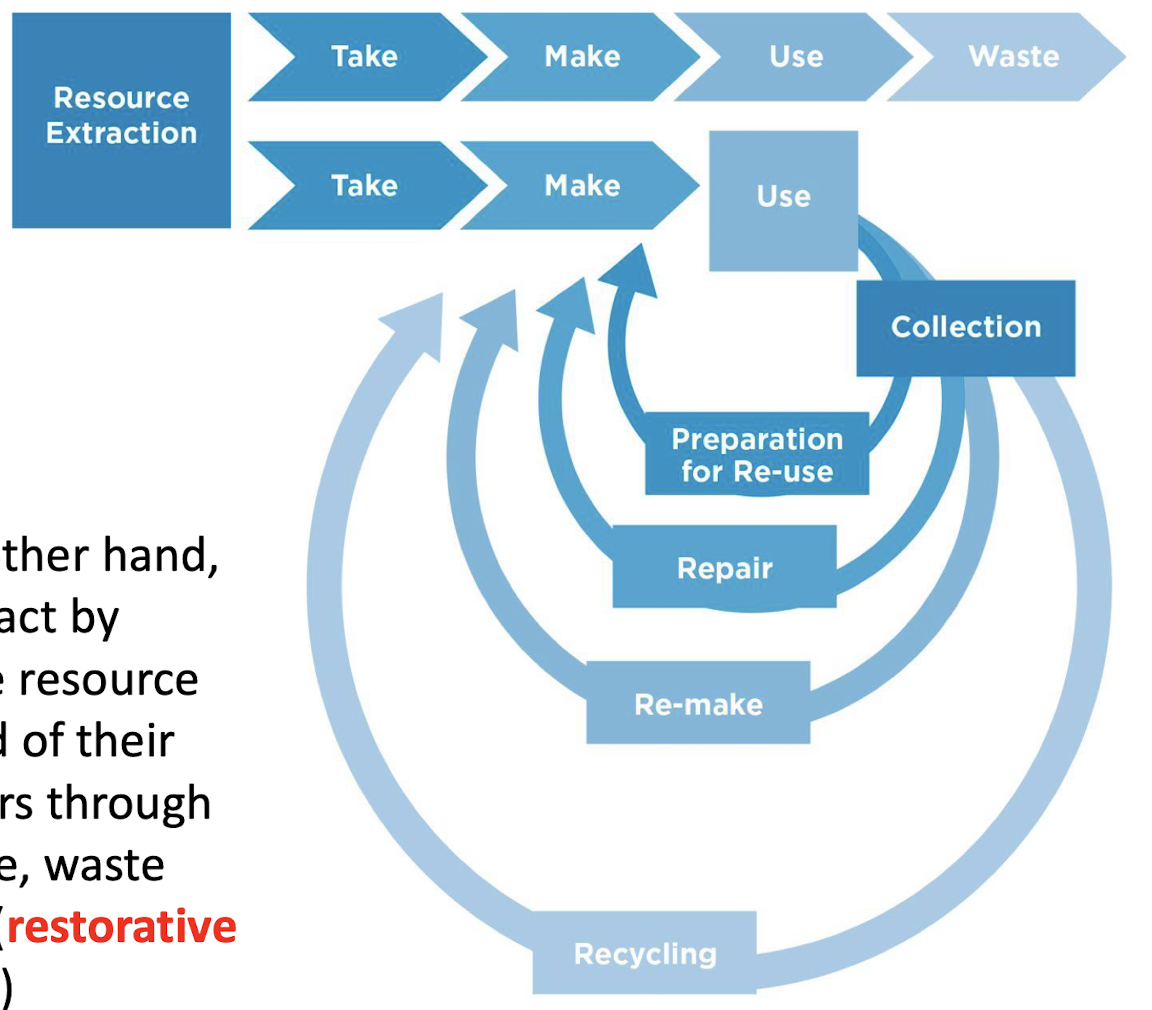
9.2.4 BSI Standards on Circular Economy
- BS 8001:2017 - Framework for implementing the principles of the circular economy in organizations – Guide
- The global population is estimated to increase to around 8 billion by 2030, probably to over 9 billion by 2050, competition for land, water and energy could intensify.
- The circular economy is not a new concept. It blends the principles of multiple schools of thought , some of which date back to the 1960s.
- In the circular economy, materials should not be discarded as wastes , but treated as raw materials with inherent value.
9.2.5 Circular Economy Concept
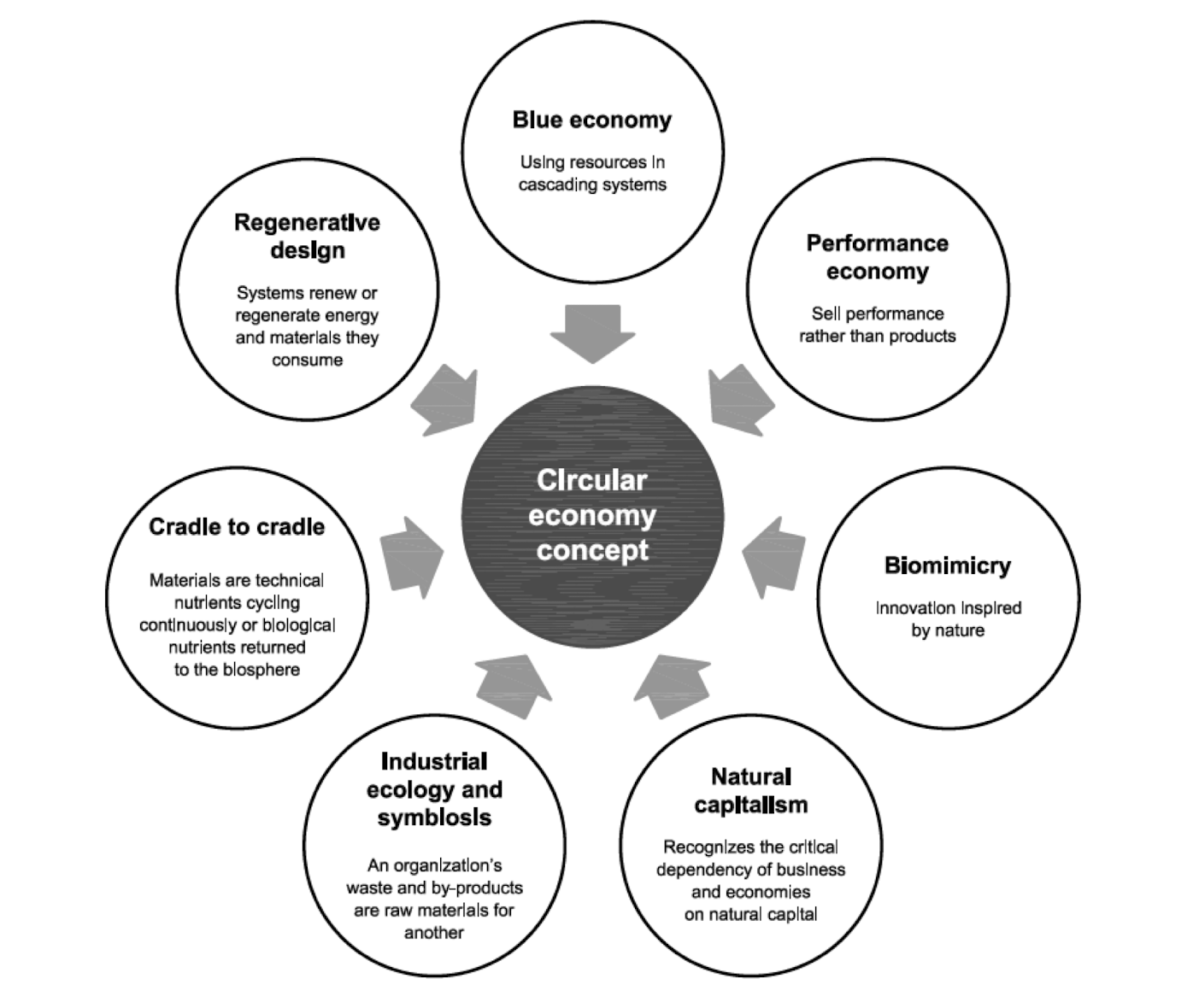
9.2.6 Framework for Implementing the Principles of the Circular Economy
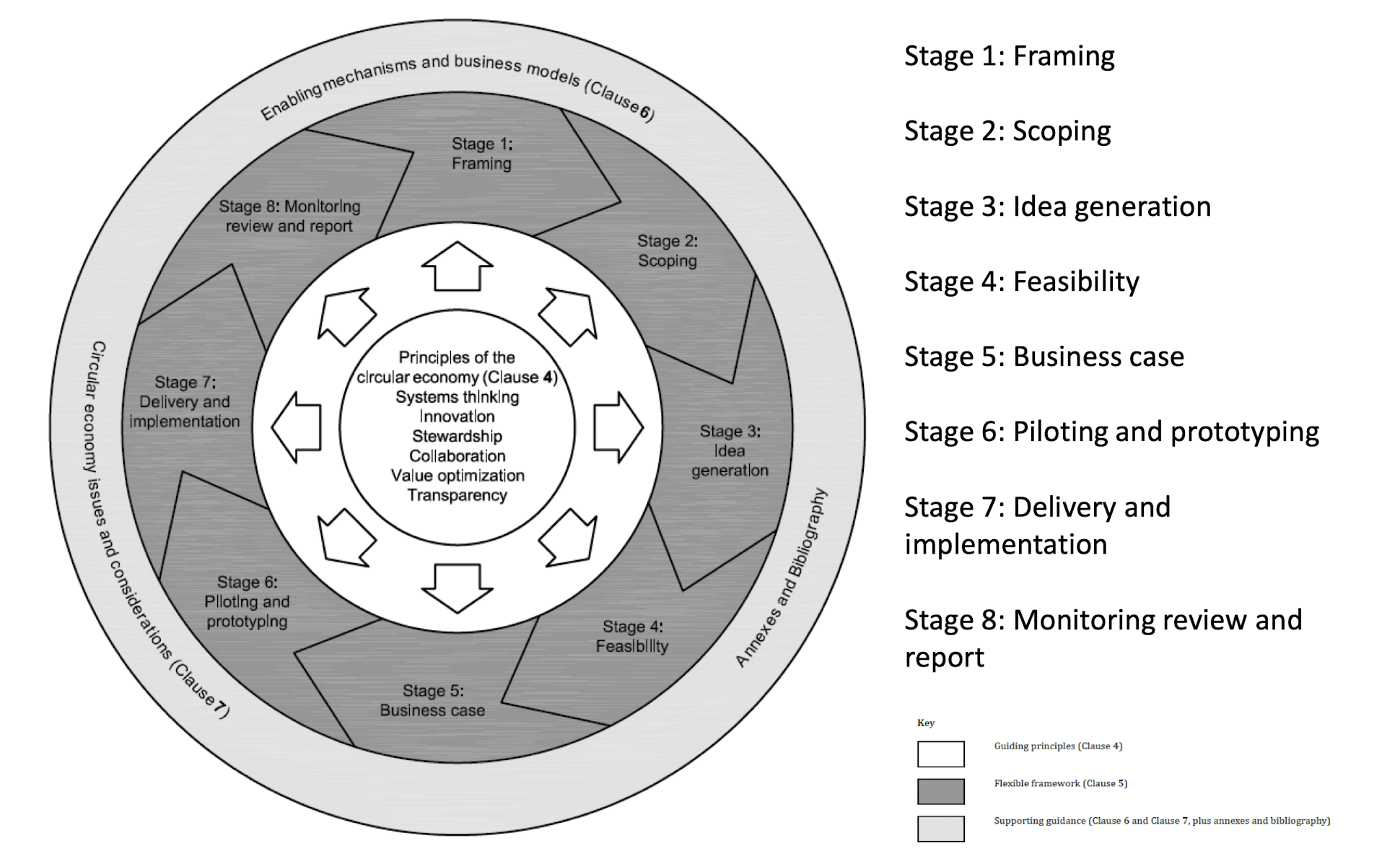
9.2.7 Circular Economy Six Principles
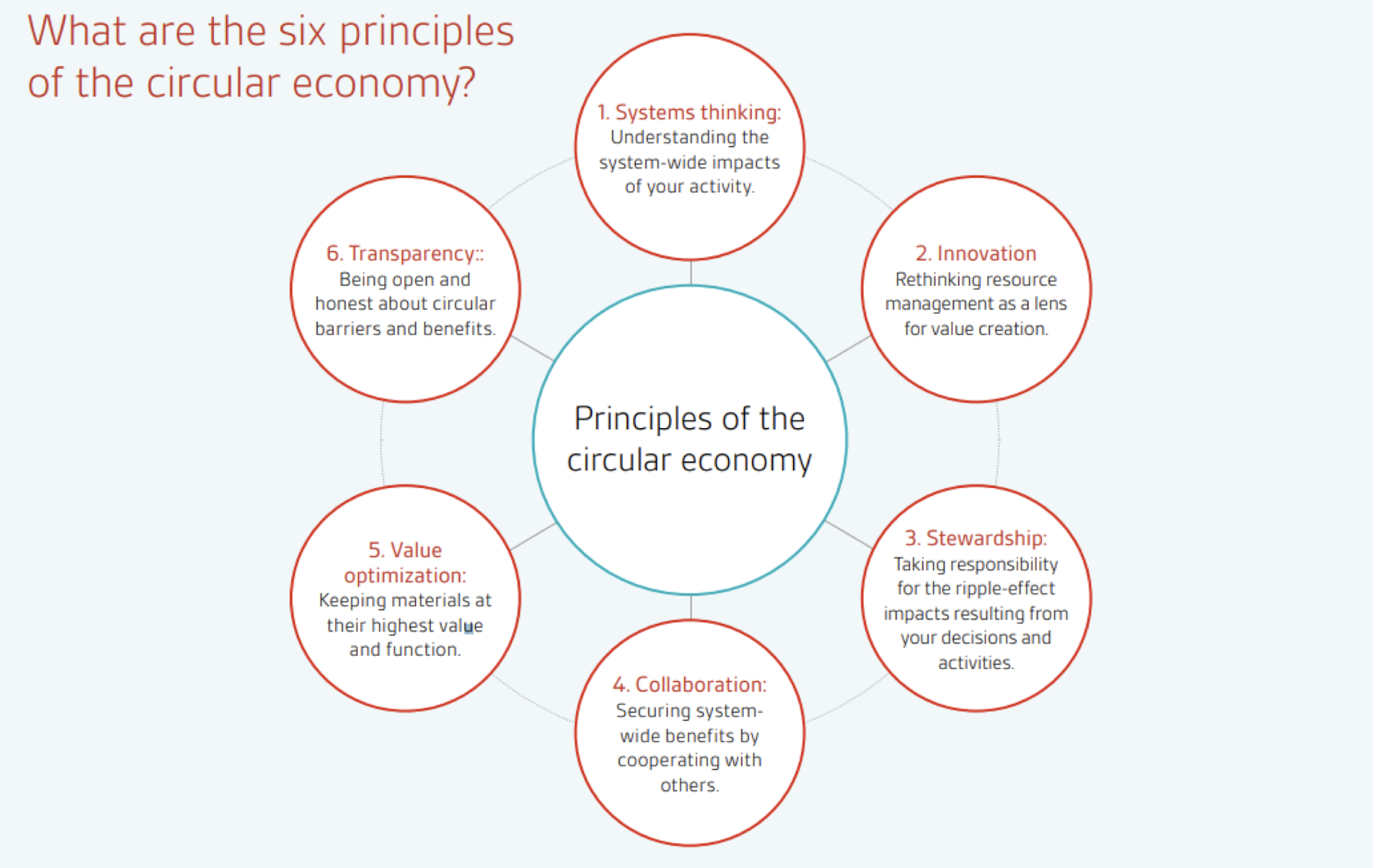
9.2.7 Level of organizational circularity maturity
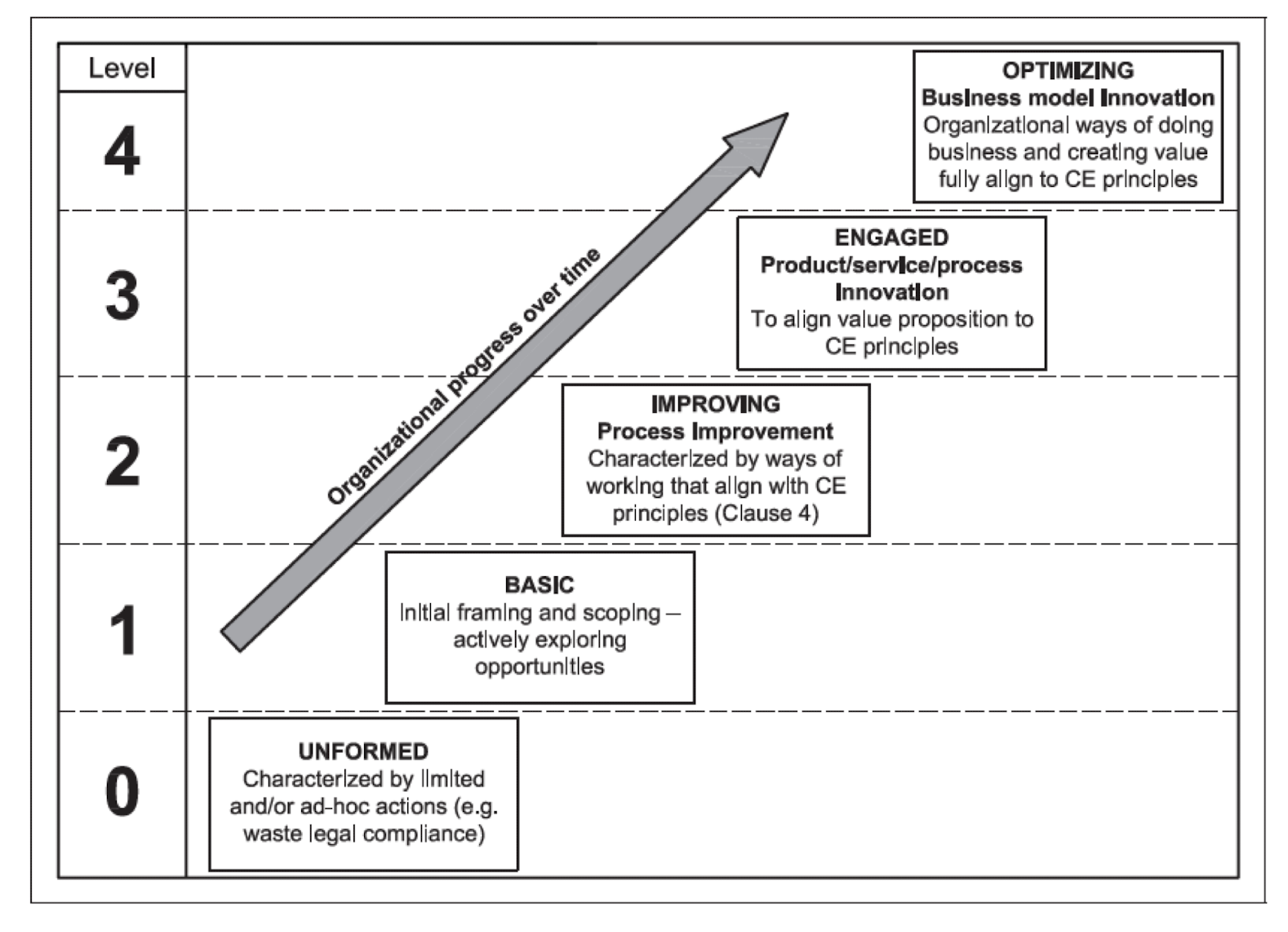
9.2.8 ISO/TC 323 CIRCULAR ECONOMY
Proposed by France in June 2018
Accepted by ISO in September 2018, 26 countries in favor of this new Technical committee
Secretariat allocated by ISO to AFNOR
Chair: C.Chevauché,SuezGroupe
Scope:
- Standardization in the field of circular economy to develop requirements, frameworks, guidance and supporting tools related to the implementation of circular economy projects. The proposed deliverables will apply to any organization or group of organizations wishing to implement circular economy projects, such as commercial organizations, public services and not-for-profit organizations.
Excluded:
- Specification of particular aspects of circular economy already covered by existing TCs, such as eco-design, life cycle assessment in ISO/TC 207 Environmental management and sustainable procurement (ISO 20400:2017–Sustainable procurement — Guidance).
9.2.9 ISO/TC 323 PARTICIPATION
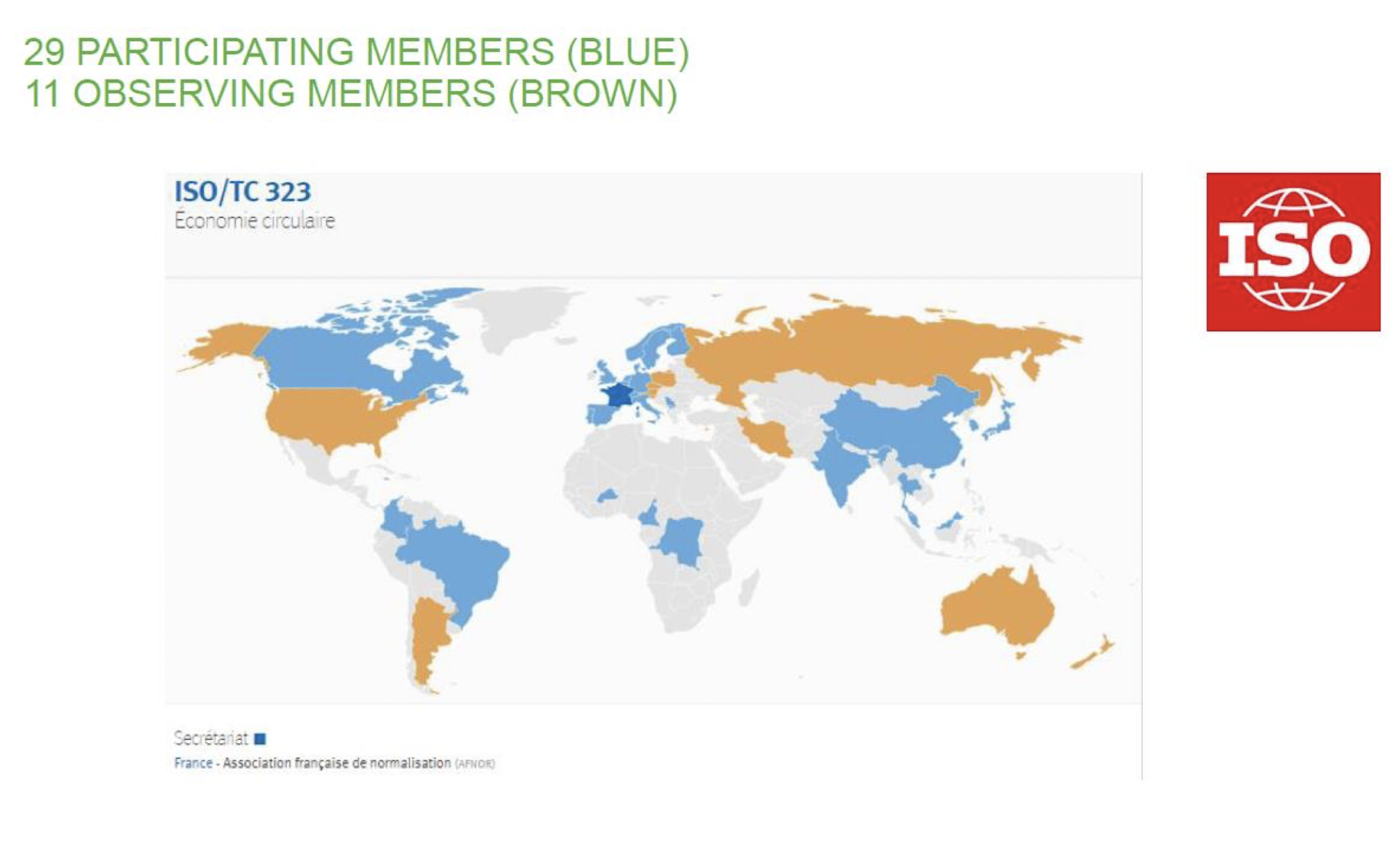
9.2.10 1ST MEETING: 20-22 MAY 2019 IN FRANCE
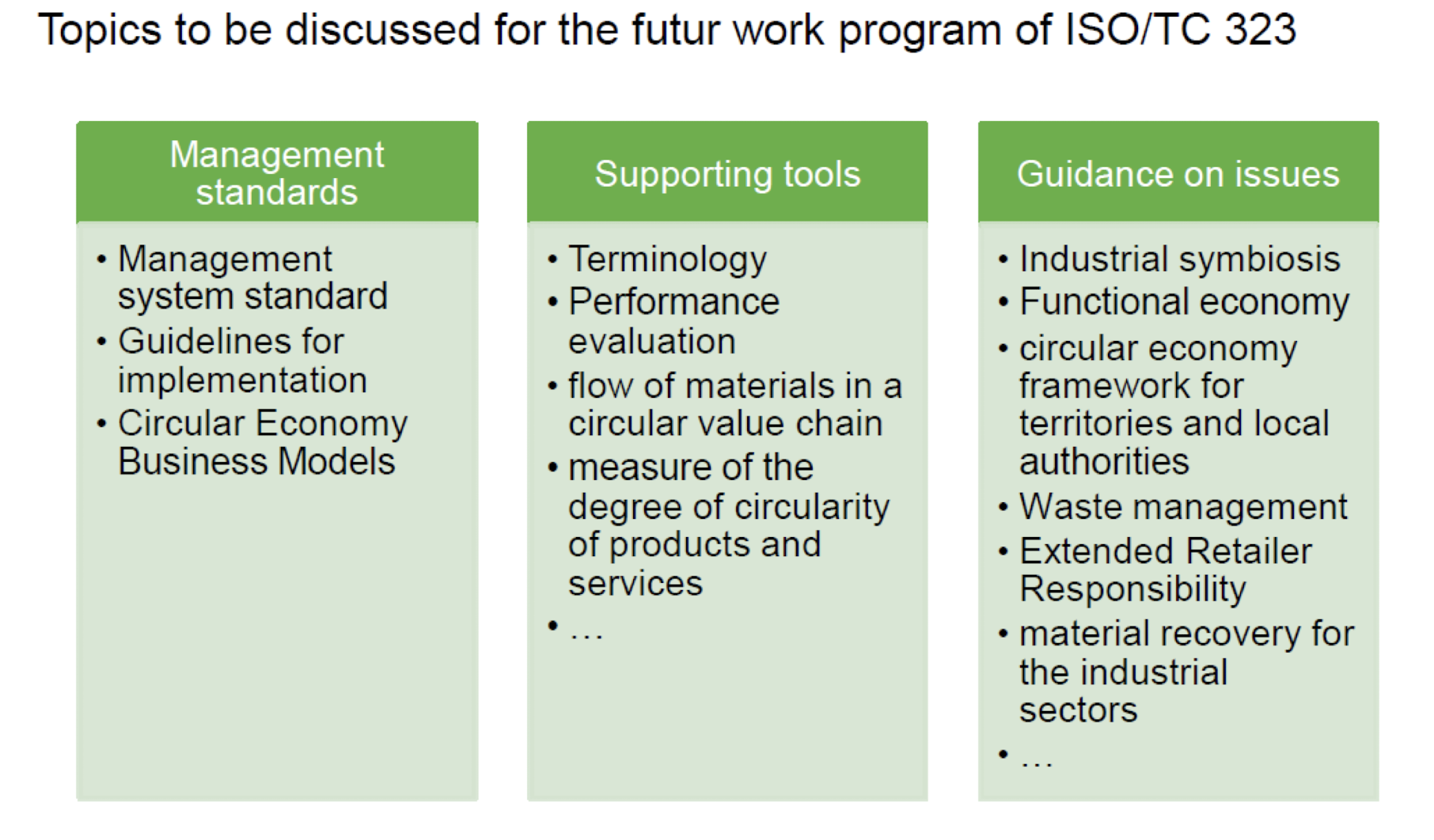
9.2.11 Sustainability Reporting

Example of Sustainability Report
https://www.tdk.com/system/files/wwwtdkcom_csr_report_pdf_sustainability_2020_en_3.pdf
10. Entrepreneurship Ecosystem
10.1 What is Business Ethics
Business Ethics

What Your Ethical Expectations are at Work?
Two Layers of Ethics in the Profession
- Truth
- Quality
10.2 What is an entrepreneur?
Attitude
- Be Positive
Creativity
- Imagination to solve the problem
Relationships
- Good with customer, employee & supplier
Organization
- Systems include Research, IT, Planning, Employees & Premises, etc.
Innovation
10.2.1 Evolution of Innovation Paradigms
- Open innovation paradigm:
- Open to new ideas.
- Open to alternatives.
- Open to ambiguity.
- Open to uncertainty.
10.2.2 Open Innovation
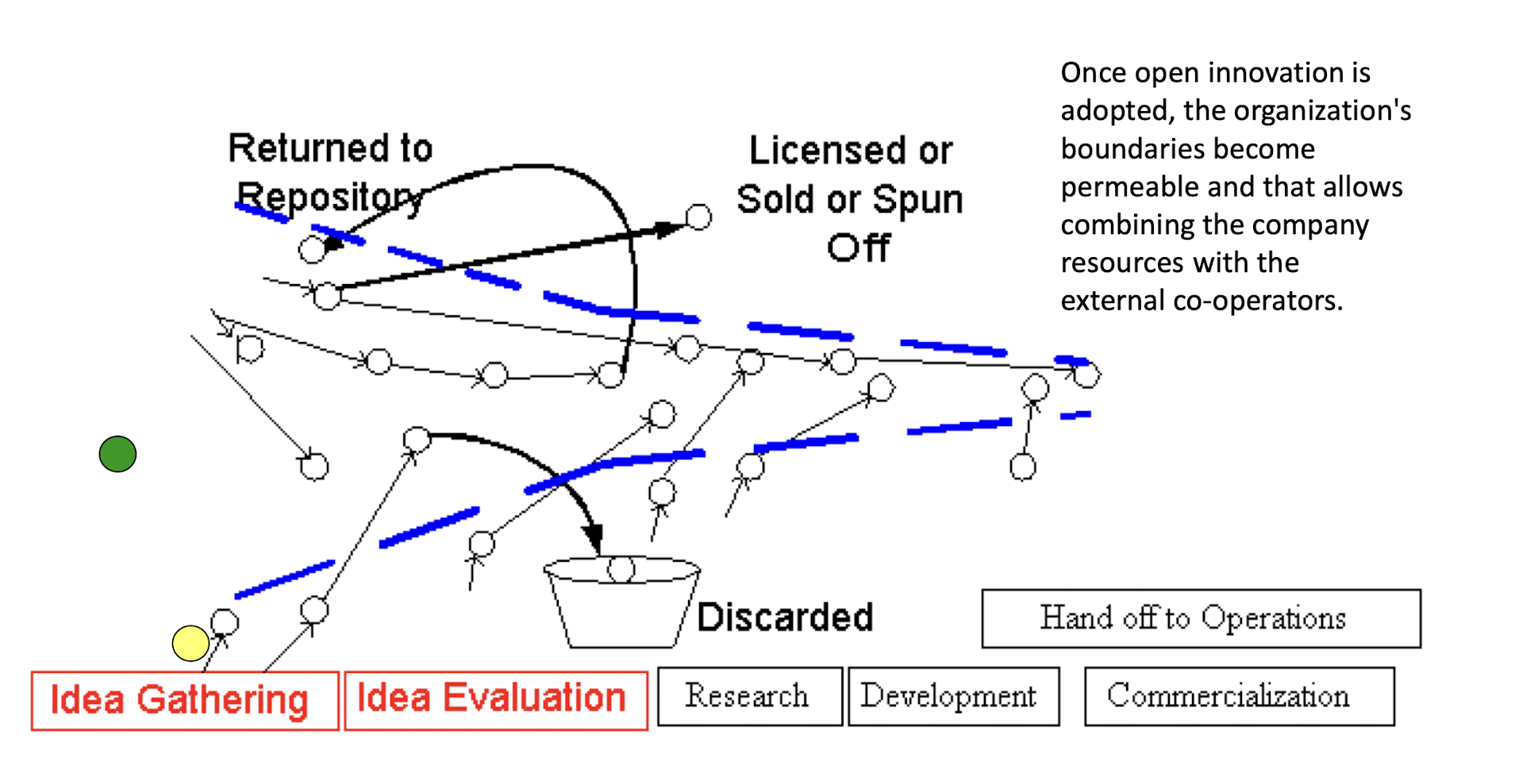
- Once open innovation is adopted, the organization’s boundaries become permeable and that allows combining the company resources with the external co-operators.
10.2.3 Rational versus Incremental
Both have advantages and disadvantages!
- Rationalist Strategy:
- analyse environment
- determine a course of action
- carry out!
- Problem: Knowledge not necessarily available – to acquire knowledge cost
- Incremental Strategy: recognise that you have imperfect knowledge; Adapt to new information and knowledge:
- take a (small) step
- evaluate the effects of that step
- adjust (if necessary) the objective and decide on the next step
- Problem: You can miss more radical innovations
10.2.4 Factors For Innovation Success
- Product Advantage - Refers to customer perceptions of product superiority with respect to quality, cost-performance ratio, or function relative to competitors’ products.
- Marketing Synergy - Represents the degree of fit between project needs and the firm’s resources and marketing skills.
- Technical Synergy - Comes from the fit between project needs and the firm’s R&D resources and competencies.
- International Orientation - New products designed and developed to meet foreign requirements, and targeted at world or nearest-neighbor export markets.
10.2.5 The Difference between Leader and Manager
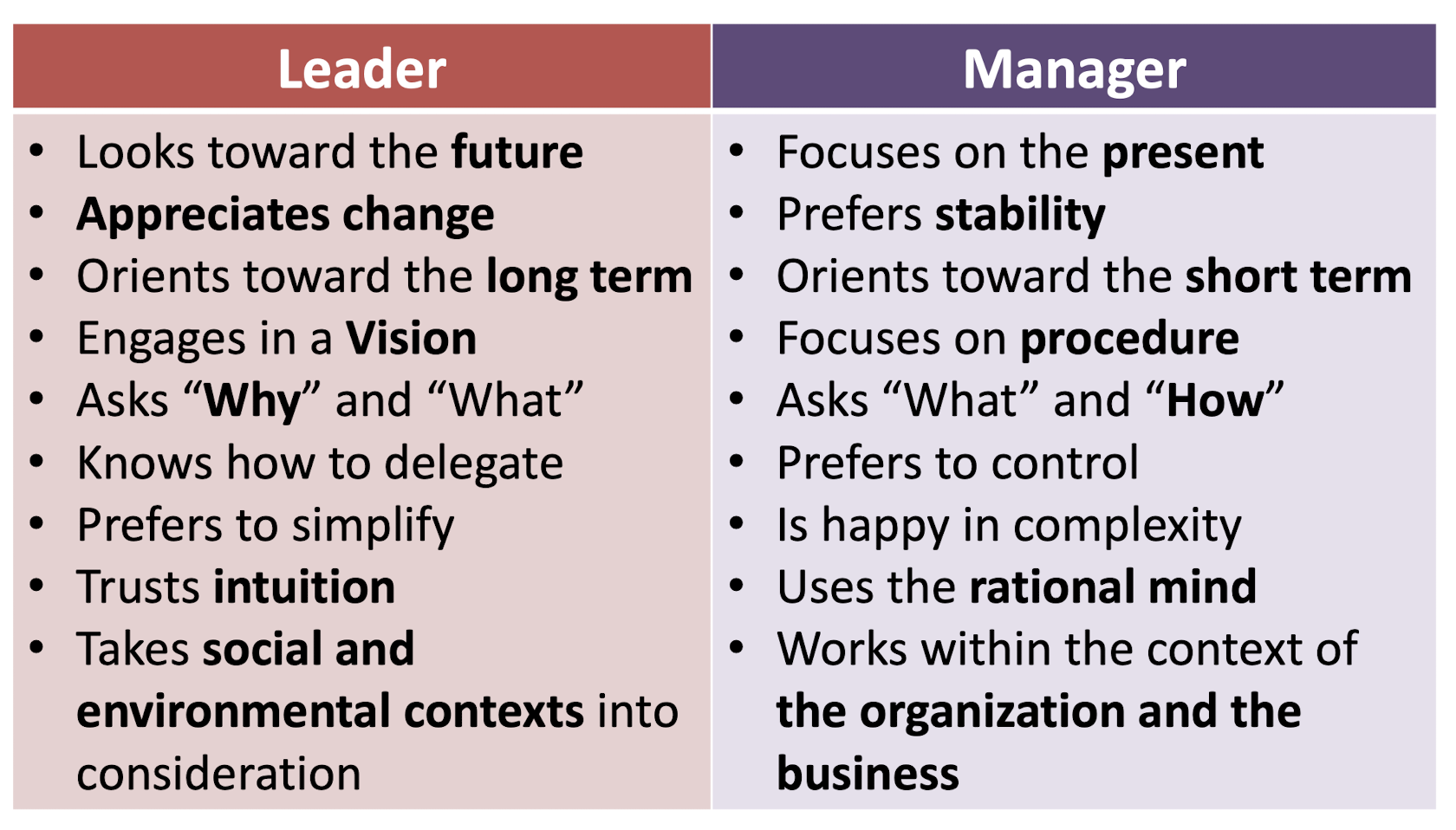
10.2.6 Leader Profile – Roles & Responsibilities
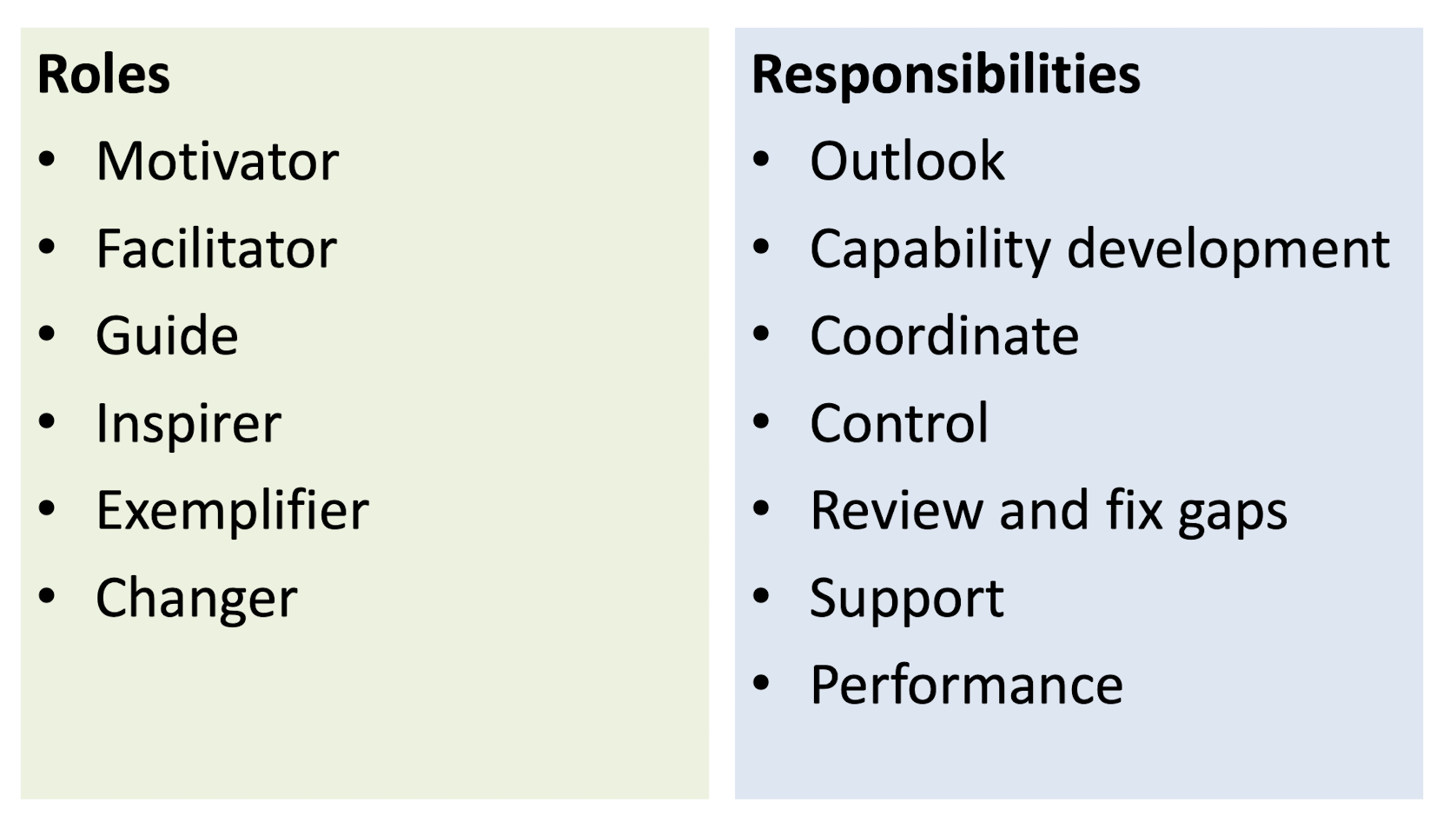
10.2.7 Select CEO
Now, we’ll send you 50 words start-ups are paying attention to. Within 30s, send in five startup keywords that are most relevant to each word. The people who get the most relevant keywords right will be chosen as CEOs.
- they want those who know how to read trends to be CEOs.
- Sharing - > USB, WiFi
- AI - > Deep learning, self-driving
- Aging Society - >
- Winter Olympics - >
- Blockchain - >
10.3 Introduction to SWOT Analysis
A process generates information that is helpful in matching an organization or group’s goals, programs, and capacities to the social environment in which it operates. Note that in itself is only a data capture – the analysis follows.
Strengths
- Positive tangible and intangible attributes, internal to an organization.
- They are within the organization’s control.
Weakness
- Factors that are within an organization’s control that detract from its ability to attain the desired goal.
- Which areas might the organization improve?
Opportunities
- External attractive factors that represent the reason for an organization to exist and develop.
- What opportunities exist in the environment, which will propel the organization? Identify them by their “time frames”
Threats
- External factors, beyond an organization’s control, which could place the organization mission or operation at risk.
- The organization may benefit by having contingency plans to address them if they should occur.
- Classify them by their “seriousness” and “probability of occurrence”.
10.3.1 History of the SWOT Analysis
- The origins of the SWOT analysis technique is credited by Albert Humphrey, who led a research project at Stanford University in the 1960s and 1970s using data from many top companies.
- The goal was to identify why corporate planning failed.
- The resulting research identified a number of key areas and the tool used to explore each of the critical areas was called SOFT analysis.
- Humphrey and the original research team used the categories “What is good in the present is Satisfactory, good in the future is an Opportunity; bad in the present is a Fault and bad in the future is a Threat.”
In 1964 Urick and Orr at a conference changed the F to a W, and it has stuck as that, soFt to sWot
https://rapidbi.com/swotanalysis/
10.3.2 Overview SWOT Matrix
- The SWOT analysis is great for developing an understanding of an organization or situation and decision-making for all sorts of situations in business, organizations and for individuals. The SWOT analysis approach headings provide a good framework for reviewing strategy, position and direction of a company, product, project or person (career).
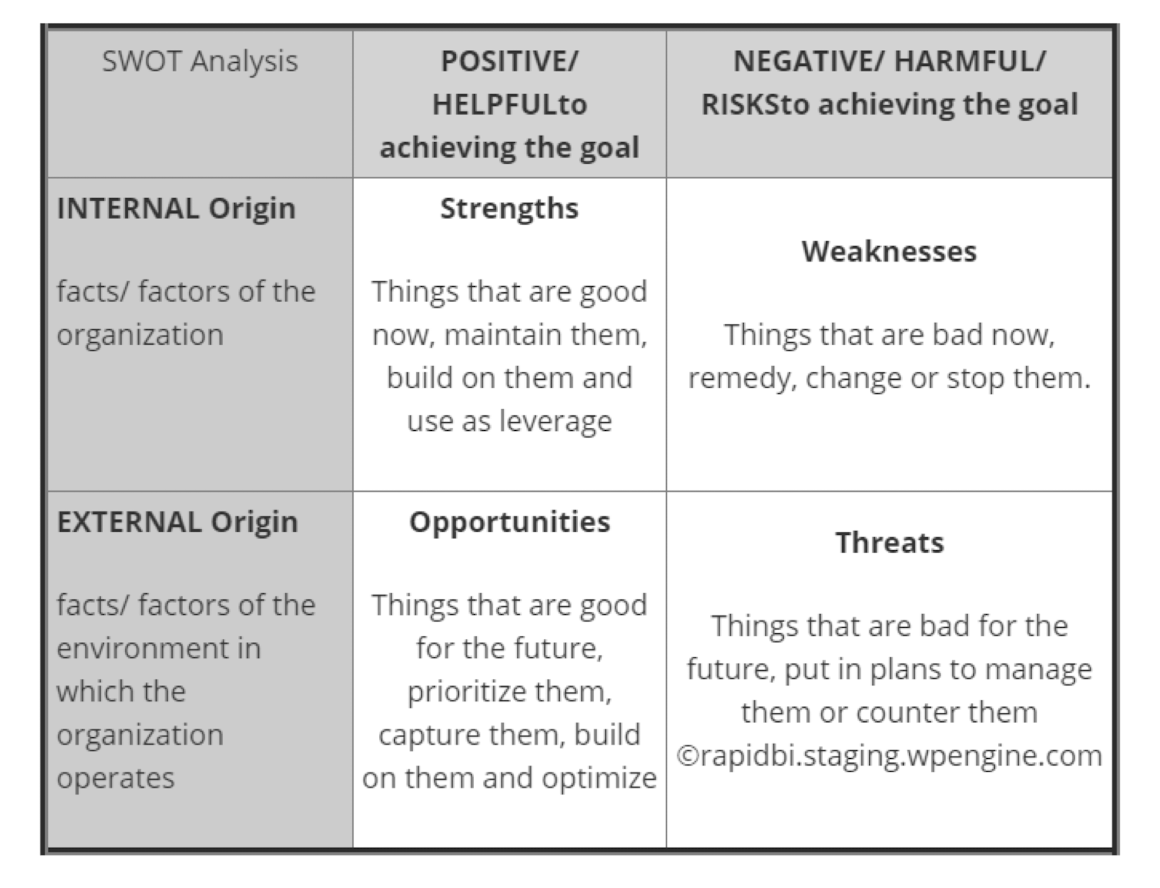
10.3.3 New Project SWOT Analysis
- Strength: characteristics of the business or project that give it an advantage over others
- (e.g. to enhance its functionality / to streamline work procedures / to produce consistent quality)
- Weaknesses: characteristics of the business that place the business or project at a disadvantage relative to others
- (e.g. high cost / lack of reputation / require a lot of resources for training)
- Opportunities: elements in the environment that the business or project could exploit to its advantage
- (e.g. untapped market / fast growth)
- Threats: elements in the environment that could cause trouble fro the business or project
- (e.g. price erosion / keen competition)
10.3.4 SWOT Analysis (STEM)
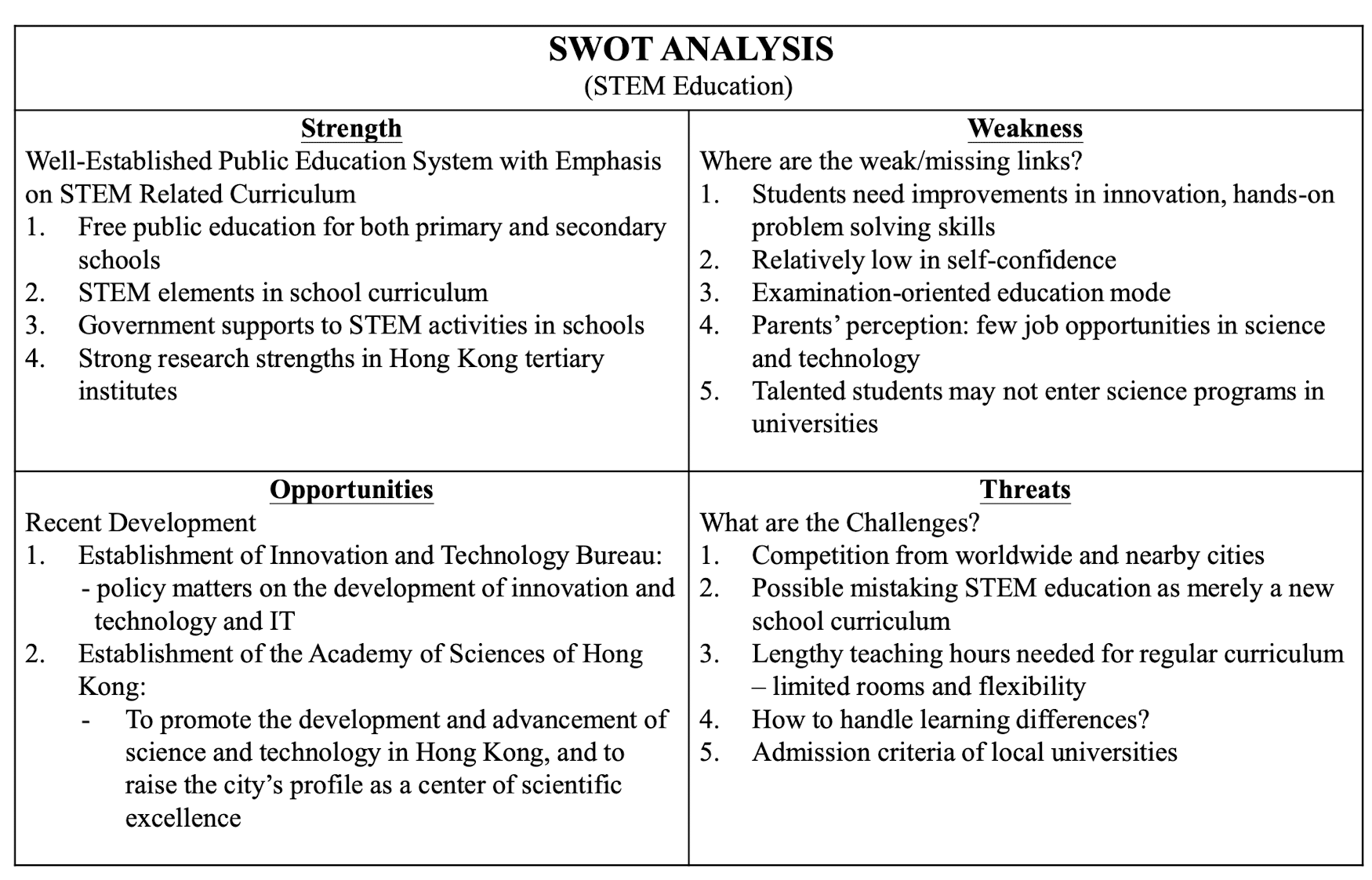
10.3.5 Personal SWOT Analysis
- A personal SWOT analysis can do the same for an individual in pursuit of their career goals. It provides insights based on your personality strengths and weaknesses, what challenges you see ahead of you, and what opportunities are present around you now and in the future.
- Begin by identifying your strengths.
- What are you good at naturally?
- What skills have you worked to develop?
- What are your talents, or natural-born gifts?
- The next step is weaknesses.
- What are your negative work habits and traits?
- Does any part of your education or training need improvement?
- What would other people see as your weaknesses?
- For the opportunities section, look at the external factors you can take advantage.
- What is the state of the economy?
- Is your industry growing?
- Is there new technology in your industry?
- Finally, look at any threats to your career growth.
- Is your industry contracting or changing direction?
- Is there strong competition for the types of jobs for which you are best suited?
- What is the biggest external danger to your goals?
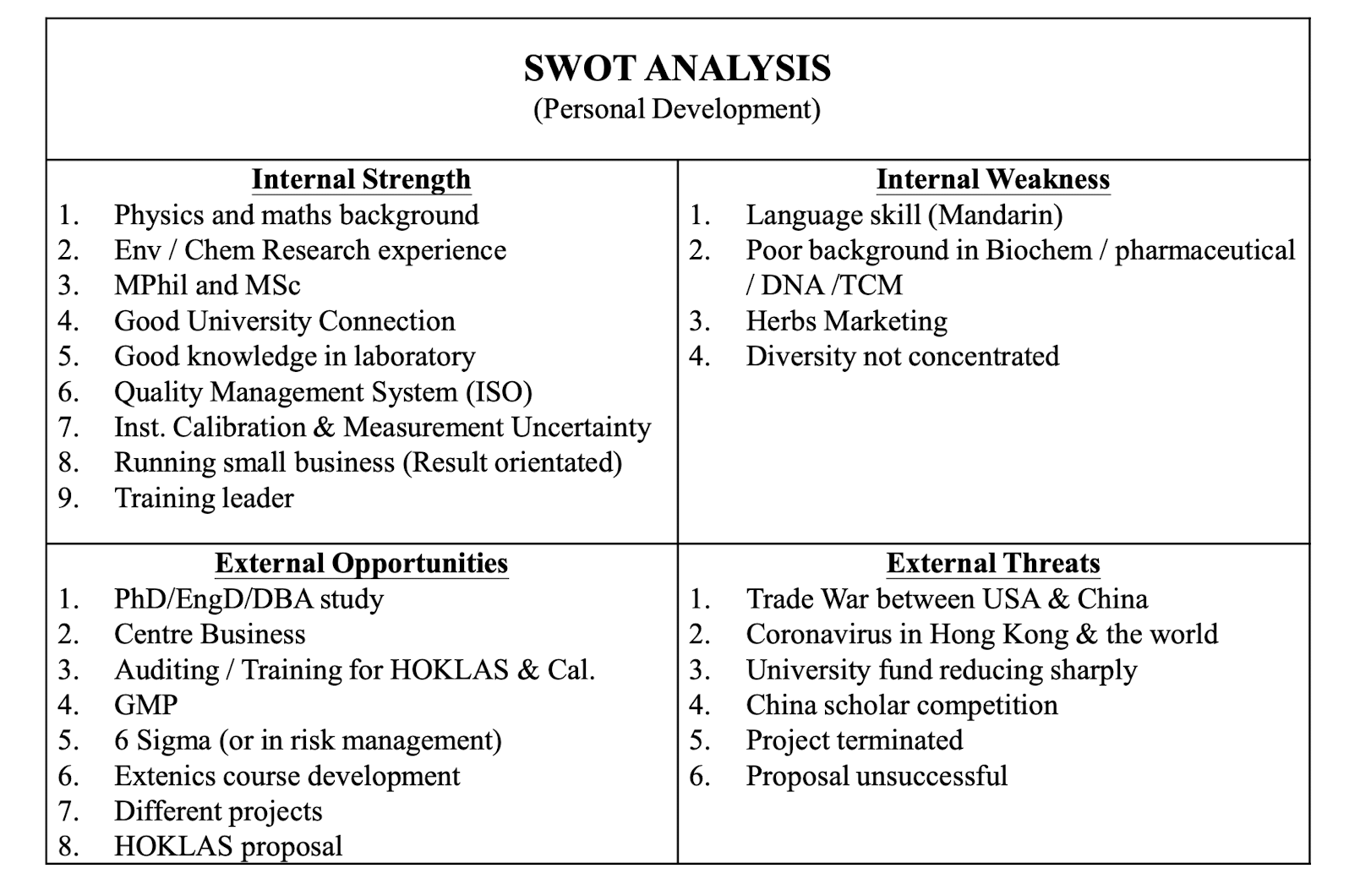
10.3.6 Startup as a Project that’s Meaning and Implementation
- Meaning
- The Golden Circle (Simon Sinek)
- Implementation
- Objectives and Key Results (OKRs)
10.4 The Golden Circle
10.4.1 WHWHW Circle: Why How What How Why
What
- Every organization on the planet knows WHAT they do. These are products they sell or the services they offer.
How
- Some organizations know HOW they do it. These are the things that make them special or set them apart from their competition.
Why
- Very few organizations know WHY they do what they do. WHY is not about making money. That’s a result. It’s a purpose, cause or belief. It’s the very reason your organization exists.
10.4.2 Idea Mapping to find “Why”
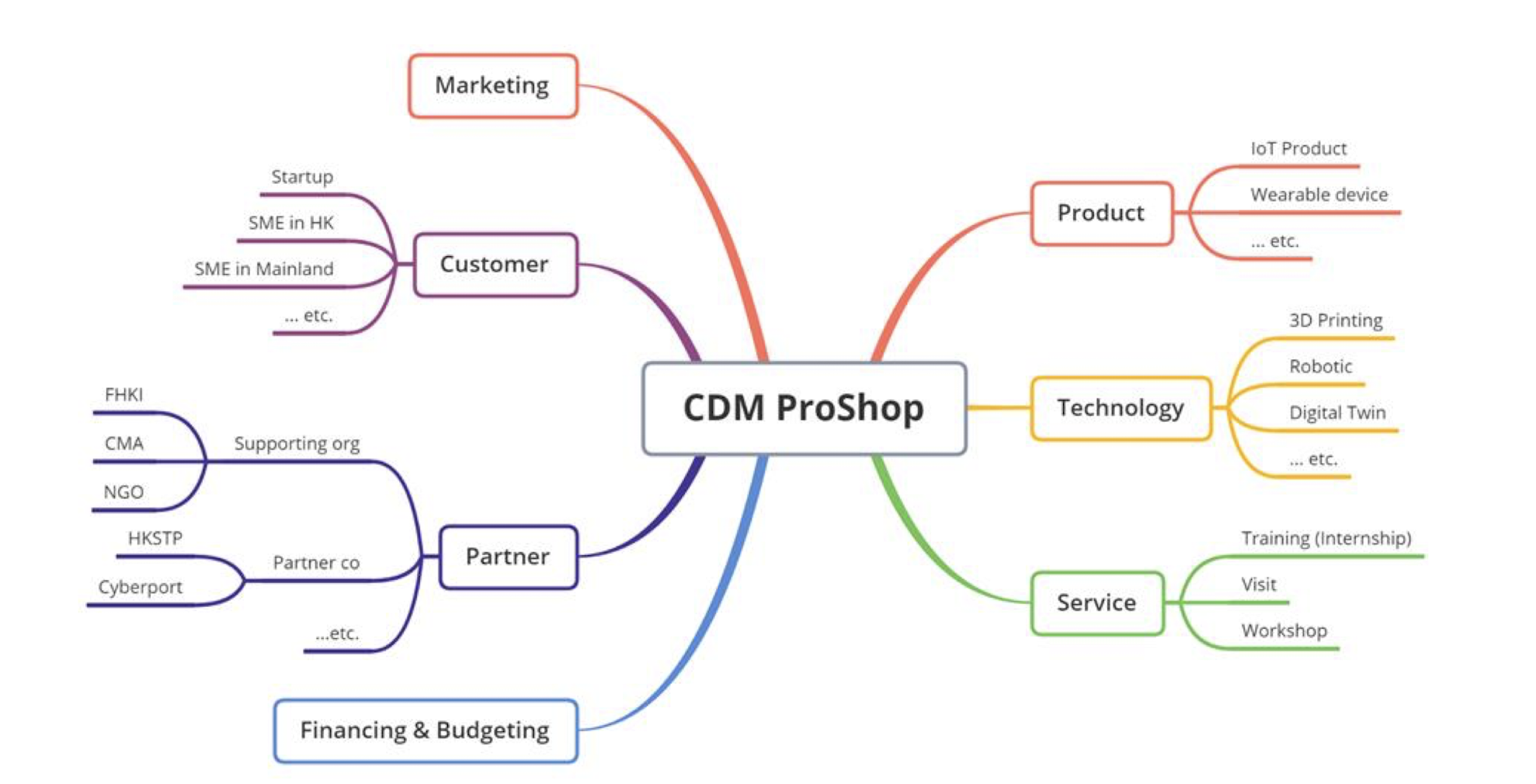
10.4.3 Objectives and Key Results (OKRs)
- “ Ideas are precious, but they’ve relatively easy. It’s execution that’s everything. “ - John Doerr (Author of “Measure What Matters: How Google, Bono, and the Gates Foundation Rock the World with OKRs”)
- John Doerr: Aspiration (Why) $\to$ Objectives (What) $\to$ Key Results (How)
https://www.youtube.com/watch?v=L4N1q4RNi9I
10.4.4 What is OKRs methodology?
- Objective – Set quarterly goals
- Key Results – Measure metrics progress
- Share it with leaders & co-workers
- One direction everyone works towards
- Aligned & linked hierarchy
- Company $\to$ Department $\to$ Team $\to$ Personal
- Transparency and open clearly communicated teamwork
10.4.5 Implementation steps of OKRs
- Soul-Search Your Aspirations (Motivational & Strategic)
- Make sure your Objectives Fit the Criteria
- Set only 3-5 Objectives Total
- Ensure the OKR process is 70% Bottom-up
- Check on Progress Frequently Without Fail
- Take Ambitious Challenges
- Specify the Tactics that will achieve each Objectives.
10.4.6 Five Payoffs
10.4.7 Timing
10.4.8 Example of OKRs
10.4.9 HKSQ OKRs Settings
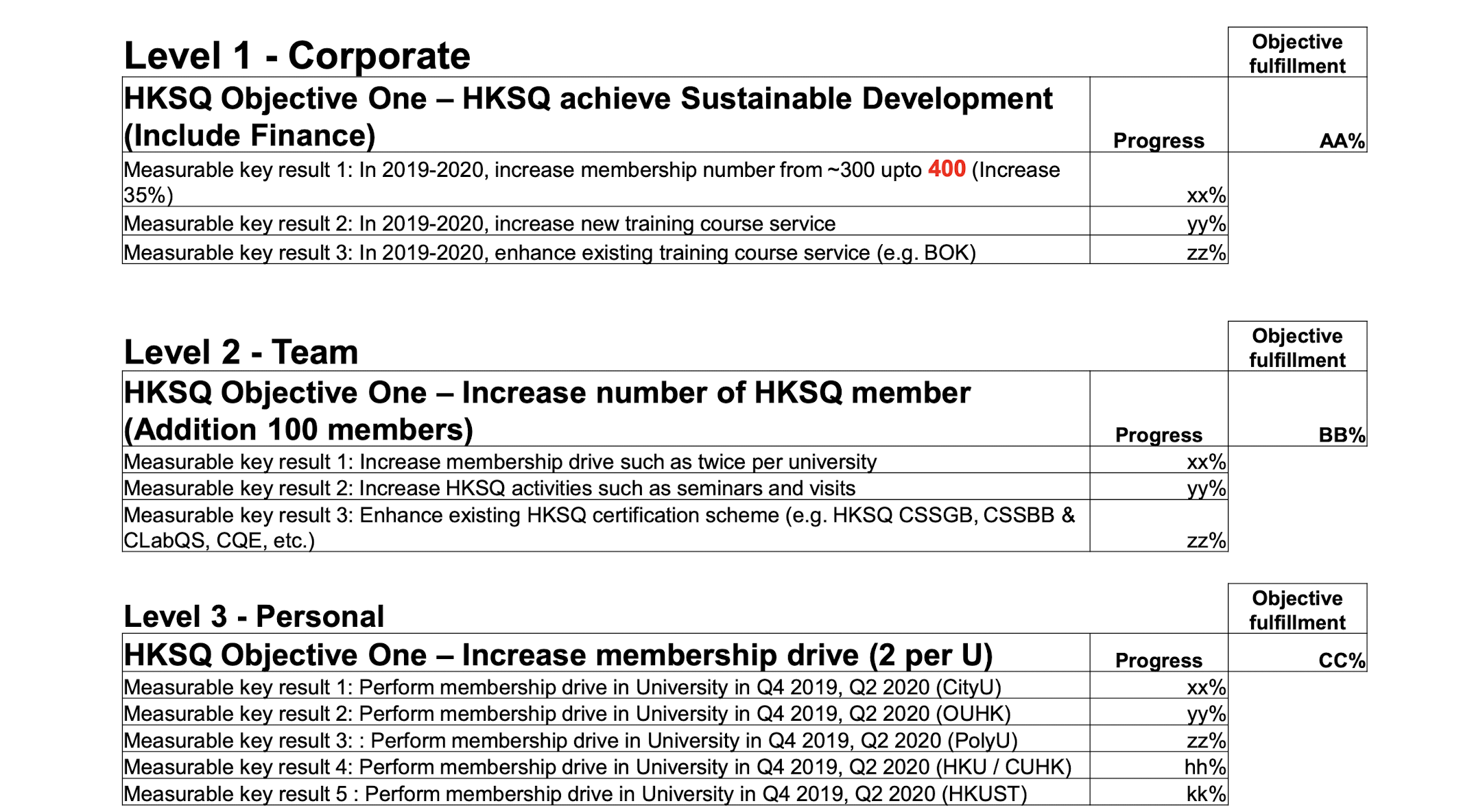
10.4.10 Distribution of HKSTP & Cyberport incubatees in HK (2018)
10.4.11 Comparison with other counties’ startup
10.4.12 Startups across a wide range of Industries
Hong Kong remains attractive to the startups in a diverse range of industries. The “Fintech” sector retained its top spot, followed by “E-commerce/ supply chain management/ logistics technology”. The pandemic had catalysed the popularity of specific sectors, which led to a healthy increase in the number of startups under “Education & learning”, “BioTech” and “Health & medical”.
10.4.13 Whole Startup Cycle under CityU & HKSTP Ecosystem
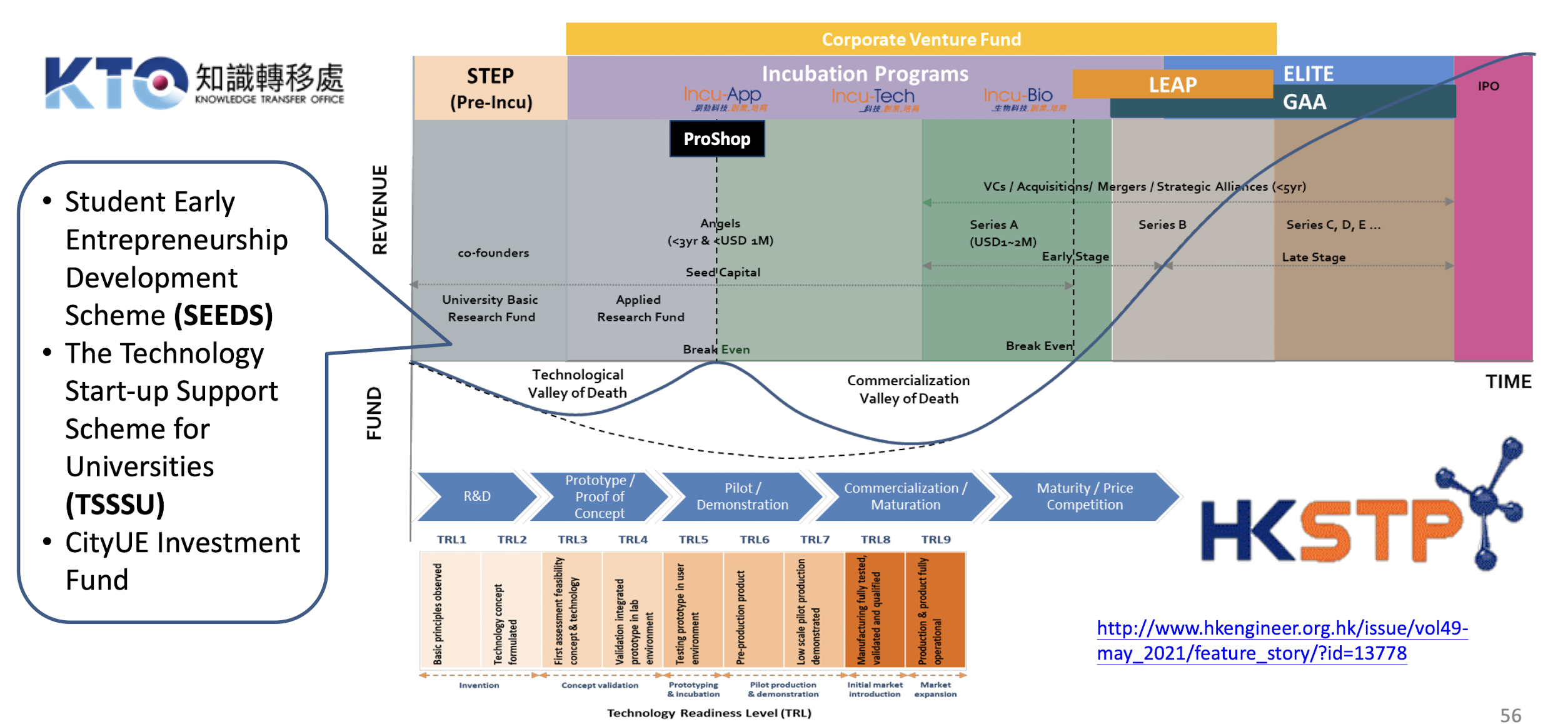
10.4.14 Four IP Protection Options
- It includes:
1. Patents (Inventions such as processes and machines; Controversial areas such as business method and software)
2. Copyright (Original work of authorship and Copyrightable matter such as software, manuals and company documents)
3. Trademark (Word, phase or symbol for slogan, company name and product line)
4. Trade Secret (Any Confidential Info that gives the owner competitive benefit or economic value)
10.4.15 Excise to understand the different
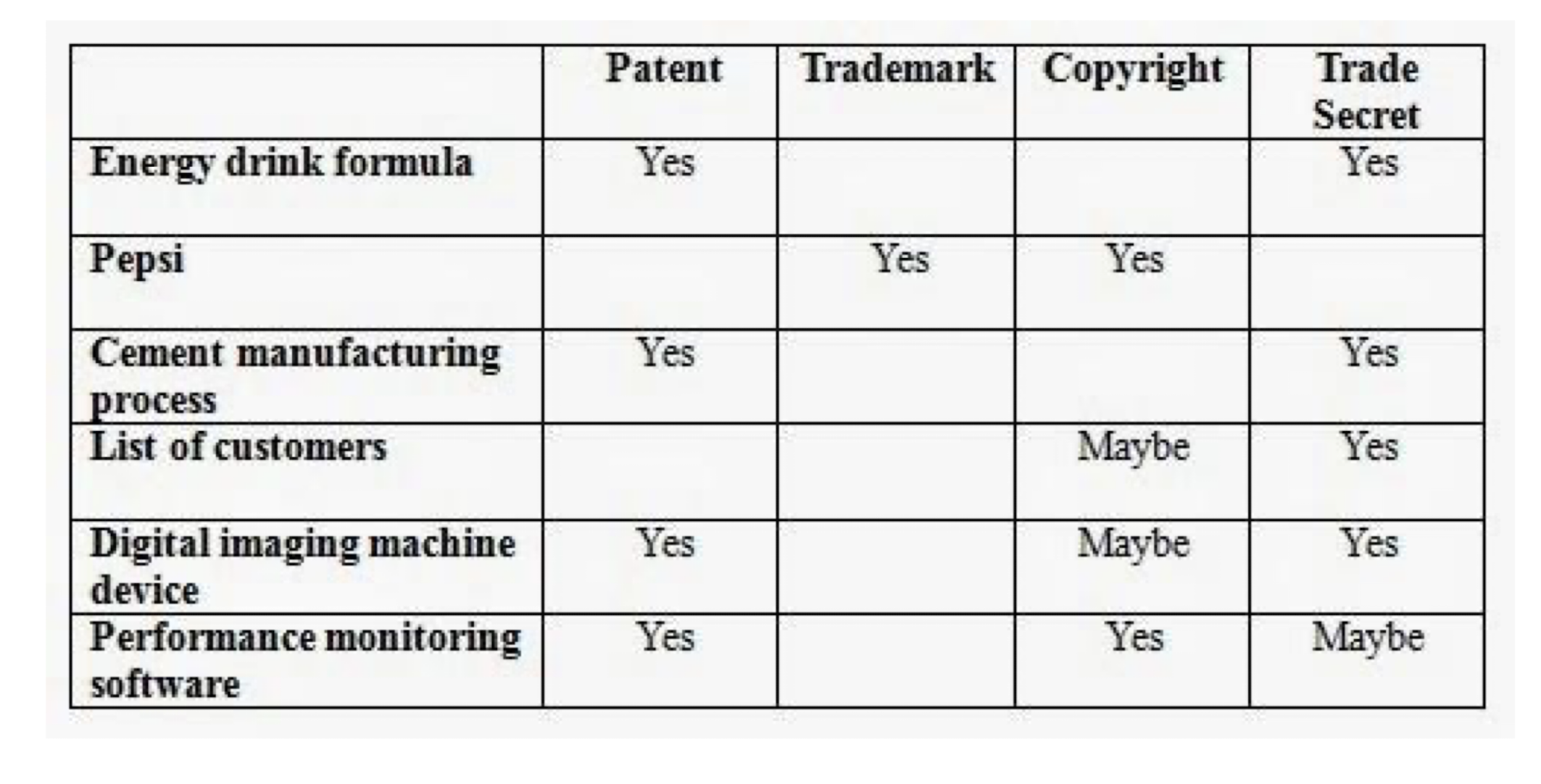
10.5.16 Startups Support from other Countries and Regions

10.5.17 Memorandum of Understanding (MOU) Hong Kong Innovation and Technology Support Programme

10.5.18 Business Model Canvas – Incubation Program
10.5 Development of Quality Startup Management System (QStarMS) Model (I)
- Limitation of Business Model Canvas
- It excludes organization’s strategic purpose (Only financial success drive start-up)
- It excludes a notion of competition
- It mixes levels of abstraction
10.5.1 ISO 9001:2015 – PDCA Cycle with Standard Structure
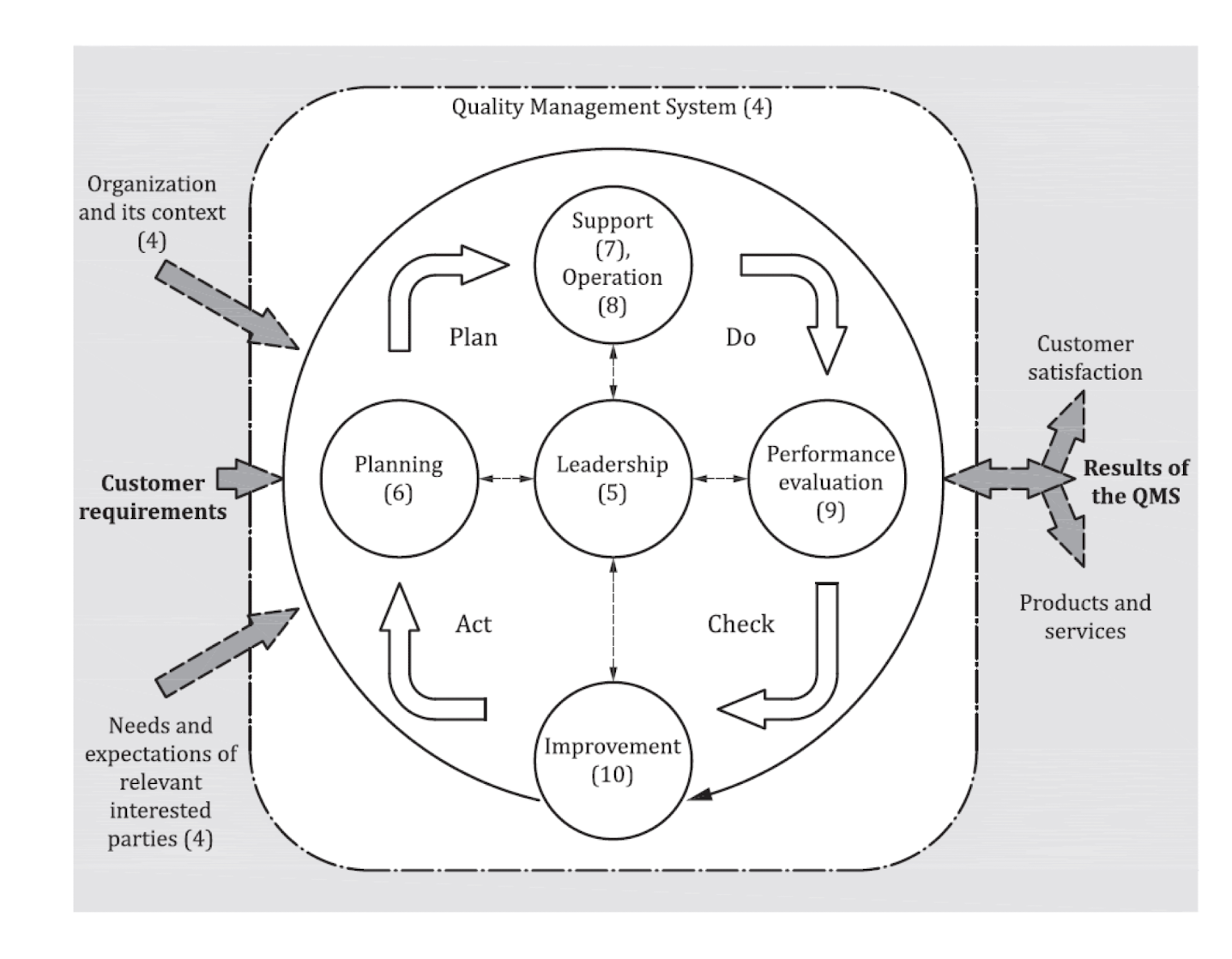
- Barriers for Start-up Company to achieve ISO 9001 QMS
- Limitation on Human Resource (Few key members in start-up only)
- Limitation on Knowledge of QMS (No training in the beginning of start-up business)
- Inadequate Management Commitment (Product & Business Development (or Survive) is the first priority.)
- Inadequate Attitude Towards Quality (Delivery first)
- Heavy Documentation Requirement (No practice on traceability)
- Over-expectation on ISO 9001 Standard (What its value on start-up in terms of business?)
- Short-sighted Goal for “Getting Certified” (Access government or big company’s tender list)
- Unrealistic Requirements
10.5.2 HKSTP Incubation Milestone Assessment
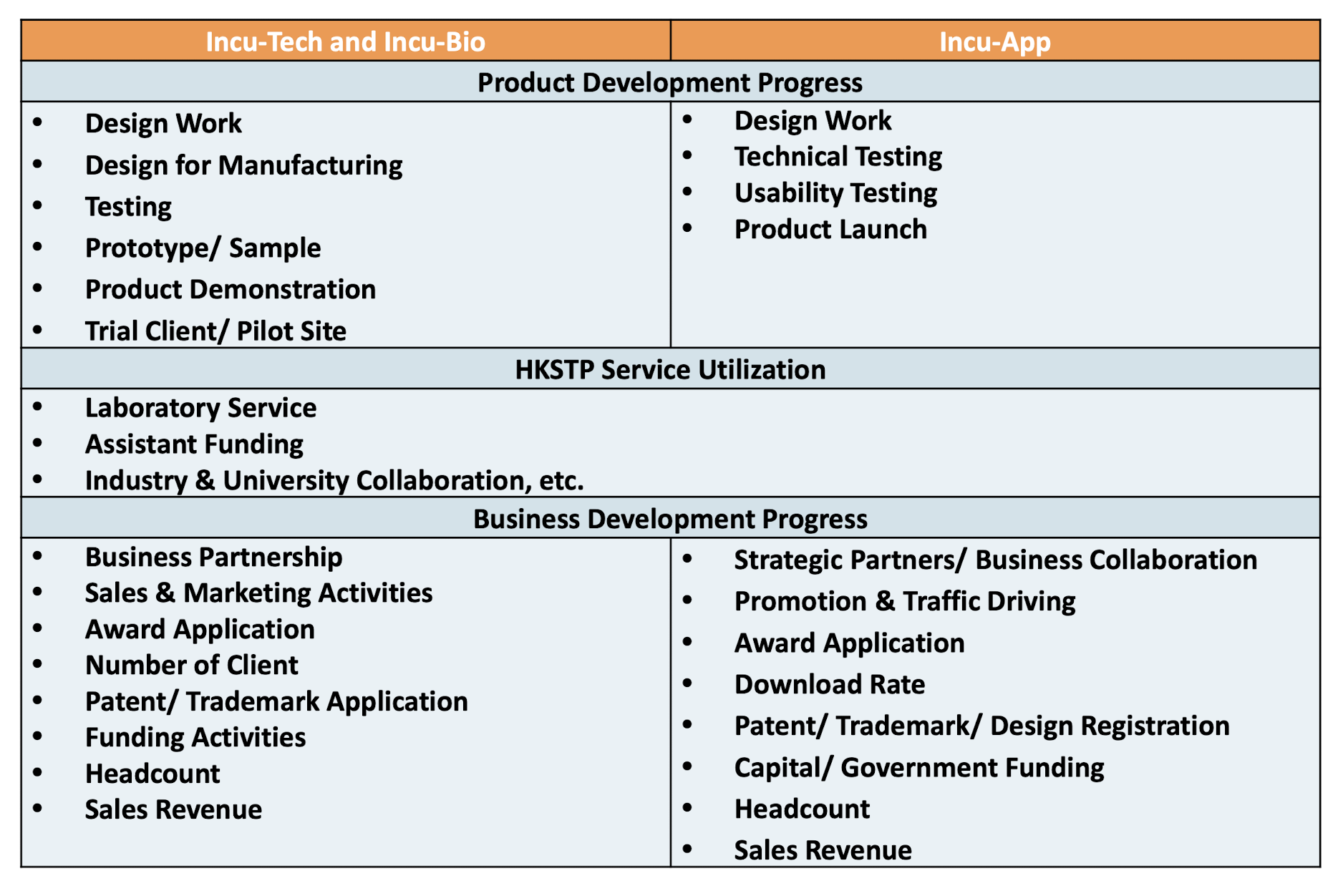
- Observations on HKSTP Incubation Milestone Assessment
- Most of start-ups had planned and met their product development under their milestone.
- About 50% of start-ups did not consider “Design for Manufacturing”. It is probably the IT dominant start-ups in the scheme.
- More than 80% of start-ups planned to employ “HKSTP Service Utilization” so as to enhance their product development.
- For Business Development , it observed:
- Difficulty to achieve the “Headcount” and “Sales Revenue” they planned in the last three milestones (on 18 th , 24 th and 30 th month).
- More than 60% of start-ups without planning for Award Application
- About 50% start-ups did not consider “Patent / Trademark Application” and “Funding Activities”.
10.5.3 HKQAA Startup Recognition Scheme – Checklist (Scope)
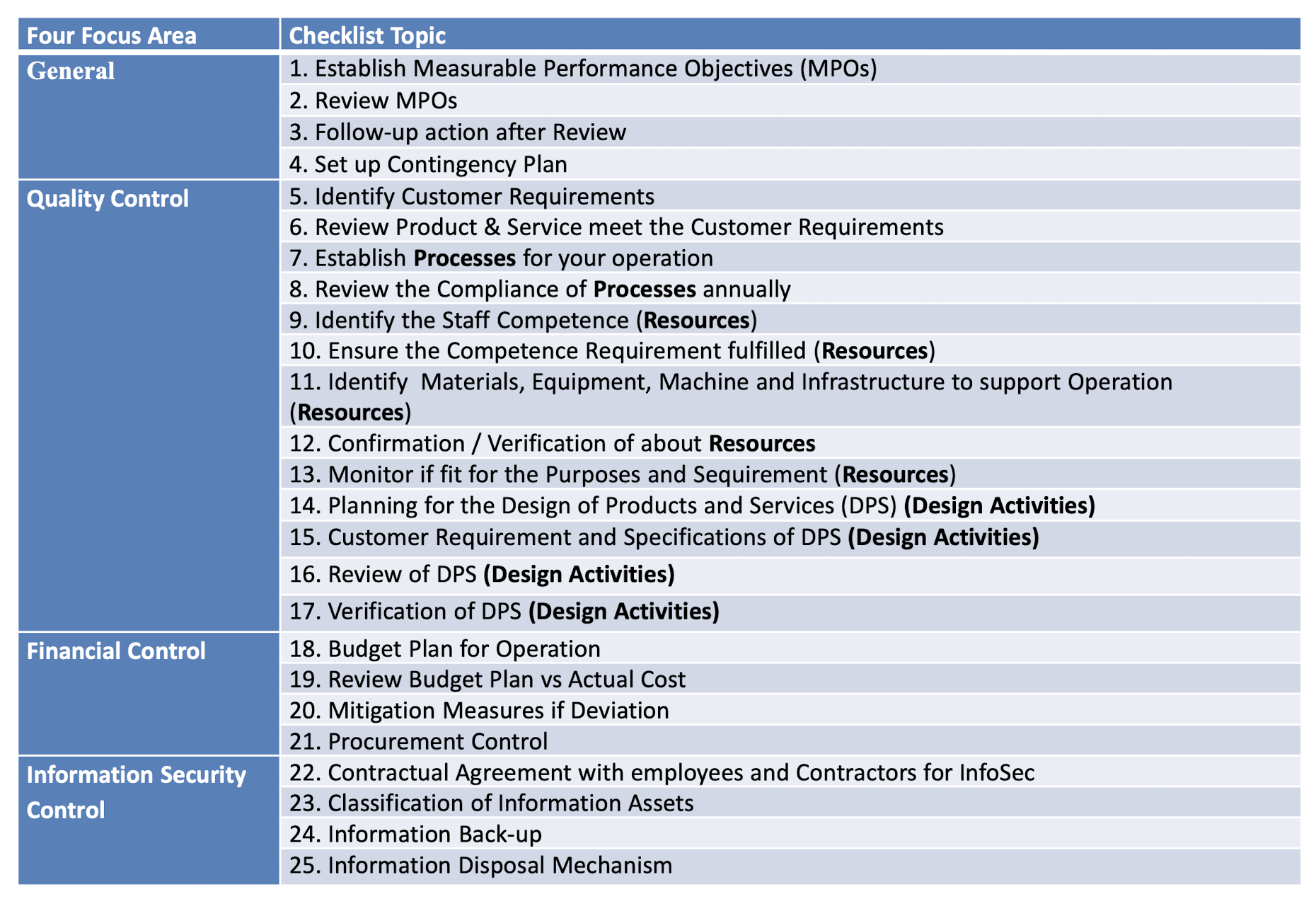
- Difficulties on HKQAA Assessment Checklist for Start-up Company
- Without systematic model for start-up to implement to achieve these requirements.
- Without a stepwise framework for QStarMS to follow.
- Without guideline for implementation, especially on three key areas control (Product, Finance & InfoSec).
10.5.4 Quality Startup Management System (QStarMS) Model
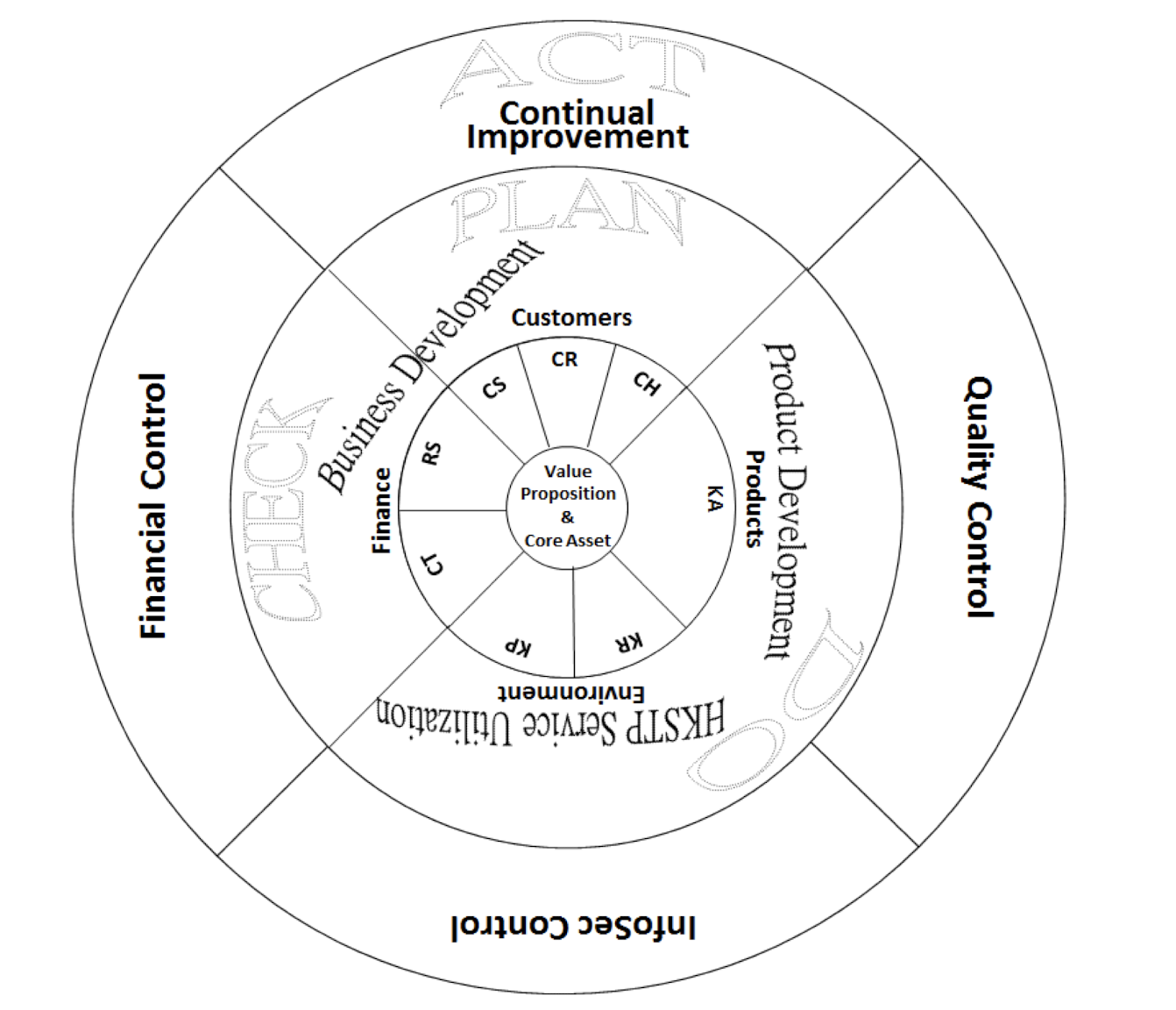
10.5.5 Conclusion for QStarMS Model
- Start-ups employ Quality Startup Management System (QStarMS) Model and have registration under HKQAA Startup Recognition Scheme:
- business opportunity and management skill level, as well as, successful rate will increase
- overcome the difficulties and limitation for start-ups’ business and product development, and to enhance their management skill level
- The implementation workshop for start-ups will be provided by HKSTP Corporate Quality Unit (CQU) and it is Free of Charge for pilot program.
10.5.6 Extenics + Quality Startup Management System (ExQStarMS)
10.6 Key Success Factors and Key Failure Factors
10 Key Success Factors for a Start-up
- Strategic Vision, Mission, Objectives
- An Articulate Profitable Business Model
- Defensible Technology Weapon
- Concentrate on the Core Competency
- Plan for Future and Growth
- CEO Quality
- A Balanced Team with Clear Role
- Execution Capability
- Product Strategy
- Financial Management and Ability to Raise Capital
10 Key Failure Factors for a Start-up
- Two Equal Shares or Multiple Equal Shares
- No Personal Commitment
- Entering into Bad Shareholders’ Agreement
- A Product Chasing a Problem
- Low Cost Producer
- Relying on 1-2 Buyers/Suppliers
- Not “locking up” company valuable asset
- Two Couples Company
- A Perfectionist Company
- A 100% Laboratory Scientists Company
11. Professional Bodies & Code of Conduct
11.1 Introduction of anti-bribery
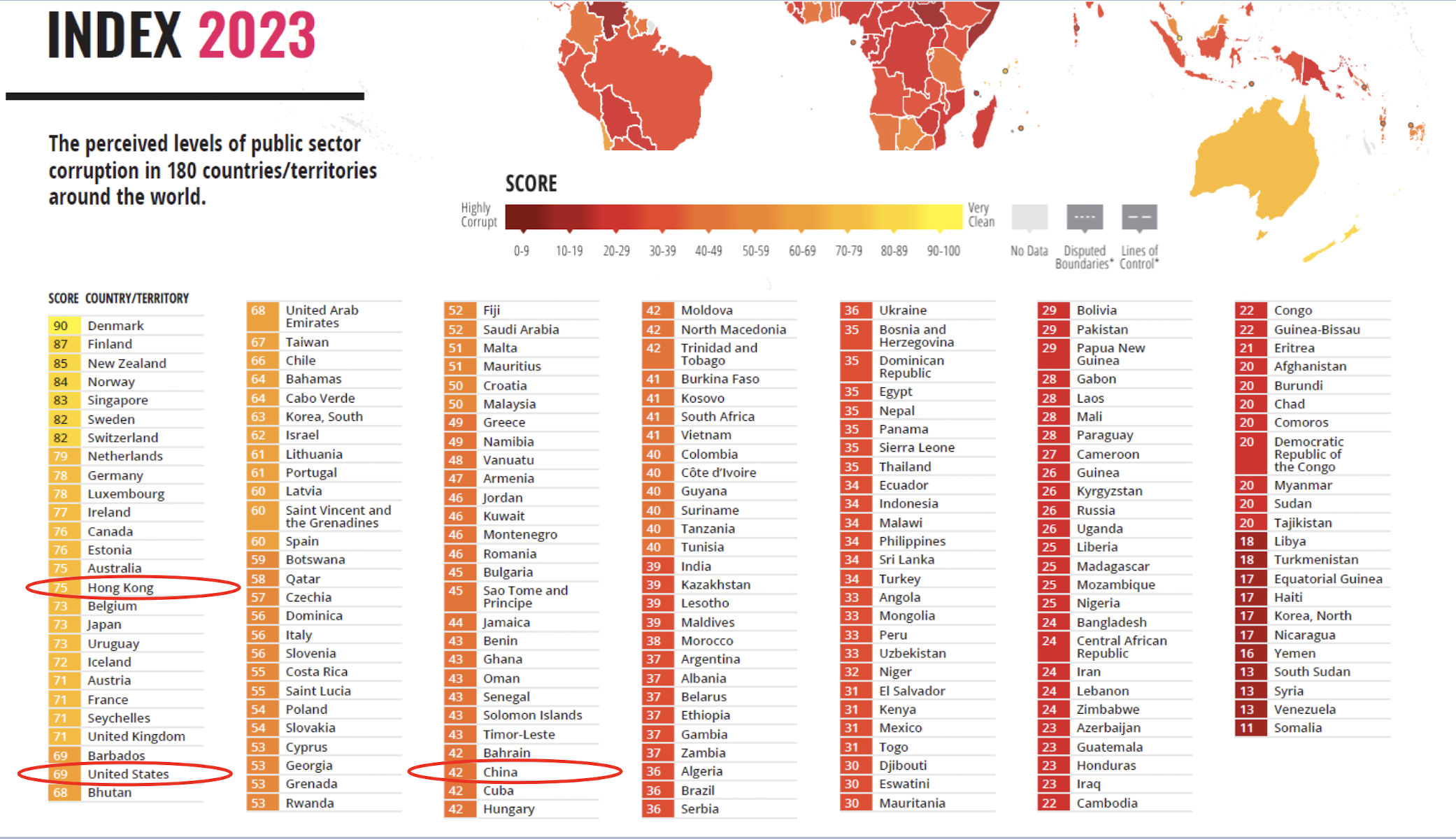
11.2 Professional Integrity
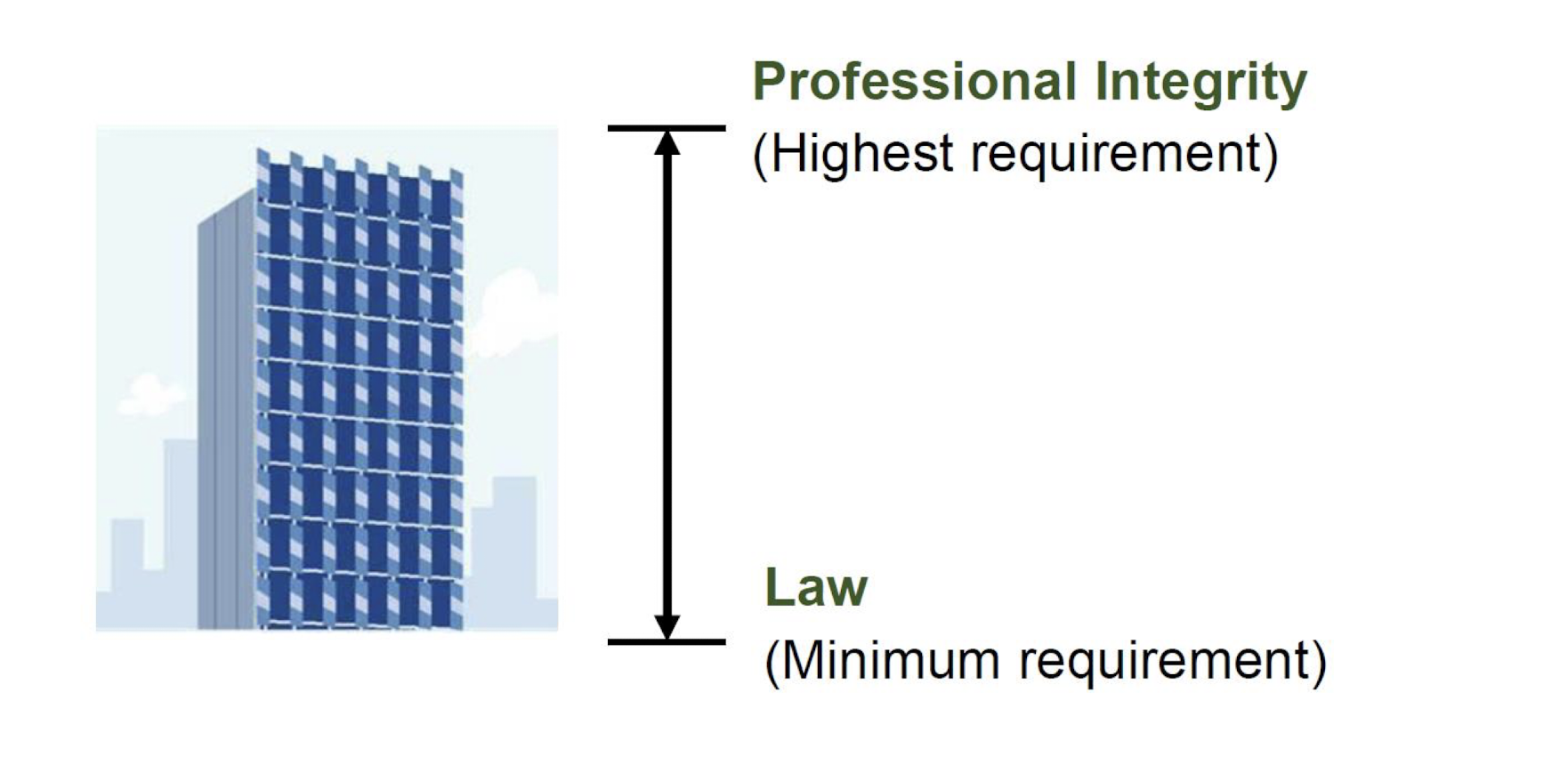
11.2 Professional Bodies Code of Conduct
11.2.1 HKCS Code of Ethics and Professional Conduct
- This Code of Ethics and Professional Conduct is directed to all members of The Hong Kong Computer Society (HKCS).
- It consists, essentially, of a series of statements, which prescribe minimum standards of Code of Ethics, to be observed by all members.
- These rules grouped into the four principal areas:
A. Professional Competence and Integrity
B. Social Implications
C. Organization and Leadership
D. Duty to the Profession
11.2.1.1 A. Professional Competence and Integrity
- As a Member of HKCS, I will…
1. Be honest and trustworthy , and will not knowingly engage in or associate with dishonest or fraudulent practices.
2. Continue to upgrade my professional knowledge and skills, and shall maintain awareness of technological developments, procedures and standards, which are relevant to my field.- Only offer to do work or provide a service, which is within my professional competence and shall not claim any level of competence that I do not possess; any professional opinion which I am asked to give shall be objective and reliable.
4. Qualify professional opinions , which I know are based on limited knowledge or experience. I will not misrepresent my skills or knowledge nor knowingly mislead a client or potential client as to the suitability of a product or service. - Not require, or attempt to influence, any person to take any action, which would involve a breach of this Code.
- Only offer to do work or provide a service, which is within my professional competence and shall not claim any level of competence that I do not possess; any professional opinion which I am asked to give shall be objective and reliable.
11.2.1.2 B. Social Implications
- As a Member of HKCS, I will…
1. Increase my awareness of issues affecting the IT profession and its relationship with the community.- Ensure that within my chosen fields, I have knowledge and understanding of relevant legislation, regulations and standards and that I comply with such requirements.
3. Honour property rights (including copyrights and patents) and give proper credit for work done by others where credit is due.
4. Honour confidentiality and respect the privacy of others.
5. Be fair and take action not to discriminate.
6. Contribute to society and human well-being and avoid harm to others.
7. Protect and promote the health and safety of those affected by my work and have regard to the protection of the environment. - Have regard for human rights and avoid any actions that adversely affect such rights.
- Endeavour to understand and give due regard to the perceptions of those affected by my work, whether or not I agree with those perceptions.
- Ensure that within my chosen fields, I have knowledge and understanding of relevant legislation, regulations and standards and that I comply with such requirements.
11.2.1.3 C. Organization
As a Member of HKCS, I will…
- Keep myself and subordinates informed of such new technologies, practices, legal requirements and standards as are relevant to my duties, and seek to conform to recognized good practices including quality standards, which are in my judgment relevant, and encourage my subordinates to do likewise.
- Encourage my colleagues, employees and students to continue their own professional development , and ensure that subordinates are trained in order to be effective in their duties and to qualify for increased responsibilities.
3. Create opportunities for members of the organization to learn the principles and limitations of IT and systems.
4. Accept professional responsibility for my work and for the work of my subordinates and associates under my direction, and shall not terminate any assignment except for good reason and on reasonable notice.
5. Avoid any situation that may give rise to a conflict of interest between myself and my client, I will make full and immediate disclosure to the client if any conflict should occur.
6. Articulate social responsibilities of members of an organizational unit and encourage full acceptance of those responsibilities.
7. Manage personnel and resources to design and build information systems that enhance the quality of working life.
8. Endeavour to provide products and services , which match the operational and financial needs of my clients and employers. - Go beyond my brief, if necessary, in order to act professionally.
Acknowledge and support proper and authorized uses of an organization’s IT resources.
Ensure that users and those who will be affected by a system have their needs clearly articulated during the assessment and design of requirements; later the system must be validated to meet requirements.
12. Articulate and support policies that protect the dignity of users and others affected by IT and systems.- Carry out work with due care and diligence in accordance with the requirements of the employer or client and will, if my professional judgment is overruled, indicate the likely consequences.
14. Endeavour to complete work undertaken on time and to budget and I will advise my employer or client as soon as practicable if any overrun is foreseen.
15. Not offer or provide, or receive in return, inducement for the introduction of business from a client unless there is full prior disclosure of the facts to the client.
16. Respect and protect my clients’ and employers’ proprietary interests. I will not disclose or authorize to be disclosed, or use for personal gain or to benefit a third party, confidential information acquired in the course of professional practice, except with prior written permission of the employer or client, or at the direction of a court of law.
17. Seek to avoid being put in a position where I may become privy to or party to activities or information concerning activities which would conflict with my responsibilities.
18. Not misrepresent or withhold information on the capabilities of products, systems or services with which I am concerned or take advantage of the lack of knowledge or inexperience of others.
19. Not (except where specifically so instructed) handle client’s monies or place contracts or orders in connection with work on which I am engaged, when acting as an independent consultant.
20. Not purport to exercise independent judgment on behalf of a client on any product or service in which I knowingly have any interest, financial or otherwise.
11.2.1.4 D. Duty to Profession
- As a Member of HKCS, I will…
1. Uphold the reputation of the profession and I will seek to improve professional development through participation in their development, use and enforcement, and shall avoid any action that will adversely affect the good standing of the profession.
2. Seek to advance public knowledge and understanding of computing and information systems and technology and to counter false or misleading statements that are detrimental to the profession.
3. Encourage and support fellow members in their professional development , and where possible, provide opportunities for the professional development of new entrants to the profession.
4. Act with integrity towards members of other professions with whom I am concerned in a professional capacity and will avoid engaging in any activity, which is incompatible with professional status.
5. Not make any public statements in my professional capacity unless I am properly qualified and, where appropriate, authorized to do so, and will have due regard to the likely consequences of any statement on others.
6. Respect , and seek when necessary, the professional opinions of colleagues in their areas of competence.
7. Not attempt to enhance my own reputation at the expense of another’s reputation.
8. Co-operate in advancing information processing by communication with other professionals, students and the public, and by contributing to the efforts of professional and scientific societies as well as universities, colleges or schools.- Distance myself professionally from someone whose professional membership of HKCS has been terminated because of unethical behavior or unsatisfactory conduct.
10. Take appropriate action if I discover a member or a potential member of HKCS engaging in unethical behavior.
11. Seek advice from the Society’s Director of Professional Development when faced with an ethical dilemma that I cannot resolve by myself. - Acknowledge my responsibility to the IT profession and in return will protect and promote professionalism in IT. Accept and provide an appropriate review of professional work of others, including review of applications for professional membership.
- Do what I can to ensure that the corporate actions of the HKCS are in accordance with this Code. 11
- Distance myself professionally from someone whose professional membership of HKCS has been terminated because of unethical behavior or unsatisfactory conduct.
11.2.2 HKIE – The Ordinance and Constitution “Rules of Conduct”
- The Ordinance and Constitution make it clear that HKIE members are required to conduct themselves in a manner which is becoming to professional engineers.
- Rule 1 - Responsibility to the Profession
- A member of the Institution shall order his conduct so as to uphold the dignity, standing and reputation of the profession.
- Rule 2 - Responsibility to Colleagues
- A member of the Institution shall not maliciously or recklessly injure nor attempt to injure whether directly or indirectly the professional reputation of another engineer, and shall foster the mutual advancement of the profession.
- Rule 3 - Responsibility to Employers or Clients
- A member of the Institution shall discharge his duties to his employer or client with integrity and in accordance with the highest standards of business ethics.
- Rule 4 - Responsibility to the Public
- A member of the Institution in discharging his responsibilities to his employer and the profession shall at all times be governed by the overriding interest of the general public, in particular their environment, welfare, health and safety.
11.2.2.1 Rule 1 - Responsibility to the Profession
- Discharge his professional responsibilities with integrity, dignity, fairness and courtesy ;
2. Not allow himself to be advertised in self-laudatory language nor in any manner derogatory to the dignity of his profession, nor improperly solicit professional work for himself or others;
3. Give opinions in his professional capacity that are, to the best of his ability, objective, reliable and honest; - Take reasonable steps to avoid damage to the environment and the waste of natural resources or the products of human skill and industry;
- Ensure adequate development of his professional competence ;
6. Accept responsibility for his actions and ensure that persons to whom he delegates authority are sufficiently competent to carry the associated responsibility;
7. Not undertake responsibility which he himself is not qualified and competent to discharge;
8. Treat colleagues and co-workers fairly and not misuse the advantage of position; - When working in a country other than Hong Kong order his conduct according to the existing recognized standards of conduct in that country , except that he should abide by these rules as applicable in the absence of local standards;
- When working within the field of another profession pay due attention to the ethics of that profession.
11.2.2.2 Rule 2 - Responsibility to Colleagues
- Where appropriate seek, accept and offer honest criticism of work and properly credit the contributions of others;
- Seek to further the interchange of information and experience with other engineers;
3. Assist and support colleagues and engineering trainees in their professional development;
4. Not abuse his connection with the Institution to further his business interests;
5. Not maliciously or falsely injure the professional reputation , prospects or practice of another member provided however that he shall bring to the notice of the Institution any evidence of unethical, illegal or unfair professional practice;
6. Support the aims and activities of the Institution.
11.2.2.3 Rule 3 - Responsibility to Employers or Clients
1. Offer complete loyalty to his employer or client, past and present, in all matters concerning remuneration and in all business affairs and at the same time act with fairness between his employer or client and any other party concerned;
2. Avoid engaging in business , investments or activities which conflict with the interests of his employer or client , and inform his employer or client in writing of any possible conflict between his own financial interests, or those of his immediate family, and the interests of his client or employer;
3. Not accept any financial or contractual obligation on behalf of his employer or client without their authority;
- Where possible advise those concerned of the consequences to be expected if his engineering judgment , in areas of his responsibility, is overruled by a non-technical authority;
- Advise his employer or client in anticipating the possible consequences of relevant developments that come to his knowledge;
6. Neither give nor accept any gift, entertainment, payment or service of more than nominal value, to or from those having a business relationship with his employer or client without the consent of the latter; - Where necessary co-operate with or arrange for the services of other experts wherever an employer’s or client’s interest might best be served thereby;
8. Safeguard confidential information in relation to his employer or client and not disclose such information to third parties without his employer’s or client’s written consent. A member shall not receive any gift, entertainment, payment or service from third parties for disclosing such information nor make use of it for personal gain.
11.2.2.4 Rule 4 - Responsibility to the Public
- Seek to protect the safety, health and welfare of the public;
- When making a public statement professionally, try to ensure that both his qualification to make the statement and his association with any benefiting party are made known to the recipients of the statement;
3. Seek to extend public understanding of the engineering profession; - Seek to assess the environmental consequences of work for which he is responsible and to influence events so as to prevent or minimize damage to, and if practicable to improve, the environment.
11.3 Anti-bribery Management System (ISO 37001 )
11.3.1 ISO 37001 – Anti-bribery Management System (ABMS)
- The standard provides guidance to help an organization implement an anti-bribery management systems**
- It can also help an organization to prevent, detect, and address bribery.
11.3.2 History of ISO 37001
BS 10500:2010
- It was published in 2011 as a response to the UK Bribery Act of 2021
ISO 37001:2016
- It specifies anti-bribery measures and controls and includes guidance for their implementation
11.3.3 Compliance with applicable anti-bribery laws
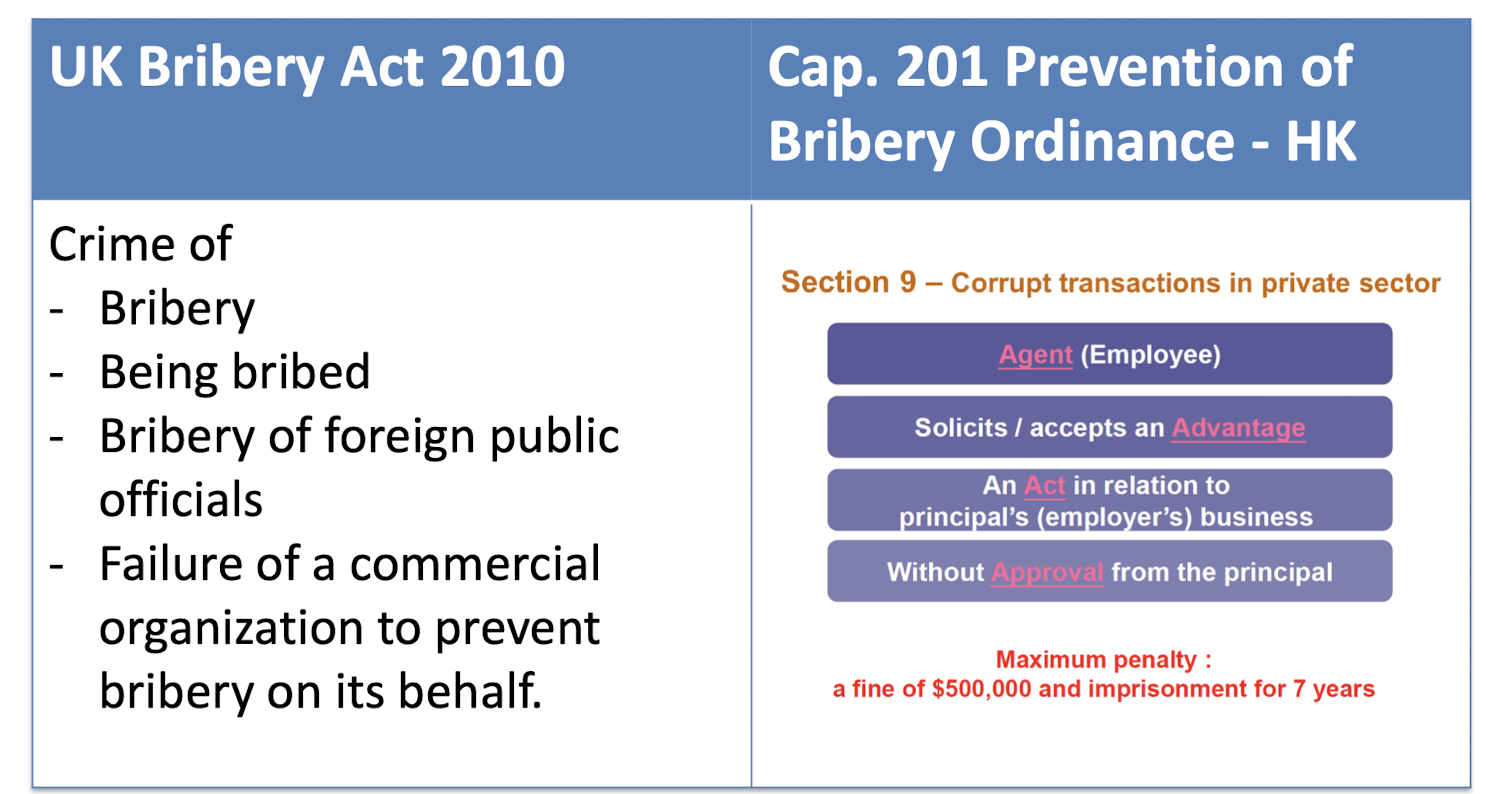
11.3.4 The drivers for ISO 37001
- Corruption is the abuse of public or private office for personal gain
- Serious impacts on economic, political and social development
- Bribery is one form of corruption
- Cost of corruption >5% of global GDP (World Economic Forum)
- Over US$ 1 trillion paid in bribes each year (World Bank)
11.3.5 ISO 37001 Development Stages
11.3.6 Three Key Components of ABMS
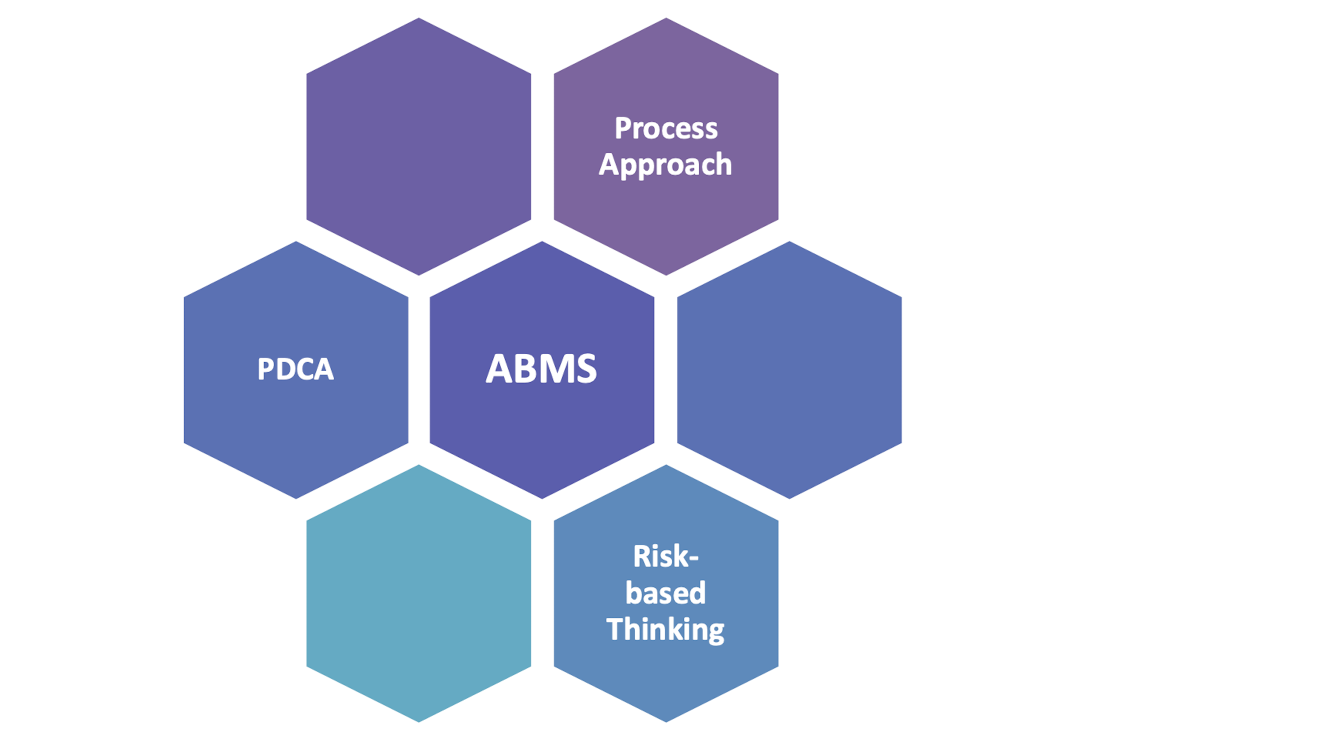
11.3.7 Potential Benefits of Implementing ABMS
It assists an organization in implementing an anti-bribery management system, or in enhancing its existing controls;
It helps provide assurance to stakeholders that the organization has implemented internationally recognized good practice anti-bribery controls;
In the event of an investigation, it helps provide evidence to the prosecutors or courts that the organization had take reasonable steps to prevent bribery.
11.3.8 Interested Party and Stakeholder
- ISO 37001 clause 3.3
- Person or organization that can affect, be affected by, or perceive itself to be affected by a decision or activity.
- Note 1 to entry: A stakeholder can be internal or external to the organization
11.3.9 Definition of Bribery
- 3.1 bribery
- offering, promising, giving, accepting or soliciting of an undue advantage of any value (which could be financial or non-financial), directly or indirectly, and irrespective of location(s), in violation of applicable law, as an inducement or reward for a person acting or refraining from acting in relation to the performance (3.16) of that person’s duties
- Note 1 to entry: The above is a generic definition. The meaning of the term “bribery” is as defined by the antibribery law applicable to the organization (3.2) and by the anti-bribery management system_ (3.5) designed by the organization.
11.3.10 ISO 37001 without cover
Fraud (欺詐), cartels/price fixing (壟斷/合謀定價) and other anti-trust/competition (反競爭) offences, money-laundering (洗黑錢) or other activities related to corrupt practices
However, an organization may choose to extend the scope of the ABMS to include above activities.
11.3.11 Governing Body
- ISO 37001 clause 3.7
- governing body
- group or body that has the ultimate responsibility and authority for an organization’s (3.2) activities, governance and policies and to which top management (3.6) reports and by which top management is held accountable
- Note 1 to entry: Not all organizations, particularly small organizations, will have a governing body separate from top management (see 3.6, Note 3 to entry).
- Note 2 to entry: A governing body can include, but is not limited to, board of directors, committees of the board, supervisory board, trustees or overseers.
11.3.12 Business Associate
- 3.26 business associate
- external party with whom the organization (3.2) has, or plans to establish, some form of business relationship
- Note 1 to entry: Business associate includes but is not limited to clients, customers, joint ventures, joint venture (JV) partners, consortium partners, outsourcing providers, contractors, consultants, sub-contractors, suppliers, vendors, advisors, agents, distributors, representatives, intermediaries and investors. This definition is deliberately broad and should be interpreted in line with the bribery risk (3.12) profile of the organization to apply to business associates which can reasonably expose the organization to bribery risks.
- Note 2 to entry: Different types of business associate pose different types and degrees of bribery risk, and an organization (3.2) will have differing degrees of ability to influence different types of business associate. Different types of business associate can be treated differently by the organization’s bribery risk assessment and bribery risk management procedures.
- Note 3 to entry: Reference to “business” in this document can be interpreted broadly to mean those activities that are relevant to the purposes of the organization’s existence.
11.3.13 ISO 37001 Requirements
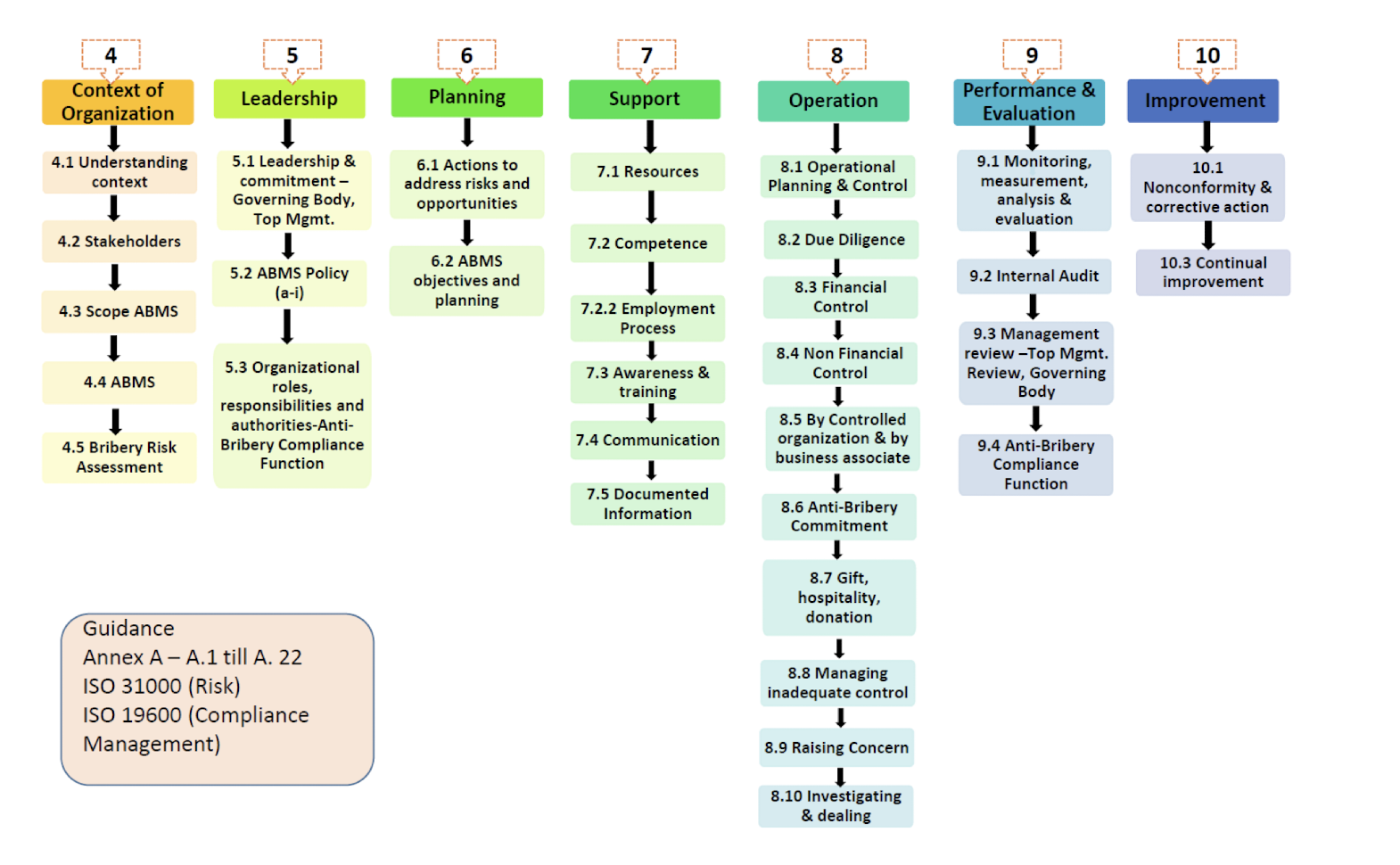
11.3.14 Bribery Risk Assessment (4.5)
- Identify the bribery risks the organization
- Analyze, assess and prioritize the identified bribery risks
- Evaluate the suitability and effectiveness of the organization’s existing controls to mitigate the assessed bribery risks.
- Establish criteria for evaluating its level of bribery risk
- Organization’s policies and objectives take into account
- Review the bribery risk assessment on a regular basis
- Retain the documented information
11.3.15 Summary – Cl.4: Context of Organization
- Understand the organization (Refer A.13.1.3)
- Determine the scope of ABMS (Refer A.2)
- Conduct bribery risk assessment (Refer A.4)
- ISO 31000:2009 Risk Management – Principles and guidelines
- ISO/IEC 31010:2009 Risk Management – Risk assessment techniques
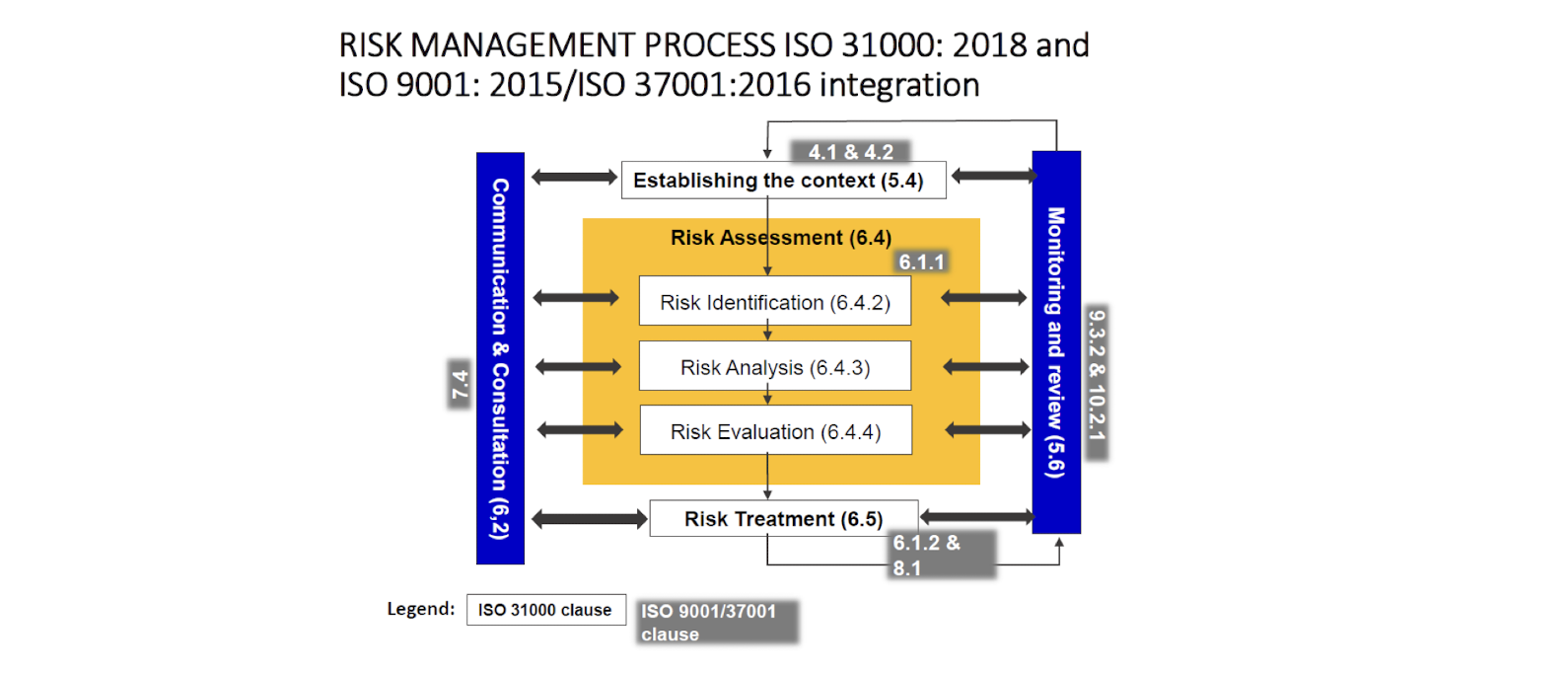
11.3.16 Summary – Cl.5: Leadership
- Governing Body
- Top management (Refer A.5)
- Anti-bribery Compliance Function (Refer A.6) – guidance ISO 19600
- Anti-bribery Policy (a-i)
Policies and Guidelines - Code of Conduct & Business Ethic
- Disciplinary Policy
- Gift / No Gift Policy
- Whistle-Blowing Policy
- Charitable Contributions / Sponsorship / Donation Policy
- Facilitation Payments
- Hospitality / Entertainment Expenses
- Conflicts of Interest, etc.
11.3.17 Examples of Anti-bribery Policy
- Coca-Cola Anti-bribery policy
- Our attitude to corruption is clear: zero tolerance.
- https://coca-colahellenic.com/en/about-us/policies/anti-bribery-policy/
- Microsoft Anti-Corruption Compliance Program (Standard & Policy)
- CISCO Anti-Corruption and Bribery Policy
11.3.18 Cl. 7: Support - Implement Procedures
- Employment procedures (7.2.2)
- Training (7.3)
- Anti-bribery control (8.5)
- Business associates (8.6)
- Gifts, hospitality, donations and similar benefit (8.7)
- Raising concerns (8.9)
- Investigating and dealing with bribery (8.10)
11.3.19 Employment Procedures (7.2.2)
- Conditions of employment must:
- Require personnel to comply with the Anti-bribery policy and ABMS
- Give the organization the right to discipline personnel in the event of noncompliance;
- Personnel to have access to Anti-bribery policy, and training on it.
- Procedures to enable disciplinary action for violation.
- Personnel will not suffer retaliation, discrimination or disciplinary action (e.g. by threats, isolation, demotion, preventing, advancement, transfer, dismissal, bullying, victimization, or other forms of harassment).
- For personnel who might be exposed to bribery, procedures
11.3.20 Summary – Cl.8: Operation
- Control of operations to reduce bribery risks ( gifts, hospitality, donations policy/procedures) (Refer A.15)
- Due diligence required for operations that is above low bribery risk (Refer A.10)
- Financial (Refer A.11) & Non-Financial Control (Refer A.12)
- Control of business associates to reduce bribery risks to the organization (Refer A.13 & Refer A.14)
- Managing concerns relating to bribery ( reporting, investigating, protect those making report) (Refer A.18)
- Managing non-compliance of controls
11.3.21 Financial Controls (8.3)
The organization shall implement financial controls that manage bribery risk.
For example, two signatures on payment, restricting use of cash, separation of duties, etc.
11.3.22 Summary – Cl.9: Performance Evaluation
- Monitoring and evaluate anti-bribery performance
- (Refer A.19)
- Refer ISO 19600:2014 Compliance Management System – Guidelines
- Internal Audit (Refer A.16)
- Review by Anti-bribery compliance function
- Review by Top Management
- Review by Governing Body
11.3.23 Cl.10: Improvement
- Cl.10.1 Nonconformity and corrective action
- Cl.10.2 Continual improvement
- Responding to non-conformities (React, Evaluate, Implement and Review Action)
- Refer A.20
11.3.24 ISO 37001 – Annex A
- A.1 General
- A.2 Scope of the anti-bribery management system
- A.2.1Stand-alone or integrated anti-bribery management system - A.2.2Facilitation and extortion payments - A.3 Reasonable and proportionate
- A.4 Bribery risk assessment
- A.5 Roles and responsibilities of governing body and top management
- A.6 Anti-bribery compliance function
- A.7 Resources
- A.8 Employment procedure
- A.8.1 Due diligence on personnel
- A.8.2Performance bonuses
- A.8.3 Conflicts of interest
- A.8.4 Bribery to the organization’s personnel
- A.8.5 Temporary staff or workers
- A.9 Awareness and training
- A.10 Due diligence
- A.11 Financial controls
- A.12 Non-financial controls
- A.13 Implementation of the anti-bribery management system by controlled organizations and by business associates
- A.13.1 General - A.13.2 Controlled organizations - A.13.3 Non-controlled business associates - A.14 Anti-bribery commitments - A.15 Gifts, hospitality, donations and similar benefits
- A.16 Internal audit
- A.17 Documented information
- A.18 Investigating and dealing with bribery
- A.19 Monitoring
- A.20 Planning and implementing changes to the anti-bribery management system
- A.21 Public officials
- A.22 Anti-bribery initiatives
11.3.25 The Journey of ISO 37001
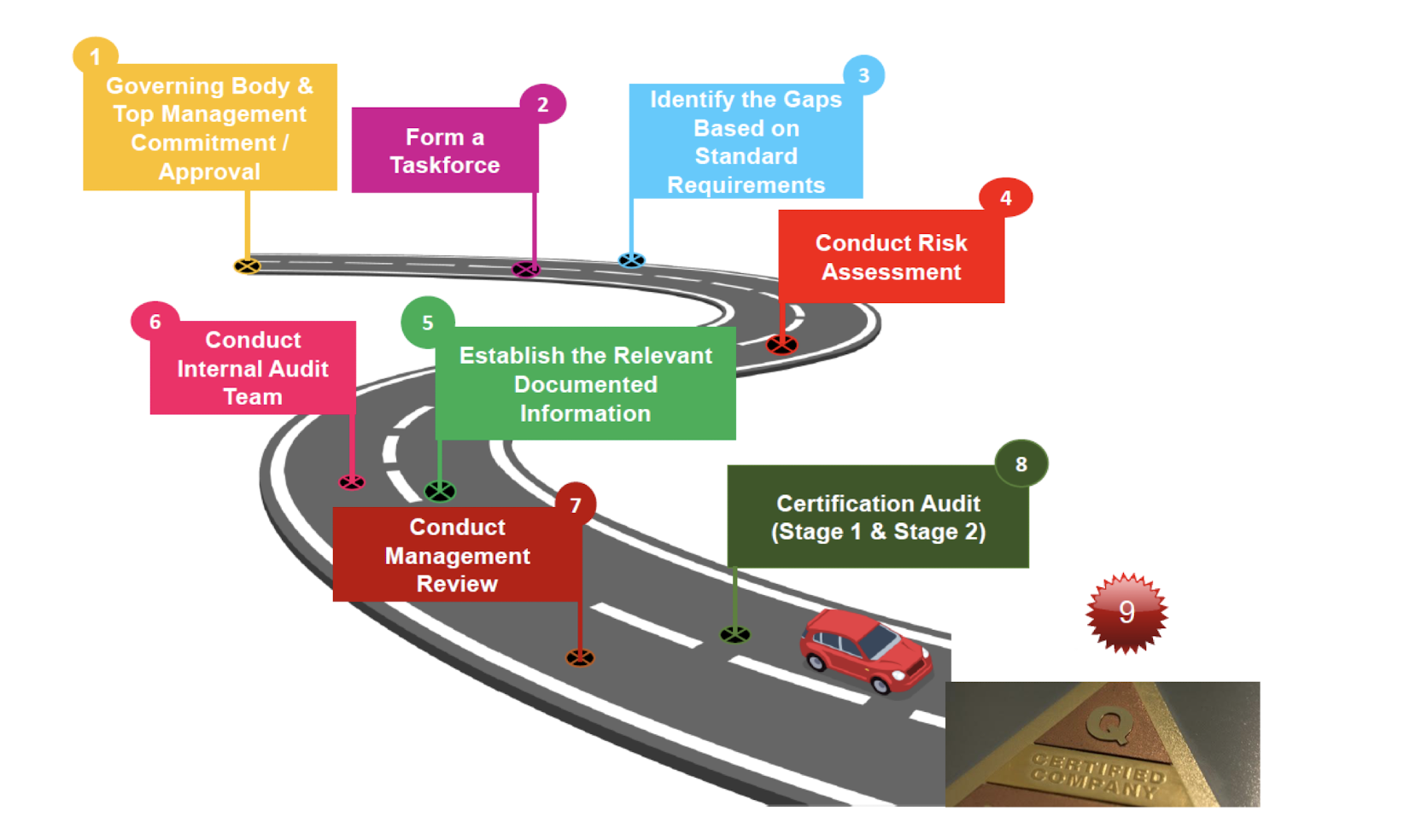
11.3.26 Essential Elements for Successful ABMS

References
Slides of COMP3511 Legal Aspect and Ethics of Computing, The Hong Kong Polytechnic University.
个人笔记,仅供参考
PERSONAL COURSE NOTE, FOR REFERENCE ONLY
Made by Mike_Zhang
